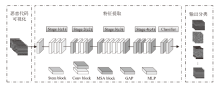
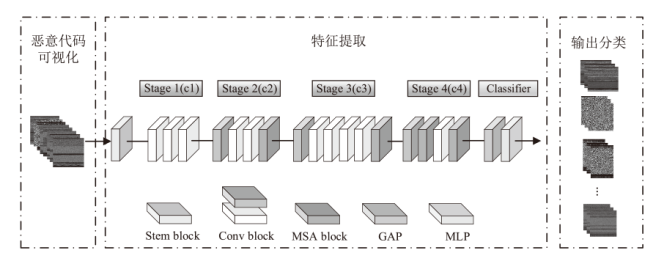
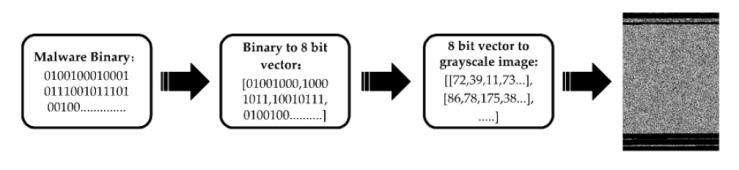
信息网络安全 ›› 2025, Vol. 25 ›› Issue (8): 1208-1222.doi: 10.3969/j.issn.1671-1122.2025.08.003
面向恶意代码检测的深度注意力网络架构
- 国防科技大学计算机学院,长沙 410073
-
收稿日期:2025-06-09出版日期:2025-08-10发布日期:2025-09-09 -
通讯作者:王飞 E-mail:wangfei09a@nudt.edu.cn -
作者简介:李思聪(2000—),女,陕西,博士研究生,主要研究方向为异常检测、开放环境下的机器学习|王飞(1984—),女,吉林,副教授,博士,主要研究方向为机器学习、网络流量异常检测|魏子令(1992—),男,湖南,副教授,博士,CCF会员,主要研究方向为网络取证和网络优化|陈曙晖(1975—),男,湖南,教授,博士,CCF会员,主要研究方向为网络取证和网络流量处理 -
基金资助:国家自然科学基金(62202486);国家自然科学基金(U22B2005);江苏省重点研发计划(BE2023004-4);湖南省科技创新计划(2024RC3139)
Deep Attention Network Architecture for Malicious Code Detection
LI Sicong, WANG Fei( ), WEI Ziling, CHEN Shuhui
), WEI Ziling, CHEN Shuhui
- College of Computer Science, National University of Defense Technology, Changsha 410073, China
-
Received:2025-06-09Online:2025-08-10Published:2025-09-09
摘要:
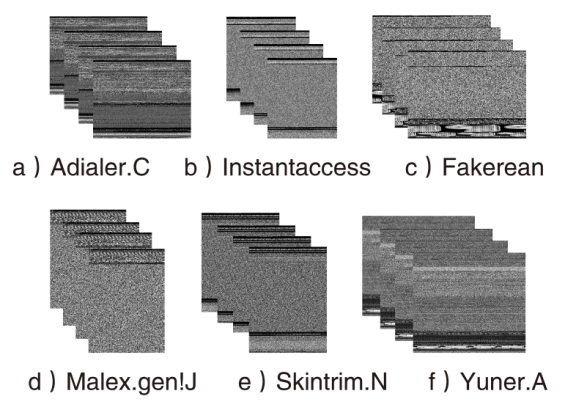
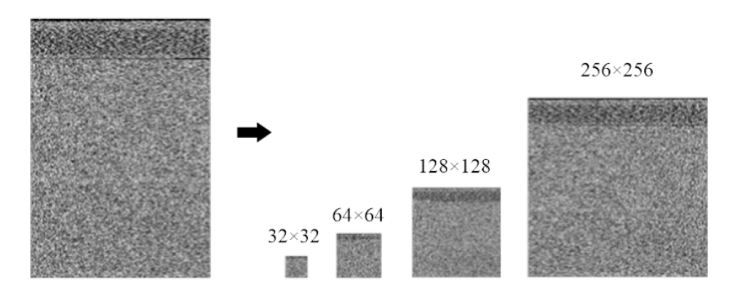
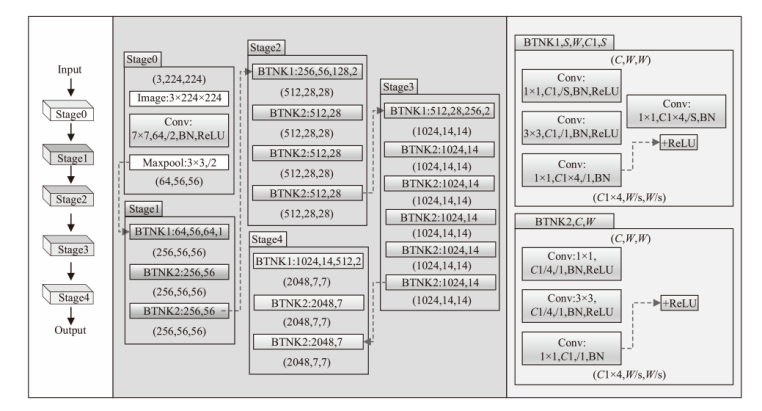
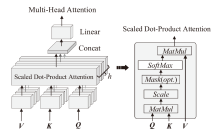
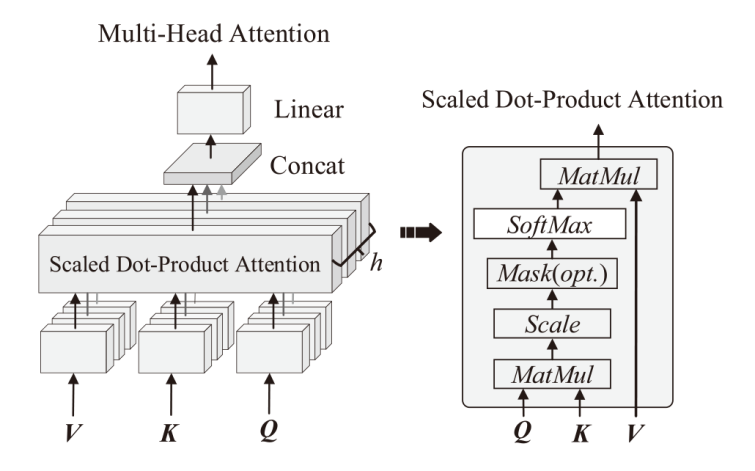
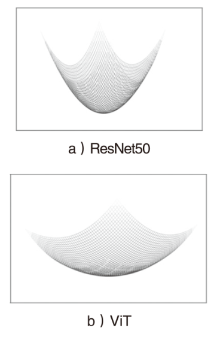
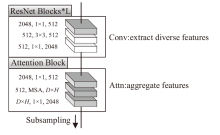
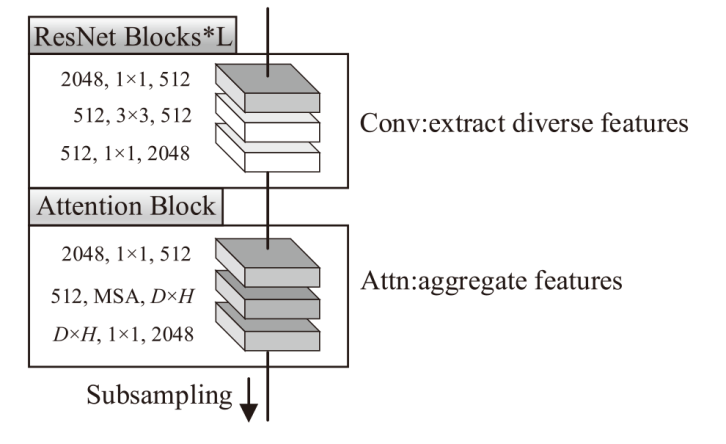
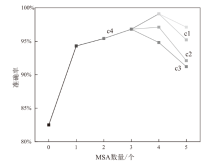
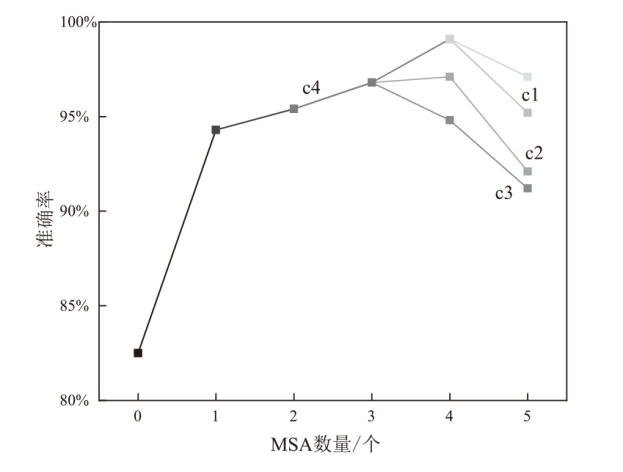
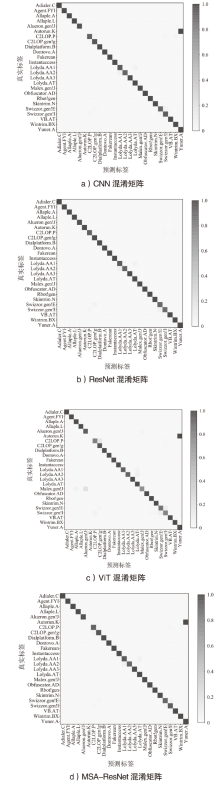
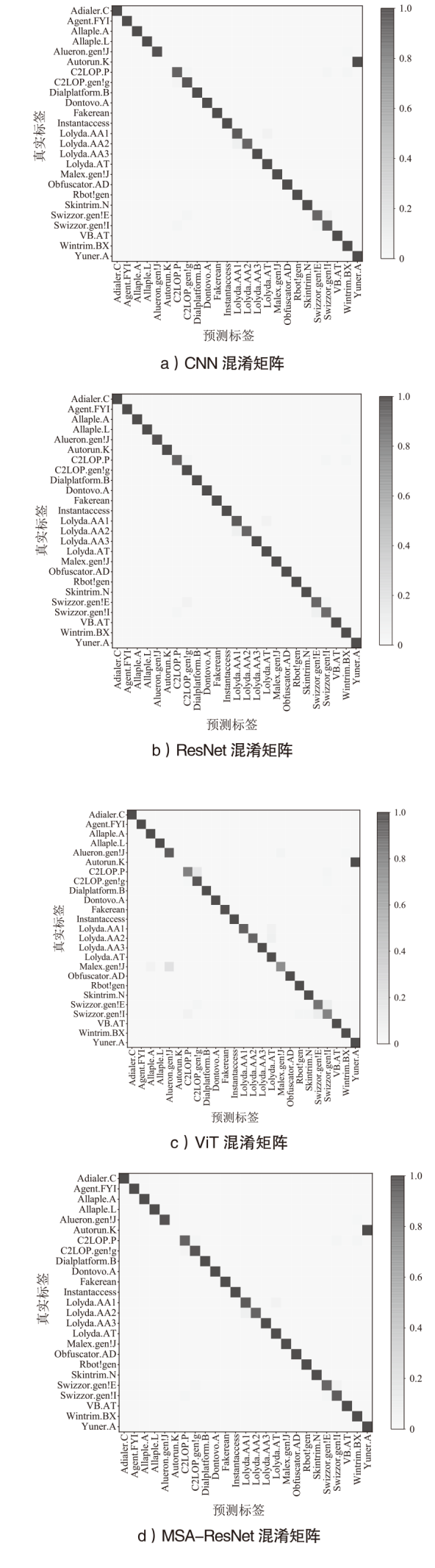
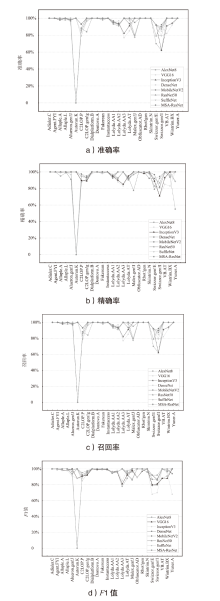
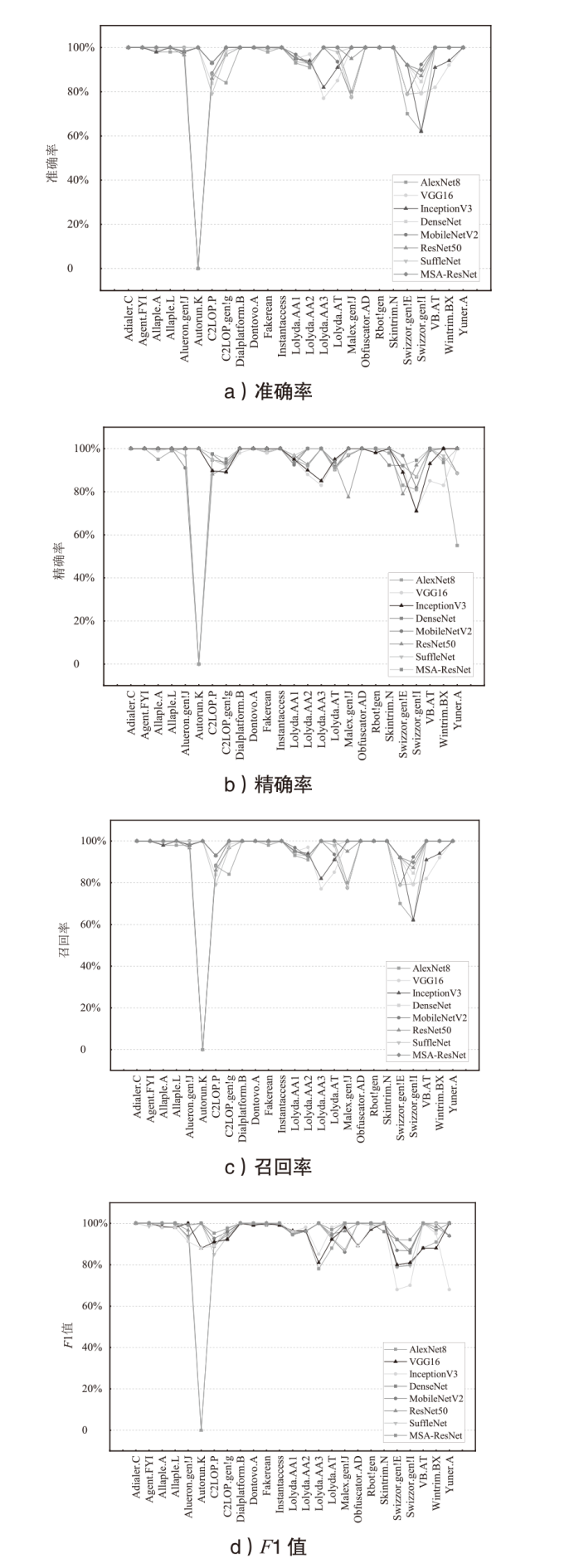
针对恶意代码变种激增导致传统检测方法效能不足的问题,文章提出一种基于混合多尺度注意力网络的恶意代码分类架构MSA-ResNet。该架构通过双线性插值算法实现图像尺寸标准化,有效保留易混淆恶意代码家族的纹理特征,并结合动态数据增强策略优化输入多样性。在网络架构中,将多尺度注意力模块嵌入ResNet50残差块末端,构建跨尺度特征交互机制,使特征点关联距离缩短,注意力收敛速度提升。实验结果表明,架构在Malimg数据集上实现99.47%的准确率与99.46%的宏平均F1分数,较传统ResNet50架构提升1.95%,参数量仅增加15%。与现有最优方法相比,分类精度提升0.49%,且对Obfuscator.AD等复杂恶意代码变种检测有效。
中图分类号:
引用本文
李思聪, 王飞, 魏子令, 陈曙晖. 面向恶意代码检测的深度注意力网络架构[J]. 信息网络安全, 2025, 25(8): 1208-1222.
LI Sicong, WANG Fei, WEI Ziling, CHEN Shuhui. Deep Attention Network Architecture for Malicious Code Detection[J]. Netinfo Security, 2025, 25(8): 1208-1222.
表2
Malimg数据集样本分布
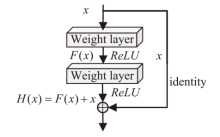
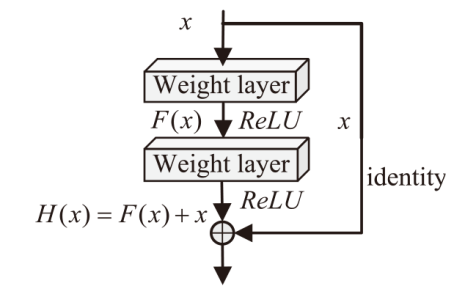
| 家族名称 | 标签编号 | 样本数/个 | 类型 |
|---|---|---|---|
| Allaple.A Allaple.L VB.AT Yuner.A | 3 | 2824 | Worm |
| 4 | 1491 | ||
| 23 | 383 | ||
| 25 | 775 | ||
| Autorun.K | 6 | 81 | Worm: AutoIT |
| Alueron.gen!J C2LOP.gen!g C2LOP.P Malex.gen!J Skintrim.N | 5 | 173 | Trojan |
| 7 | 175 | ||
| 8 | 121 | ||
| 17 | 111 | ||
| 20 | 55 | ||
| Adialer.C Dialplatform.B Instantaccess | 1 | 97 | Dialer |
| 9 | 152 | ||
