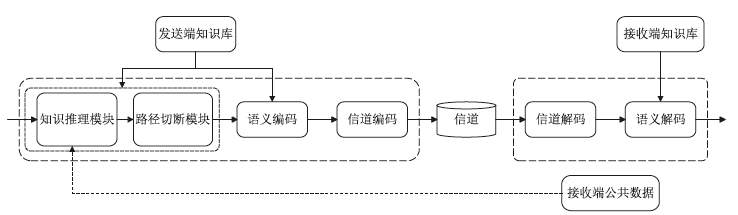
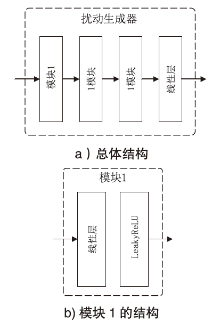
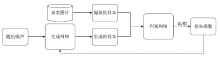
Netinfo Security ›› 2025, Vol. 25 ›› Issue (12): 1827-1846.doi: 10.3969/j.issn.1671-1122.2025.12.001
Previous Articles Next Articles
Semantic Communication Security: Multi-Layered Threats and Countermeasures
JIN Zhigang( ), LUO Houyang, LIU Zepei, DING Yu
), LUO Houyang, LIU Zepei, DING Yu
- School of Electrical and Information Engineering, Tianjin University, Tianjin 300072, China
-
Received:2025-11-08Online:2025-12-10Published:2026-01-06 -
Contact:JIN Zhigang E-mail:zgjin@tju.edu.cn
CLC Number:
Cite this article
JIN Zhigang, LUO Houyang, LIU Zepei, DING Yu. Semantic Communication Security: Multi-Layered Threats and Countermeasures[J]. Netinfo Security, 2025, 25(12): 1827-1846.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.12.001
| 文献 | 技术类型 | 要点 | 主要指标与结论 | |
|---|---|---|---|---|
| 攻击 | 防御 | |||
| 文献[ | √ | √ | 构造逆向解码器重构原始输入;在特征层注入噪声 | 无防护时重构SSIM高达0.92;加噪可压降重构 质量 |
| 文献[ | √ | √ | 建模收发双方知识差异,切断敏感推理路径 | 敏感路径泄露率降低40%+,优于传统DP方法 |
| 文献[ | √ | √ | 引入互信息变分上界,利用对抗训练最小化隐私互信息 | 攻击者重构SSIM降至0.3以下,分类精度保持92% |
| 文献[ | √ | √ | 对称密钥+神经网络加密器,对抗训练生成“语义乱码” | 合法用户几乎无损解码,窃听者重构SSIM < 0.1 |
| 文献[ | √ | √ | 引入全黑图像损失项,动态监测并压制窃听质量 | 低SNR下使窃听PSNR降低约10 dB,实现阈值触发保护 |
| 文献 | 技术类型 | 要点 | 主要指标与结论 | |
|---|---|---|---|---|
| 攻击 | 防御 | |||
| 文献[ | √ | √ | SemAdv生成物理层扰动;SemMixed联合训练 | SNR=0dB下攻击成功率降至45%;防御提升30% |
| 文献[ | √ | √ | 操纵语义符号重构;基于逆向工程清除后门 | 攻击成功率大于98%;剪枝清除率99.9%,性能损耗小于2.2% |
| 文献[ | √ | × | 联合优化数据层扰动与物理层干扰 | 低PNR(-12dB)下攻击成功率大于80%,效能提升10倍 |
| 文献[ | √ | √ | 动态Softmax温度缩放,平滑输出分布 | 替代模型攻击成功率从91%降至67% |
| 文献[ | √ | √ | 注入伪样本与误导特征,最大化反演损失 | 黑盒攻击成功率降至0%,模型效用损失小于2% |
| 文献 | 技术类型 | 要点 | 主要指标与结论 | |
|---|---|---|---|---|
| 攻击 | 防御 | |||
| 文献[ | √ | √ | SemMixed联合训练,物理层注入对抗样本 | 恶劣信道下鲁棒性提升30%,优于OFDM |
| 文献[ | √ | √ | 语义感知损失函数,阈值触发全黑扰动 | 低SNR下窃听PSNR降低10 dB,实现选择性保护 |
| 文献[ | √ | √ | 噪声导向掩码+码本正交化,阻断噪声传播 | -3 dB SNR下Top-1准确率大于85%,开销降至 JPEG 1% |
| 文献[ | √ | √ | 星座图对角映射+CSI相位噪声混淆 | 窃听准确率小于12%,延迟较AES降低73% |
| 文献[ | √ | √ | 量子态嵌入语义+隐形传态,利用不可克隆性 | 5比特系统解码误码率小于10%,实现无条件匿名 |
