Netinfo Security ›› 2025, Vol. 25 ›› Issue (5): 713-721.doi: 10.3969/j.issn.1671-1122.2025.05.004
Previous Articles Next Articles
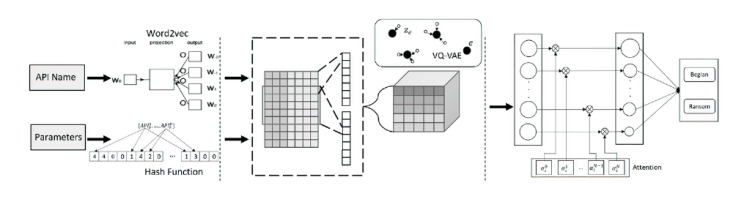
Dynamic Detection of Ransomware Based on Enhanced API Sequences with Running Parameters
WEI Songjie( ), WU Qinqin, YUAN Junyi
), WU Qinqin, YUAN Junyi
- School of Computer Science & Engineering, Nanjing University of Science and Technology, Nanjing 210094, China
-
Received:2024-12-30Online:2025-05-10Published:2025-06-10
CLC Number:
Cite this article
WEI Songjie, WU Qinqin, YUAN Junyi. Dynamic Detection of Ransomware Based on Enhanced API Sequences with Running Parameters[J]. Netinfo Security, 2025, 25(5): 713-721.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.05.004
| [1] | AUSTRALIAN C S C. ACSC Annual Cyber Threat Report[EB/OL]. (2020-09-20)[2024-10-25]. https://www.cyber.gov.au. |
| [2] | SOPHOS. The State of Ransomware 2020[EB/OL]. (2020-11-14)[2024-10-25]. https://www.sophos.com/en-us/medialibrary/Gated-Assets/whitepapers/sophos-the-state-of-ransomware-2020-wp.pdf. |
| [3] | HASSAN N. Ransomware Revealed[M]. Berkeley: Berkeley Apress, 2019. |
| [4] |
CHEN Changqing, GUO Chun, CUI Yunhe, et al. Ransomware Early Detection Method Based on Short API Sequence[J]. Acta Electronica Sinica, 2021, 49(3): 586-595.
doi: 10.12263/DZXB.20200623 |
|
陈长青, 郭春, 崔允贺, 等. 基于API短序列的勒索软件早期检测方法[J]. 电子学报, 2021, 49(3): 586-595.
doi: 10.12263/DZXB.20200623 |
|
| [5] | HAMPTON N, BAIG Z, ZEADALLY S. Ransomware Behavioural Aanalysis on Windows Platforms[J]. Journal of Information Security and Applications, 2018, 40: 44-51. |
| [6] | DAVIDIAN M, KIPERBERG M, VANETIK N. Early Ransomware Detection with Deep Learning Models[J]. Future Internet, 2024, 16(8): 291-296. |
| [7] | ZHANG Shuqin, DU Tianhui, SHI Peiyu, et al. Early Detection and Defense Countermeasure Inference of Ransomware Based on API Sequence[J]. International Journal of Advanced Computer Science and Applications, 2023, 14(10): 632-641. |
| [8] | DING Zhenquan, XU Hui, GUO Yonghe, et al. Mal-Bert-GCN: Malware Detection by Combining Bert and GCN[C]// IEEE. 2022 IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom). New York: IEEE, 2022: 175-183. |
| [9] | ALRIMY B A S, MAAROF M A, SHAID S Z M. Ransomware Threat Success Factors, Taxonomy, and Countermeasures: A Survey and Research Directions[J]. Computers & Security, 2018, 74: 144-166. |
| [10] | LI Hao, QIAN Liping. Overview of Research on Malicious Code Visualization Detection Technology[J]. Software Guide, 2022, 21(5): 9-16. |
| 李豪, 钱丽萍. 恶意代码可视化检测技术研究综述[J]. 软件导刊, 2022, 21(5): 9-16. | |
| [11] | AHMED M E, KIM H, CAMTEPE S, et al. Peeler: Profiling Kernel-Level Events to Detect Ransomware[C]]// Springer. 26th European Symposium on Research in Computer Security. Heidelberg: Springer, 2021: 240-260. |
| [12] | DAS S, LIU Yang, ZHANG Wei, et al. Semantics-Based Online Malware Detection: Towards Efficient Real-Time Protection against Malware[J]. IEEE Transactions on Information Forensics and Security, 2015, 11(2): 289-302. |
| [13] | GUO Chun, CHEN Changqing, SHEN Guowei, et al. A Ransomware Classification Method Based on Visualization[J]. Netinfo Security, 2020, 20(4): 31-39. |
| 郭春, 陈长青, 申国伟, 等. 一种基于可视化的勒索软件分类方法[J]. 信息网络安全, 2020, 20(4): 31-39. | |
| [14] | SHARMA S, SINGH S. Texture-Based Automated Classification of Ransomware[J]. Journal of The Institution of Engineers, 2021, 102(1): 131-142. |
| [15] | SUBEDIU K P, BUDHATHOKI D R, DASGUPTA D. Forensic Analysis of Ransomware Families Using Static and Dynamic Analysis[C]// IEEE. 2018 IEEE Security and Privacy Workshops (SPW). New York: IEEE, 2018: 180-185. |
| [16] | ZAVARSKY P, LINDSKOG D. Experimental Analysis of Ransomware on Windows and Android Platforms: Evolution and Characterization[J]. Procedia Computer Science, 2016, 94: 465-472. |
| [17] | KHARRAZ A, ARSHAD S, MULLINER C, et al. Unveil:A Large-Scale, Automated Approach to Detecting Ransomware[C]// USENIX. 25th USENIX Security Symposium. Berkeley: USENIX, 2016:757-772. |
| [18] | VINAYAKUMAR R, SOMAN K P, VELAN K K S, et al. Evaluating Shallow and Deep Networks for Ransomware Detection and Classification[C]// IEEE. 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI). New York: IEEE, 2017: 259-265. |
| [19] | FENG Yun, LIUChaoge, LIUBaoxu. Poster: A New Approach to Detecting Ransomware with Deception[C]// IEEE. The 38th IEEE Symposium on Security and Privacy. New York: IEEE, 2017: 7-8. |
| [20] | KOK S H, ABDULLAH A, JHANJHI N Z, et al. Prevention of Crypto-Ransomware Using a Pre-Encryption Detection Algorithm[J]. Computers, 2019, 8(4): 79-84. |
| [21] | ALJABRI M, ALHAIDARI F, ALBUAINAIN A, et al. Ransomware Detection Based on Machine Learning Using Memory Features[J]. Egyptian Informatics Journal, 2024, 25: 445-451. |
| [22] | WEN J C C, VIMAL K, PANOS P, et al. Real-Time System Call-Based Ransomware Detection[J]. International Journal of Information Security, 2024, 23(3): 1839-1858. |
| [23] | ULLAH F, JAVAID Q, SALAM A, et al. Modified Decision Tree Technique for Ransomware Detection at Runtime Through API Calls[J]. Scientific Programming, 2020(1): 833-844. |
| [24] | HWANG J, KIM J, LEE S, et al. Two-Stage Ransomware Detection Using Dynamic Analysis and Machine Learning Techniques[J]. Wireless Personal Communications, 2020, 112(4): 2597-2609. |
| [25] | SHEEN S, YADAV A. Ransomware Detection by Mining API Call Usage[C]// IEEE. 2018 International Conference on Advances in Computing, Communications and Informatics(ICACCI). New York: IEEE, 2018: 983-987. |
| [26] | SGANDURRA D, MUNOZ-GONZALEZ L, MOHSEN R, et al. Automated Dynamic Analysis of Ransomware: Benefits, Limitations and Use for Detection[EB/OL]. (2016-10-26)[2024-10-25]. https://www.semanticscholar.org/paper/76d36dc27072b39bf42c6b7e4a954ca1afc7e373. |
| [27] | HOMAYOUN S, DEHGHANTANHA A, AHMADZADEH M, et al. DRTHIS: Deep Ransomware Threat Hunting and Intelligence System at the Fog Layer[J]. Future Generation Computer Systems, 2019, 90: 94-104. |
| [1] | LIU Qiang, WANG Jian, WANG Yanan, WANG Shan. A Dynamic Malware Detection Method Based on Ensemble Learning [J]. Netinfo Security, 2025, 25(1): 159-172. |
| [2] | XU Ruzhi, ZHANG Ning, LI Min, LI Zixuan. Research on a High Robust Detection Model for Malicious Software [J]. Netinfo Security, 2024, 24(8): 1184-1195. |
| [3] | LI Yixuan, JIA Peng, FAN Ximing, CHEN Chen. Control Flow Transformation Based Adversarial Example Generation for Attacking Malware Detection GNN Model [J]. Netinfo Security, 2024, 24(12): 1896-1910. |
| [4] | HU Wentao, XU Jingkai, DING Weijie. Unsupervised Network Traffic Anomaly Detection Based on Abductive Learning [J]. Netinfo Security, 2024, 24(11): 1675-1684. |
| [5] | ZHU Yixin, MIAO Zhangwang, GAN Jinghong, MA Cunqing. Design of Ransomware Defense System Based on Fine-Grained Access Control Scheme [J]. Netinfo Security, 2023, 23(10): 31-38. |
| [6] | WANG Yu, LYU Liangshuang, XIA Chunhe. A Windows Malware Detection Method Based on Semantic Analysis [J]. Netinfo Security, 2023, 23(10): 58-63. |
| [7] | XU Guotian, LIU Mengmeng. Malware Detection Method Based on Improved Harris Hawks Optimization Synchronization Optimization Feature Selection [J]. Netinfo Security, 2021, 21(12): 9-18. |
| [8] | GUO Chun, CHEN Changqing, SHEN Guowei, JIANG Chaohui. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [9] | LÜ Zongping, ZHAO Chundi, GU Zhaojun, ZHOU Jingxian. Dynamic Detection of Ransomware Based on Stacking Model Fusion [J]. Netinfo Security, 2020, 20(2): 57-57. |
| [10] | XU Guotian, SHEN Yaotong. A Malware Detection Method Based on XGBoost and LightGBM Two-layer Model [J]. Netinfo Security, 2020, 20(12): 54-63. |
| [11] | TAN Yang, LIU Jiayong, ZHANG Lei. Malware Familial Classification of Deep Auto-encoder Based on Mixed Features [J]. Netinfo Security, 2020, 20(12): 72-82. |
| [12] | Xin SONG, Kai ZHAO, Linlin ZHANG, Wenbo FANG. Research on Android Malware Detection Based on Random Forest [J]. Netinfo Security, 2019, 19(9): 1-5. |
| [13] | Ming YIN, Shijie JIA. A Technology to Prevent Ransomware Attacks Based on Solid State Drives in LAN [J]. Netinfo Security, 2019, 19(9): 71-75. |
| [14] | Jian ZHANG, Bohan CHEN, Liangyi GONG, Zhaojun GU. Research on Malware Detection Technology Based on Image Analysis [J]. Netinfo Security, 2019, 19(10): 24-31. |
| [15] | Yunchun LI, Wentao LU, Wei LI. Malware Detection Method Based on Shapelet [J]. Netinfo Security, 2018, 18(3): 70-77. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||