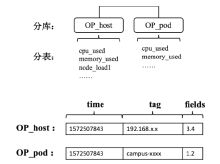
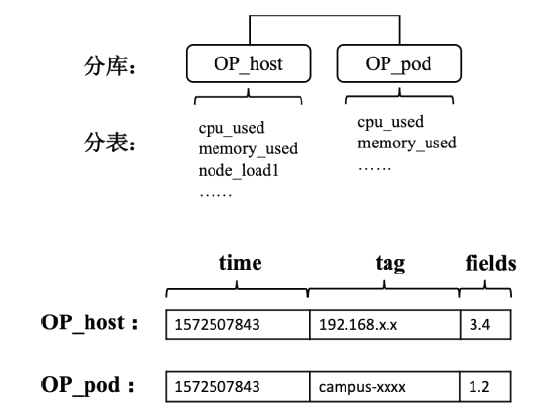
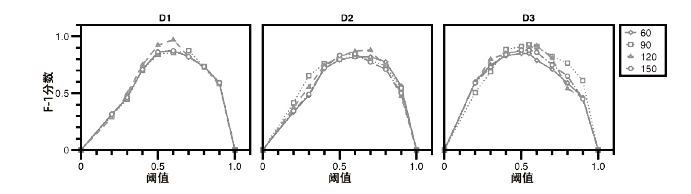
Netinfo Security ›› 2021, Vol. 21 ›› Issue (11): 85-94.doi: 10.3969/j.issn.1671-1122.2021.11.010
Previous Articles Next Articles
An Anomaly Detection and Location Algorithm Based on TCN and Attention Mechanism
WU Jiajie1, WU Shaoling2, WANG Wei1( )
)
- 1. School of Data Science and Engineering, East China Normal University, Shanghai 200062, China
2. Department of Computer Science and Technology, Tongji University, Shanghai 201804, China
-
Received:2020-05-06Online:2021-11-10Published:2021-11-24 -
Contact:WANG Wei E-mail:wwang@dase.ecnu.edu.cn
CLC Number:
Cite this article
WU Jiajie, WU Shaoling, WANG Wei. An Anomaly Detection and Location Algorithm Based on TCN and Attention Mechanism[J]. Netinfo Security, 2021, 21(11): 85-94.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.11.010
| [1] | DRAGONI N, GIALLORENZO S, LAFUENTE A L, et al. Present and Ulterior Software Engineering || Microservices: Yesterday, Today, and Tomorrow[M]. Berlin: Springer-Verlag, 2017. |
| [2] | LI Chunxia. Overview of Microservice Architecture Research[J]. Software Guide, 2019, 18(8):1-3, 7. |
| 李春霞. 微服务架构研究概述[J]. 软件导刊, 2019, 18(8):1-3,7. | |
| [3] | TANG Zhitao, LIU Xing. Evolution of Enterprise Application System Architecture[EB/OL]. https://www.cnki.com.cn/Article/CJFDTOTAL-CXYY201735067.htm, 2021-02-27. |
| 唐志涛, 刘星. 企业应用系统架构演进[EB/OL]. https://www.cnki.com.cn/Article/CJFDTOTAL-CXYY201735067.htm, 2021-02-27. | |
| [4] | ZHANG Shifeng, PAN Shanliang. Application of Docker Technology in Microservices[J]. Electronic Technology and Software Engineering, 2019, 19(4):164. |
| 章仕锋, 潘善亮. Docker技术在微服务中的应用[J]. 电子技术与软件工程, 2019, 19(4):164. | |
| [5] | KHAZAEI H, BARNA C, BEIGI-MOHAMMADI N, et al. Efficiency Analysis of Provisioning Microservices[C]// IEEE. 2016 IEEE International Conference on Cloud Computing Technology and Science (CloudCom), December 12-15, 2016, Piscataway, USA. New York: IEEE, 2016: 261-268. |
| [6] | FAN Yamin, FU Jian. The Way of Microservices: Metric Driven Development[M]. Beijing: China Machine Press, 2020. |
| 范亚敏, 傅健. 微服务之道:度量驱动开发[M]. 北京: 机械工业出版社, 2020. | |
| [7] | BLOHOWIAK A, BASIRI A. A Platform for Automating Chaos Experiments[C]// IEEE. 2016 IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW), October 23-27, 2016, Ottawa, Ontario, Canada. Piscataway: IEEE, 2016: 5-8. |
| [8] | SHYU Meiling, CHEN Shuching, SARINNAPAKORN K, et al. A Novel Anomaly Detection Scheme Based on Principal Component Classifier[C]// IEEE. Proceedings of the IEEE Foundations and New Directions of Data Mining Workshop, in Conjunction with the Third IEEE International Conference on Data Mining (ICDM03), November 19-22, 2003, Melbourne, Florida. USA. New York: IEEE, 2003: 172-179. |
| [9] | LIU Fei, TING Kaiming, ZHOU Zhihua, et al. Isolation Forest[C]// IEEE. 2008 Eighth IEEE International Conference on Data Mining, December 15-19, 2008, Washington, USA. New York: IEEE, 2008: 413-422. |
