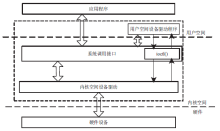
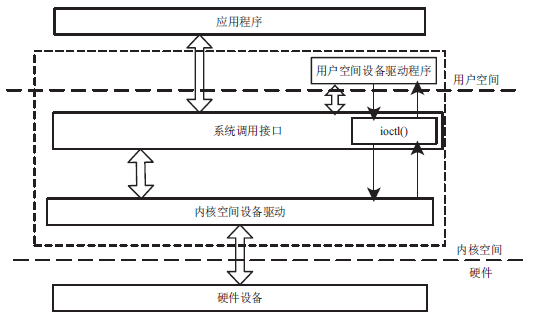
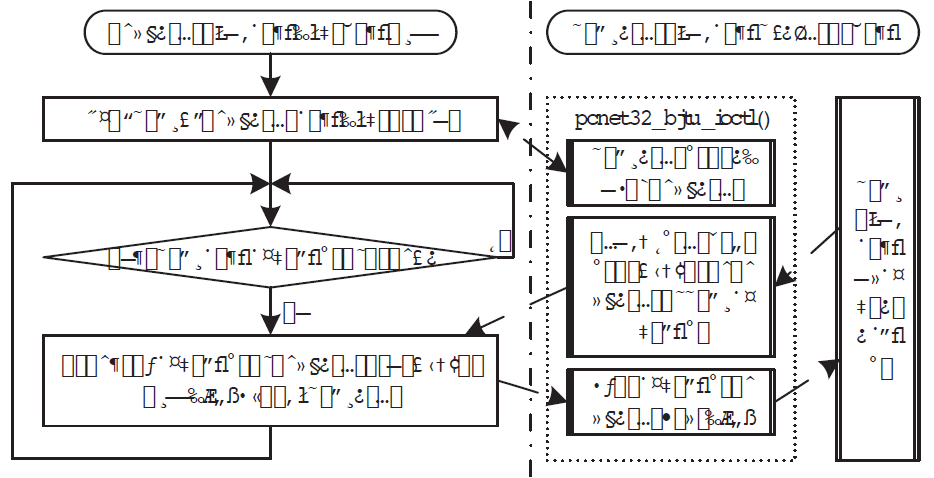
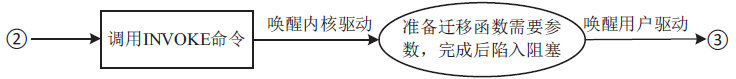
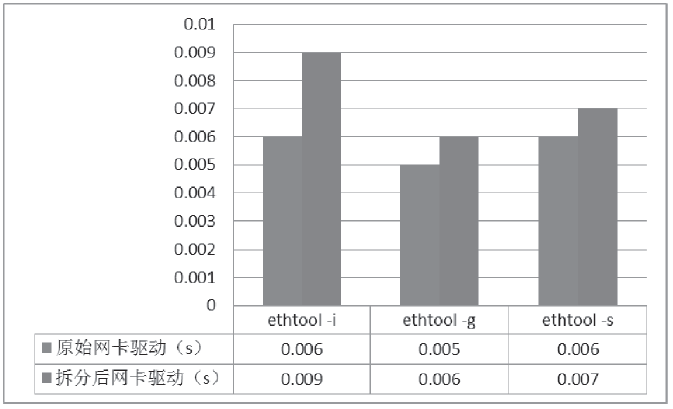
| [1] |
MATIAS R, PRINCE M, BORGES L, et al.An Empirical Exploratory Study on Operating System Reliability[C]// ACM. The 29th Annual ACM Symposium on Applied Computing, March 24-28, 2014, Gyeongju, Republic of Korea. New York: ACM, 2014: 1523-1528.
|
| [2] |
ZHAI Gaoshou, GUO Tao, HUANG Jie.SCIATool: A Tool for Analyzing SELinux Policies Based on Access Control Spaces, Information Flows and CPNs[M]. AG Switzerland: Springer, 2015: 294-309.