| 12 | 356 | ||
| Lolyda.AA1 Lolyda.AA2 Lolyda.AA3 Lolyda.AT | 13 | 153 | PWS |
| 14 | 159 | ||
| 15 | 98 | ||
| 16 | 134 | ||
| Dontovo.A Obfuscator.AD Swizzor.gen!E Swizzor.gen!I Wintrim.BX | 10 | 137 | Trojan Downloader |
| 18 | 117 | ||
| 21 | 103 | ||
| 22 | 107 | ||
| 24 | 72 | ||
| Fakerean | 11 | 306 | Rogue |
| Agent.FYI | 2 | 91 | Backdoor |
| Rbot!gen | 19 | 133 |
表8
不同模型的实验结果
| 模型 | 准确率 | 精确率 | 召回率 | F1值 |
|---|---|---|---|---|
| AlexNet8 | 94.12% | 92.77% | 94.12% | 93.19% |
| VGG16 | 97.11% | 97.00% | 97.11% | 97.03% |
| DenseNet | 99.07% | 99.08% | 99.07% | 99.06% |
| MobileNetV2 | 97.63% | 96.72% | 97.63% | 97.10% |
| ResNet50 | 97.92% | 97.54% | 97.92% | 97.40% |
| ShuffleNet | 98.35% | 98.41% | 98.35% | 98.33% |
| InceptionV3 | 98.71% | 98.72% | 98.71% | 98.71% |
| MSA-ResNet | 99.47% | 99.49% | 99.47% | 99.46% |
表9
各恶意代码分类方法的性能指标
| 方法 | 数据集 | 模型概述 | 准确率 | 精确率 | 召回率 | F1值 |
|---|---|---|---|---|---|---|
| 文献[ | Malimg | GIST+KNN | 97.18% | — | — | — |
| 文献[ | Malimg | SPAM | 97.40% | — | — | — |
| 文献[ | Malimg | DRBA+CNN | 94.50% | 96.60% | 88.40% | — |
| 文献[ | Malimg | LGMP+KNN | 98.40% | — | 98.20% | 97.1% |
| 文献[ | Malimg | NSGAII+CNN | 97.60% | 97.60% | 88.40% | — |
| 文献[ | Malimg | CNN+LSTM | 96.30% | 96.30% | 96.20% | 96.20% |
| 文献[ | Malimg | CNN+BiGRU | 96.30% | 91.80% | 91.50% | 91.60% |
| 文献[ | Malimg | CSGM+KNN | 98.40% | — | 98.20% | 97.10% |
| 文献[ | Malimg | MxN+GLCM | 98.58% | 98.04% | 98.06% | 98.05% |
| 文献[ | Malimg | SWS+RF | 98.65% | 98.86% | 98.63% | 98.74% |
| 文献[ | Malimg | DCNN | 98.79% | 98.79% | 98.47% | 98.46% |
| 文献[ | Malimg | IMCFN | 98.82% | 98.85% | 98.81% | 98.75% |
| 文献[ | Malimg | DenseNet201 | 98.97% | — | — | 98.88% |
| 文献[ | Malimg | DEAM+Densenet | 98.50% | 96.90% | 96.60% | 96.70% |
| 文献[ | Malimg | Two-level ANN | 99.13% | — | — | — |
| 文献[ | Malimg | MCFT-CNN | 99.19% | 97.72% | 97.76% | 97.68% |
| 文献[ | Malimg | DTMIC | 98.93% | 99.00% | 99.00% | 99.00% |
| 本文方法 | Malimg | MSA-ResNet | 99.47% | 99.49% | 99.47% | 99.46% |
| 文献[ | BIG2015 | CNN+Gray | 97.49% | — | — | 94.38% |
| 文献[ | BIG2015 | CNN+LSTM+Gray | 98.20% | — | — | 95.77% |
| 文献[ | BIG2015 | LeNet5+RGB+ Word2Vec | 98.76% | — | — | — |
| 文献[ | BIG2015 | RNN+Word2Vec+ skip-gram | 97.80% | — | — | — |
| 文献[ | BIG2015 | CFG+LSTM | 87.80% | — | — | 84.20% |
| 文献[ | BIG2015 | CFG+Graph+ transformer | 92.70% | — | — | 90.10% |
| 文献[ | BIG2015 | One-class SVM | 92.00% | — | — | — |
| 文献[ | BIG2015 | PCA+KNN | 96.60% | — | — | — |
| 文献[ | BIG2015 | Mcs-ResNet | 97.21% | — | — | — |
| 本文方法 | BIG2015 | MSA-ResNet | 99.36% | 99.29% | 99.35% | 99.32% |
| [1] | China Internet Network Information Centre. The 55th Statistical Report on the Development of the Internet in China[EB/OL]. (2025-01-17)[2025-04-15]. https://www.cnnic.net.cn/. |
| 中国互联网络信息中心. 第55次《中国互联网络发展状况统计报告》[EB/OL]. (2025-01-17)[2025-04-15]. https://www.cnnic.net.cn/. | |
| [2] | National Computer Network Emergency Response Technical Team/Coordination Center of China (CNCERT/CC). 2021 First Half Year China Internet Network Security Monitoring Data Analysis Report[EB/OL]. (2021-06-30)[2025-04-15]. https://www.cert.org.cn/. |
| 国家计算机网络应急技术处理协调中心(CNCERT/CC). 2021年上半年我国互联网网络安全监测数据分析报告[EB/OL]. (2021-06-30)[2025-04-15]. https://www.cert.org.cn/. | |
| [3] | DAMODARAN A, TROIA F D, VISAGGIO C A, et al. A Comparison of Static, Dynamic, and Hybrid Analysis for Malware Detection[J]. Journal of Computer Virology and Hacking Techniques, 2017, 13: 1-12. |
| [4] | ALAZAB M. Profiling and Classifying the Behavior of Malicious Codes[J]. Journal of Systems and Software, 2015, 100: 91-102. |
| [5] |
WANG Shuo, WANG Jian, WANG Ya'nan, et al. A Fast Malicious Code Detection Method Based on Feature Fusion[J]. Acta Electronica Sinica, 2023, 51(1): 57-66.
doi: 10.12263/DZXB.20211701 |
|
王硕, 王坚, 王亚男, 等. 一种基于特征融合的恶意代码快速检测方法[J]. 电子学报, 2023, 51(1):57-66.
