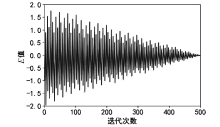
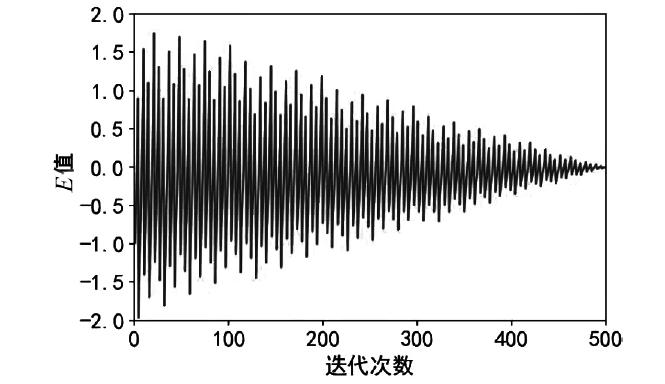
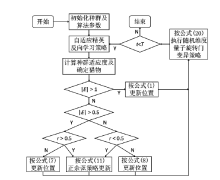
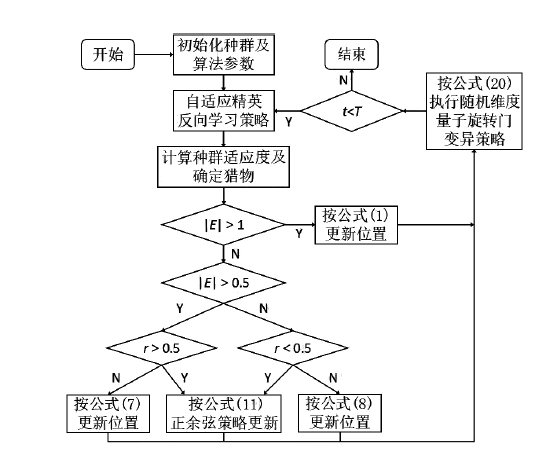
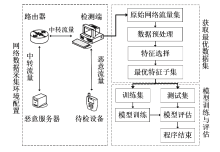
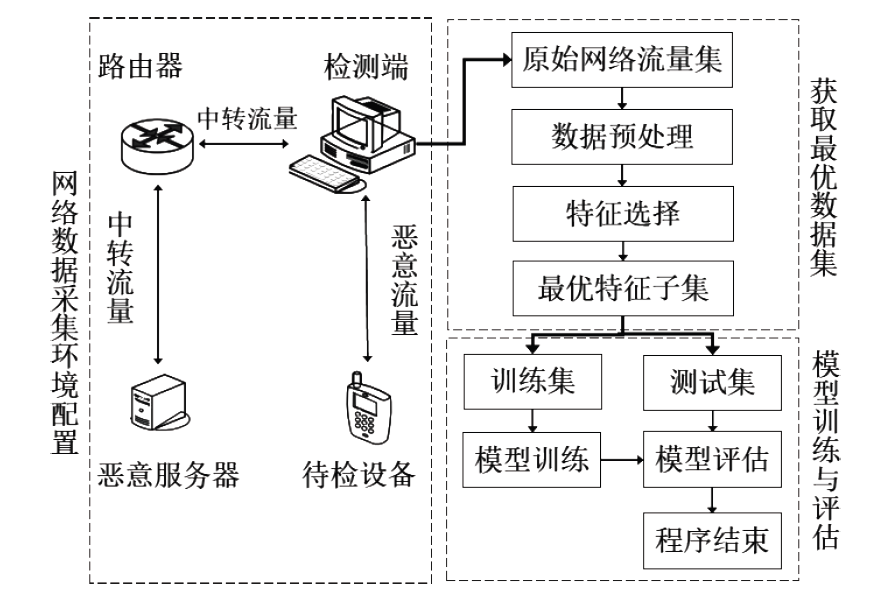
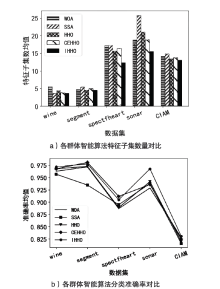
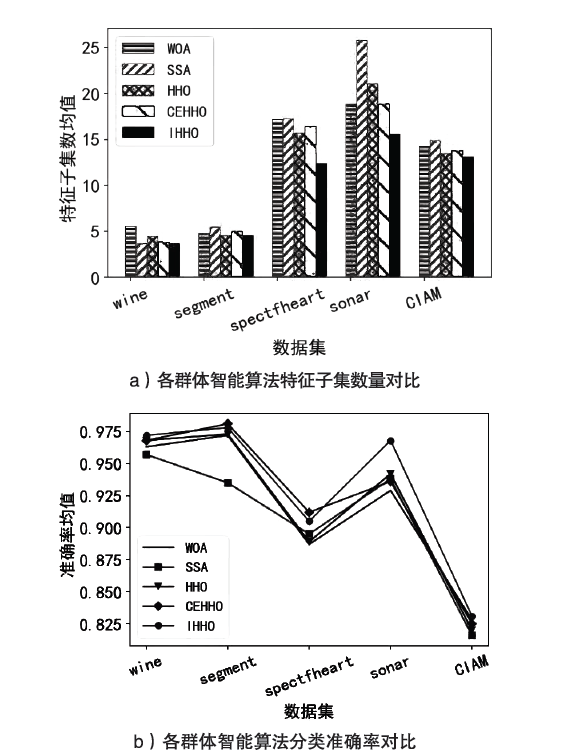
| [1] |
China Internet Network Information Center. The 48th Statistical Report on China’s Internet Development[EB/OL]. http://www.cnnic.net.cn/hlwfzyj/hlwxzbg/hlwtjbg/202109/t20210915_71543.htm, 2021-09-15.
|
|
中国互联网络信息中心. 第48次中国互联网络发展状况统计报告[EB/OL]. http://www.cnnic.net.cn/hlwfzyj/hlwxzbg/hlwtjbg/202109/t20210915_71543.htm, 2021-09-15.
|
| [2] |
LI Wenjia, GE Jigang, DAI Guqian. Detecting Malware for Android Platform: an SVM-based Approach[C]// IEEE. 2015 2nd International Conference on Cyber Security and Cloud Computing, November 3-6, 2015, New Jersey, USA. New York: IEEE, 2016: 464-469.
|
| [3] |
ARP D, SPREITZENBARTH M, HUBNER M, et al. DREBIN: Effective and Explainable Detection of Android Malware in Your Pocket[C]// NDSS. 21st Network and Distributed System Security Symposium, February 23-26, 2014, California, USA. California: NDSS, 2014: 23-26.
|
| [4] |
CHAN P P K, SONG Wenkai. Static Detection of Android Malware by Using Permissions and API calls[C]// IEEE. 2014 International Conference on Machine Learning and Cybernetics, July 13-16, 2014, Lanzhou, China. New York: IEEE, 2014: 82-87.
|
| [5] |
YU Yuaner, ZHANG Linlin, ZHAO Kai, et al. Android Malware Family Classification Method Based on Sensitive Permissions and API[J]. Journal of Zhengzhou University(Natural Science Edition), 2020, 52(3):75-79, 91.
|
|
于媛尔, 张琳琳, 赵楷, 等. 基于敏感权限和API的Android恶意软件家族分类方法[J]. 郑州大学学报(理学版), 2020, 52(3):75-79,91.
|
| [6] |
XIAO Yunchang, SU Haifeng, QIAN Yucun, et al. A Behavior-based Family Clustering Method for Android Malware[J]. Journal of Wuhan University(Natural Science Edition), 2016, 62(5):429-436.
|
|
肖云倡, 苏海峰, 钱雨村, 等. 一种基于行为的Android恶意软件家族聚类方法[J]. 武汉大学学报(理学版), 2016, 62(5):429-436.
|
| [7] |
SARACINO A, SCANDURRA D, DINI G, et al. MADAM: Effective and Efficient Behavior-based Android Malware Detection and Prevention[J]. IEEE Transactions on Dependable and Secure Computing, 2018, 15(1):83-97.
doi: 10.1109/TDSC.2016.2536605
URL
|
| [8] |
HAO Jingwei, PAN Limin, LI Rui. Low Redundancy Feature Selection Method for Android Malware Detection[N]. Journal of Beijing University of Aeronautics and Astronautics, 2021-03-02(3)
|
|
郝靖伟, 潘丽敏, 李蕊. Android恶意软件检测低冗余特征选择方法[N]. 北京航空航天大学学报, 2021-03-02(3).
|
| [9] |
FATIMA A, MAURYA R, DUTTA M K, et al. Android Malware Detection Using Genetic Algorithm Based Optimized Feature Selection and Machine Learning[C]// IEEE. 2019 42nd International Conference on Telecommunications and Signal Processing (TSP), July 1-3, 2019, Budapest, Hungary. New York: IEEE, 2019: 220-223.
|
| [10] |
MOODI M, GHAZVINI M, MOODI H. A Hybrid Intelligent Approach to Detect Android Botnet Using Smart Self-adaptive Learning-based PSO-SVM[J]. Knowledge-Based Systems, 2021, 22(2):831-860.
|
| [11] |
JIA Heming, LI Yao, SUN Kangjian. Simultaneous Feature Selection Optimization Based on Hybrid Sooty Tern Optimization Algorithm and Genetic Algorithm[N]. Acta Automatica Sinica, 2021-09-08(9).
|
|
贾鹤鸣, 李瑶, 孙康健. 基于遗传乌燕鸥算法的同步优化特征选择[N]. 自动化学报, 2021-09-08(9).
|
| [12] |
ALJARAH I, ALA’M A Z, FARIS H, et al. Simultaneous Feature Selection and Support Vector Machine Optimization Using the Grasshopper Optimization Algorithm[J]. Cognitive Computation, 2018, 10(2):478-495.
doi: 10.1007/s12559-017-9542-9
URL
|
| [13] |
ALABERT A, BERTI A, CABALLERO R, et al. No-free-lunch Theorems in the Continuum[J]. Theoretical Computer Science, 2015, 60(2):98-106.
|
| [14] |
JIAO Shan, CHONG Guoshuang, HUANG Changcheng, et al. Orthogonally Adapted Harris Hawks Optimization for Parameter Estimation of Photovoltaic Models[J]. Energy, 2020, 20(3):732-763.
|
| [15] |
QAIS M H, HASANIEN H M, ALGHUWAINEM S. Parameters Extraction of Three-diode Photovoltaic Model Using Computation and Harris Hawks Optimization[J]. Energy, 2020, 19(5):649-670.
|
| [16] |
HEIDARI A A, MIRJALILI S, FARIS H, et al. Harris Hawks Optimization: Algorithm and Applications[J]. Future Generation Computer Systems, 2019, 32(3):849-872.
|
| [17] |
TIZHOOSH H R. Opposition-based Learning: A New Scheme for Machine Intelligence[C]// IEEE. Proceedings of Computational Intelligence for Modelling, November 28-30, 2005, Vienna, Austria. New York: IEEE, 2005: 695-701.
|
| [18] |
TANG Andi, HAN Tong, XU Dengwu, et al. Chaotic elite Harris Hawks Optimization Algorithm[J]. Journal of Computer Applications, 2021, 41(8):2265-2272.
|
|
汤安迪, 韩统, 徐登武, 等. 混沌精英哈里斯鹰优化算法[J]. 计算机应用, 2021, 41(8):2265-2272.
|
| [19] |
TAHERI L, FITRIAH A, LASHKARI A. H. et al. Extensible Android Malware Detection and Family Classification Using Network-flows and API-Calls[C]// IEEE. 53rd International Carnahan Conference on Security Technology, October 1-3, 2019, Chennai, India. New York: IEEE, 2019: 1-8.
|