信息网络安全 ›› 2025, Vol. 25 ›› Issue (9): 1456-1464.doi: 10.3969/j.issn.1671-1122.2025.09.013
多尺度多层次特征融合的深度伪造人脸检测方法
- 中国人民公安大学信息网络安全学院,北京 100038
-
收稿日期:2024-12-09出版日期:2025-09-10发布日期:2025-09-18 -
通讯作者:蔡满春caimanchun@ppsuc.edu.cn -
作者简介:陈咏豪(2000—),男,广东,硕士研究生, CCF会员,主要研究方向为网络安全、人工智能|蔡满春(1972—),男,河北,副教授,博士,主要研究方向为网络与通信保密、人工智能安全|张溢文(2000—),男,安徽,硕士研究生,主要研究方向为人工智能、网络安全|彭舒凡(1998—),男,江苏,博士研究生,主要研究方向为信息网络安全|姚利峰(1998—),男,山西,硕士研究生,主要研究方向为深度学习、流量分析和入侵检测|朱懿(2000—),男,上海,硕士研究生,主要研究方向为深度学习、流量分析 -
基金资助:国家重点研发计划(2018YFC23205);中国人民公安大学2022年度基本科研业务费项目(2022JKF02009)
A Multi-Scale and Multi-Level Feature Fusion Approach for Deepfake Face Detection
CHEN Yonghao, CAI Manchun( ), ZHANG Yiwen, PENG Shufan, YAO Lifeng, ZHU Yi
), ZHANG Yiwen, PENG Shufan, YAO Lifeng, ZHU Yi
- College of Information and Cyber Security, People’s Public Security University of China, Beijing 100038, China
-
Received:2024-12-09Online:2025-09-10Published:2025-09-18
摘要:
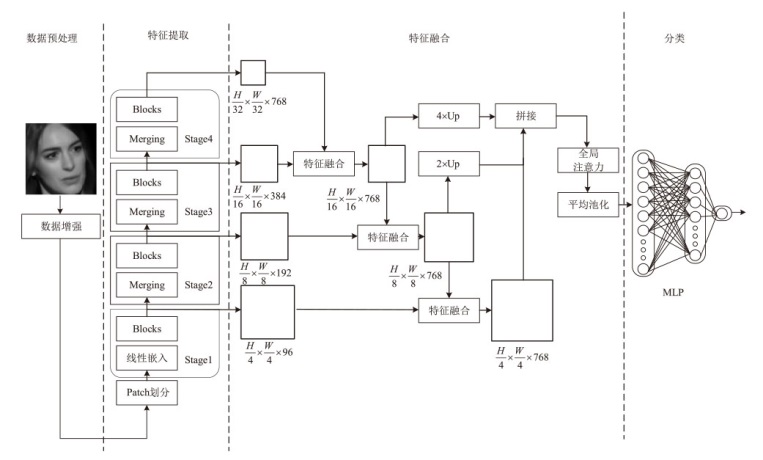
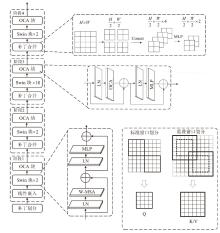
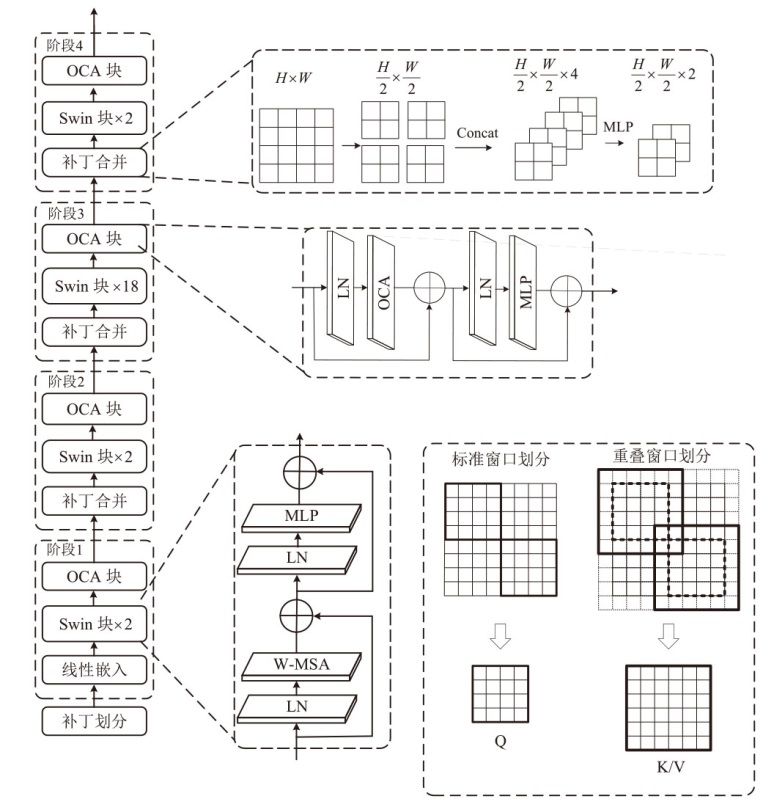
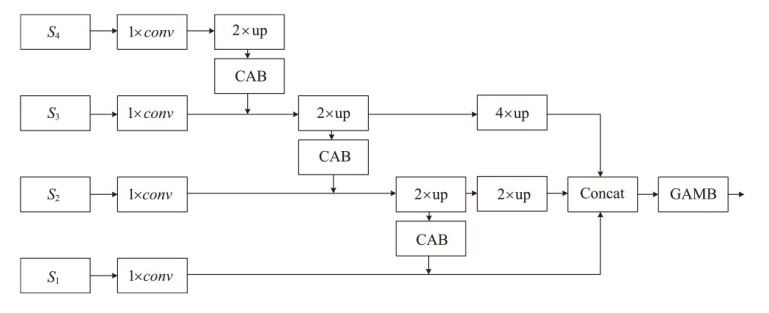
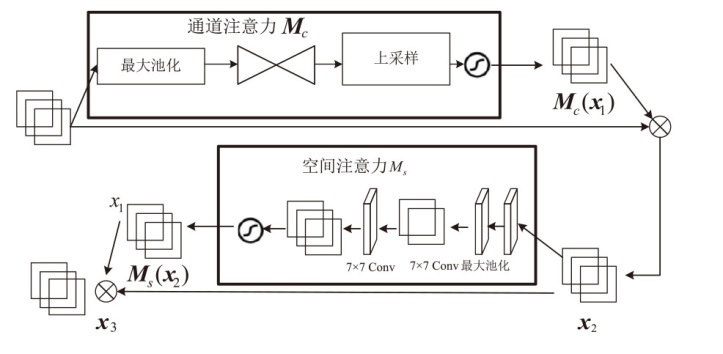
随着深度伪造技术的发展,现有伪造人脸特征呈现多尺度特点,且伪造特征会在不同层级特征中保留。然而,现有检测方案普遍未能充分利用这些特征。针对该问题,文章提出一种基于多尺度多层次特征融合的深度伪造人脸检测方法。首先,在滑动窗口变压器(Swin Transformer)中引入重叠窗口注意力单元,用于提取多尺度伪造特征;然后,设计了一种创新性的多尺度特征融合模块,该模块能够对不同层次提取的多尺度特征进行融合,从而获得表达能力更强、鲁棒性更优的多层次特征表示;最后,在FaceForensics++(FF++)和Celeb-DF(V2)数据集上验证了所提方法的有效性。
中图分类号:
引用本文
陈咏豪, 蔡满春, 张溢文, 彭舒凡, 姚利峰, 朱懿. 多尺度多层次特征融合的深度伪造人脸检测方法[J]. 信息网络安全, 2025, 25(9): 1456-1464.
CHEN Yonghao, CAI Manchun, ZHANG Yiwen, PENG Shufan, YAO Lifeng, ZHU Yi. A Multi-Scale and Multi-Level Feature Fusion Approach for Deepfake Face Detection[J]. Netinfo Security, 2025, 25(9): 1456-1464.
表2
域内实验
| 方法 | FF++ (C23) | Celeb-DF(V2) | Params/个 | 计算量/GFLOPs | ||
|---|---|---|---|---|---|---|
| ACC | AUC | ACC | AUC | |||
| MesoNet | 85.9% | 88.0% | — | — | — | — |
| Xception | 95.3% | 96.3% | — | 97.6% | 2.58×107 | 18.9 |
| ResNet | 93.2% | 95.4% | 96.9% | 98.6% | 4.46×107 | 23.6 |
| F3-Net | 97.5% | 98.1% | — | — | — | 67.3 |
| Cross Vit Net | 98.1% | 98.6% | 98.4% | 99.0% | 1.01×108 | — |
| M2TR | 97.9% | 99.5% | 98.3% | 99.4% | — | — |
| 本文方法 | 98.8% | 99.7% | 99.3% | 99.4% | 7.13×107 | 38.4 |
| [1] | NGUYEN T T, NGUYEN Q V H, NGUYEN D T, et al. Deep Learning for Deepfakes Creation and Detection: A Survey[EB/OL]. (2022-08-11)[2024-09-12]. https://arxiv.org/abs/1909.11573. |
| [2] | CHESNEY B, CITRON D. Deep Fakes: A Looming Challenge for Privacy, Democracy, and National Security[J]. California Law Review, 2019, 107: 1753-1820. |
| [3] | LI Xurong, JI Shouling, WU Chunming, et al. A Survey on Deepfakes and Detection Techniques[J]. Journal of Software, 2020, 32(2): 496-518. |
| 李旭嵘, 纪守领, 吴春明, 等. 深度伪造与检测技术综述[J]. 软件学报, 2020, 32(2): 496-518. | |
| [4] | TOLOSANA R, VERA-RODRIGUEZ R, FIERREZ J, et al. Deepfakes and Beyond: A Survey of Face Manipulation and Fake Detection[J]. Information Fusion, 2020, 64: 131-148. |
| [5] | GUO Cuicui, LUO Guibo, ZHU Yuesheng. A Detection Method for Facial Expression Reenacted Forgery in Videos[C]// SPIE. Tenth International Conference on Digital Image Processing (ICDIP 2018). San Diego: SPIE, 2018: 414-422. |
| [6] | KOOPMAN M, RODRIGUEZ A M, GERADTS Z. Detection of Deepfake Video Manipulation[C]// IAPR. The 20th Irish Machine Vision and Image Processing Conference (IMVIP). Heidelberg: Springer, 2018: 133-136. |
| [7] | MCClOSKEY S, ALBRIGHT M. Detecting GAN-Generated Imagery Using Saturation Cues[C]// IEEE. 2019 IEEE International Conference on Image Processing (ICIP). New York: IEEE, 2019: 4584-4588. |
| [8] | BOHAEK M, FARID H. Protecting World Leaders against Deep Fakes Using Facial, Gestural, and Vocal Mannerisms[EB/OL]. (2022-07-20)[2024-11-12]. https://www.nstl.gov.cn/paper_detail.html?id=1e2166894a6601a5f4ae6d8e93d36a18. |
| [9] | LI Yuezun, CHANG M, LYU Siwei. In Ictu Oculi: Exposing AI Created Fake Videos by Detecting Eye Blinking[C]// IEEE. 2018 IEEE International Workshop on Information Forensics and Security (WIFS). New York: IEEE, 2018: 1-7. |
| [10] | MATERN F, RIESS C, STAMMINGER M. Exploiting Visual Artifacts to Expose Deepfakes and Face Manipulations[C]// IEEE. 2019 IEEE Winter Applications of Computer Vision Workshops (WACVW). New York: IEEE, 2019: 83-92. |
| [11] | YANG Xin, LI Yuezun, LYU Siwei. Exposing Deep Fakes Using Inconsistent Head Poses[C]// IEEE. 2019 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP). New York: IEEE, 2019: 8261-8265. |
| [12] | SUN Zekun, HAN Yujie, HUA Zeyu, et al. Improving the Efficiency and Robustness of Deepfakes Detection through Precise Geometric Features[C]// IEEE. The IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2021: 3609-3618. |
| [13] | PENG Shufan, CAI Manchun, MA Rui, et al. Deepfake Detection Algorithm for High-Frequency Components of Shallow Features[J]. Laser & Optoelectronics Progress, 2023, 60(10): 1-11. |
| 彭舒凡, 蔡满春, 马瑞, 等. 面向浅层特征高频分量的深度伪造检测算法[J]. 激光与光电子进展, 2023, 60(10): 1-11. | |
| [14] | ZHAO Hanqing, ZHOU Wenbo, CHEN Dongdong, et al. Multi-Attentional Deepfake Detection[C]// IEEE. The IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2021: 2185-2194. |
| [15] | YANG Shaocong, WANG Jian, SUN Yunlian, et al. Multi-Level Features Global Consistency for Human Facial Deepfake Detection[J]. Journal of Image and Graphics, 2022, 27(9): 2708-2720. |
| 杨少聪, 王健, 孙运莲, 等. 多级特征全局一致性的伪造人脸检测[J]. 中国图象图形学报, 2022, 27(9): 2708-2720. | |
| [16] | AFCHAR D, NOZICK V, YAMAGISHI J, et al. Mesonet: A Compact Facial Video Forgery Detection Network[C]// IEEE. 2018 IEEE International Workshop on Information Forensics and Security (WIFS). New York: IEEE, 2018: 1-7. |
| [17] | NGUYEN H H, YAMAGISHI J, ECHIZEN I. Use of a Capsule Network to Detect Fake Images and Videos[EB/OL]. (2019-09-19)[2024-09-12]. https://arxiv.org/abs/1910.12467. |
| [18] | AMERINI I, GALTERI L, CALDELLI R, et al. Deepfake Video Detection through Optical Flow Based Cnn[C]// IEEE. The IEEE/CVF International Conference on Computer Vision Workshops. New York: IEEE, 2019: 1-10. |
| [19] | SABIR E, CHENG Jiaxin, JAISWAL A, et al. Recurrent Convolutional Strategies for Face Manipulation Detection in Videos[J]. Interfaces (GUI), 2019, 3(1): 80-87. |
| [20] | MI Zhongjie, JIANG Xinghao, SUN Tanfeng, et al. GAN-Generated Image Detection with Self-Attention Mechanism against GAN Generator Defect[J]. IEEE Journal of Selected Topics in Signal Processing, 2020, 14(5): 969-981. |
| [21] | GOODFELLOW I, POUGET-ABADIE J, MIRZA M, et al. Generative Adversarial Nets[C]// NIPS.Proceedings of the 27th International Conference on Neural Information Processing Systems. Cambridge: MIT Press, 2014: 2672-2680. |
| [22] | DOSOVITSKIY A, BEYER L, KOLESNIKOV A, et al. An Image Is Worth 16x16 Words: Transformers for Image Recognition at Scale[EB/OL]. (2010-11-29)[2024-09-12]. https://arxiv.org/pdf/2010.11929/1000. |
| [23] | WODAJO D, EMIRE S A. Haricot Beans Flour: Effect of Varieties and Processing Methods to Favor the Utilization of Underconsumed Common Beans[J]. International Journal of Food Properties, 2022, 25(1): 1186-1202. |
| [24] | DOLHANSKY B, BITTON J, PFLAUM B, et al. The Deepfake Detection Challenge (DFDC) Dataset[EB/OL]. (2020-10-28)[2024-09-12]. https://arxiv.org/abs/2006.07397. |
| [25] | COCCOMINI D A, MESSINA N, GENNARO C, et al. Combining Efficientnet and Vision Transformers for Video Deepfake Detection[C]// Springer. Image Analysis and Processing-ICIAP 2022: 21st International Conference. Heidelberg: Springer, 2022: 219-229. |
| [26] | CHEN Xiangyu, WANG Xintao, ZHOU Jiantao, et al. Activating More Pixels in Image Super-Resolution Transformer[C]// IEEE. The IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2023: 22367-22377. |