| 文献[ | √ | √ | 波分复用+动态密钥池,分级保护语义数据 | 高敏任务密钥覆盖率100%,利用率提升40% |
| 文献 | 技术类型 | 要点 | 主要指标与结论 | |
|---|---|---|---|---|
| 攻击 | 防御 | |||
| 文献[ | √ | √ | FGSM扰动实体嵌入;对抗训练+一致性检测 | 语义恢复错误率大于35%;防御提升15%~25% |
| 文献[ | √ | ◎ | 逻辑推理生成恶意事实,绕过异常检测 | 攻击成功率提升300%,隐蔽性强 |
| 文献[ | √ | ◎ | 子图结构权重指导删除+相似度筛选添加 | FB15K-237/WN18RR上实现最佳攻击效果 |
| 文献[ | √ | ◎ | 基于评分函数与梯度近似选择最优三元组投毒 | FB15K/WN18上MRR/Hit@10显著下降 |
| 文献[ | √ | × | 视觉毒样本注入知识库,操控检索与生成 | Top-K检索召回率大于90%,生成准确率大降 |
| 文献[ | √ | ◎ | 在KG中插入少量三元组构建误导性多跳路径 | 精确匹配率下降81%,生成错误答案带证据链 |
| 文献[ | √ | √ | 将逻辑算子结合嵌入空间进行目标/后门攻击,并提供过滤+对抗增强 | 高成功率且旁路损伤低 |
| 文献[ | √ | ◎ | DRL序贯决策增删事实优化目标推荐 | MovieLens等数据集上显著提升曝光/命中 |
| 文献[ | √ | √ | 影子模型动态优化投毒,利用聚合更新植入; LLM代理进行常识逻辑巡查与修正 | 目标攻击成功率近100%;清除95%以上逻辑投毒条目,无需人工干预 |
| 文献[ | √ | √ | 信任图维护节点信誉,动态隔离恶意节点 | 30%恶意节点下仍维持 共识 |
| [1] | ZHANG Ping, XU Wenjun, LIU Yiming, et al. Intellicise Wireless Networks From Semantic Communications: A Survey, Research Issues, and Challenges[J]. IEEE Communications Surveys & Tutorials, 2025, 27(3): 2051-2084. |
| [2] | STRINATI E C, BARBAROSSA S. 6G Networks: Beyond Shannon towards Semantic and Goal-Oriented Communications[EB/OL]. (2021-05-08)[2025-06-30]. https://arxiv.org/abs/2011.14844. |
| [3] |
GUNDUZ D, QIN Zhijin, AGUERRI I E, et al. Beyond Transmitting Bits: Context, Semantics, and Task-Oriented Communications[J]. IEEE Journal on Selected Areas in Communications, 2023, 41(1): 5-41.
doi: 10.1109/JSAC.2022.3223408 URL |
| [4] |
XU Wenjun, ZHANG Yimeng, WANG Fengyu, et al. Semantic Communication for the Internet of Vehicles: A Multiuser Cooperative Approach[J]. IEEE Vehicular Technology Magazine, 2023, 18(1): 100-109.
doi: 10.1109/MVT.2022.3227723 URL |
| [5] | WANG Yanhu, GUO Shuaishuai. Large Language Model-Based Semantic Communications: Status, Challenges, and Prospects[J]. Mobile Communications, 2024, 48(2): 16-21. |
| 王衍虎, 郭帅帅. 基于大语言模型的语义通信:现状,挑战与展望[J]. 移动通信, 2024, 48(2): 16-21. | |
| [6] |
KHAN L U, TUN Y K, ALSENWI M, et al. A Dispersed Federated Learning Framework for 6G-Enabled Autonomous Driving Cars[J]. IEEE Transactions on Network Science and Engineering, 2024, 11(6): 5656-5667.
