信息网络安全 ›› 2017, Vol. 17 ›› Issue (9): 63-68.doi: 10.3969/j.issn.1671-1122.2017.09.015
虚拟机自省技术研究
- 1. 天津理工大学计算机科学与工程学院,天津 300384
2. 中国民航大学信息安全测评中心,天津 300300
-
收稿日期:2017-08-01出版日期:2017-09-20发布日期:2020-05-12 -
作者简介:作者简介: 张健(1968—),男,天津,正高级工程师,博士,主要研究方向为网络空间安全、恶意代码防治;高铖(1994—),男,陕西,硕士研究生,主要研究方向为信息安全;宫良一(1987—),男,天津,讲师,博士,主要研究方向为普适计算、网络与信息安全;顾兆军(1966—),男,山东,教授,博士,主要研究方向为网络与信息安全、民航信息系统。
-
基金资助:国家重点研发计划[2016YFB0800805];天津市科技服务业科技重大专项[16ZXFWGX00140];中国民航大学信息安全测评中心开放基金课题[CAAC-ISECCA-201501]
Research on Virtual Machine Introspection Technology
Jian ZHANG1( ), Cheng GAO1, Liangyi GONG1, Zhaojun GU2
), Cheng GAO1, Liangyi GONG1, Zhaojun GU2
- 1. School of Computer Science and Engineering, Tianjin University of Technology, Tianjin 300384, China
2. Information Security Evaluation Center, Civil Aviation University of China, Tianjin 300300, China
-
Received:2017-08-01Online:2017-09-20Published:2020-05-12
摘要:
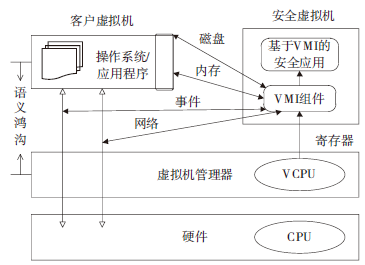
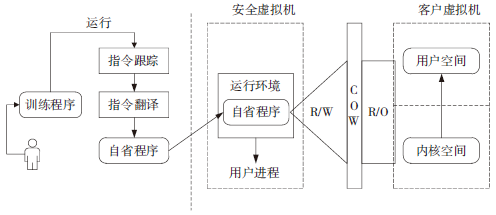
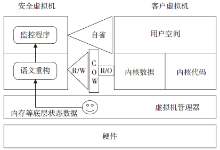
虚拟机自省是从虚拟机外部获取客户虚拟机操作系统内部状态信息的技术,该技术打破了传统安全防护技术的瓶颈,受到了安全领域的广泛关注。近年来,该技术已经在入侵检测、恶意软件分析、数字取证等领域得到应用,尤其是针对日益凸显的云安全问题,具有极好的应用前景。文章深入分析了VMI技术的实现原理和发展历史,提出了一种新的VMI技术分类方法,并研究了VMI技术的应用情况,分析提出了VMI技术存在的问题和未来发展方向。
中图分类号:
引用本文
张健, 高铖, 宫良一, 顾兆军. 虚拟机自省技术研究[J]. 信息网络安全, 2017, 17(9): 63-68.
Jian ZHANG, Cheng GAO, Liangyi GONG, Zhaojun GU. Research on Virtual Machine Introspection Technology[J]. Netinfo Security, 2017, 17(9): 63-68.
| [1] | 牛鹏飞,张健,常青,等. 基于Xen的异常行为在线检测平台研究与设计[J]. 信息网络安全,2016(9):139-144. |
| [2] | BAUMAN E, AYOADE G, LIN Z.A Survey on Hypervisor-based Monitoring: Approaches, Applications, and Evolutions[J]. ACM Computing Surveys, 2015, 48(1): 1-33. |
| [3] | 王文旭,张健,常青,等. 云计算虚拟化平台安全问题研究[J]. 信息网络安全,2016(9):163-168. |
| [4] | 李保珲,徐克付,张鹏,等. 虚拟机自省技术研究与应用进展[J]. 软件学报,2016,27(6):1384-1401. |
| [5] | 崔超远,乌云,李平,等. 虚拟机自省中一种消除语义鸿沟的方法[J]. 通信学报,2015,36(8):31-37. |
| [6] | GARFINKEL T, ROSENBLUM M. A Virtual Machine Introspection Based Architecture for Intrusion Detection[EB/OL]. , 2017-5-11. |
| [7] | HEBBAL Y, LANIEPCE S, MENAUD J M.Virtual Machine Introspection: Techniques and Applications[C]//IEEE. 10th International Conference on Availability, Reliability and Security (ARES), August 24-27, 2015, Toulouse, France. New Jersey: IEEE, 2015: 676-685. |
| [8] | 李勇钢,崔超远,李平. 基于虚拟机自省的客户机进程内容获取[J]. 计算机工程与设计,2016,37(6):1697-1700. |
| [9] | PETRONI N L, FRASER T, MOLINA J, et al.Copilot - A Coprocessor-based Kernel Runtime Integrity Monitor[C]//ACM. 13th Conference on USENIX Security Symposium, August 9-13, 2004, San Diego, CA, USA. New York: ACM, 2004: 179-194. |
| [10] | PAYNE B D, CARBONE M, SHARIF M, et al.Lares: An Architecture for Secure Active Monitoring Using Virtualization[C]//IEEE. 2008 IEEE Symposium on Security and Privacy, May 18-22, 2008, Oakland, CA, USA. New Jersey: IEEE, 2008: 233-247. |
| [11] | DOLAN-GAVITT B, LEEK T, ZHIVICH M, et al.Virtuoso: Narrowing the Semantic Gap in Virtual Machine Introspection[C]//IEEE. 2011 IEEE Symposium on Security and Privacy, May 22-25, 2011, Berkeley, CA, USA. New Jersey: IEEE, 2011: 297-312. |
| [12] | SUNEJA S, ISCI C, DE LARA E, et al.Exploring VM Introspection: Techniques and Trade-offs[J]. ACM Sigplan Notices, 2015, 50(7): 133-146. |
| [13] | FU Yangchun, LIN Zhiqiang.Space Traveling across VM: Automatically Bridging the Semantic Gap in Virtual Machine Introspection via Online Kernel Data Redirection[C]//IEEE. 2012 IEEE Symposium on Security and Privacy, May 20-23, 2012, San Francisco, CA, USA. New Jersey: IEEE, 2012: 586-600. |
| [14] | SABERI A, FU Yangchun, LIN Zhiqiang. HYBRID-BRIDGE: Efficiently Bridging the Semantic Gap in Virtual Memory Introspection via Decoupled Execution and Training Memoization[EB/OL]. , 2017-5-11. |
| [15] | 乌云,李平,李勇钢. 基于虚拟机自省的隐藏文件检测方法[J]. 计算机系统应用,2016,25(1):175-180. |
| [16] | MISHRA P, PILLI E S, VARADHARAJAN V, et al.Intrusion Detection Techniques in Cloud Environment: A Survey[J]. Journal of Network & Computer Applications, 2017, 77(C): 18-47. |
| [17] | MISHRA P, PILLI E S, VARADHARAJANT V, et al.NvCloudIDS: A Security Architecture to Detect Intrusions at Network and Virtualization Layer in Cloud Environment[C]//IEEE. 2016 International Conference on Advances in Computing, Communications and Informatics, September 21-24, 2016, Jaipur, India. New Jersey: IEEE, 2016: 56-62. |
| [18] | RILEY R, JIANG Xuxian, XU Dongyan.Multi-aspect Profiling of Kernel Rootkit Behavior[C]//ACM. 4th ACM European Conference on Computer Systems, April 1-3, 2009, Nuremberg, Germany. New York: ACM, 2009: 47-60. |
| [19] | XUAN Chaoting, COPELAND J, BEYAH R.Toward Revealing Kernel Malware Behavior in Virtual Execution Environments[C]//Springer. 12th International Symposium on Recent Advances in Intrusion Detection, September 23-25, 2009, Saint-Malo, France. Heidelberg: Springer, 2009: 304-325. |
| [20] | CHENG Yingxin, FU Xiao, DU Xiaojiang, et al. A Lightweight Live Memory Forensic Approach Based on Hardware Virtualization[EB/OL]. , 2017-5-11. |
| [21] | XIAO Jidong, LU Lei, WANG Haining, et al.HyperLink: Virtual Machine Introspection and Memory Forensic Analysis without Kernel Source Code[C]//IEEE. 2016 IEEE International Conference on Autonomic Computing. IEEE, July 17-22, 2016, Wurzburg, Germany. New Jersey: IEEE, 2016: 127-136. |
| [22] | WESTPHAL F, AXELSSON S, NEUHAUS C, et al.VMI-PL: A Monitoring Language for Virtual Platforms using Virtual Machine Introspection[J]. Digital Investigation, 2014, 11(4): S85-S94. |
| [23] | HAN Yyandong, HAO Zhiyu, CUI Lei, et al.A Hybrid Monitoring Mechanism in Virtualized Environments[C]//IEEE. 2016 IEEE International Conference on Trust, Security and Privacy in Computing and Communications, August 23-26, 2016, Tianjin, China. New Jersey: IEEE, 2016: 1038-1045. |
| [24] | FU Yangchun, ZENG Junjuan, LIN Zhiqiang.HYPERSHELL: A Practical Hypervisor Layer Guest OS Shell for Automated in-VM Management[C]//USENIX. 2014 USENIX conference on USENIX Annual Technical Conference, June 19-20, 2014, Philadelphia USA. New York: ACM, 2014: 85-96. |
| [25] | BAEK H W, SRIVASTAVA A, VAN D M J. CloudVMI: Virtual Machine Introspection as a Cloud Service[C]//IEEE. 2014 IEEE International Conference on Cloud Engineering, March 11-14, 2014, Boston, MA, USA. New Jersey: IEEE, 2014: 153-158. |
| [26] | TAUBMANN B, FRÄDRICH C, DUSOLD D, et al. TLSkex: Harnessing Virtual Machine Introspection for Decrypting TLS Communication[J]. Digital Investigation, 2016(16): S114-S123. |
| [27] | SHI Jiangyong, YANG Yuexiang, TANG Chuan.Hardware Assisted Hypervisor Introspection[J]. SpringerPlus, 2016, 5(1): 647. |
| [28] | 池亚平,姜停停,戴楚屏,等. 基于BLP的虚拟机多级安全强制访问控制系统设计与实现[J]. 信息网络安全,2016(10):1-7. |
| [1] | 王晓, 赵军, 张建标. 基于可信软件基的虚拟机动态监控机制研究[J]. 信息网络安全, 2020, 20(2): 7-13. |
| [2] | 张健, 栗文真, 宫良一. 恶意邮件检测技术研究[J]. 信息网络安全, 2018, 18(9): 80-85. |
| [3] | 张建标, 杨石松, 涂山山, 王晓. 面向云计算环境的vTPCM可信管理方案[J]. 信息网络安全, 2018, 18(4): 9-14. |
| [4] | 翟高寿, 刘晨, 向勇. 基于内核函数监控的Linux系统防护方法的研究与实现[J]. 信息网络安全, 2018, 18(3): 26-38. |
| [5] | 梅东晖, 李红灵. 基于多目标混合粒子群算法的虚拟机负载均衡研究[J]. 信息网络安全, 2018, 18(2): 78-83. |
| [6] | 何利, 姚元辉. 基于上下文聚类的云虚拟机异常检测与识别策略[J]. 信息网络安全, 2018, 18(12): 54-65. |
| [7] | 王东亮, 衣俊艳, 李时慧, 王洪新. 融合负载均衡和蝙蝠算法的云计算任务调度[J]. 信息网络安全, 2017, 17(1): 23-28. |
| [8] | 刘佳佳, 俞研, 胡恒伟, 吴家顺. 一种基于虚拟机定制的应用保护方法研究[J]. 信息网络安全, 2017, 17(1): 63-67. |
| [9] | 宫月, 李超, 吴薇. 虚拟化安全技术研究[J]. 信息网络安全, 2016, 16(9): 73-78. |
| [10] | 牛鹏飞, 张健, 常青, 顾兆军. 基于Xen的异常行为在线检测平台研究与设计[J]. 信息网络安全, 2016, 16(9): 139-144. |
| [11] | 王文旭, 张健, 常青, 顾兆军. 云计算虚拟化平台安全问题研究[J]. 信息网络安全, 2016, 16(9): 163-168. |
| [12] | 谭茁, 翟高寿. 设备驱动非内核化通信架构的研究与实现[J]. 信息网络安全, 2016, 16(11): 57-65. |
| [13] | 池亚平, 姜停停, 戴楚屏, 孙尉. 基于BLP的虚拟机多级安全强制访问控制系统设计与实现[J]. 信息网络安全, 2016, 16(10): 1-7. |
| [14] | 卿斯汉. 关键基础设施安全防护[J]. 信息网络安全, 2015, 15(2): 1-6. |
| [15] | 吴继康, 于徐红, 王虹. 基于第三方可信平台的混合云安全存储系统构建[J]. 信息网络安全, 2015, 15(12): 28-33. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||