| [27] | LIU Ze, LIN Yutong, CAO Yue, et al. Swin Transformer: Hierarchical Vision Transformer Using Shifted Windows[C]// IEEE. The IEEE/CVF International Conference on Computer Vision. New York: IEEE, 2021: 10012-10022. |
| [28] | ZHANG Kaipeng, ZHANG Zhanpeng, LI Zhifeng, et al. Joint Face Detection and Alignment Using Multitask Cascaded Convolutional Networks[J]. IEEE Signal Processing Letters, 2016, 23(10): 1499-1503. |
| [29] | LIU Yichao, SHAO Zongru, HOFFMANN N. Global Attention Mechanism: Retain Information to Enhance Channel-Spatial Interactions[EB/OL]. (2021-06-21)[2024-09-12]. https://arxiv.org/abs/2112.05561. |
| [30] | ROSSLER A, COZZOLINO D, VERDOLIVA L, et al. Faceforensics++: Learning to Detect Manipulated Facial Images[C]// IEEE. The IEEE/CVF International Conference on Computer Vision. New York: IEEE, 2019: 1-11. |
| [31] | LI Yuezun, YANG Xin, SUN Pu, et al. Celeb-Df: A Large-Scale Challenging Dataset for Deepfake Forensics[C]// IEEE. The IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2020: 3207-3216. |
| [32] | HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep Residual Learning for Image Recognition[EB/OL]. (2016-08-16)[2024-09-12]. https://arxiv.org/abs/1512.03385. |
| [33] | WANG Junke, WU Zuxuan, OUYANG Wenhao, et al. M2tr: Multi-Modal Multi-Scale Transformers for Deepfake Detection[C]// ACM. The 2022 International Conference on Multimedia Retrieval. New York: ACM, 2022: 615-623. |
| [34] | QIAN Yuyang, YIN Guojun, SHENG Lu, et al. Thinking in Frequency: Face Forgery Detection by Mining Frequency-Aware Clues[C]// Springer. Computer Vision-ECCV 2020: 16th European Conference. Heidelberg: Springer, 2020: 86-103. |
| [1] | 徐茹枝, 武晓欣, 吕畅冉. 基于Transformer的超分辨率网络对抗样本防御方法研究[J]. 信息网络安全, 2025, 25(9): 1367-1376. |
| [2] | 王新猛, 陈俊雹, 杨一涛, 李文瑾, 顾杜娟. 贝叶斯优化的DAE-MLP恶意流量识别模型[J]. 信息网络安全, 2025, 25(9): 1465-1472. |
| [3] | 金志刚, 李紫梦, 陈旭阳, 刘泽培. 面向数据不平衡的网络入侵检测系统研究综述[J]. 信息网络安全, 2025, 25(8): 1240-1253. |
| [4] | 王钢, 高雲鹏, 杨松儒, 孙立涛, 刘乃维. 基于深度学习的加密恶意流量检测方法研究综述[J]. 信息网络安全, 2025, 25(8): 1276-1301. |
| [5] | 张兴兰, 陶科锦. 基于高阶特征与重要通道的通用性扰动生成方法[J]. 信息网络安全, 2025, 25(5): 767-777. |
| [6] | 金增旺, 江令洋, 丁俊怡, 张慧翔, 赵波, 方鹏飞. 工业控制系统安全研究综述[J]. 信息网络安全, 2025, 25(3): 341-363. |
| [7] | 陈红松, 刘新蕊, 陶子美, 王志恒. 基于深度学习的时序数据异常检测研究综述[J]. 信息网络安全, 2025, 25(3): 364-391. |
| [8] | 李海龙, 崔治安, 沈燮阳. 网络流量特征的异常分析与检测方法综述[J]. 信息网络安全, 2025, 25(2): 194-214. |
| [9] | 武浩莹, 陈杰, 刘君. 改进Simon32/64和Simeck32/64神经网络差分区分器[J]. 信息网络安全, 2025, 25(2): 249-259. |
| [10] | 金地, 任昊, 唐瑞, 陈兴蜀, 王海舟. 基于情感辅助多任务学习的社交网络攻击性言论检测技术研究[J]. 信息网络安全, 2025, 25(2): 281-294. |
| [11] | 陈晓静, 陶杨, 吴柏祺, 刁云峰. 面向骨骼动作识别的优化梯度感知对抗攻击方法[J]. 信息网络安全, 2024, 24(9): 1386-1395. |
| [12] | 许楷文, 周翊超, 谷文权, 陈晨, 胡晰远. 基于多尺度特征融合重建学习的深度伪造人脸检测算法[J]. 信息网络安全, 2024, 24(8): 1173-1183. |
| [13] | 徐茹枝, 张凝, 李敏, 李梓轩. 针对恶意软件的高鲁棒性检测模型研究[J]. 信息网络安全, 2024, 24(8): 1184-1195. |
| [14] | 田钊, 牛亚杰, 佘维, 刘炜. 面向车联网的车辆节点信誉评估方法[J]. 信息网络安全, 2024, 24(5): 719-731. |
| [15] | 张光华, 刘亦纯, 王鹤, 胡勃宁. 基于JSMA对抗攻击的去除深度神经网络后门防御方案[J]. 信息网络安全, 2024, 24(4): 545-554. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||