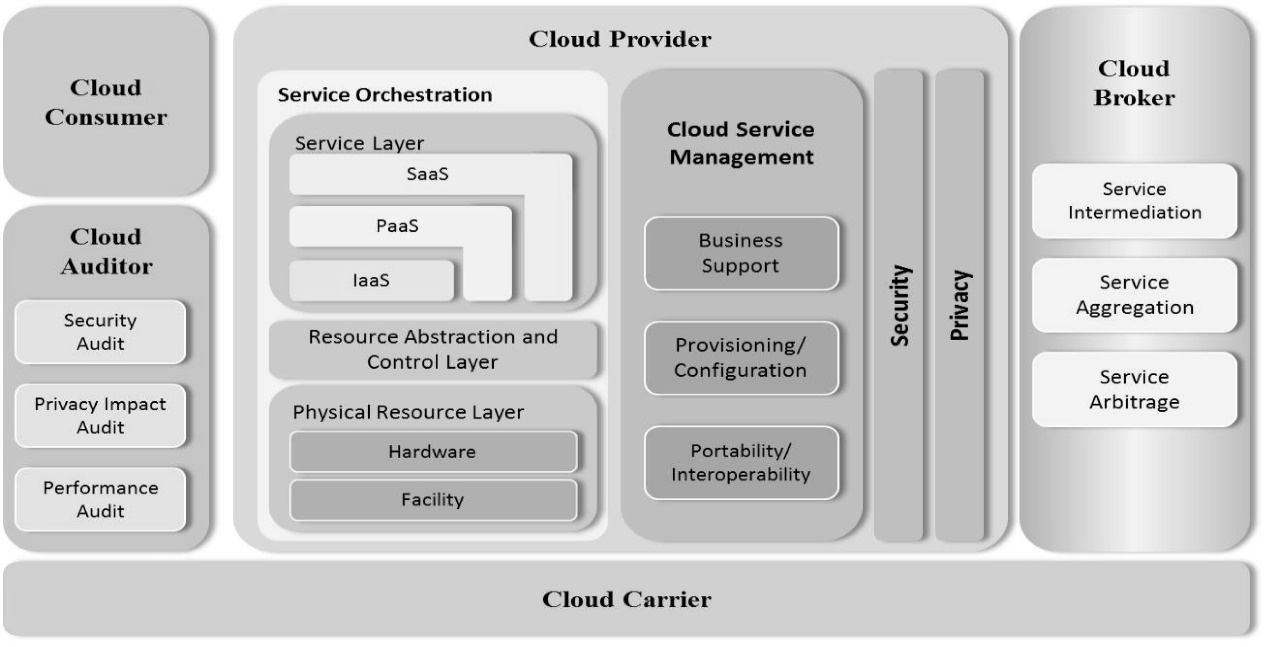
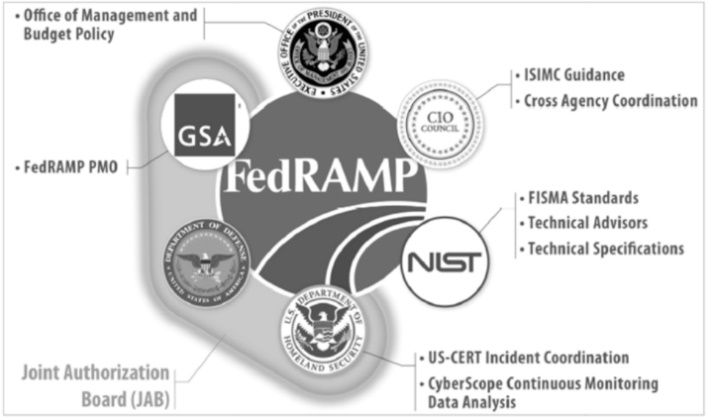
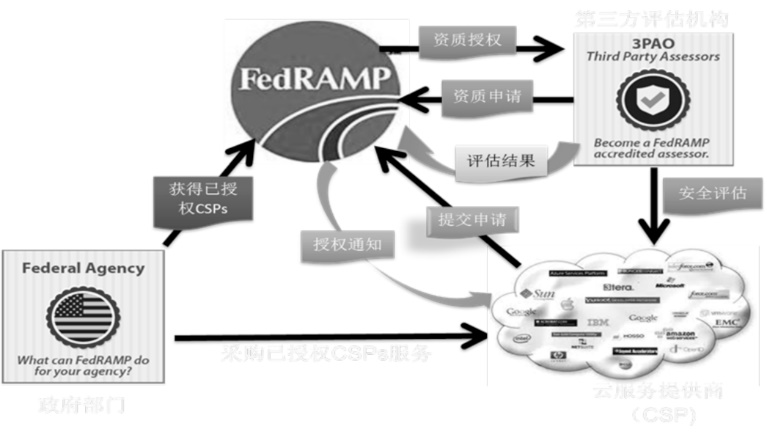
信息网络安全 ›› 2015, Vol. 15 ›› Issue (2): 1-6.doi: 10.3969/j.issn.1671-1122.2015.02.001
• • 下一篇
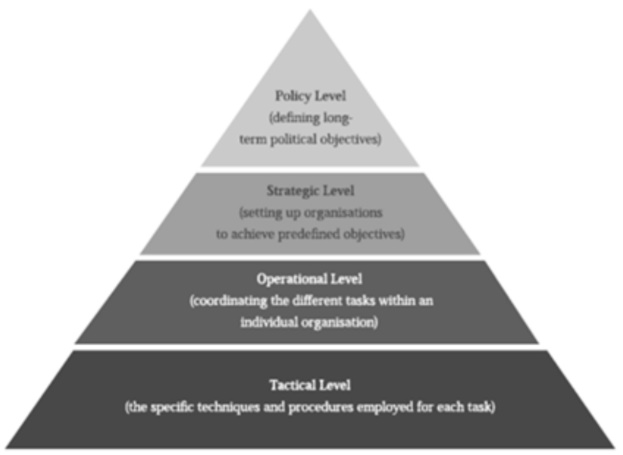
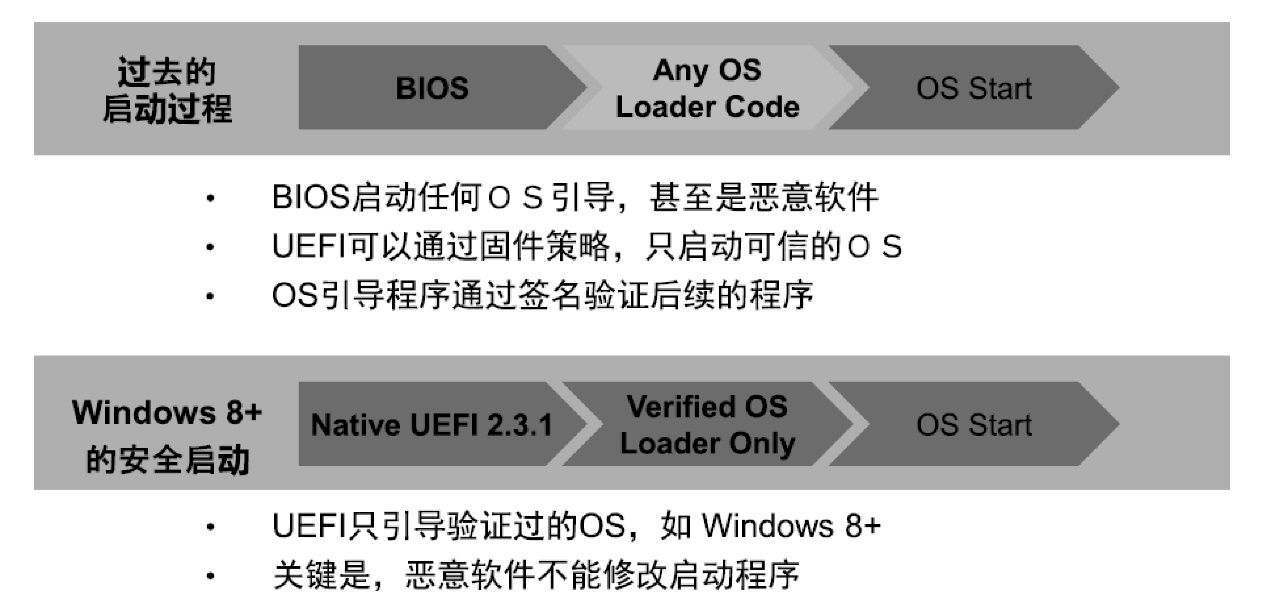
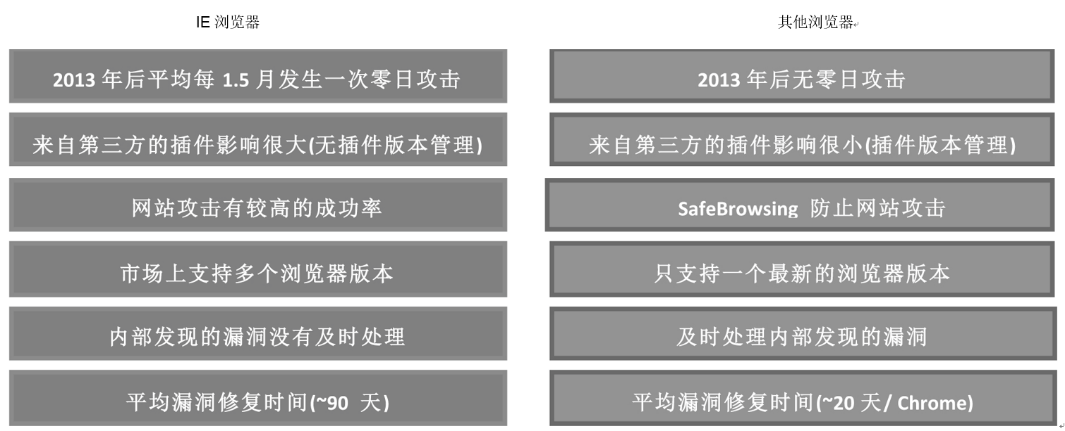
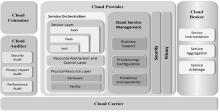
关键基础设施安全防护
卿斯汉1,2,3
- 1. 中国科学院软件研究所,北京 100190
2. 信息安全国家重点实验室, 北京 100093
3. 北京大学软件与微电子学院,北京 102600
Security Protection of Critical Infrastructure
Si-han QING1,2,3
- 1. Institute of Software, Chinese Academy of Sciences, Beijing 100190, China
2. State Key Laboratory of Information Security, Beijing 100093, China
3. School of Software & Microelectronics, Peking University, Beijing 102600, China