doi: 10.1109/TNSE.2022.3188571 URL |
| [7] |
CHEN Ruxiao, GUO Shuaishuai. Look-Ahead Task Offloading for Multi-User Mobile Augmented Reality in Edge-Cloud Computing[J]. IEEE Network, 2023, 37(4): 40-46.
doi: 10.1109/MNET.001.2200593 URL |
| [8] | REN Kui, MENG Quanrun, YAN Shoukun, et al. Survey of Artificial Intelligence Data Security and Privacy Protection[J]. Chinese Journal of Network and Information Security, 2021, 7(1): 1-10. |
| 任奎, 孟泉润, 闫守琨, 等. 人工智能模型数据泄露的攻击与防御研究综述[J]. 网络与信息安全学报, 2021, 7(1): 1-10. | |
| [9] | QIN Zhijin, TAO Xiaoming, LU Jianhua, et al. Semantic Communications: Principles and Challenges[EB/OL]. (2022-06-27)[2025-06-30]. https://arxiv.org/abs/2201.01389. |
| [10] |
NAN Guoshun, LI Zhichun, ZHAI Jinli, et al. Physical-Layer Adversarial Robustness for Deep Learning-Based Semantic Communications[J]. IEEE Journal on Selected Areas in Communications, 2023, 41(8): 2592-2608.
doi: 10.1109/JSAC.2023.3288249 URL |
| [11] |
HE Yingzhe, MENG Guozhu, CHEN Kai, et al. Towards Security Threats of Deep Learning Systems: A Survey[J]. IEEE Transactions on Software Engineering, 2022, 48(5): 1743-1770.
doi: 10.1109/TSE.2020.3034721 URL |
| [12] |
LI Jingyi, LIAO Guocheng, CHEN Lin, et al. Roulette: A Semantic Privacy-Preserving Device-Edge Collaborative Inference Framework for Deep Learning Classification Tasks[J]. IEEE Transactions on Mobile Computing, 2024, 23(5): 5494-5510.
doi: 10.1109/TMC.2023.3312304 URL |
| [13] | CAO Mingge, ZHU Haopeng, MIN Minghui, et al. Protecting Personalized Trajectory with Differential Privacy under Temporal Correlations[C]// IEEE.2024 IEEE Wireless Communications and Networking Conference (WCNC). New York: IEEE, 2024: 1-6. |
| [14] | KIRCHENBAUER J, GEIPING J, WEN Yuxin, et al. A Watermark for Large Language Models[C]// PMLR. The 40th International Conference on Machine Learning. New York: PMLR, 2023: 17061-17084. |
| [15] |
XU Yongliang, CHENG Hang, LIU Ximeng, et al. PCSE: Privacy-Preserving Collaborative Searchable Encryption for Group Data Sharing in Cloud Computing[J]. IEEE Transactions on Mobile Computing, 2025, 24(5): 4558-4572.
doi: 10.1109/TMC.2025.3526232 URL |
| [16] | MENG Rui, GAO Song, FAN Dayu, et al. A Survey of Secure Semantic Communications[EB/OL]. (2025-07-31)[2025-11-05]. https://arxiv.org/abs/2501.00842. |
| [17] | SHI Jiting, ZENG Weihao, ZHANG Qianyun, et al. Semantic Communication Security: A Survey[J]. Journal of Nanjing University of Information Science & Technology, 2025, 17(1): 1-12. |
| 施继婷, 曾维昊, 张骞允, 等. 语义通信安全研究综述[J]. 南京信息工程大学学报, 2025, 17(1): 1-12. | |
| [18] | JEGOROVA M, KAUL C, MAYOR C, et al. Survey: Leakage and Privacy at Inference Time[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2023, 45(7): 9090-9108. |
| [19] |
LU Kun, ZHOU Qingyang, LI Rongpeng, et al. Rethinking Modern Communication from Semantic Coding to Semantic Communication[J]. IEEE Wireless Communications, 2023, 30(1): 158-164.
doi: 10.1109/MWC.013.2100642 URL |
| [20] |
CHEN Jian, ZHANG Xuxin, ZHANG Rui, et al. De-Pois: An Attack-Agnostic Defense against Data Poisoning Attacks[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 3412-3425.
doi: 10.1109/TIFS.2021.3080522 URL |
| [21] | ZHOU Enyuan, GUO Song, MA Zhixiu, et al. Poisoning Attack on Federated Knowledge Graph Embedding[C]// ACM. The ACM Web Conference 2024. New York: ACM, 2024: 1998-2008. |
| [22] | ZHOU Yuan, HU R Q, QIAN Yi. Backdoor Attacks and Defenses on Semantic-Symbol Reconstruction in Semantic Communications[C]// IEEE. ICC 2024-IEEE International Conference on Communications. New York: IEEE, 2024: 734-739. |
| [23] | ZHANG Zhenguo, YANG Qianqian, HE Shibo. Deep Learning-Based Image Semantic Communication System[J]. ZTE Communications, 2023, 29(2): 54-61. |
| 张振国, 杨倩倩, 贺诗波. 基于深度学习的图像语义通信系统[J]. 中兴通讯技术, 2023, 29(2): 54-61. | |
| [24] |
MAO Jin, XIONG Ke, LIU Ming, et al. A GAN-Based Semantic Communication for Text Without CSI[J]. IEEE Transactions on Wireless Communications, 2024, 23(10): 14498-14514.
doi: 10.1109/TWC.2024.3415363 URL |
| [25] |
XU Mingkai, WU Yongpeng, SHI Yuxuan, et al. Learnable Residual-Based Latent Denoising in Semantic Communication[J]. IEEE Wireless Communications Letters, 2025, 14(5): 1376-1380.
doi: 10.1109/LWC.2025.3542811 URL |
| [26] |
HOANG V T, NGUYEN V L, CHANG R G, et al. Adversarial Attacks against Shared Knowledge Interpretation in Semantic Communications[J]. IEEE Transactions on Cognitive Communications and Networking, 2025, 11(2): 1024-1040.
doi: 10.1109/TCCN.2025.3528891 URL |
| [27] | XU Zhishuang, ZHANG Kun, FAN Junchao, et al. Construction Method of Cybersecurity Knowledge Graph Based on Ontology[J]. Netinfo Security, 2025, 25(3): 451-466. |
| 许智双, 张昆, 范俊超, 等. 基于本体的网络安全知识图谱构建方法[J]. 信息网络安全, 2025, 25(3): 451-466. | |
| [28] | KANG Jiawen, HE Jiayi, DU Hongyang, et al. Adversarial Attacks and Defenses for Semantic Communication in Vehicular Metaverses[J]. IEEE Wireless Communications, 2023, 30(4): 48-55. |
| [29] |
QIN Zhijin, ZHAO Tantan, LI Fan, et al. Survey of Research on Multimodal Semantic Communication[J]. Journal on Communications, 2023, 44(5): 28-41.
doi: 10.11959/j.issn.1000-436x.2023105 |
|
秦志金, 赵菼菼, 李凡, 等. 多模态语义通信研究综述[J]. 通信学报, 2023, 44(5): 28-41.
doi: 10.11959/j.issn.1000-436x.2023105 |
|
| [30] | YANG Ke, WANG Sixian, DAI Jincheng, et al. WITT: A Wireless Image Transmission Transformer for Semantic Communications[C]// IEEE.2023 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP). New York: IEEE, 2023: 1-5. |
| [31] | GUO Shaolong, WANG Yuntao, ZHANG Ning, et al. A Survey on Semantic Communication Networks: Architecture, Security, and Privacy[J]. IEEE Communications Surveys & Tutorials, 2025, 27(5): 2860-2894. |
| [32] | LI Xiao, SONG Xiao, LI Yong. Research on Differential Privacy Methods for Medical Diagnosis Based on Knowledge Distillation[J]. Netinfo Security, 2025, 25(4): 524-535. |
| 李骁, 宋晓, 李勇. 基于知识蒸馏的医疗诊断差分隐私方法研究[J]. 信息网络安全, 2025, 25(4): 524-535. | |
| [33] |
CHENG Shiqi, ZHANG Xuefei, SUN Yao, et al. Knowledge Discrepancy Oriented Privacy Preserving for Semantic Communication[J]. IEEE Transactions on Vehicular Technology, 2024, 73(8): 11637-11646.
doi: 10.1109/TVT.2024.3381222 URL |
| [34] |
WANG Yanhu, GUO Shuaishuai, DENG Yiqin, et al. Privacy-Preserving Task-Oriented Semantic Communications against Model Inversion Attacks[J]. IEEE Transactions on Wireless Communications, 2024, 23(8): 10150-10165.
doi: 10.1109/TWC.2024.3369170 URL |
| [35] |
LUO Xinlai, CHEN Zhiyong, TAO Meixia, et al. Encrypted Semantic Communication Using Adversarial Training for Privacy Preserving[J]. IEEE Communications Letters, 2023, 27(6): 1486-1490.
doi: 10.1109/LCOMM.2023.3269768 URL |
| [36] |
ZHANG Maojun, LI Yang, ZHANG Zezhong, et al. Wireless Image Transmission with Semantic and Security Awareness[J]. IEEE Wireless Communications Letters, 2023, 12(8): 1389-1393.
doi: 10.1109/LWC.2023.3275383 URL |
| [37] | SAGDUYU Y E, ERPEK T, ULUKUS S, et al. Is Semantic Communication Secure? A Tale of Multi-Domain Adversarial Attacks[J]. IEEE Communications Magazine, 2023, 61(11): 50-55. |
| [38] |
JIANG Wenbo, LI Hongwei, XU Guowen, et al. A Comprehensive Defense Framework against Model Extraction Attacks[J]. IEEE Transactions on Dependable and Secure Computing, 2024, 21(2): 685-700.
doi: 10.1109/TDSC.2023.3261327 URL |
| [39] |
GONG Xueluan, WANG Ziyao, LI Shuaike, et al. A GAN-Based Defense Framework against Model Inversion Attacks[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 4475-4487.
doi: 10.1109/TIFS.2023.3295944 URL |
| [40] |
HU Qiyu, ZHANG Guangyi, QIN Zhijin, et al. Robust Semantic Communications with Masked VQ-VAE Enabled Codebook[J]. IEEE Transactions on Wireless Communications, 2023, 22(12): 8707-8722.
doi: 10.1109/TWC.2023.3265201 URL |
| [41] | GUO Qin, TONG Haonan, WANG Sihua, et al. A Secure Semantic Communication System Based on Knowledge Graph[EB/OL]. [2025-11-05]. https://arxiv.org/abs/2511.13246. |
| [42] |
KHALID U, ULUM M S, FAROOQ A, et al. Quantum Semantic Communications for Metaverse: Principles and Challenges[J]. IEEE Wireless Communications, 2023, 30(4): 26-36.
doi: 10.1109/MWC.002.2200613 URL |
| [43] |
KAEWPUANG R, XU Minrui, LIM W Y B, et al. Cooperative Resource Management in Quantum Key Distribution (QKD) Networks for Semantic Communication[J]. IEEE Internet of Things Journal, 2024, 11(3): 4454-4469.
doi: 10.1109/JIOT.2023.3301033 URL |
| [44] |
LIU Yating, WANG Xiaojie, NING Zhaolong, et al. A Survey on Semantic Communications: Technologies, Solutions, Applications and Challenges[J]. Digital Communications and Networks, 2024, 10(3): 528-545.
