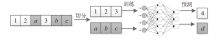
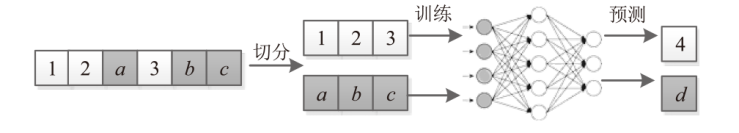
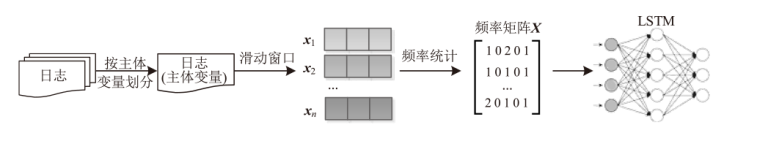
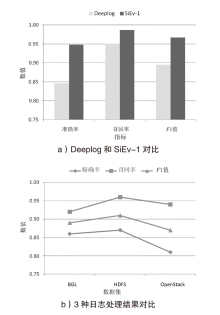
| [1] |
HE Shilin, HE Pinjia, CHEN Zhuangbin, et al. A Survey on Automated Log Analysis for Reliability Engineering[J]. ACM Computing Surveys (CSUR), 2021, 54(6): 1-37.
|
| [2] |
OLINER A, GANAPATHI A, XU Wei. Advances and Challenges in Log Analysis[J]. Communications of the ACM, 2012, 55(2): 55-61.
|
| [3] |
LIAO H J, LIN C H R, LIN Y C, et al. Intrusion Detection System: A Comprehensive Review[J]. Journal of Network and Computer Applications, 2013, 36(1): 16-24.
doi: 10.1016/j.jnca.2012.09.004
URL
|
| [4] |
LANDAUER M, SKOPIK F, WURZENBERGER M, et al. System Log Clustering Approaches for Cyber Security Applications: A Survey[EB/OL]. (2020-05-01) [2023-05-30]. https://www.sciencedirect.com/science/article/pii/S0167404820300250.
|
| [5] |
HE Shilin, ZHU Jieming, HE Pinjia, et al. Experience Report: System Log Analysis for Anomaly Detection[C]// IEEE. 2016 IEEE 27th International Symposium on Software Reliability Engineering (ISSRE). New York: IEEE, 2016: 207-218.
|
| [6] |
KRUEGEL C, VIGNA G. Anomaly Detection of Web-Based Attacks[C]// ACM. Proceedings of the 10th ACM Conference on Computer and Communications Security. New York: ACM, 2003: 251-261.
|
| [7] |
LANDAUER M, WURZENBERGER M, SKOPIK F, et al. Dynamic Log File Analysis: An Unsupervised Cluster Evolution Approach for Anomaly Detection[J]. Computers & Security, 2018(79): 94-116.
|
| [8] |
DU Min, LI Feifei, ZHENG Guineng, et al. Deeplog: Anomaly Detection and Diagnosis from System Logs Through Deep Learning[C]// ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 1285-1298.
|
| [9] |
MENG Weibin, LIU Ying, ZHU Yichen, et al. LogAnomaly: Unsupervised Detection of Sequential and Quantitative Anomalies in Unstructured Logs[C]// ACM. Proceedings of the 28th International Joint Conference on Artificial Intelligence (IJCAI). New York: ACM, 2019: 4739-4745.
|
| [10] |
YANG Ruipeng, QU Dan, GAO Ying, et al. nLSALog: An Anomaly Detection Framework for Log Sequence in Security Management[J]. IEEE Access, 2019(7): 181152-181164.
|
| [11] |
ZHU Bei, LI Jing, GU Rongbin, et al. An Approach to Cloud Platform Log Anomaly Detection Based on Natural Language Processing and LSTM[C]// ACM. 2020 3rd International Conference on Algorithms, Computing and Artificial Intelligence. New York: ACM, 2020: 1-7.
|
| [12] |
LANDAUER M, ONDER S, SKOPIK F, et al. Deep Learning for Anomaly Detection in Log Data: A Survey[EB/OL]. (2023-05-15) [2023-05-30]. https://arxiv.org/abs/2207.03820.
|
| [13] |
LE V H,ZHANG Hongyu. Log-Based Anomaly Detection without Log Parsing[C]// IEEE. 2021 36th IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2021: 492-504.
|
| [14] |
HE Shilin, ZHU Jieming, HE Pinjia, et al. Loghub: A Large Collection of System Log Datasets Towards Automated Log Analytics[EB/OL]. (2020-08-14) [2023-05-30]. https://arxiv.org/abs/2008.06448.
|
| [15] |
XU Wei, HUANG Ling, FOX A, et al. Detecting Large-Scale System Problems by Mining Console Logs[C]// ACM. Proceedings of the ACM SIGOPS 22nd Symposium on Operating Systems Principles. New York: ACM, 2009: 117-132.
|
| [16] |
HAN Shangbin, WU Qianhong, ZHANG Han, et al. Log-Based Anomaly Detection with Robust Feature Extraction and Online Learning[J]. IEEE Transactions on Information Forensics and Security, 2021(16): 2300-2311.
|
| [17] |
CAO Qimin, QIAO Yinrong, LYU Zhong. Machine Learning to Detect Anomalies in Web Log Analysis[C]// IEEE. 2017 3rd IEEE International Conference on Computer and Communications (ICCC). New York: IEEE, 2017: 519-523.
|
| [18] |
YING Shi, WANG Bingming, WANG Lu, et al. An Improved KNN-Based Efficient Log Anomaly Detection Method with Automatically Labeled Samples[J]. ACM Transactions on Knowledge Discovery from Data (TKDD), 2021, 15(3): 1-22.
|
| [19] |
WURZENBERGER M, SKOPIK F, LANDAUER M, et al. Incremental Clustering for Semi-Supervised Anomaly Detection Applied on Log Data[C]// ACM. Proceedings of the 12th International Conference on Availability, Reliability and Security. New York: ACM, 2017: 1-6.
|
| [20] |
ZHANG Xu, XU Yong, LIN Qingwei, et al. Robust Log-Based Anomaly Detection on Unstable Log Data[C]// ACM. Proceedings of the 2019 27th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering. New York: ACM, 2019: 807-817.
|
| [21] |
BARIL X, COUSTIE O, MOTHE J, et al. Application Performance Anomaly Detection with LSTM on Temporal Irregularities in Logs[C]// ACM. Proceedings of the 29th ACM International Conference on Information & Knowledge Management. New York: ACM, 2020: 1961-1964.
|
 )
)