信息网络安全 ›› 2016, Vol. 16 ›› Issue (9): 73-78.doi: 10.3969/j.issn.1671-1122.2016.09.015
虚拟化安全技术研究
- 公安部第一研究所,北京 100048
Research on the Security Technology in Virtualization
- The First Research Institute of the Ministry of Public Security of PRC, Beijing 100048, China
摘要:
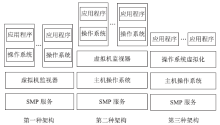
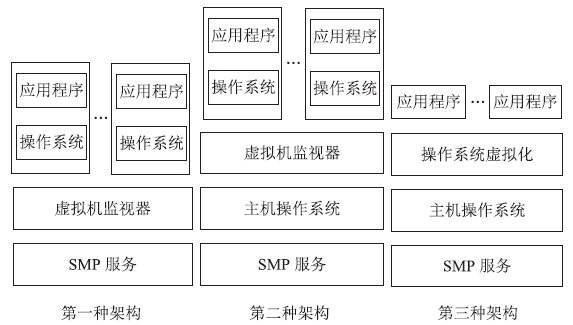
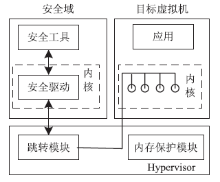
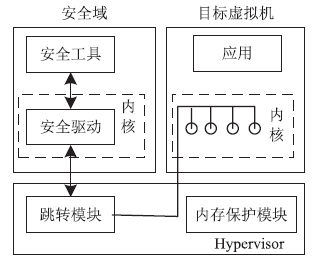
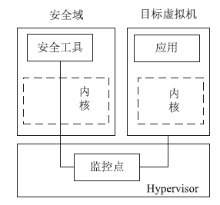
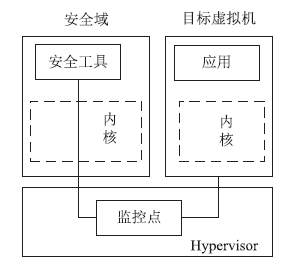
云计算在经济、高效、敏捷和创新等方面的突出优势受到各国政府的广泛重视。随着云计算的广泛应用,作为核心技术的虚拟化技术也得到了进一步的发展。虚拟化技术在为云计算的应用带来便利条件的同时,也引入了一些新的安全挑战。文章对现有虚拟化相关资料和实际情况进行了深入的研究,从虚拟化安全隐患和虚拟化安全攻击两个方面,对虚拟机蔓延(Virtual Machine Sprawl)、虚拟机迁移(Virtual Machine Sprawl)、特殊配置隐患(Peculiar Set-up Hidden)、虚拟机跳跃(Virtual Machine Hopping)、虚拟机逃逸(Virtual Machine Escape)和拒绝服务攻击(Denial of Service Attack)进行了分析。并在此基础上,从宿主机安全机制、Hypervisor安全机制和虚拟机安全机制3个层面提出了虚拟化安全的解决方案,为构建一个坚实可靠的虚拟化系统奠定良好基础,为云计算基础设施平台的建设提供安全技术保障。
中图分类号: