信息网络安全 ›› 2025, Vol. 25 ›› Issue (10): 1604-1614.doi: 10.3969/j.issn.1671-1122.2025.10.011
基于共性伪造线索感知的物理和数字人脸攻击联合检测方法
- 1.太原理工大学电子信息工程学院,晋中 030600
2.中国科学院自动化研究所,北京 100190
-
收稿日期:2025-04-23出版日期:2025-10-10发布日期:2025-11-07 -
通讯作者:梁凤梅 E-mail:fm_liang@163.com -
作者简介:梁凤梅(1969—),女,山西,副教授,博士,主要研究方向为信息安全、图像处理、图像通信、计算机视觉、智能信息处理|潘正豪(2001—),男,山西,硕士研究生,主要研究方向为计算机视觉、图像处理、人脸活体检测|刘阿建(1992—),男,山西,助理研究员,博士,主要研究方向为计算机视觉、人脸活体检测 -
基金资助:国家自然科学基金(62406320)
A Joint Detection Method for Physical and Digital Face Attacks Based on Common Forgery Clue Awareness
LIANG Fengmei1( ), PAN Zhenghao1, LIU Ajian2
), PAN Zhenghao1, LIU Ajian2
- 1. College of Electronic Information Engineering, Taiyuan University of Technology, Jinzhong 030600, China
2. Institute of Automation, Chinese Academy of Sciences, Beijing 100190, China
-
Received:2025-04-23Online:2025-10-10Published:2025-11-07 -
Contact:LIANG Fengmei E-mail:fm_liang@163.com
摘要:
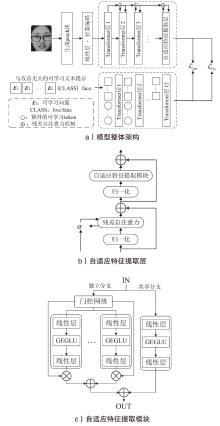
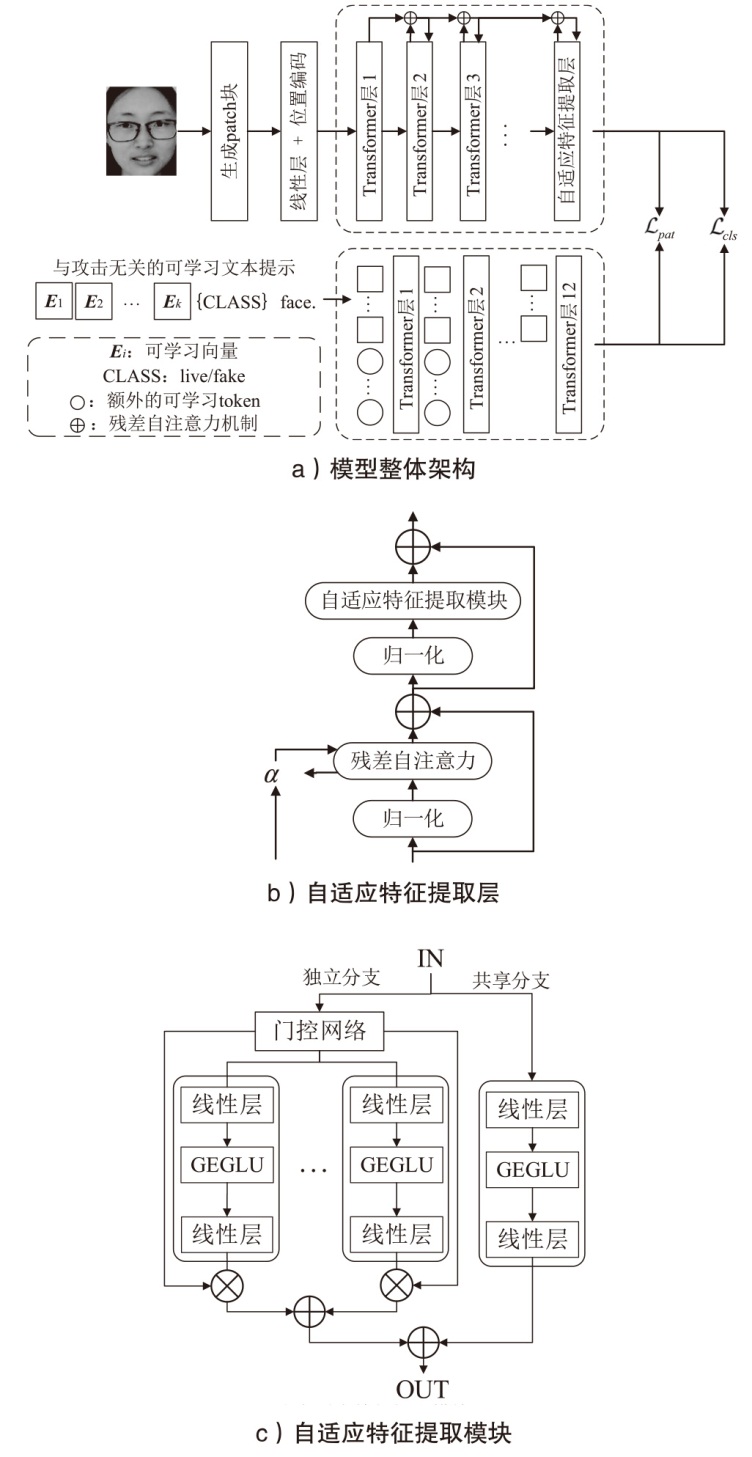
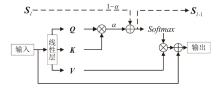
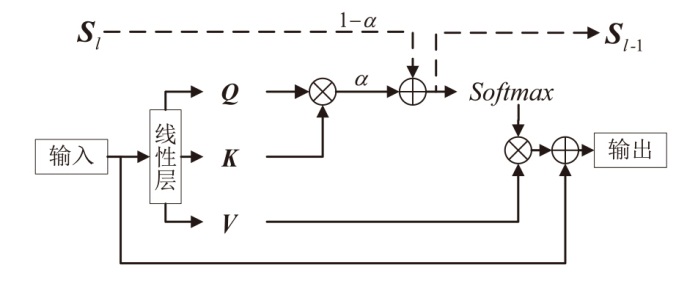
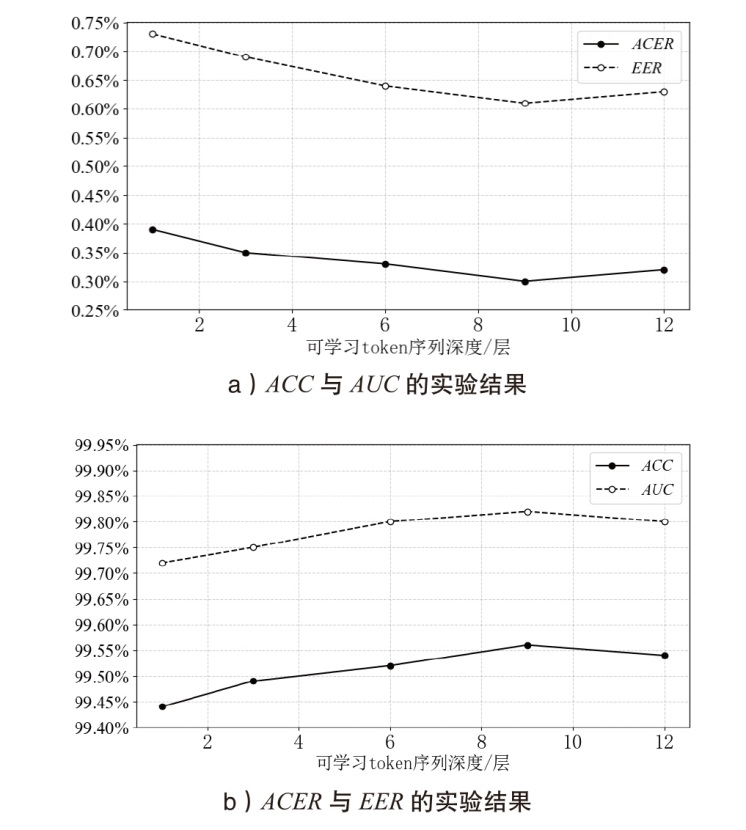
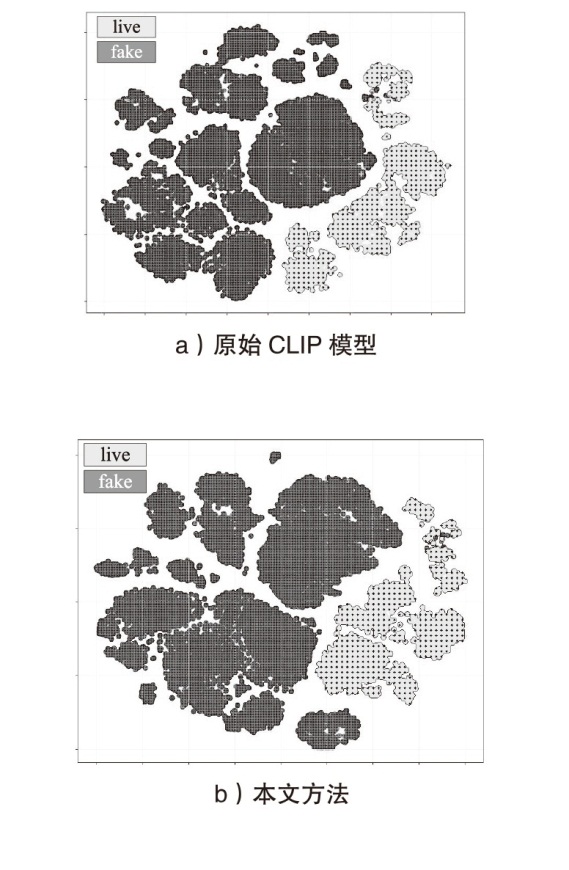
