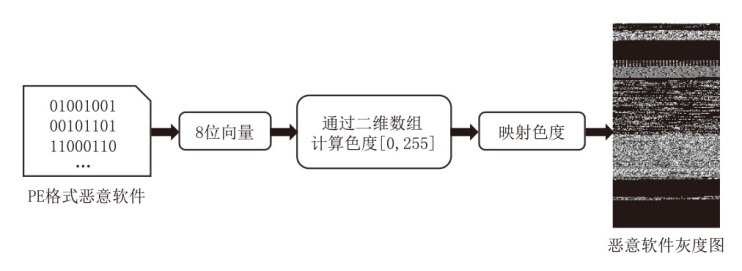
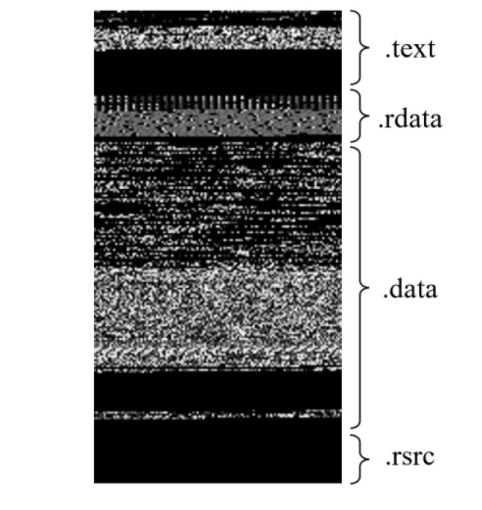
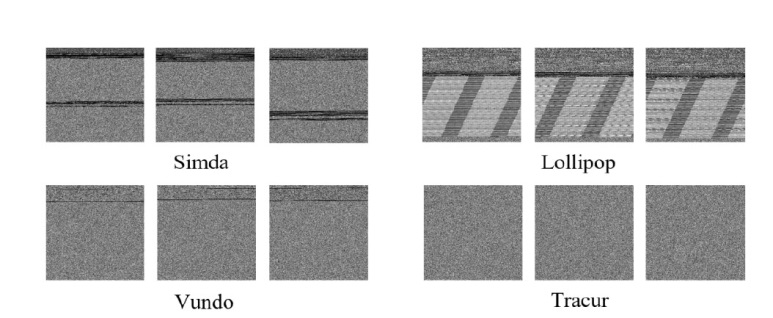
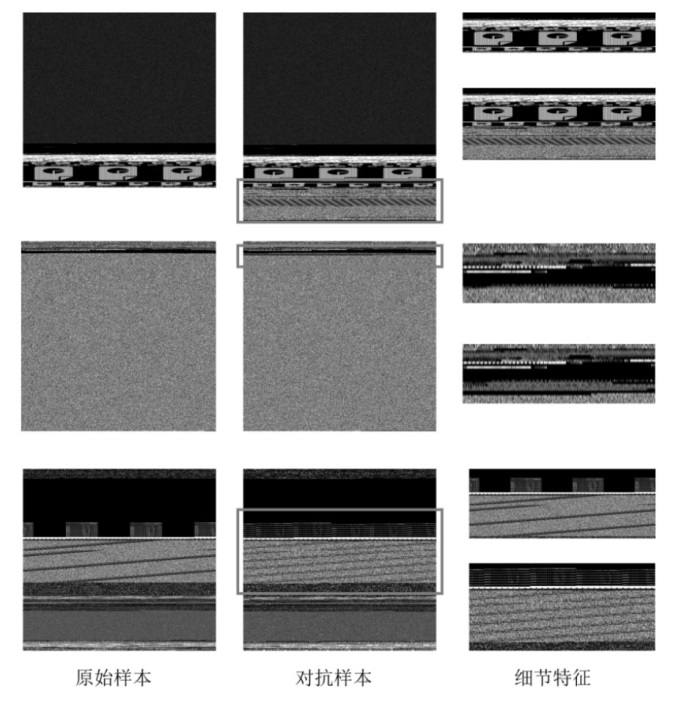
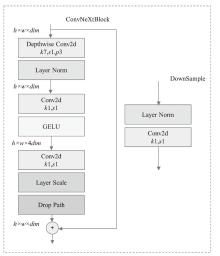
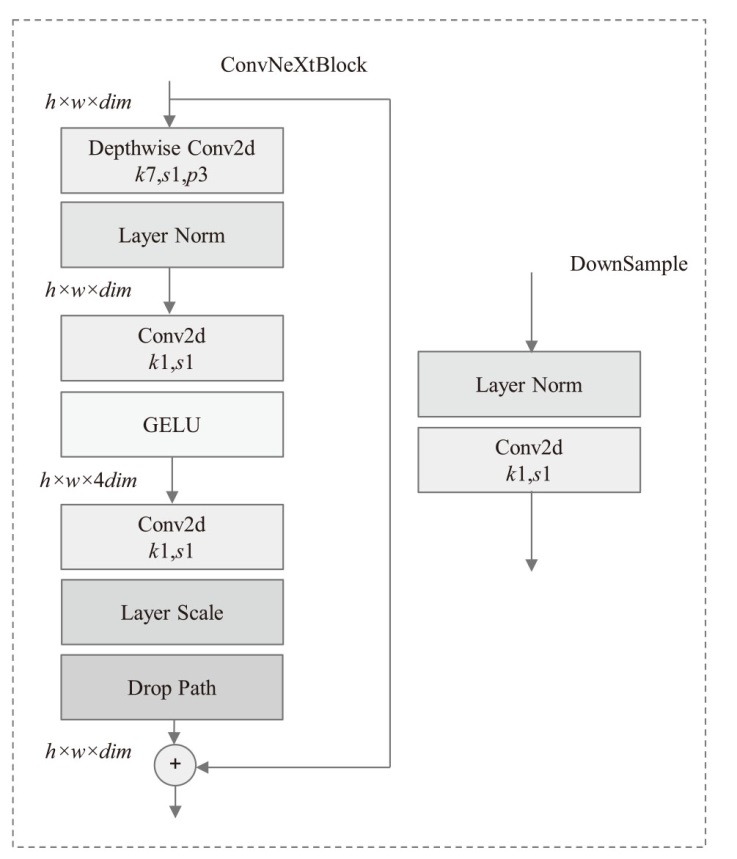
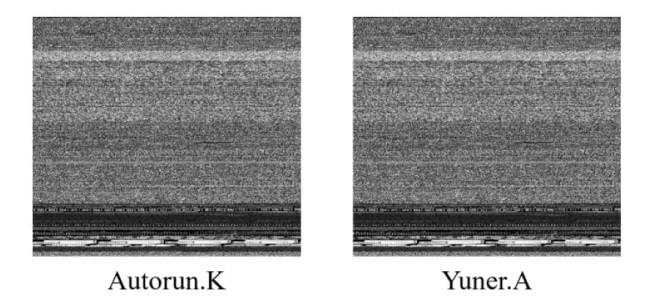
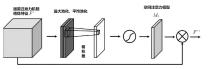
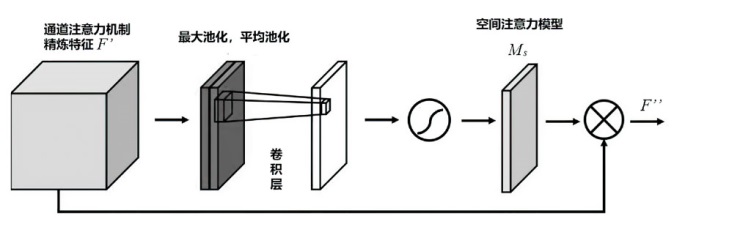
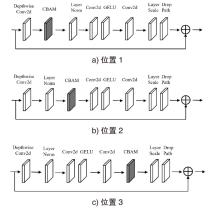
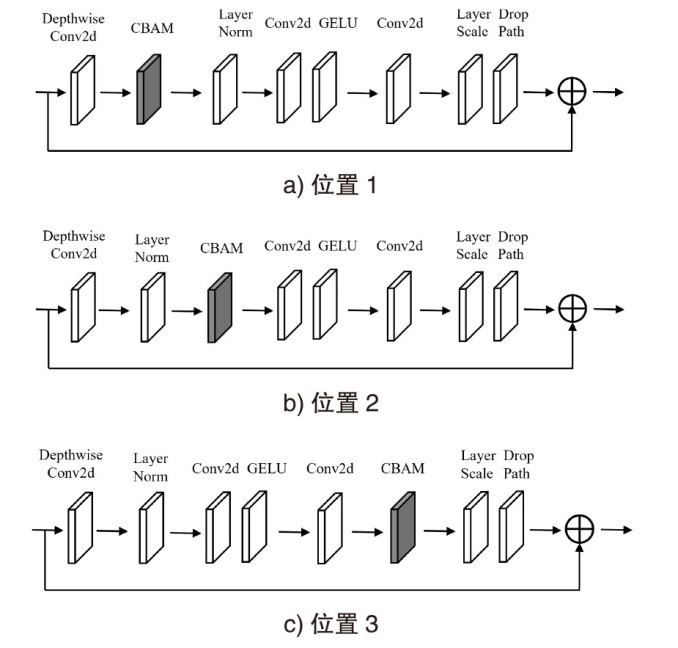
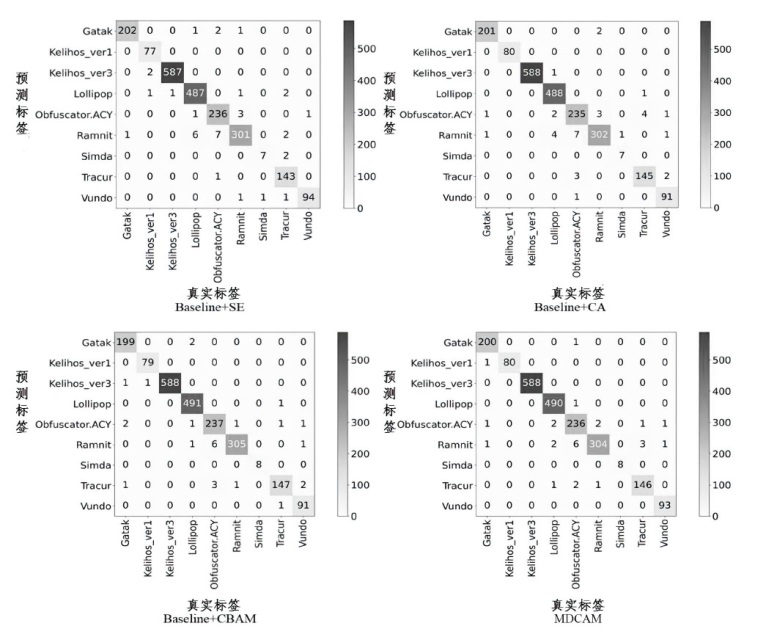
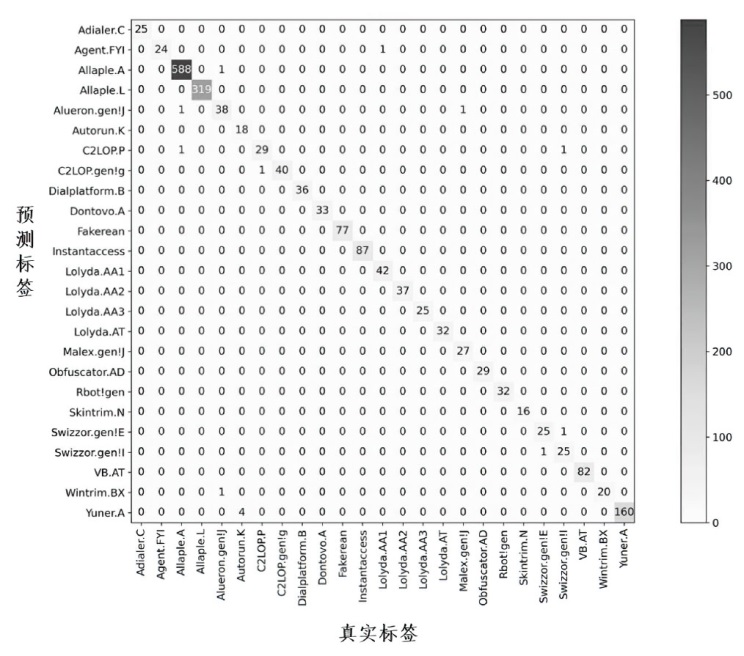
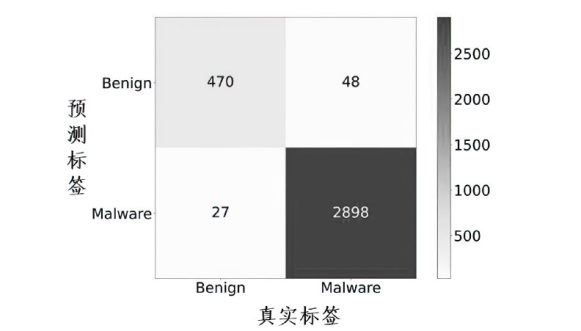
Netinfo Security ›› 2024, Vol. 24 ›› Issue (8): 1184-1195.doi: 10.3969/j.issn.1671-1122.2024.08.005
Previous Articles Next Articles
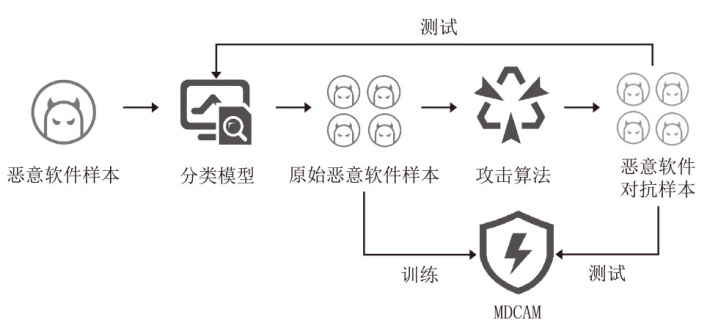
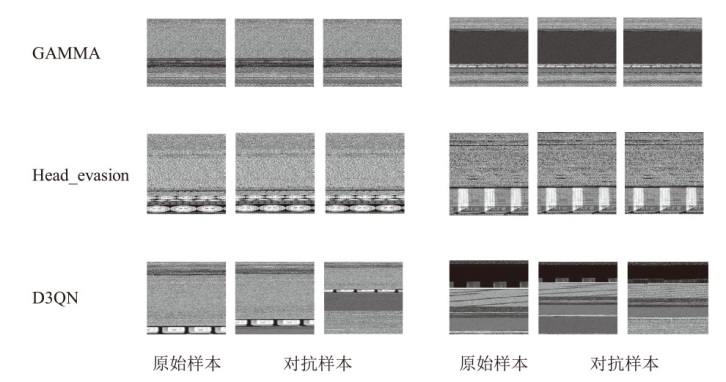
Research on a High Robust Detection Model for Malicious Software
XU Ruzhi, ZHANG Ning( ), LI Min, LI Zixuan
), LI Min, LI Zixuan
- School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
-
Received:2024-05-25Online:2024-08-10Published:2024-08-22
CLC Number:
Cite this article
XU Ruzhi, ZHANG Ning, LI Min, LI Zixuan. Research on a High Robust Detection Model for Malicious Software[J]. Netinfo Security, 2024, 24(8): 1184-1195.
share this article
| 数据集 | 方法 | 精确率 | 召回率 | F1值 | 准确率 |
|---|---|---|---|---|---|
| BIG2015 | IDA+DRBA | 93.28% | 93.54% | 93.41% | 93.40% |
| Deam+DenseNet | 95.30% | 95.40% | 95.40% | 97.30% | |
| DenseNet-based | 98.46% | 98.58% | 97.84% | 98.21% | |
| ALexNet | 97.53% | 92.42% | 94.91% | 96.64% | |
| VGG16 | 96.34% | 93.47% | 94.88% | 96.04% | |
| ResNet50 | 98.10% | 92.10% | 95.01% | 98.07% | |
| GoogleNet | 96.38% | 91.02% | 93.62% | 95.37% | |
| SwinTransformer | 93.37% | 95.66% | 94.50% | 97.28% | |
| MDCAM(本文) | 98.71% | 98.62% | 98.67% | 98.76% | |
| Malimg | GIST+SVM | 92.50% | 91.40% | 91.95% | 92.20% |
| GIST+KNN | 92.10% | 91.70% | 91.90% | 91.90% | |
| IDA+DRBA | 94.60% | 94.50% | 94.55% | 94.50% | |
| NSGA-II | 97.60% | 88.40% | 92.77% | 97.60% | |
| Deam+DenseNet | 96.90% | 96.60% | 96.70% | 98.50% | |
| DenseNet-based | 98.23% | 97.78% | 97.92% | 97.85% | |
| ALexNet | 97.80% | 98.80% | 97.80% | 97.80% | |
| VGG16 | 96.16% | 96.23% | 96.19% | 96.22% | |
| ResNet50 | 93.49% | 93.76% | 93.62% | 97.82% | |
| GoogleNet | 96.95% | 96.81% | 96.66% | 96.44% | |
| SwinTransformer | 92.64% | 92.24% | 92.44% | 95.37% | |
| MDCAM(本文) | 98.68% | 98.25% | 98.42% | 98.90% | |
| Leopard Mobile | ALexNet | 90.82% | 94.38% | 92.57% | 96.14% |
| VGG16 | 91.33% | 94.78% | 93.03% | 96.37% | |
| ResNet50 | 93.90% | 96.40% | 95.05% | 97.50% | |
| GoogleNet | 92.42% | 95.96% | 94.16% | 96.95% | |
| SwinTransformer | 83.30% | 74.60% | 77.95% | 90.50% | |
| MDCAM(本文) | 94.91% | 96.47% | 95.68% | 97.82% |
| [1] | AV-TEST. Malware Statistics & Trends Report[EB/OL]. (2024-05-01)[2024-05-20]. https://www.av-test.org/en/statistics/malware/. |
| [2] | GLOBAL STATS. Desktop Operating System Market Share Worldwide[EB/OL]. (2024-05-04)[2024-05-20]. https://gs.statcounter.com/os-market-share/desktop/worldwide. |
| [3] | CNCERT/CC. 2020 China Internet Cyber Security Report[EB/OL]. (2021-07-21)[2024-05-12]. https://www.cert.org.cn/publish/main/46/2021/20210721130944504525772/20210721130944504525772_.html, 2020 |
| 国家计算机网络应急技术处理协调中心. 2020年中国互联网网络安全报告[EB/OL]. (2021-07-21)[2024-05-12]. https://www.cert.org.cn/publish/main/46/2021/20210721130944504525772/20210721130944504525772_.html, 2020 | |
| [4] | SHU Longhui, DONG Shi, SU Huadong, et al. Android Malware Detection Methods Based on Convolutional Neural Network: A Survey[J]. IEEE Transactions on Emerging Topics in Computational Intelligence, 2023, 7(5): 1330-1350. |
| [5] | KOLOSNJAJI B, ZARRAS A, WEBSTER G, et al. Deep Learning for Classification of Malware System Call Sequences[C]// Australasian AI Community. Australasian Joint Conference on Artificial Intelligence. Hobart: Australasian AI Community, 2016: 137-149. |
| [6] | RAFF E, BARKER J, SYLVESTER J, et al. Malware Detection by Eating a Whole EXE[C]// AAAI. Workshops at the Thirty-Second AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2018: 268-276. |
| [7] | GIBERT D, MATEU C, PLANES J. The Rise of Machine Learning for Detection and Classification of Malware: Research Developments, Trends and Challenges[J]. Journal of Network and Computer Applications, 2020, 153: 102526-102530. |
| [8] | GOODFELLOW I J, SHLENS J, SZEGEDY C. Explaining and Harnessing Adversarial Examples[EB/OL]. (2014-12-20)[2024-03-15]. https://arxiv.org/abs/1412.6572. |
| [9] | CASTRO R L, SCHMITT C, DREO G. Aimed: Evolving Malware with Genetic Programming to Evade Detection[C]// IEEE. 18th IEEE International Conference on Trust, Security And Privacy in Computing and Communications/13th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE). New York: IEEE, 2019: 240-247. |
| [10] | BERNARDI M L, CIMITILE M, DISTANTE D, et al. Dynamic Malware Detection and Phylogeny Analysis Using Process Mining[J]. International Journal of Information Security, 2019, 18(3): 257-284. |
| [11] | DAVID B, FILIOL E, GALLIENNE K. Structural Analysis of Binary Executable Headers for Malware Detection Optimization[J]. Journal of Computer Virology and Hacking Techniques, 2017, 13(2): 87-93. |
| [12] | KIRAT D, VIGNA G. Malgene: Automatic Extraction of Malware Analysis Evasion Signature[C]// ACM. Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security (CCS). New York: ACM, 2015: 769-780. |
| [13] | SCHULTZ M G, ESKIN E, ZADOK F, et al. Data Mining Methods for Detection of New Malicious Executables[C]// IEEE. Proceedings of 2001 IEEE Symposium on Security and Privacy. New York: IEEE, 2000: 38-49. |
| [14] | MOSKOVITCH R, STOPEL D, FEHER C, et al. Unknown Malcode Detection via Text Categorization and the Imbalance Problem[C]// IEEE. 2008 IEEE International Conference on Intelligence and Security Informatics. New York: IEEE, 2008: 156-161. |
| [15] | GALAL H S, MAHDY Y B, ATIEA M A. Behavior-Based Features Model for Malware Detection[J]. Journal of Computer Virology and Hacking Techniques, 2016, 12(2): 59-67. |
| [16] | RABADI D, TEO S G. Advanced Windows Methods on Malware Detection and Classification[C]// IEEE. Annual Computer Security Applications Conference (ACSAC). New York: IEEE, 2020: 54-68. |
| [17] | ZHANG Zhaoqi, QI Panpan, WANG Wei. Dynamic Malware Analysis with Feature Engineering and Feature Learning[C]// AAAI. Proceedings of the AAAI Conference on Artificial Intelligence (AAAI). Menlo Park: AAAI, 2020, 34(1): 1210-1217. |
| [18] | RAGHURAMAN C, SURESH S, SHIVSHANKAR S, et al. Static and Dynamic Malware Analysis Using Machine Learning[C]// Springer. Proceedings of the First International Conference on Sustainable Technologies for Computational Intelligence. Heidelberg: Springer, 2020: 793-806. |
| [19] | ANDERSON H S, ROTH P. Ember: An Open Dataset for Training Static Pe Malware Machine Learning Models[EB/OL]. (2018-04-12)[2024-05-07]. https://arxiv.org/abs/1804.04637. |
| [20] | SAXE J, BERLIN K. Deep Neural Network Based Malware Detection Using Two Dimensional Binary Program Features[C]// IEEE. 2015 10th International Conference on Malicious and Unwanted Software (MALWARE). New York: IEEE, 2015, 20: 11-20. |
| [21] | ATHIWARATKUN B, STOKES J W. Malware Classification with LSTM and GRU Language Models and a Character-Level CNN[C]// IEEE. 2017 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP). New York: IEEE, 2017: 2482-2486. |
| [22] | DONG Shi, SHU Longhui, NIE Shan. Android Malware Detection Method Based on CNN and DNN Bybrid Mechanism[J]. IEEE Transactions on Industrial Informatics, 2024, 20(5): 7744-7753. |
| [23] | NAEEM H, CHENG Xiaochun, ULLAH F, et al. A Deep Convolutional Neural Network Stacked Ensemble for Malware Threat Classification in Internet of Things[J]. Journal of Circuits, Systems and Computers, 2022, 31(17): 1-21. |
| [24] | NAEEM H, DONG Shi, FALANA O J, et al. Development of a Deep Stacked Ensemble with Process Based Volatile Memory Forensics for Platform Independent Malware Detection and Classification[J]. Expert Systems with Applications, 2023, 223: 119952-119957. |
| [25] | HEMALATHA J, ROSELINE S A, GEETHA S, et al. An Efficient Densenet-Based Deep Learning Model for Malware Detection[J]. Entropy, 2021, 23(3): 344-345. |
| [26] | WANG Changguang, ZHAO Ziqiu, WANG Fangwei, et al. A Novel Malware Detection and Family Classification Scheme for IoT Based on DEAM and DenseNet[J]. Security and Communication Networks, 2021, 2021(11): 1-16. |
| [27] | LIU Zhuang, MAO Hanzi, WU C Y, et al. A Convnet for the 2020s[C]// IEEE. Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2022: 11976-11986 |
| [28] | WOO S, PARK J, LEE J Y, et al. Cbam: Convolutional Block Attention Module[C]// Springer. Proceedings of the European Conference on Computer Vision (ECCV). Heiderberg: Springer, 2018: 3-19. |
| [29] | LIN T Y, GOYAL P, GIRSHICK R, et al. Focal Loss for Dense Object Detection[C]// IEEE. Proceedings of the IEEE International Conference on Computer Vision. New York: IEEE, 2017: 2980-2988. |
| [30] | HU Jie, SHEN Li, SUN Gang. Squeeze-and-Excitation Networks[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2018: 7132-7141. |
| [31] | HOU Qibin, ZHOU Daquan, FENG Jieshi. Coordinate Attention for Efficient Mobile Network Design[C]// IEEE. Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2021: 13713-13722. |
| [32] | RAFF E, BARKER J, SYLVESTER J, et al. Malware Detection by Eating a Whole Exe[C]// AAAI. Workshops at the Thirty-Second AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2018: 268-276. |
| [33] | DEMETRIO L, BIGGIO B, LAGORIO G, et al. Functionality-Preserving Black-Box Optimization of Adversarial Windows Malware[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 3469-3478. |
| [34] | NISI D, GRAZIANO M, FRATANTONIO Y, et al. Lost in the Loader: The Many Faces of the Windows PE File Format[C]// ACM. Proceedings of the 24th International Symposium on Research in Attacks, Intrusions and Defenses. New York: ACM, 2021: 177-192. |
| [35] | ANDERSON H S, ROTH P. Ember: An Open Dataset for Training Static Pe Malware Machine Learning Models[EB/OL]. (2018-04-12)[2024-05-07]. https://arxiv.org/abs/1804.04637. |
| [1] | TIAN Zhao, NIU Yajie, SHE Wei, LIU Wei. A Reputation Evaluation Method for Vehicle Nodes in V2X [J]. Netinfo Security, 2024, 24(5): 719-731. |
| [2] | ZHANG Guanghua, LIU Yichun, WANG He, HU Boning. Defense Scheme for Removing Deep Neural Network Backdoors Based on JSMA Adversarial Attacks [J]. Netinfo Security, 2024, 24(4): 545-554. |
| [3] | XU Zirong, GUO Yanping, YAN Qiao. Malicious Software Adversarial Defense Model Based on Feature Severity Ranking [J]. Netinfo Security, 2024, 24(4): 640-649. |
| [4] | YANG Zhipeng, LIU Daidong, YUAN Junyi, WEI Songjie. Research on Network Local Security Situation Fusion Method Based on Self-Attention Mechanism [J]. Netinfo Security, 2024, 24(3): 398-410. |
| [5] | JIANG Rong, LIU Haitian, LIU Cong. Unsupervised Network Intrusion Detection Method Based on Ensemble Learning [J]. Netinfo Security, 2024, 24(3): 411-426. |
| [6] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [7] | ZHAO Pengcheng, YU Junqing, LI Dong. An Optimal Algorithm for Traffic Scheduling in SRv6 Network Based on Deep Learning [J]. Netinfo Security, 2024, 24(2): 272-281. |
| [8] | JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference [J]. Netinfo Security, 2024, 24(2): 293-302. |
| [9] | XUE Yu, ZHANG Yixuan. Survey on Deep Neural Architecture Search [J]. Netinfo Security, 2023, 23(9): 58-74. |
| [10] | SHEN Hua, TIAN Chen, GUO Sensen, MU Zhiying. Research on Adversarial Machine Learning-Based Network Intrusion Detection Method [J]. Netinfo Security, 2023, 23(8): 66-75. |
| [11] | LI Chenwei, ZHANG Hengwei, GAO Wei, YANG Bo. Transferable Image Adversarial Attack Method with AdaN Adaptive Gradient Optimizer [J]. Netinfo Security, 2023, 23(7): 64-73. |
| [12] | LIU Yuxiao, CHEN Wei, ZHANG Tianyue, WU Lifa. Explainable Anomaly Traffic Detection Based on Sparse Autoencoders [J]. Netinfo Security, 2023, 23(7): 74-85. |
| [13] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [14] | ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning [J]. Netinfo Security, 2023, 23(4): 20-29. |
| [15] | TAN Liuyan, RUAN Shuhua, YANG Min, CHEN Xingshu. Educational Data Classification Based on Deep Learning [J]. Netinfo Security, 2023, 23(3): 96-102. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||