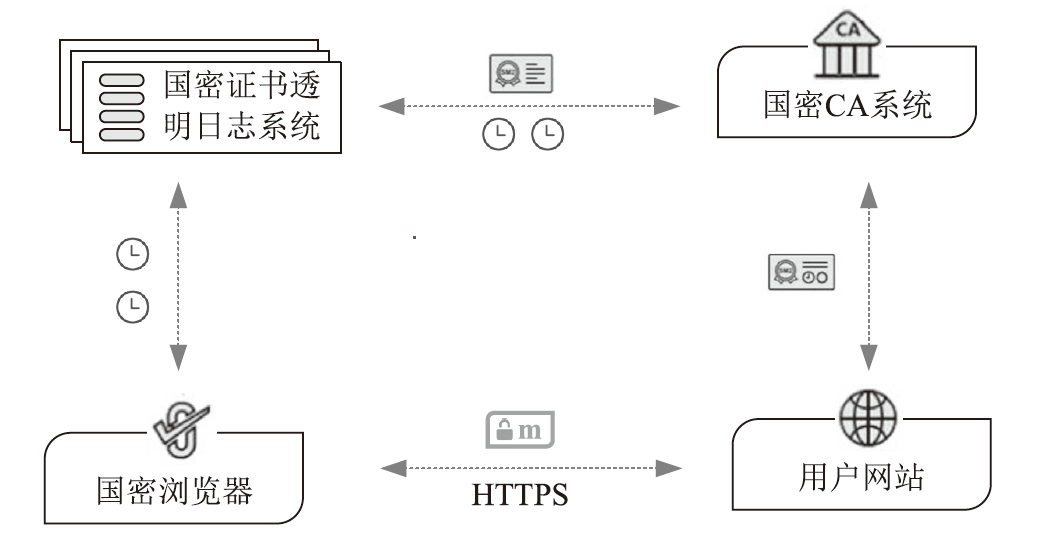
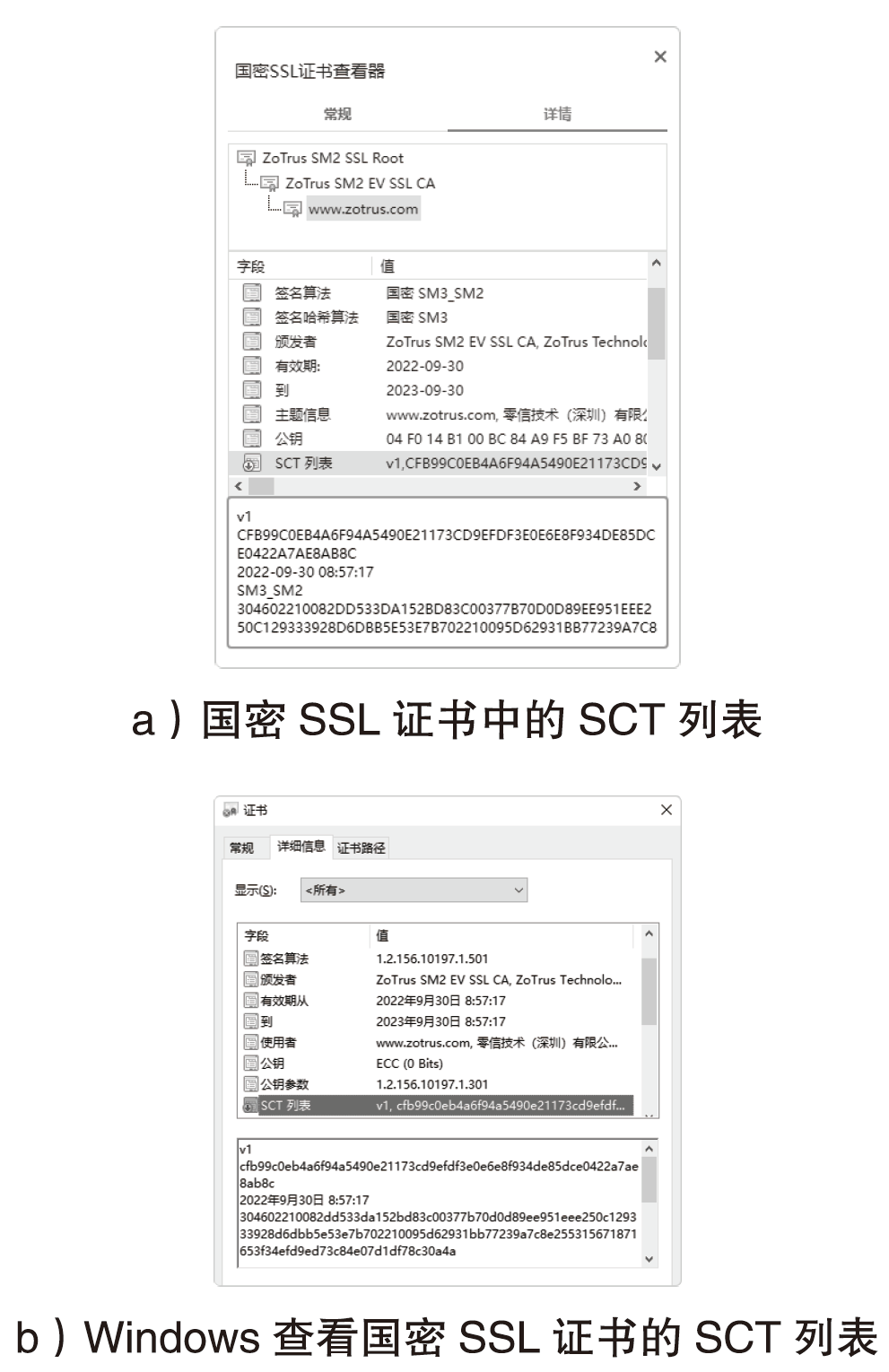
| [1] |
LU Rongjie, LIU Zhigui, ZHENG Xiaohong. United Authentication Platform Based on HTTPS Tunnel Technology[J]. Application Research of Computers, 2006, 23(12): 168-170.
|
|
陆荣杰, 刘知贵, 郑晓红. 基于HTTPS隧道技术的统一认证平台研究与实现[J]. 计算机应用研究, 2006, 23(12): 168-170.
|
| [2] |
LAURIE B, LANGLEY A, KASPER E. Certificate Transparency RFC 6962[EB/OL]. [2023-03-16]. https://datatracker.ietf.org/doc/rfc6962/.
|
| [3] |
ZHANG Jie, WANG Wei, MA Di, et al. Overview on Security Issues of Certificate Transparency[J]. Computer Systems & Applications, 2018, 27(10): 232-239.
|
|
张婕, 王伟, 马迪, 等. 数字证书透明性CT机制安全威胁研究[J]. 计算机系统应用, 2018, 27(10): 232-239.
|
| [4] |
KIM H J, HUANG L S, PERRING A, et al. Accountable Key Infrastructure (AKI): A Proposal for a Public-Key Validation Infrastructure[EB/OL]. [2023-05-23]. https://www.linshunghuang.com/papers/aki.pdf.
|
| [5] |
BASIN D, CREMERS C, KIM T, et al. ARPKI: Attack Resilient Public-Key Infrastructure[C]// ACM. Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2014: 382-393.
|
| [6] |
ALEXANDRA D, DAVID K, ROBERT M, et al. LogPicker: Strengthening Certificate Transparency Against Covert Adversaries[J]. Proceedings on Privacy Enhancing Technologies, 2021(4): 184-202.
|
| [7] |
WANG Xinmiao, SUN Tingting, MA Jingjun. Research Progress of RSA Algorithm in Network Data Transmission[J]. Computer Science, 2023, 50(S1): 703-709.
|
|
王鑫淼, 孙婷婷, 马晶军. RSA算法在网络数据传输中的研究进展[J]. 计算机科学, 2023, 50(S1): 703-709.
|
| [8] |
ZHANG Yongjian. Research of RSA Algorithm and SM2 Algorithm[D]. Nanchang: Jiangxi University of Science and Technology, 2016.
|
|
张永建. RSA算法和SM2算法的研究[D]. 南昌: 江西理工大学, 2016.
|
| [9] |
CHEN Chu. RFCcertDT: A Testing Tool for Certificate Validation in SSL/TLS[J]. Journal of Xidian University, 2019, 46(3): 20-25.
|
|
陈矗. RFCcertDT: SSL/TLS中证书验证的测试工具[J]. 西安电子科技大学学报, 2019, 46(3): 20-25.
|
| [10] |
MERKLE R C. A Digital Signature Based on a Conventional Encryption Function[C]// Springer. Conference on the Theory and Application of Cryptographic Techniques. Berlin:Springer, 1987: 369-378.
|
| [11] |
HAO Ronglin. Security Analysis of Hash Functions[D]. Hefei: University of Science and Technology of China, 2014.
|
|
郝荣林. 杂凑函数的安全性分析[D]. 合肥: 中国科学技术大学, 2014.
|
| [12] |
LI Bin, ZHOU Qinglei, CHEN Xiaojie, et al. Optimization of Reconfigurable SM2 Algorithm over Prime Filed[J]. Journal on Communications, 2022, 43(3): 30-41.
doi: 10.11959/j.issn.1000-436x.2022043
|
|
李斌, 周清雷, 陈晓杰, 等. 可重构的素域SM2算法优化方法[J]. 通信学报, 2022, 43(3): 30-41.
doi: 10.11959/j.issn.1000-436x.2022043
|
| [13] |
CHEN Boyu, WANG Hong. An Optimized Realization of SM3 Algorithm Based on FPGA[J]. Information Technology, 2018, 42(7): 143-147.
|
|
陈博宇, 王宏. 基于FPGA的SM3算法的优化实现[J]. 信息技术, 2018, 42(7): 143-147.
|
| [14] |
MELARA M S, BLANKSTEIN A, BONNEAU J, et al. Bringing Key Transparency to End Users[C]// USENIX. 24th USENIX Security Symposium (USENIX Security 15). Washington: USENIX, 2015: 383-398.
|
| [15] |
FU Na, GAO Jun, QIN Le. Research on Intellectual Property Risks of IoT Open Source Software[J]. Telecommunication Network Technology, 2018(1): 27-30.
|
|
付娜, 高隽, 秦乐. 物联网开源软件知识产权风险研究[J]. 电信网技术, 2018(1): 27-30.
|
| [16] |
CHENG Xiaohang, GUAN Li’an, ZHU Libin, et al. Flight Plan Verification Algorithm Based on Merkle Tree[J]. Command Information System and Technology, 2022, 13(5): 41-44.
|
|
程晓航, 关礼安, 朱立彬, 等. 基于默克尔树的飞行计划校验算法[J]. 指挥信息系统与技术, 2022, 13(5): 41-44.
|
 ), XUE Yuxin1, JIANG Yinghua1,2, ZHU Yaqing1
), XUE Yuxin1, JIANG Yinghua1,2, ZHU Yaqing1