人脸识别系统在实际应用中面临物理攻击与数字攻击的双重威胁。由于两类攻击存在显著异质性,通常需要依赖不同的模型分别应对。为了节约计算资源及硬件部署成本,针对物理攻击和数字攻击在特征空间中呈现显著分布差异且按攻击类型聚类的特点,文章提出基于对比语言和图像预训练模型的物理和数字人脸攻击联合检测方法。首先,文章基于混合专家结构提出自适应特征提取模块,通过稀疏激活并结合共享分支实现攻击类型自适应的特征选择;然后,提出一种与攻击无关的可学习文本提示,探索物理和数字攻击的共性伪造线索,实现不同攻击特征簇的有效聚合;最后,引入残差自注意力机制,并设计了细粒度对齐损失,优化共性伪造线索提取过程。在UniAttackData和JFSFDB数据集的联合训练协议上的实验结果表明,相较于其他算法,该方法实现了较低的平均分类错误率。
中图分类号:
引用本文
梁凤梅, 潘正豪, 刘阿建. 基于共性伪造线索感知的物理和数字人脸攻击联合检测方法[J]. 信息网络安全, 2025, 25(10): 1604-1614.
LIANG Fengmei, PAN Zhenghao, LIU Ajian. A Joint Detection Method for Physical and Digital Face Attacks Based on Common Forgery Clue Awareness[J]. Netinfo Security, 2025, 25(10): 1604-1614.
