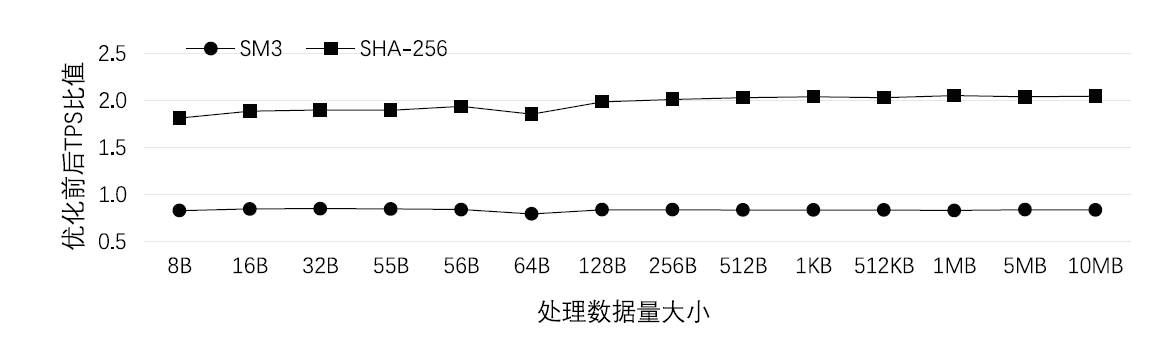
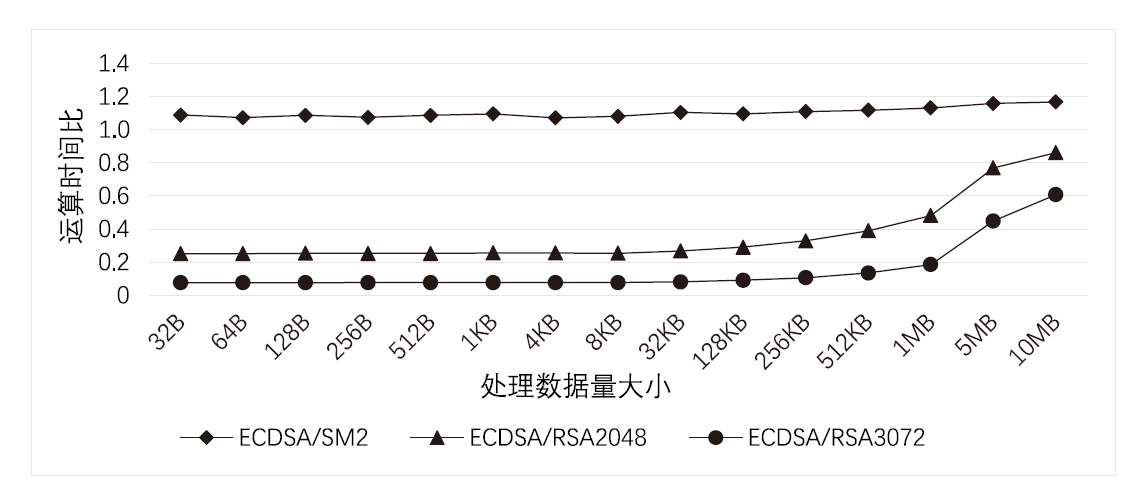
| [1] |
National Institute of Standards and Technology. Federal Information Processing Standards Publication 180-3, Secure Hash Standards(SHS)[S]. Gaithersburg: National Institute of Standards and Technology, 2008.
|
| [2] |
WANG Xiaoyun, YU Hongbo. How to Break MD5 and Other Hash Functions [C]//Springer. 24th Annual International Conference on Theory and Applications of Cryptographic Techniques, May 22-26, 2005, Aarhus, Denmark. Berlin: Springer, 2005: 19-35.
|
| [3] |
National Cryptography Administration. SM3 Cryptographic Hash Algorithm[EB/OL]. https://sca.gov.cn/sca/xwdt/2010-12/17/content_1002389.shtml, 2010-12-17.
|
|
国家密码管理局. SM3密码杂凑算法[EB/OL]. https://sca.gov.cn/sca/xwdt/2010-12/17/content_1002389.shtml, 2010-12-17.
|
| [4] |
SHEN Yanzhao. Analysis of SM3 Cryptographic Hash Algorithm[D]. Shanghai: Donghua University, 2013.
|
|
申延召. SM3密码杂凑算法分析[D]. 上海:东华大学, 2013.
|
| [5] |
National Cryptography Administration. Public Key Cryptographic Algorithm SM2 Based Elliptic Curves[EB/OL]. https://sca.gov.cn/sca/xwdt/2010-12/17/content_1002386.shtml, 2010-12-17.
|
|
国家密码管理局. SM2椭圆曲线公钥密码算法[EB/OL]. https://sca.gov.cn/sca/xwdt/2010-12/17/content_1002386.shtml, 2010-12-17.
|
| [6] |
JOHNSON D, MENEZES A, VANSTONE S. The Elliptic Curve Digital Signature Algorithm (ECDSA)[J]. International Journal of Information Security, 2001, 1(1):36-63.
doi: 10.1007/s102070100002
URL
|
| [7] |
RIVEST R L. A Method for Obtaining Digital Signatures and Public-key Cryptosystems[J]. Communications of the ACM, 1978, 26(2):96-99.
doi: 10.1145/357980.358017
URL
|
| [8] |
SUN Rongyan, CAI Changshu, ZHOU Zhou, et al. The Comparision Between Digital Signature Based on SM2 and ECDSA[J]. Network Security Technology and Application, 2013(2):60-62.
|
|
孙荣燕, 蔡昌曙, 周洲, 等. 国密SM2数字签名算法与ECDSA算法对比分析研究[J]. 网络安全技术与应用, 2013(2):60-62.
|
| [9] |
ASSOCIATION A B. Public Key Cryptography for the Financial Services Industry, Key Agreement and Key Transport Using Elliptic Curve Cryptography[J]. Speculum, 2006, 81(2):566-569.
doi: 10.1017/S0038713400003262
URL
|
| [10] |
BIRYUKOV A, CANNIÈRE C D. Data Encryption Standard(DES)[J]. Encyclopedia of Cryptography & Security, 2011, 28(2):295-301.
|
| [11] |
DAEMEN J, RIJMEN V. Rijndael, the Advanced Encryption Standard[J]. Dr Dobbs Journal, 2001, 26(3):137-139.
|
| [12] |
National Cryptography Administration. Announcement of the State Password Administration(No.7)[EB/OL]. https://www.oscca.gov.cn/sca/xwdt/2006-01/06/content_1002355.shtml, 2016-11-04.
|
|
国家密码管理局 国家密码管理局公告(第7号)[EB/OL]. https://www.oscca.gov.cn/sca/xwdt/2006-01/06/content_1002355.shtml, 2016-11-04.
|
| [13] |
MERKLE R C, HELLMAN M E. On the Security of Multiple Encryption[J]. Communications of the ACM, 1981, 24(7):465-467.
doi: 10.1145/358699.358718
URL
|
| [14] |
OORSCHOT P C V, WIENER M J. A Known-plaintext Attack on Two-key Triple Encryption[J]. Springer, 1991(473):318-325.
|
| [15] |
DAEMEN J. The Design of Rijndael[J]. Information Security & Cryptography, 2001, 26(3):137-139.
|
 ), WU Jintan1,2
), WU Jintan1,2