|
| [3] |
ALEXEY K, VADIM M,ALEXANDER P, et al.Establishing Linux Driver Verification Process[C]// Springer-Verlag Berlin. The 7th international Andrei Ershov Memorial conference on Perspectives of Systems Informatics, June 15-19, 2009, Novosibirsk, Russia. Springer-Verlag Berlin Heidelberg, 2010: 165-176.
|
| [4] |
BALAKRISHNAN A, KRISHNAN S. Factorization of Device Driver Code between Kernel and User Spaces, Technical Report [EB/OL]. , 2016-8-1.
|
| [5] |
HERDER J N, BOS H, GRAS B, et al.Fault Isolation for Device Drivers[C]// IEEE Computer Society. 2009 IEEE/IFIP International Conference on Dependable Systems & Networks, June 29-July 2, 2009, Lisbon, Portugal. Washington: IEEE Computer Society, 2009: 33-42.
|
| [6] |
LESLIE B, FITZROY-DALE N, HEISER G.Encapsulated User-Level Device Drivers in the Mungi Operating System[C]// University of Adelaide. Workshop on Object Systems and Software Architectures, January 11-14, 2004, Victor Harbor, South Australia. South Australia: The University of Adelaide, 2004: 16-30.
|
| [7] |
SWIFT M M, MARTIN S, LEVY H M, et al.Nooks: An Architecture for Reliable Device Drivers[C]//ACM. The 10th workshop on ACM SIGOPS European workshop, July 01, 2002, Saint-Emilion, France. New York: ACM, 2002: 102-107.
|
| [8] |
WANG X, CHENG C.Access Control Using Trusted Virtual Machine Based on Xen[M]//Applied Informatics and Communication. Berlin: Springer Berlin Heidelberg, 2011: 94-101.
|
| [9] |
ZHOU F, CONDIT J, ANDERSON Z, et al.SafeDrive: Safe and Recoverable Extensions Using Language-Based Techniques[C]// USENIX Association. The 7th symposium on Operating systems design and implementation, November 6-8, 2006, Washington, USA. Berkeley: USENIX Association, 2006: 45-60.
|
| [10] |
TSIGKOGIANNIS I. Introduction to the User-Mode Driver Framework [EB/OL]. , 2006-10-10.
|
| [11] |
HERDER J N, BOS H, GRAS B, et al.MINIX 3: A Highly Reliable, Self-Repairing Operating System[J]. ACM SIGOPS Operating Systems Review, 2006, 40(3): 80-89.
|
| [12] |
GANAPATHY V, RENZELMANN M, BALAKRISHNAN A, et al.The Design and Implementation of Microdrivers[J]. ACM SIGARCH Computer Architecture News, 2008, 36(1):168-178.
|
| [13] |
PROVOS N.Improving Host Security with System Call Policies[C]// USENIX Association. The 12th conference on USENIX Security Symposium, August 04 - 08, 2003, Washington, DC. Berkeley: USENIX Association, 2003:257-272.
|
| [14] |
NEIRA-AYUSO P, GASCA R M, LEFEVRE L.Communicating between the Kernel and User-Space in Linux Using Netlink Sockets[J]. Software: Practice and Experience, 2010, 40(9): 797-810.
|
| [15] |
ZHOU Li, TAN Fangyong, GAO Xiaohui.Research on Application of Netlink Socket Communication in Linux IPSec Support Mechanism[C]// IEEE. ICCSE 2010: 5th International Conference on Computer Science and Education, August 24-27, 2010, Hefei, China. IEEE, 2010: 933-936.
|
| [16] |
卿斯汉. 关键基础设施安全防护[J]. 信息网络安全,2015(2):1-6.
|
| [17] |
王永娟, 郝家宝. 网络信息安全的威胁与防范技术研究[J]. 中国管理信息化,2015,18(20):146.
|
| [18] |
文伟平,郭荣华,孟正,等. 信息安全风险评估关键技术研究与实现[J]. 信息网络安全,2015(2):7-14.
|
| [19] |
杨宁学, 诸昌钤, 聂爱丽. 内存映射文件及其在大数据量文件快速存取中的应用[J]. 计算机应用研究, 2004, 21(8): 187-188.
|