表2
UniAttackData数据集上的实验结果
| 方法 | ACER | ACC | AUC | EER |
|---|---|---|---|---|
| ResNet50 | 1.35% | 98.83% | 99.79% | 1.18% |
| ViT-B/16 | 5.92% | 92.29% | 97.00% | 9.14% |
| Auxiliary | 1.13% | 98.68% | 99.82% | 1.23% |
| CDCN | 1.40% | 98.57% | 99.52% | 1.42% |
| FFD | 2.01% | 97.97% | 99.57% | 2.01% |
| UniAttackDetect | 0.52% | 99.45% | 99.95% | 0.53% |
| La-SoftMoE | 0.32% | 99.54% | 99.72% | 0.56% |
| MoAE-CR | 0.37% | 99.47% | 99.97% | 0.49% |
| 本文方法 | 0.30% | 99.56% | 99.82% | 0.61% |
表3
JFSFDB数据集上的实验结果
| 方法 | ACER | ACC | AUC | EER |
|---|---|---|---|---|
| ResNet50 | 7.70% | 90.43% | 98.04% | 6.71% |
| ViT-B/16 | 8.75% | 90.11% | 98.16% | 7.54% |
| Auxiliary | 11.16% | 87.40% | 97.39% | 9.16% |
| CDCN | 12.31% | 86.18% | 95.93% | 10.29% |
| FFD | 9.86% | 89.41% | 95.48% | 9.98% |
| La-SoftMoE | 4.21% | 95.85% | 99.11% | 4.19% |
| MoAE-CR | 4.40% | 95.33% | 98.97% | 4.66% |
| 本文方法 | 4.17% | 95.89% | 99.23% | 4.51% |
| [1] |
SUN Zhenan, HE Ran, WANG Liang, et al. Overview of Biometrics Research[J]. Journal of Image and Graphics, 2021, 26(6): 1254-1329.
doi: 10.11834/jig.210078 URL |
| 孙哲南, 赫然, 王亮, 等. 生物特征识别学科发展报告[J]. 中国图象图形学报, 2021, 26(6):1254-1329. | |
| [2] | ZHANG Zhiwei, YAN Junjie, LIU Sifei, et al. A Face Anti-Spoofing Database with Diverse Attacks[C]// IEEE. 5th IAPR International Conference on Biometrics (ICB). New York: IEEE, 2012: 26-31. |
| [3] | CHINGOVSKA I, ANJOS A, MARCEL S. On the Effectiveness of Local Binary Patterns in Face Anti-Spoofing[C]// IEEE. BIOSIG-Proceedings of the International Conference of Biometrics Special Interest Group (BIOSIG). New York: IEEE, 2012: 1-7. |
| [4] |
LIU Ajian, ZHAO Chenxu, YU Zitong, et al. Contrastive Context-Aware Learning for 3D High-Fidelity Mask Face Presentation Attack Detection[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 2497-2507.
doi: 10.1109/TIFS.2022.3188149 URL |
| [5] | CIFTCI U A. Fakecatcher: Detection of Synthetic Portrait Videos Using Biological Signals[EB/OL]. (2020-07-15)[2025-03-13]. https://ieeexplore.ieee.org/abstract/document/9141516. |
| [6] |
TOLOSANA R, VERA-RODRIGUEZ R, FIERREZ J, et al. Deepfakes and Beyond: A Survey of Face Manipulation and Fake Detection[J]. Information Fusion, 2020, 64: 131-148.
doi: 10.1016/j.inffus.2020.06.014 URL |
| [7] |
YU Zitong, CAI Rizhao, CUI Yawen, et al. Visual Prompt Flexible-Modal Face Anti-Spoofing[J]. IEEE Transactions on Dependable and Secure Computing, 2024, 22: 2597-2606.
doi: 10.1109/TDSC.2024.3520534 URL |
| [8] | WANG Chundong, LI Quan, FU Haoran, et al. Face Anti-Spoofing Method with Adversarial Robustness[EB/OL]. (2024-06-06) [2025-03-13]. https://www.jsjkx.com/CN/10.11896/jsjkx.230400022. |
| 王春东, 李泉, 付浩然, 等. 具有对抗鲁棒性的人脸活体检测方法[EB/OL]. (2024-06-06)[2025-03-13]. https://www.jsjkk.com/CN/10.11896/jsjkk.230400022. | |
| [9] | ZHOU Yansen, XU Chuankai, CUI Jianquan. Face Recognition in Vivo Based on Temporal Optical Flow and Micro-Expression[J]. Computer Applications and Software, 2024, 41(12): 188-192. |
| 周延森, 徐传凯, 崔见泉. 基于时序光流与微表情的人脸活体识别[J]. 计算机应用与软件, 2024, 41(12):188-192. | |
| [10] | AGARWAL A. MagNet: Detecting Digital Presentation Attacks on Face Recognition[EB/OL]. (2021-12-08)[2025-03-13]. https://www.frontiersin.org/journals/artificial-intelligence/articles/10.3389/frai.2021.643424/full. |
| [11] | ZHU Xintong, TANG Yunqi, GENG Pengzhi. Detection Algorithm of Tamper and Deepfake Image Based on Feature Fusion[J]. Netinfo Security, 2021, 21(8): 70-81. |
| 朱新同, 唐云祁, 耿鹏志. 基于特征融合的篡改与深度伪造图像检测算法[J]. 信息网络安全, 2021, 21(8):70-81. | |
| [12] | XU Kaiwen, ZHOU Yichao, GU Wenquan, et al. A Multi-Scale Feature Fusion Deepfake Detection Algorithm Based on Reconstruction Learning[J]. Netinfo Security, 2024, 24(8): 1173-1183. |
| 许楷文, 周翊超, 谷文权, 等. 基于多尺度特征融合重建学习的深度伪造人脸检测算法[J]. 信息网络安全, 2024, 24(8):1173-1183. | |
| [13] | DEB D, LIU Xiaoming, JAIN A K. Unified Detection of Digital and Physical Face Attacks[C]// IEEE. 17th International Conference on Automatic Face and Gesture Recognition (FG). New York: IEEE, 2023: 1-8. |
| [14] |
YU Zitong, CAI Rizhao, LI Zhi, et al. Benchmarking Joint Face Spoofing and Forgery Detection with Visual and Physiological Cues[J]. IEEE Transactions on Dependable and Secure Computing, 2024, 21(5): 4327-4342.
doi: 10.1109/TDSC.2024.3352049 URL |
| [15] | FANG Hao, LIU Ajian, YUAN Haocheng, et al. Unified Physical-Digital Face Attack Detection[C]// IJCAI. The Thirty-Third International Joint Conference on Artificial Intelligence. San Francisco: Morgan Kaufmann, 2024: 749-757. |
| [16] | ZOU Hang, DU Chenxi, ZHANG Hui, et al. La-SoftMoE CLIP for Unified Physical-Digital Face Attack Detection[C]// IEEE. 2024 IEEE International Joint Conference on Biometrics (IJCB). New York: IEEE, 2024: 1-11. |
| [17] | CHEN Shunxin, LIU Ajian, ZHENG Junze, et al. Mixture-of-Attack-Experts with Class Regularization for Unified Physical-Digital Face Attack Detection[C]// AAAI. Proceedings of the AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2025: 2195-2203. |
| [18] | RADFORD A, KIM J W, HALLACY C, et al. Learning Transferable Visual Models from Natural Language Supervision[C]// IMLS. The 38th International Conference on Machine Learning. Massachusetts: PMLR, 2021: 8748-8763. |
| [19] | DAI Damai, DENG Chengqi, ZHAO Chenggang, et al. DeepSeekMoE: Towards Ultimate Expert Specialization in Mixture-of-Experts Language Models[C]// ACL. Proceedings of the 62nd Annual Meeting of the Association for Computational Linguistics. Stroudsburg: ACL, 2024: 1280-1297. |
| [20] | DIKO A. ReViT: Enhancing Vision Transformers Feature Diversity with Attention Residual Connections[EB/OL]. (2024-12-01)[2025-03-13]. https://www.sciencedirect.com/science/article/abs/pii/S0031320324006046. |
| [21] | HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep Residual Learning for Image Recognition[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2016: 770-778. |
| [22] | DOSOVITSKIY A. An Image is Worth 16x16 Words: Transformers for Image Recognition at Scale[EB/OL]. (2020-11-22)[2025-03-13]. https://arxiv.org/abs/2010.11929. |
| [23] | DANG Hao, LIU Feng, STEHOUWWER J, et al. On the Detection of Digital Face Manipulation[C]// IEEE. Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern recognition. New York: IEEE, 2020: 5781-5790. |
| [24] | YU Zitong, ZHAO Chenxu, WANG Zezheng, et al. Searching Central Difference Convolutional Networks for Face Anti-Spoofing[C]// IEEE. Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2020: 5295-5305. |
| [25] | LIU Yaojie, JOURABLOO A, LIU Xiaoming. Learning Deep Models for Face Anti-Spoofing: Binary or Auxiliary Supervision[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2018: 389-398. |
| [26] | CAI T T, MA Rong. Theoretical Foundations of T-SNE for Visualizing High-Dimensional Clustered Data[J]. Journal of Machine Learning Research, 2022, 23(301): 1-54. |
| [1] | 徐茹枝, 武晓欣, 吕畅冉. 基于Transformer的超分辨率网络对抗样本防御方法研究[J]. 信息网络安全, 2025, 25(9): 1367-1376. |
| [2] | 陈咏豪, 蔡满春, 张溢文, 彭舒凡, 姚利峰, 朱懿. 多尺度多层次特征融合的深度伪造人脸检测方法[J]. 信息网络安全, 2025, 25(9): 1456-1464. |
| [3] | 王新猛, 陈俊雹, 杨一涛, 李文瑾, 顾杜娟. 贝叶斯优化的DAE-MLP恶意流量识别模型[J]. 信息网络安全, 2025, 25(9): 1465-1472. |
| [4] | 李思聪, 王飞, 魏子令, 陈曙晖. 面向恶意代码检测的深度注意力网络架构[J]. 信息网络安全, 2025, 25(8): 1208-1222. |
| [5] | 金志刚, 李紫梦, 陈旭阳, 刘泽培. 面向数据不平衡的网络入侵检测系统研究综述[J]. 信息网络安全, 2025, 25(8): 1240-1253. |
| [6] | 王钢, 高雲鹏, 杨松儒, 孙立涛, 刘乃维. 基于深度学习的加密恶意流量检测方法研究综述[J]. 信息网络安全, 2025, 25(8): 1276-1301. |
| [7] | 张兴兰, 陶科锦. 基于高阶特征与重要通道的通用性扰动生成方法[J]. 信息网络安全, 2025, 25(5): 767-777. |
| [8] | 李元诚, 孙鹤洋, 张桐, 张贺方, 杨立群. 基于DACDiff的分布式电源调度控制系统FDIAs防御方法[J]. 信息网络安全, 2025, 25(4): 578-586. |
| [9] | 金增旺, 江令洋, 丁俊怡, 张慧翔, 赵波, 方鹏飞. 工业控制系统安全研究综述[J]. 信息网络安全, 2025, 25(3): 341-363. |
| [10] | 陈红松, 刘新蕊, 陶子美, 王志恒. 基于深度学习的时序数据异常检测研究综述[J]. 信息网络安全, 2025, 25(3): 364-391. |
| [11] | 李海龙, 崔治安, 沈燮阳. 网络流量特征的异常分析与检测方法综述[J]. 信息网络安全, 2025, 25(2): 194-214. |
| [12] | 武浩莹, 陈杰, 刘君. 改进Simon32/64和Simeck32/64神经网络差分区分器[J]. 信息网络安全, 2025, 25(2): 249-259. |
| [13] | 金地, 任昊, 唐瑞, 陈兴蜀, 王海舟. 基于情感辅助多任务学习的社交网络攻击性言论检测技术研究[J]. 信息网络安全, 2025, 25(2): 281-294. |
| [14] | 李古月, 张子豪, 毛承海, 吕锐. 基于累积量与深度学习融合的水下调制识别模型[J]. 信息网络安全, 2025, 25(10): 1554-1569. |
| [15] | 陈晓静, 陶杨, 吴柏祺, 刁云峰. 面向骨骼动作识别的优化梯度感知对抗攻击方法[J]. 信息网络安全, 2024, 24(9): 1386-1395. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||