信息网络安全 ›› 2018, Vol. 18 ›› Issue (1): 1-8.doi: 10.3969/j.issn.1671-1122.2018.01.001
• • 下一篇
云环境下可重构虚拟可信根的设计框架
张建标1,2,3, 赵子枭1,2,3( ), 胡俊1,2,3, 王晓1,2,3
), 胡俊1,2,3, 王晓1,2,3
- 1.北京工业大学信息学部, 北京 100124
2.可信计算北京市重点实验室, 北京 100124
3.信息安全等级保护关键技术国家工程实验室,北京 100124
The Design Framework of Reconfi gurable Virtual Root of Trust in Cloud Environment
Jianbiao ZHANG1,2,3, Zixiao ZHAO1,2,3( ), Jun HU1,2,3, Xiao WANG1,2,3
), Jun HU1,2,3, Xiao WANG1,2,3
- 1. Faculty of Information Technology, Beijing University of Technology, Beijing 100124, China
2. Beijing Key Laboratory of Trusted Computing, Beijing 100124, China
3. National Engineering Laboratory for Critical Technologies of Information Security Classified Protection, Beijing 100124,China
摘要:
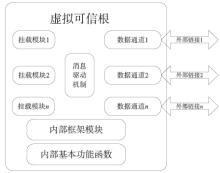
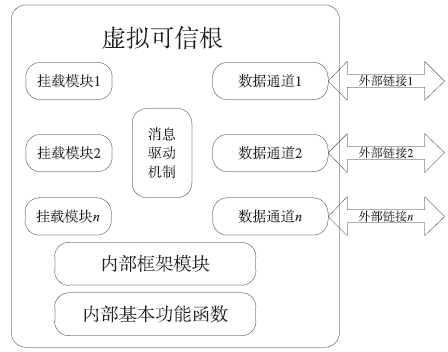
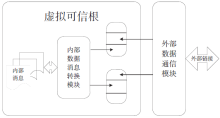
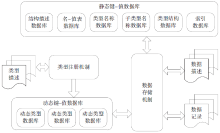
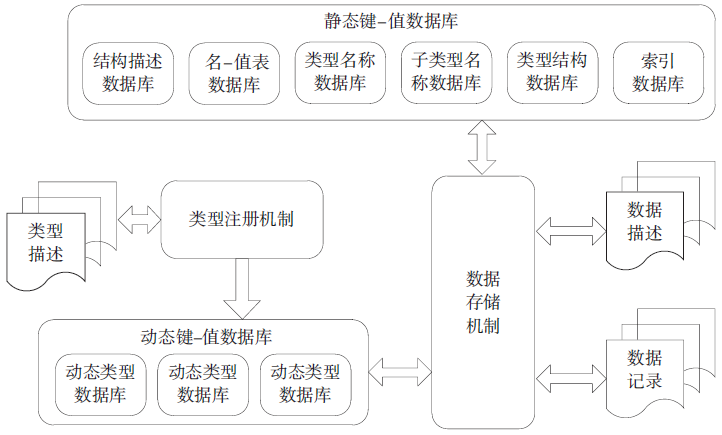
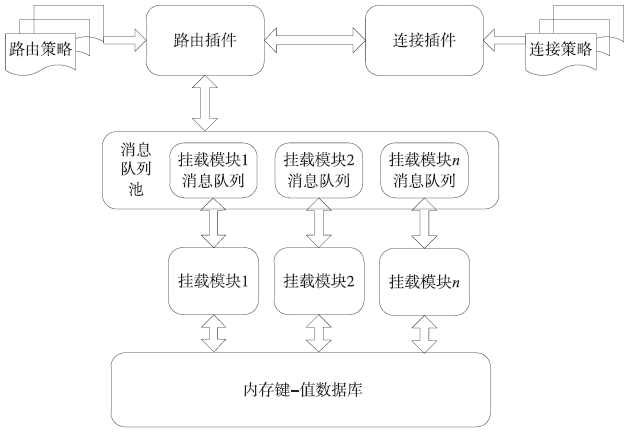
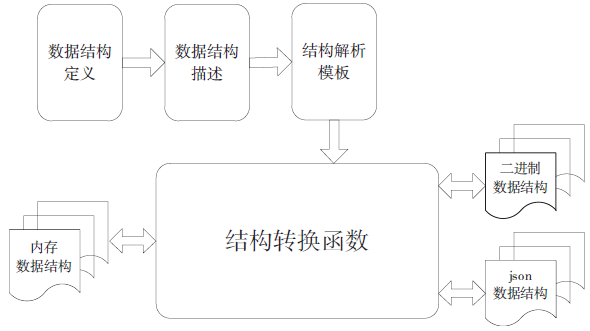
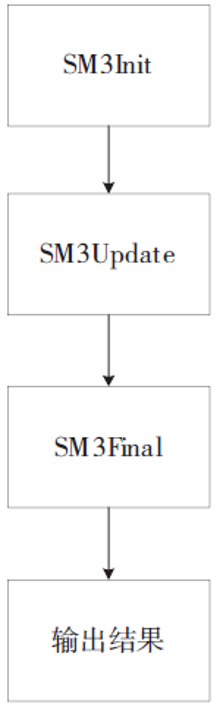
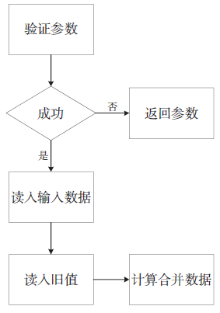
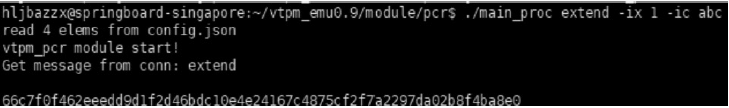
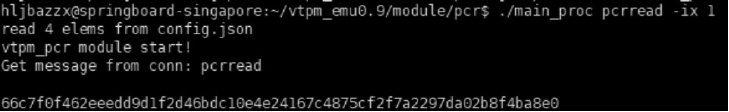
可信计算技术与云计算技术的结合,使得可信云逐渐成为解决云安全问题的一大重要手段。但是目前可信云的可信原点——虚拟可信根仍存在一些问题:仅支持TPM而不支持TPCM,无法做到主动防御;内部结构不便修改与扩展;所使用的密码算法符合国外标准,国内无法达到自主可控。因此,文章提出了一种全新的虚拟可信根设计方案,该方案以模块化的结构对可信根进行重构,各个模块之间通过内部统一的消息格式来协调合作,为云环境提供安全可靠的计算保障。基于此方案的可重构虚拟可信根具有以下特点:具备高可扩展性,其结构易改造从而达到多元异构,能够模拟不同的TPM或TPCM架构;同时具备自主可控性,其核心密码算法遵循国家标准。
中图分类号: