信息网络安全 ›› 2015, Vol. 15 ›› Issue (12): 28-33.doi: 10.3969/j.issn.1671-1122.2015.12.005
基于第三方可信平台的混合云安全存储系统构建
- 1.贵州师范大学贵州省信息与计算科学重点实验室,贵州贵阳 550001
2. 解放军第309医院,北京100091
Research on Security of Hybrid Cloud Based on Trusted Computing Technology
WU Jikang1( ), YU Xuhong1, WANG Hong2
), YU Xuhong1, WANG Hong2
- 1. Key Laboratory of Information and Computational Science of Guizhou Province, Guizhou Normal University,Guiyang Guizhou 550001, China
2. The 309TH Hospital of Chinese Peole's Libertation Army 100091, China
摘要:
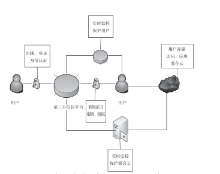
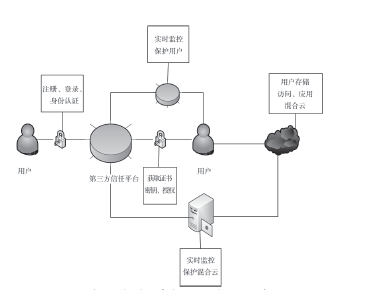
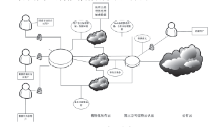
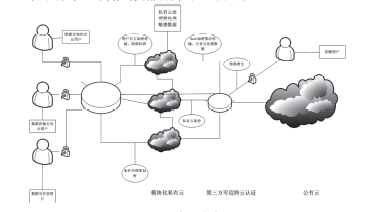
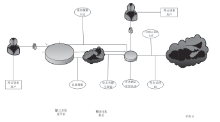
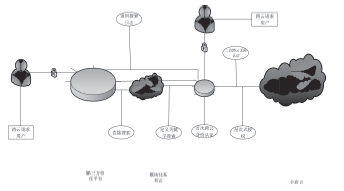
文章首先分析了现实中混合云存在的安全问题:由于混合云的开放性,云服务器的管理者与外部攻击者能够直接或间接获取用户数据,特别是用户敏感数据,从而造成用户隐私数据泄漏与滥用。文章结合可信计算技术对各问题做出解决,并给出具体的操作步骤:身份认证中为用户划分信用组别,同时也对混合云上的各种应用和事项进行登记评估;存储中将数据分开处理,采用全同态加密算法加密数据后再对其进行操作,并对服务器数据的完整持有进行验证,保障数据正确持有;跨云身份认证中由第三方认证平台管理用户身份,用户跨云无需多次认证。然后对此方案的性能进行分析,说明此方案适用于用户变化不大的一般性企业。最后,对可行性、数据安全性、数据可用性、用户隐私安全、效率性等指标与现有研究方案进行比较,表明此混合云安全存储系统具有更好的优越性。
中图分类号: