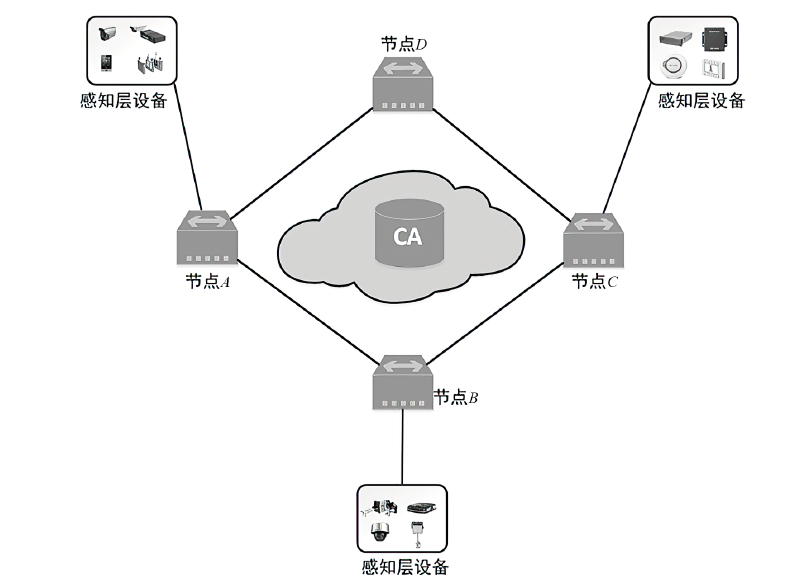
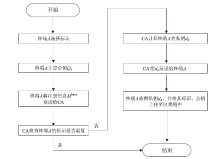
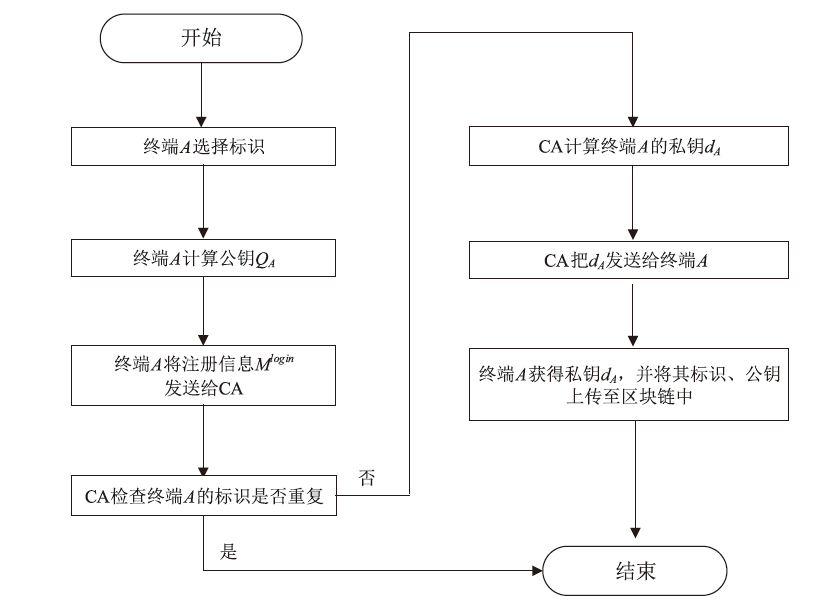
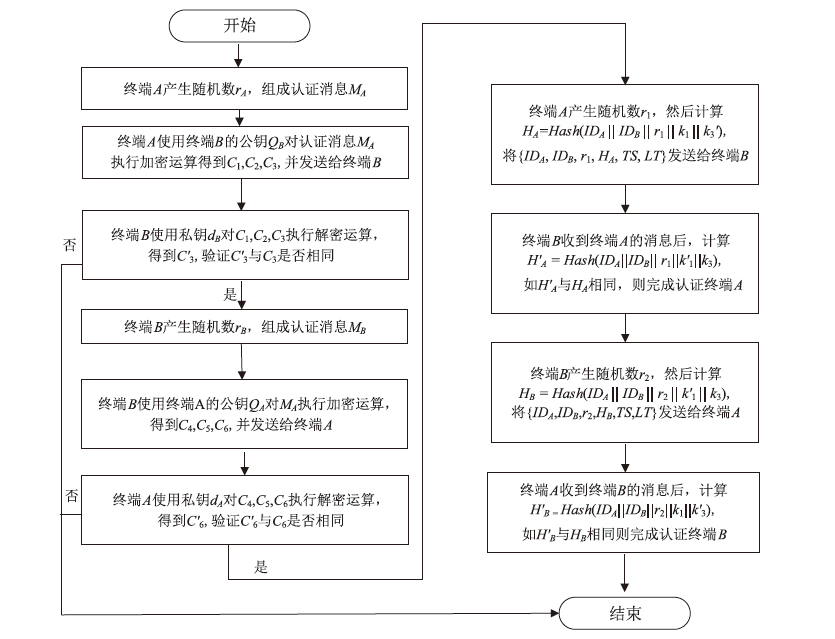
Netinfo Security ›› 2024, Vol. 24 ›› Issue (2): 179-187.doi: 10.3969/j.issn.1671-1122.2024.02.002
Previous Articles Next Articles
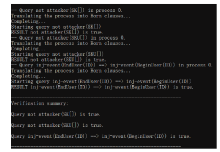
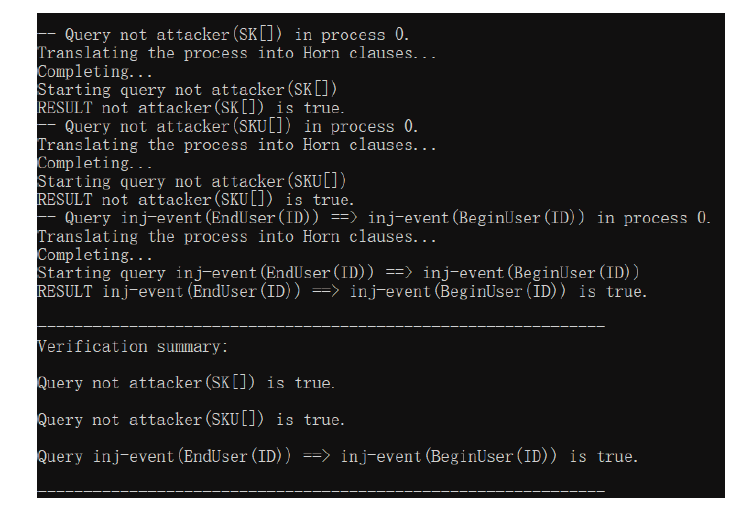
An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment
ZHAI Peng1,2, HE Jingsha1,2( ), ZHANG Yu2
), ZHANG Yu2
- 1. Faculty of Information Technology, Beijing University of Technology, Beijing 100124, China
2. School of Computer Science and Engineering, Jining University, Jining 273100, China
-
Received:2023-02-27Online:2024-02-10Published:2024-03-06 -
Contact:HE Jingsha E-mail:jhe@bjut.edu.cn
CLC Number:
Cite this article
ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment[J]. Netinfo Security, 2024, 24(2): 179-187.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.02.002
| 符号 | 符号含义 | 符号 | 符号含义 |
|---|---|---|---|
素数 | 终端A的标识 | ||
| 终端B的标识 | |||
| 终端A的公钥 | |||
| KGC | 标识密码认证机构的密钥 生成中心 | 终端A的私钥 | |
| 密钥派生函数 | 终端B的公钥 | ||
| 密钥派生函数生成的字符串 | 终端B的私钥 | ||
| CA | 标识密码认证机构 | 随机数 | |
| 私钥生成函数识别符 | 时间戳 | ||
| 标识密码认证机构服务器的标识 | 生存时间 | ||
| 标识密码认证机构服务器的主公钥 | 用密钥 | ||
| 标识密码认证机构服务器的主私钥 | 用密钥 |
| 模型 | 抵御 重放攻击 | 抵御 篡改攻击 | 抵御 串谋攻击 | 抵御 仿冒攻击 | 抵御 中间人 攻击 | 抵御拒 绝服务 攻击 | 前向 安全 |
|---|---|---|---|---|---|---|---|
| 文献[ | No | No | Yes | Yes | No | Yes | Yes |
| 文献[ | Yes | Yes | Yes | No | Yes | Yes | No |
| 文献[ | Yes | No | No | Yes | Yes | No | Yes |
| 文献[ | Yes | No | No | Yes | No | No | Yes |
| 文献[ | No | No | No | Yes | No | No | Yes |
| 文献[ | Yes | Yes | Yes | No | Yes | Yes | No |
| 文献[ | Yes | No | No | No | No | No | Yes |
| 文献[ | No | No | Yes | No | Yes | Yes | Yes |
| 本文 | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| [1] | PORAMBAGE P, KUMAR P, SCHMITT C, et al. Certificate-Based Pairwise Key Establishment Protocol for Wireless Sensor Networks[C]// IEEE. 2013 IEEE 16th International Conference on Computational Science and Engineering. New York: IEEE, 2013: 667-674. |
| [2] | DIAZ-SANCHEZ D, MARIN-LOPEZ A, ALMENAREZ F. TLS/PKI Challenges and Certificate Pinning Techniques for IoT and M2M Secure Communications[C]// IEEE. IEEE Communications Surveys & Tutorials. New York: IEEE, 2019: 3502-3531. |
| [3] |
KUMAR P, GURTOV A, IINATTI J, et al. Lightweight and Secure Session-Key Establishment Scheme in Smart Home Environments[J]. IEEE Sensors Journal, 2016, 16(1): 254-264.
doi: 10.1109/JSEN.2015.2475298 URL |
| [4] | GE Chunpeng, XIA Jinyue, FANG Liming. Key-Private Identity-Based Proxy Re-Encryption[J]. Cmc-Computers Materials & Continua, 2020, 63(2): 633-647. |
| [5] |
RIVEST R L, SHAMIR A, ADLEMAN L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems[J]. Communications of the ACM, 1978, 21(2): 120-126.
doi: 10.1145/359340.359342 URL |
| [6] |
CHENG Xu, ZHANG Ziyang, CHEN Fulong, et al. Secure Identity Authentication of Community Medical Internet of Things[J]. IEEE Access, 2019, 7: 115966-115977.
doi: 10.1109/ACCESS.2019.2935782 |
| [7] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. Workshop on the Theory and Application of Cryptographic Techniques. Heidelberg: Springer, 1984: 47-53. |
| [8] |
XIAO Hao, WEI Ren, FEI Yangyang, et al. A Blockchain-Based Cross-Domain and Autonomous Access Control Scheme for Internet of Things[J]. IEEE Transactions on Services Computing, 2023, 16(2): 773-786.
doi: 10.1109/TSC.2022.3179727 URL |
| [9] | XIE Yong, XU Fang, LI Xiang, et al. EIAS: An Efficient Identity-Based Aggregate Signature Scheme for WSNs against Coalition Attack[J]. Cmc-Computers Materials & Continua, 2019, 59(3): 903-924. |
| [10] | YAN Hongyang, WANG Yu, JIA Chunfu, et al. IoT-FBAC: Function-Based Access Control Scheme Using Identity-Based Encryption in IoT[J]. Future Generation Computer Systems-the International Journal of Escience, 2019, 95: 344-353. |
| [11] | SIDDHARTHA V G, KANSAL L. A Lightweight Authentication Protocol Using Implicit Certificates for Securing IoT Systems[J]. Procedia Computer Science, 2020, 16(7): 9-17. |
| [12] | CUI Zhihua, XUE Fei, ZHANG Shiqiang, et al. A Hybrid BlockChain-Based Identity Authentication Scheme for Multi-WSN[J]. IEEE Transactions on Services Computing, 2020, 13(2): 241-251. |
| [13] |
PUTRA G, DEDEOGLU V, KANHERE S, et al. Trust-Based Blockchain Authorization for IoT[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1646-1658.
doi: 10.1109/TNSM.2021.3077276 URL |
| [14] |
CHENG Guanjie, CHEN Yan, DENG Shuiguang, et al. A Blockchain-Based Mutual Authentication Scheme for Collaborative Edge Computing[J]. IEEE Transactions on Computational Social Systems, 2022, 9(1): 146-158.
doi: 10.1109/TCSS.2021.3056540 URL |
| [15] |
XUE Kaiping, LUO Xinyi, MA Yongjin, et al. A Distributed Authentication Scheme Based on Smart Contract for Roaming Service in Mobile Vehicular Networks[J]. IEEE Transactions on Vehicular Technology, 2022, 71(5): 5284-5297.
doi: 10.1109/TVT.2022.3148303 URL |
| [16] | GU Pengpeng, CHEN Liquan. An Efficient Blockchain-Based Cross-Domain Authentication and Secure Certificate Revocation Scheme[C]// IEEE. 2020 IEEE 6th International Conference on Computer and Communications (ICCC). New York:IEEE, 2020: 1776-1782. |
| [17] | LAI Jianchang, HUANG Xinyi, HE Debiao, et al. Security Analysis of SM9 Digital Signature and Key Encapsulation[J]. Science China: Information, 2021, 51(11): 1900-1913. |
| 赖建昌, 黄欣沂, 何德彪, 等. 国密 SM9 数字签名和密钥封装算法的安全性分析[J]. 中国科学:信息科学, 2021, 51(11): 1900-1913. | |
| [18] | YANG Yatao, ZHANG Xiaowei, YUAN Zheng. Privacy Preserving Scheme in Block Chain with Provably Secure Based on SM9 Algorithm[J]. Journal of Software, 2019, 30(6): 1692−1704. |
| 杨亚涛, 张筱薇, 袁征. 基于SM9算法可证明安全的区块链隐私保护方案[J]. 软件学报, 2019, 30(6): 1692-1704. | |
| [19] | YUAN Feng, CHENG Chaohui. Overview on SM9 Identity-Based Cryptographic Algorithm[J]. Journal of Information Security Research. 2016, 2(11): 18-27. |
| 袁峰, 程朝辉. SM9标识密码算法综述[J]. 信息安全研究, 2016, 2(11): 18-27. | |
| [20] | PENG Cong, HE Debiao, LUO Min. An Identity-Based Ring Signature Scheme for SM9 Algorithm[J]. Journal of Cryptologic Research, 2021, 8(4): 724-734. |
| 彭聪, 何德彪, 罗敏. 基于SM9标识密码算法的环签名方案[J]. 密码学报, 2021, 8(4): 724-734. | |
| [21] | ZHANG Xiaoshuai, LIU Chao, CHAI K, et al. A Privacy-Preserving Consensus Mechanism for an Electric Vehicle Charging Scheme[J]. Journal of Network and Computer Applications, 2021, 174: 161-174. |
| [22] | LI Yue. Design of a Key Establishment Protocol for Smart Home Energy Management System[C]// IEEE. 2013 Fifth International Conference on Computational Intelligence, Communication Systems and Networks. New York: IEEE, 2013: 88-93. |
| [23] | BINOD V D M, HUSSEIN T, MOUFTAH. Device Authentication Mechanism for Smart Energy Home Area Networks[C]// IEEE. 2011 IEEE International Conference on Consumer Electronics (ICCE). New York:IEEE, 2011: 787-788. |
| [24] | SCIANCALEPORE S, PIRO G, BOGGIA G, et al. Public Key Authentication and Key Agreement in IoT Devices with Minimal Airtime Consumption[C]// IEEE. IEEE Embedded Systems Letters. New York: IEEE, 2017: 1-4. |
| [25] |
HAN K, KIM J, SHON T, et al. A Novel Secure Key Paring Protocol for RF4CE Ubiquitous Smart Home Systems[J]. Personal and Ubiquitous Computing, 2012, 17(5): 945-965.
doi: 10.1007/s00779-012-0541-2 URL |
| [26] | HOSSAIN M, NOOR S, HASAN R. HSC-IoT: A Hardware and Software Co-Verification Based Authentication Scheme for Internet of Things[C]// IEEE. 2017 5th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud). New York:IEEE, 2017: 212-219. |
| [27] |
KUMAR P, BRAEKEN A, GURTOV A, et al. Anonymous Secure Framework in Connected Smart Home Environments[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(4): 968-979.
doi: 10.1109/TIFS.2016.2647225 URL |
| [28] | PATEL S P D R, NAVIK A P. Energy Efficient Integrated Authentication and Access Control Mechanisms for Internet of Things[C]// IEEE. 2016 International Conference on Internet of Things and Applications (IOTA). New York:IEEE, 2016: 304-319. |
| [1] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [2] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| [3] | WU Haotian, LI Yifan, CUI Hongyan, DONG Lin. Federated Learning Incentive Scheme Based on Zero-Knowledge Proofs and Blockchain [J]. Netinfo Security, 2024, 24(1): 1-13. |
| [4] | WANG Junyan, YI Peng, JIA Hongyong, ZHANG Jianhui. IoT Terminal Risk Assessment Model Based on Improved CAE [J]. Netinfo Security, 2024, 24(1): 150-159. |
| [5] | ZHU Guocheng, HE Debiao, AN Haoyang, PENG Cong. The Proxy Voting Scheme Based on the Blockchain and SM9 Digital Signature [J]. Netinfo Security, 2024, 24(1): 36-47. |
| [6] | GONG Pengfei, XIE Sijiang, CHENG Andong. The Multi-Leader Consensus Algorithm Based on Improvements to HotStuff [J]. Netinfo Security, 2023, 23(9): 108-117. |
| [7] | ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption [J]. Netinfo Security, 2023, 23(9): 37-46. |
| [8] | ZHAO Jiahao, JIANG Jiajia, ZHANG Yushu. Cross-Chain Data Consistency Verification Model Based on Dynamic Merkle Hash Tree [J]. Netinfo Security, 2023, 23(9): 95-107. |
| [9] | SHAO Zhenzhe, JIANG Jiajia, ZHAO Jiahao, ZHANG Yushu. An Improved Weighted Byzantine Fault Tolerance Algorithm for Cross-Chain System [J]. Netinfo Security, 2023, 23(8): 109-120. |
| [10] | ZHANG Wei, LI Zixuan, XU Xiaoyu, HUANG Haiping. SDP-CoAP: Design of Security Enhanced CoAP Communication Framework Based on Software Defined Perimeter [J]. Netinfo Security, 2023, 23(8): 17-31. |
| [11] | QIN Sihang, DAI Weiqi, ZENG Haiyan, GU Xianjun. Secure Sharing of Power Application Data Based on Blockchain [J]. Netinfo Security, 2023, 23(8): 52-65. |
| [12] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [13] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| [14] | LI Zhihua, WANG Zhihao. IoT Device Identification Method Based on LCNN and LSTM Hybrid Structure [J]. Netinfo Security, 2023, 23(6): 43-54. |
| [15] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||