| [10] | ZONG Bo, SONG Qi, MIN M R, et al. Deep Autoencoding Gaussian Mixture Model for Unsupervised Anomaly Detection[C]// ICLR. International Conference on Learning Representations 2018, April 30-May 3, 2018, Vancouver, BC, Canada. USA: ICLR, 2018: 1-19. |
| [11] |
ZHANG Chuxu, SONG Dongjin, CHEN Yuncong, et al. A Deep Neural Network for Unsupervised Anomaly Detection and Diagnosis in Multivariate Time Series Data[J]. Proceedings of the AAAI Conference on Artificial Intelligence, 2019, 33(1):1409-1416.
doi: 10.1609/aaai.v33i01.33011409 URL |
| [12] | MALHOTRA P, RAMAKRISHNAN A, ANAND G, et al. LSTM-based Encoder-decoder for Multi-sensor Anomaly Detection[EB/OL]. https://arxiv.org/pdf/1607.00148.pdf, 2021-01-19. |
| [13] |
HE Yangdong, ZHAO Jiabao. Temporal Convolutional Networks for Anomaly Detection in Time Series[J]. Journal of Physics: Conference Series, 2019, 1213(4):42050.
doi: 10.1088/1742-6596/1213/4/042050 URL |
| [14] | MUNIR M, SIDDIQUI S A, DENGEL A, et al. DeepAnT: A Deep Learning Approach for Unsupervised Anomaly Detection in Time Series[J]. IEEE Access, 2019, 19(7):1991-2005. |
| [15] | LAPTEV N, AMIZADEH S, FLINT I, et al. Generic and Scalable Framework for Automated Time-series Anomaly Detection[C]// ACM. Proceedings of the 21th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, August 10-13, 2015, Sydney, NSW, Australia. New York: IEEE, 2015: 1939-1947. |
| [16] | Etsy. Skyline: It’ll Detect Your Anomalies[EB/OL]. https://github.com/etsy/skyline, 2021-01-15. |
| [17] | Netflix. Surus: A Collection of Tools for Analysis in Pig and Hive[EB/OL] https://github.com/netflix/surus, 2021-02-22. |
| [18] | XU Haowen, CHEN Wenxiao, ZHAO Nengwen, et al. Unsupervised Anomaly Detection via Variational Auto-encoder for Seasonal KPIs in Web Applications[C]// ACM. WWW 2018: International World Wide Web Conferences, April 23-27, 2018, Lyon, France. New York: ACM, 2018: 187-196. |
| [19] | LIU Dapeng, ZHAO Youjian, XU Haowen, et al. Opprentice: Towards Practical and Automatic Anomaly Detection Through Machine Learning[C]// ACM. Proceedings of the 2015 Internet Measurement Conference On, October 28-30, 2015, Tokyo, Japan. New York: ACM, 2015: 211-224. |
| [20] | BAI S, KOLTER Z, KOLTUN V, et al. An Empirical Evaluation of Generic Convolutional and Recurrent Networks for Sequence Modeling[EB/OL]. export.arxiv.org/pdf/1803.01271, 2021-01-16. |
| [21] | LUONG M T, PHAM H, MANNING C D, et al. Effective Approaches to Attention-based Neural Machine Translation[C]// ACL. Proceedings of the 2015 Conference on Empirical Methods in Natural Language Processing, September 17-18, 2015, Lisbon, Portugal. Stroudsbrug, Pennsylvania: ACL, 2015: 1412-1421. |
| [22] | CLEVELAND R B. STL: A Seasonal-trend Decomposition Procedure Based on Loess[J]. Journal of Office Statistics, 1990, 6(1):3-7. |
| [23] | TAYLOR S, LETHAM B. Forecasting at Scale[J]. The American Statistician, 2018, 7(1):37-45. |
| [24] |
HOCHREITER S, SCHMIDHUBER J. Long Short-term Memory[J]. Neural Computation, 1997, 9(8):1735-1780.
doi: 10.1162/neco.1997.9.8.1735 URL |
| [1] | QIN Zhongyuan, HU Ning, FANG Lanting. Network Anomaly Detection Method Based on Immune Bionic Mechanism and Graph Neural Network [J]. Netinfo Security, 2021, 21(8): 10-16. |
| [2] | XU Hongping, MA Zewen, YI Hang, ZHANG Longfei. Network Traffic Anomaly Detection Technology Based on Convolutional Recurrent Neural Network [J]. Netinfo Security, 2021, 21(7): 54-62. |
| [3] | LI Jiawei, WU Kehe, ZHANG Bo. Research on Anomaly Detection of Power Industrial Control System Based on Gaussian Mixture Clustering [J]. Netinfo Security, 2021, 21(3): 53-63. |
| [4] | LU Jiali. Log Anomaly Detection Method Based on Improved Time Series Model [J]. Netinfo Security, 2020, 20(9): 1-5. |
| [5] | HUANG Na, HE Jingsha, WU Yabiao, LI Jianguo. Method of Insider Threat Detection Based on LSTM Regression Model [J]. Netinfo Security, 2020, 20(9): 17-21. |
| [6] | WANG Yudi, LIU Xiaojie, WANG Yunpeng. Research on Anomaly Detection Method Based on Improved Negative Selection Algorithm [J]. Netinfo Security, 2020, 20(10): 75-82. |
| [7] | Wei WANG, Xudong SHEN. Research on Transfer Time Series Anomaly Detection Algorithm Based on Instance [J]. Netinfo Security, 2019, 19(3): 11-18. |
| [8] | Weichao YANG, Yuanbo GUO, Ya ZHONG, Shuaihui ZHEN. IoT Traffic Anomaly Detection Based on Device Type Identification and BP Neural Network [J]. Netinfo Security, 2019, 19(12): 53-63. |
| [9] | ZHU Haiqi, JIANG Feng. Research and Analysis of Anomaly Detection Technology for Operation and Maintenance Data in the Era of Artificial Intelligence [J]. Netinfo Security, 2019, 19(11): 24-35. |
| [10] | Hailian DENG, Yujing LIU, Yixuan GE, Jinshu SU. Research on Inter-domain Routing Anomaly Detection Technology [J]. Netinfo Security, 2019, 19(11): 63-70. |
| [11] | Wei LI, Xiaoxiao DI, Di WANG, Yunchun LI. Subgraph-based Network Behavior Models and Anomaly Detection for Server [J]. Netinfo Security, 2018, 18(2): 1-9. |
| [12] | Li HE, Yuanhui YAO. Detection and Recognition Strategy for Anomaly of Cloud Virtual Machine Based on Context Clustering [J]. Netinfo Security, 2018, 18(12): 54-65. |
| [13] | Gang ZHAO, Xingren YAO. Anomaly Detection Model Based on User Portrait [J]. Netinfo Security, 2017, 17(7): 18-24. |
| [14] | Xin WU, Yuesong YAN, Xiaoran LIU. Program Behavior Anomaly Detection Method Based on Improved HMM [J]. Netinfo Security, 2016, 16(9): 108-112. |
| [15] | Mingliang HE, Zemao CHEN, Jin ZUO. Cluster Anomaly Detection Algorithm Based on Multi-windows Mechanism [J]. Netinfo Security, 2016, 16(11): 33-39. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||