doi: 10.1016/j.dcan.2023.05.010 URL |
| [45] | ZHANG Ping, LIU Yiming, SONG Yile, et al. Advances and Challenges in Semantic Communications: A Systematic Review[J]. National Science Open, 2024, 3(4): 172-207. |
| [46] | YOU Xiaoyu, SHENG Beina, DING Daizong, et al. MaSS:Model-Agnostic, Semantic and Stealthy Data Poisoning Attack on Knowledge Graph Embedding[C]// ACM. The ACM Web Conference 2023. New York: ACM, 2023: 2000-2010. |
| [47] | ZHANG Yuxiao, DU Xiaojing, CHEN Qingfeng. Adversarial Attack against Knowledge Graph Embedding Based on Subgraph Structure[J]. Journal of Chinese Computer Systems, 2024, 45(4): 807-814. |
| 张玉潇, 杜晓敬, 陈庆锋. 融合子图结构的知识图谱嵌入对抗性攻击方法[J]. 小型微型计算机系统, 2024, 45(4): 807-814. | |
| [48] | ZHAO Ting, CHEN Jun, RU Yi, et al. Untargeted Adversarial Attack on Knowledge Graph Embeddings[C]// ACM. The 47th International ACM SIGIR Conference on Research and Development in Information Retrieval. New York: ACM, 2024: 1701-1711. |
| [49] |
LU Yuqian, ASGHAR M R. Semantic Communications between Distributed Cyber-Physical Systems towards Collaborative Automation for Smart Manufacturing[J]. Journal of Manufacturing Systems, 2020, 55: 348-359.
doi: 10.1016/j.jmsy.2020.05.001 |
| [50] |
LIN Yijing, DU Hongyang, NIYATO D, et al. Blockchain-Aided Secure Semantic Communication for AI-Generated Content in Metaverse[J]. IEEE Open Journal of the Computer Society, 2023, 4: 72-83.
doi: 10.1109/OJCS.2023.3260732 URL |
| [51] | ZHANG Hengtong, ZHENG Tianhang, GAO Jing, et al. Data Poisoning Attack against Knowledge Graph Embedding[EB/OL]. (2019-06-24)[2025-11-05]. https://arxiv.org/abs/1904.12052. |
| [52] | ZHANG Chenyang, ZHANG Xiaoyu, LOU Jian, et al. PoisonedEye: Knowledge Poisoning Attack on Retrieval-Augmented Generation Based Large Vision-Language Models[C]// PMLR. The Forty-Second International Conference on Machine Learning (ICML 2025). New York: PMLR, 2025, 267: 76811-76830. |
| [53] | ZHAO Tianzhe, CHEN Jiaoyan, RU Yanchi, et al. RAG Safety: Exploring Knowledge Poisoning Attacks to Retrieval-Augmented Generation[EB/OL]. (2025-07-09)[2025-11-05]. https://arxiv.org/abs/2507.08862. |
| [54] | XI Zhaohan, DU Tianyu, LI Changjiang, et al. On the Security Risks of Knowledge Graph Reasoning[EB/OL]. (2023-05-03)[2025-11-05]. https://arxiv.org/abs/2305.02383. |
| [55] |
WU Z W, CHEN C T, HUANG S H. Poisoning Attacks against Knowledge Graph-Based Recommendation Systems Using Deep Reinforcement Learning[J]. Neural Computing and Applications, 2022, 34(4): 3097-3115.
doi: 10.1007/s00521-021-06573-8 |
| [56] | WEI Qianshan, YANG Tengchao, WANG Yaochen, et al. A-MemGuard: A Proactive Defense Framework for LLM-Based Agent Memory[EB/OL]. (2025-09-29)[2025-11-05]. https://arxiv.org/abs/2510.02373. |
| [57] | ZENG Weihao, XU Xinyu, ZHANG Qianyun, et al. A Secure and Efficient Distributed Semantic Communication System for Heterogeneous Internet of Things[EB/OL]. (2024-07-19)[2025-11-05]. https://arxiv.org/abs/2407.14140. |
| [58] | ZHAO Fangzhou, SUN Yao, LAN Jianglin, et al. Adaptive Semantic Communication for UAV/UGV Cooperative Path Planning[EB/OL]. (2025-10-08)[2025-11-05]. https://arxiv.org/abs/2510.06901. |
| [59] |
SHAO Zhiyu, WU Qiong, FAN Pingyi, et al. Semantic-Aware Spectrum Sharing in Internet of Vehicles Based on Deep Reinforcement Learning[J]. IEEE Internet of Things Journal, 2024, 11(23): 38521-38536.
doi: 10.1109/JIOT.2024.3448538 URL |
| [60] | ZHENG Wenting, POPA R A, GONZALEZ J E, et al. Helen: Maliciously Secure Coopetitive Learning for Linear Models[C]// IEEE. 2019 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2019: 724-738. |
| [1] | YANG Liqun, LI Zhen, WEI Chaoren, YAN Zhimin, QIU Yongxin. Research on Protocol Fuzzing Technology Guided by Large Language Models [J]. Netinfo Security, 2025, 25(12): 1847-1862. |
| [2] | HU Dan, YANG Jilong. An Efficient Method for Router Alias Identification with Active-Passive Collaboration [J]. Netinfo Security, 2025, 25(12): 1863-1877. |
| [3] | PANG Shuchao, LI Zhengxiao, QU Junyi, MA Ruhao, CHEN Hechang, DU Anan. Detecting Poisoned Samples for Untargeted Backdoor Attacks [J]. Netinfo Security, 2025, 25(12): 1878-1888. |
| [4] | XIE Xiangpeng, SHAO Xingchen. Secure Gain-Scheduling Method for Stochastic Nonlinear CPS Based on Dual-Domain Polynomial Framework [J]. Netinfo Security, 2025, 25(12): 1889-1900. |
| [5] | ZHANG Xuefeng, WANG Kehang. A Proxy Ring Signature Scheme Based on SM9 Algorithm [J]. Netinfo Security, 2025, 25(12): 1901-1913. |
| [6] | HAN Yiliang, PENG Yixuan, WU Xuguang, LI Yu. Multimodal Feature Fusion Encrypted Traffic Classification Model Based on Graph Variational Auto-Encoder [J]. Netinfo Security, 2025, 25(12): 1914-1926. |
| [7] | FU Zhangjie, CHEN Tianyu, CUI Qi. Dynamic Handwritten Signature Verification Models Protection Method Based on Contrastive Learning [J]. Netinfo Security, 2025, 25(12): 1927-1935. |
| [8] | LIU Dahe, XIU Jiapeng, YANG Zhengqiu. Research on Community Detection and Core Node Discovery Based on Improved Louvain Algorithm [J]. Netinfo Security, 2025, 25(12): 1936-1947. |
| [9] | ZHANG Guanping, WEI Fushan, CHEN Xi, GU Chunxiang. Blockchain-Based Privacy-Preserving Cross-Domain Authentication Protocol [J]. Netinfo Security, 2025, 25(12): 1948-1960. |
| [10] | QIN Siying, SUN Bing, FU Shaojing, TANG Xiaomei. Key Switching for Somewhat Homomorphic Encryption Based on RLWR [J]. Netinfo Security, 2025, 25(12): 1961-1974. |
| [11] | WANG Houzhen, JIANG Haolang, LIU Jichen, TU Hang. Privacy-Preserving Sorting Scheme Based on Paillier Homomorphic Encryption [J]. Netinfo Security, 2025, 25(12): 1975-1989. |
| [12] | MENG Hui, MAO Linlin, PENG Juzhi. Sanitize Processing and Recognition Method Driven by Large Language Model [J]. Netinfo Security, 2025, 25(12): 1990-1998. |
| [13] | ZHU Hui, FANG Yunyi, WANG Fengwei, XU Wei. Research Progress on Data Security Processing Integrating Confidential Computing [J]. Netinfo Security, 2025, 25(11): 1643-1657. |
| [14] | HAO Meng, LI Jiayong, YANG Hongwei, ZHANG Weizhe. Heterogeneous CPU-GPU System Confidential Computing Survey [J]. Netinfo Security, 2025, 25(11): 1658-1672. |
| [15] | GUAN Zhi, HU Jianbin, LI Yue, CHEN Zhong. A Comprehensive Survey of Blockchain Technologies and Applications Based on Trusted Execution Environments [J]. Netinfo Security, 2025, 25(11): 1673-1690. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||