doi: 10.12263/DZXB.20211701 |
|
| [6] | CONTI G, BRATUS S, SHUBINA A, et al. Automated Mapping of Large Binary Objects Using Primitive Fragment Type Classification[J]. Digital Investigation, 2010, 7: 3-12. |
| [7] | NATARAJ L, KARTHIKEYAN S, JACOB G, et al. Malware Images: Visualization and Automatic Classification[C]// ACM. The 8th International Symposium on Visualization for Cyber Security. New York: ACM, 2011: 1-7. |
| [8] |
HAN Xiaoguang, QU Wu, YAO Xuanxia, et al. Research on Malicious Code Variants Detection Based on Texture Fingerprint[J]. Journal on Communications, 2014, 35(8): 125-136.
doi: 10.3969/j.issn.1000-436x.2014.08.016 |
|
韩晓光, 曲武, 姚宣霞, 等. 基于纹理指纹的恶意代码变种检测方法研究[J]. 通信学报, 2014, 35(8):125-136.
doi: 10.3969/j.issn.1000-436x.2014.08.016 |
|
| [9] | NATARAJ L, YEGNESWARAN V, PORRAS P, et al. A Comparative Assessment of Malware Classification Using Binary Texture Analysis and Dynamic Analysis[C]// ACM. The 4th ACM Workshop on Security and Artificial Intelligence. New York: ACM, 2011: 21-30. |
| [10] | WANG Jialai, ZHANG Chao, QI Xuyan, et al. A Survey of Intelligent Malware Detection on Windows Platform[J]. Journal of Computer Research and Development, 2021, 58(5): 977-994. |
| 汪嘉来, 张超, 戚旭衍, 等. Window平台恶意软件智能检测综述[J]. 计算机研究与发展, 2021, 58(5):977-994. | |
| [11] |
REN Zhuojun, CHEN Guang, LU Wenke. Malware Visualization Methods Based on N-Gram Features[J]. Acta Electronica Sinica, 2019, 47(10): 2108-2115.
doi: 10.3969/j.issn.0372-2112.2019.10.012 |
|
任卓君, 陈光, 卢文科. 基于N-gram特征的恶意代码可视化方法[J]. 电子学报, 2019, 47(10):2108-2115.
doi: 10.3969/j.issn.0372-2112.2019.10.012 |
|
| [12] |
NATARAJ L, MANJUNATH B S. SPAM: Signal Processing to Analyze Malware[J]. IEEE Signal Processing Magazine, 2016, 33(2): 105-117.
doi: 10.1109/MSP.2015.2507185 |
| [13] | KANCHERLA K, MUKKAMALA S. Image Visualization Based Malware Detection[C]// IEEE. 2013 IEEE Symposium on Computational Intelligence in Cyber Security. New York: IEEE, 2013: 40-44. |
| [14] |
LIU Yashu, WANG Zhihai, YAN Hanbing, et al. Method of Anti-Confusion Texture Feature Descriptor for Malware Images[J]. Journal on Communications, 2018, 39(11): 44-53.
doi: 10.11959/j.issn.1000-436x.2018227 |
|
刘亚姝, 王志海, 严寒冰, 等. 抗混淆的恶意代码图像纹理特征描述方法[J]. 通信学报, 2018, 39(11):44-53.
doi: 10.11959/j.issn.1000-436x.2018227 |
|
| [15] | NAEEM H, GUO Bing, NAEEM M R, et al. Identification of Malicious Code Variants Based on Image Visualization[J]. Computers & Electrical Engineering, 2019, 76: 225-237. |
| [16] | LU Xidong, DUAN Zhemin, QIAN Yekui, et al. Malicious Code Classification Method Based on Deep Forest[J]. Journal of Software, 2020, 31(5): 1454-1464. |
| 卢喜东, 段哲民, 钱叶魁, 等. 一种基于深度森林的恶意代码分类方法[J]. 软件学报, 2020, 31(5):1454-1464. | |
| [17] | GIBERT D, MATEU C, PLANES J, et al. Using Convolutional Neural Networks for Classification of Malware Represented as Images[J]. Journal of Computer Virology and Hacking Techniques, 2019, 15(1): 15-28. |
| [18] | VASAN D, ALAZAB M, WASSAN S, et al. IMCFN: Image-Based Malware Classification Using Fine-Tuned Convolutional Neural Network Architecture[EB/OL]. (2025-01-17)[2025-04-15].https://www.cnnic.net.cn/. |
| [19] | KABANGA E K, KIM C H. Malware Images Classification Using Convolutional Neural Network[J]. Journal of Computer and Communications, 2018, 6(1): 153-158. |
| [20] | CUI Zhihua, XUE Fei, CAI Xingjuan, et al. Detection of Malicious Code Variants Based on Deep Learning[J]. IEEE Transactions on Industrial Informatics, 2018, 14(7): 3187-3196. |
| [21] |
CUI Zhihua, DU Lei, WANG Penghong, et al. Malicious Code Detection Based on CNNs and Multi-Objective Algorithm[J]. Journal of Parallel and Distributed Computing, 2019, 129: 50-58.
doi: 10.1016/j.jpdc.2019.03.010 |
| [22] | HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep Residual Learning for Image Recognition[C]// IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2016: 770-778. |
| [23] | ZHANG Chenjia, ZHU Lei, CHEN Pu, et al. Individual Recognition Method of Communication Emitter Based on Attention Mechanism[J]. Communications Technology, 2021, 54(7): 1594-1600. |
| 张宸嘉, 朱磊, 陈璞, 等. 基于注意力机制的通信辐射源个体识别方法[J]. 通信技术, 2021, 54(7):1594-1600. | |
| [24] | ZHOU Chenchao, CHEN Qun, LI Zhanhuai, et al. Evaluation Object Category Determination Based on Attention and Two-Way LSTM[J]. Journal of Northwestern Polytechnical University, 2019, 37 (3): 558-564. |
| 周陈超, 陈群, 李战怀, 等. 基于注意力和双向LSTM的评价对象类别判定[J]. 西北工业大学学报, 2019, 37(3):558-564. | |
| [25] | VASWANI A, SHAZEER N, PARMAR N, et al. Attention All You Need[C]// Neural Information Processing Systems. The 31st International Conference on Neural Information Processing Systems. New York: Curran Associates, 2017: 6000-6010. |
| [26] | RONEN R, RADU M, FEUERSTEIN C, et al. Microsoft Malware Classification Challenge[EB/OL]. (2018-02-22)[2025-04-15]. https://arxiv.org/abs/1802.10135. |
| [27] |
LI Qi, MI Jiaxin, LI Weishi, et al. CNN-Based Malware Variants Detection Method for Internet of Things[J]. IEEE Internet of Things Journal, 2021, 8(23): 16946-16962.
doi: 10.1109/JIOT.2021.3075694 |
| [28] | SUDHAKAR S K. MCFT-CNN: Malware Classification with Fine-Tuning Convolution Neural Networks Using Traditional and Transfer Learning in the Internet of Things[J]. Future Generation Computer Systems, 2021, 125: 334-351. |
| [29] |
VINAYAKUMAR R, ALAZAB M, SOMAN K P, et al. Robust Intelligent Malware Detection Using Deep Learning[J]. IEEE Access, 2019, 7: 46717-46738.
doi: 10.1109/ACCESS.2019.2906934 |
| [30] | VENKATRAMAN S, ALAZAB M, VINAYAKUMAR R. A Hybrid Deep Learning Image-Based Analysis for Effective Malware Detection[J]. Journal of Information Security and Applications, 2019, 47: 377-389. |
| [31] | NAEEM H, GUO Bing, ULLAH F, et al. A Cross-Platform Malware Variant Classification Based on Image Representation[J]. KSII Transactions on Internet and Information Systems, 2019, 13(7): 3756-3777. |
| [32] | VERMA V, MUTTOO S K, SINGH V B. Multiclass Malware Classification via First- and Second-Order Texture Statistics[EB/OL]. (2020-10-01)[2025-04-15]. https://doi.org/10.1016/j.cose.2020.101895. |
| [33] | ROSELINE S A, GEETHA S, KADRY S, et al. Intelligent Vision-Based Malware Detection and Classification Using Deep Random Forest Paradigm[J]. IEEE Access, 2020, 8: 206303-206324. |
| [34] | NAEEM H, ULLAH F, NAEEM M R, et al. Malware Detection in Industrial Internet of Things Based on Hybrid Image Visualization and Deep Learning Model[EB/OL]. (2020-08-01)[2025-04-15]. https://doi.org/10.1016/j.adhoc.2020.102154. |
| [35] | ANANDH V, VINOD P, MENON V G. Malware Visualization and Detection Using DenseNets[J]. Personal and Ubiquitous Computing, 2021, 28: 153-169. |
| [36] | WANG Changguang, ZHAO Ziqiu, WANG Fangwei, et al. A Novel Malware Detection and Family Classification Scheme for IoT Based on DEAM and DenseNet[EB/OL]. (2021-01-05)[2025-04-15]. https://doi.org/10.1155/2021/6658842. |
| [37] | MOUSSAS V, ANDREATOS A. Malware Detection Based on Code Visualization and Two-Level Classification[EB/OL]. (2021-03-11)[2025-04-15]. https://doi.org/10.3390/info12030118. |
| [38] | SUDHAKAR, KUMAR S. MCFT-CNN: Malware Classification with Fine-Tuned Convolution Neural Networks Using Traditional and Transfer Learning in the Internet of Things[J]. Future Generation Computer Systems, 2021, 125: 334-351. |
| [39] | KUMAR S, JANET B. DTMIC: Deep Transfer Learning for Malware Image Classification[EB/OL]. (2022-02-01)[2025-04-15]. https://doi.org/10.1016/j.jisa.2021.103063. |
| [40] | VU D L, NGUYEN T K, NGUYEN T V, et al. A Convolutional Transformation Network for Malware Classification[C]// IEEE. 2019 6th NAFOSTED Conference on Information and Computer Science. New York: IEEE, 2019: 234-239. |
| [41] | LE Quan, BOYDELL O, MAC N B, et al. Deep Learning at the Shallow End: Malware Classification for Non-Domain Experts[J]. Digital Investigation, 2018, 26: 118-126. |
| [42] | QIAO Yanchen, JIANG Qingshan, JIANG Zhenchao, et al. A Multi-Channel Visualization Method for Malware Classification Based on Deep Learning[C]// IEEE. 2019 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/13th IEEE International Conference on Big Data Science and Engineering. New York: IEEE, 2019: 757-762. |
| [43] | CHEN Jun, GUO Shize, MA Xin, et al. SLAM: A Malware Detection Method Based on Sliding Local Attention Mechanism[EB/OL]. (2020-09-25)[2025-04-15]. https://doi.org/10.1155/2020/6724513. |
| [44] | HUO Xuan, LI Ming, ZHOU Zhihua. Control Flow Graph Embedding Based on Multi-Instance Decomposition for Bug Localization[C]// AAAI. The AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2020: 4223-4230. |
| [45] | MOON H J, BU S J, CHO S B. Directional Graph Transformer-Based Control Flow Embedding for Malware Classification[C]// Springer. Intelligent Data Engineering and Automated Learning-IDEAL 2021: 22nd International Conference. Heidelberg: Springer, 2021: 426-436. |
| [46] | BURNAEV E, SMOLYAKOV D. One-Class SVM with Privileged Information and Its Application to Malware Detection[C]// IEEE. 2016 IEEE 16th International Conference on Data Mining Workshops. New York: IEEE, 2016: 273-280. |
| [47] | NARAYANAN B N, DJANEYE-BOUNDJOU O, KEBEDE T M. Performance Analysis of Machine Learning and Pattern Recognition Algorithms for Malware Classification[C]// IEEE. 2016 IEEE National Aerospace and Electronics Conference (NAECON) and Ohio Innovation Summit (OIS). New York: IEEE, 2016: 338-342. |
| [48] | SHAO Yanli, LU Yang, WEI Dan, et al. Malicious Code Classification Method Based on Deep Residual Network and Hybrid Attention Mechanism for Edge Security[EB/OL]. (2022-01-01)[2025-04-15]. https://doi.org/10.1155/2022/3301718. |
| [1] | 张兴兰, 陶科锦. 基于高阶特征与重要通道的通用性扰动生成方法[J]. 信息网络安全, 2025, 25(5): 767-777. |
| [2] | 秦广雪, 李丽莎. 基于量子卷积神经网络的ARX分组密码区分器[J]. 信息网络安全, 2025, 25(3): 467-477. |
| [3] | 张双全, 殷中豪, 张环, 高鹏. 基于残差卷积神经网络的网络攻击检测技术研究[J]. 信息网络安全, 2025, 25(2): 240-248. |
| [4] | 刘联海, 黎汇业, 毛冬晖. 基于图像凸包特征的CBAM-CNN网络入侵检测方法[J]. 信息网络安全, 2024, 24(9): 1422-1431. |
| [5] | 许楷文, 周翊超, 谷文权, 陈晨, 胡晰远. 基于多尺度特征融合重建学习的深度伪造人脸检测算法[J]. 信息网络安全, 2024, 24(8): 1173-1183. |
| [6] | 薛羽, 张逸轩. 深层神经网络架构搜索综述[J]. 信息网络安全, 2023, 23(9): 58-74. |
| [7] | 苑文昕, 陈兴蜀, 朱毅, 曾雪梅. 基于深度学习的HTTP负载隐蔽信道检测方法[J]. 信息网络安全, 2023, 23(7): 53-63. |
| [8] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [9] | 李志华, 王志豪. 基于LCNN和LSTM混合结构的物联网设备识别方法[J]. 信息网络安全, 2023, 23(6): 43-54. |
| [10] | 赵小林, 王琪瑶, 赵斌, 薛静锋. 基于机器学习的匿名流量分类方法研究[J]. 信息网络安全, 2023, 23(5): 1-10. |
| [11] | 赵彩丹, 陈璟乾, 吴志强. 基于多通道联合学习的自动调制识别网络[J]. 信息网络安全, 2023, 23(4): 20-29. |
| [12] | 姚远, 樊昭杉, 王青, 陶源. 基于多元时序特征的恶意域名检测方法[J]. 信息网络安全, 2023, 23(11): 1-8. |
| [13] | 李思聪, 王坚, 宋亚飞, 黄玮. 基于BiTCN-DLP的恶意代码分类方法[J]. 信息网络安全, 2023, 23(11): 104-117. |
| [14] | 秦一方, 张健, 梁晨. 基于神经网络的电子病历数据特征提取技术研究[J]. 信息网络安全, 2023, 23(10): 70-76. |
| [15] | 刘光杰, 段锟, 翟江涛, 秦佳禹. 基于多特征融合的移动流量应用识别[J]. 信息网络安全, 2022, 22(7): 18-26. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||