信息网络安全 ›› 2017, Vol. 17 ›› Issue (1): 63-67.doi: 10.3969/j.issn.1671-1122.2017.01.010
一种基于虚拟机定制的应用保护方法研究
- 南京理工大学计算机科学与工程学院,江苏南京 210094
Research on a Protection Mechanism Based on Virtual Machine Customization
Jiajia LIU, Yan YU( ), Hengwei HU, Jiashun WU
), Hengwei HU, Jiashun WU
- School of Computer Science and Engineering, Nanjing University of Science and Technology, Nanjing Jiangsu 210094, China
摘要:
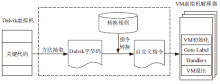
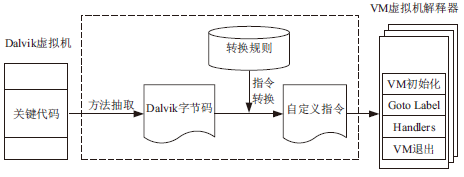
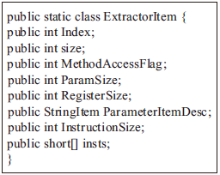
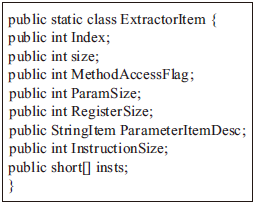
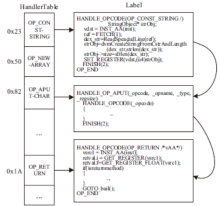
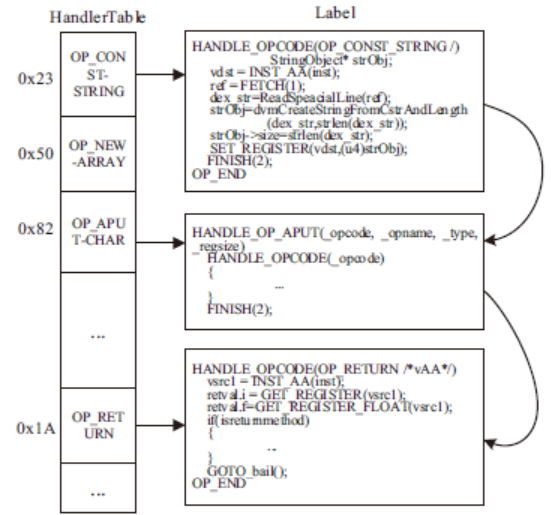
移动互联网的快速发展促进了智能手机应用的繁荣,Android系统凭借其开源特点迅速成为市场份额最大的智能手机系统。与此同时,Android应用也成为了攻击者的重要攻击目标,加上第三方应用市场监管不周,导致Android应用面临重打包、恶意篡改等严峻的安全威胁。为提高攻击者逆向分析Android APP中DEX文件的难度,文章提出了一种基于虚拟机定制的Android应用保护方法。首先提取待保护方法的指令及其属性信息,并通过一定的转换规则将其转换成特定的虚拟指令格式;然后通过专用的VM解释器解释执行生成的虚拟指令;最后构建轻量级原型系统,以开源应用程序为测试样本完成实验验证。实验结果表明,该方法可以有效提高代码不可读性,从而在较小的时空消耗上大幅增加攻击者逆向分析的难度。
中图分类号: