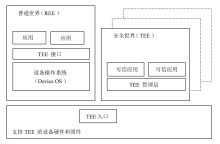
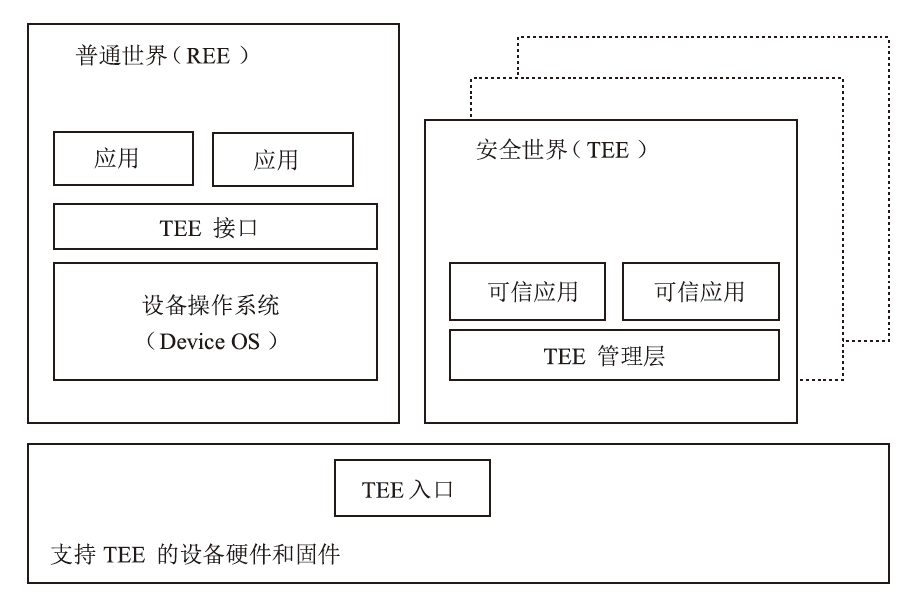
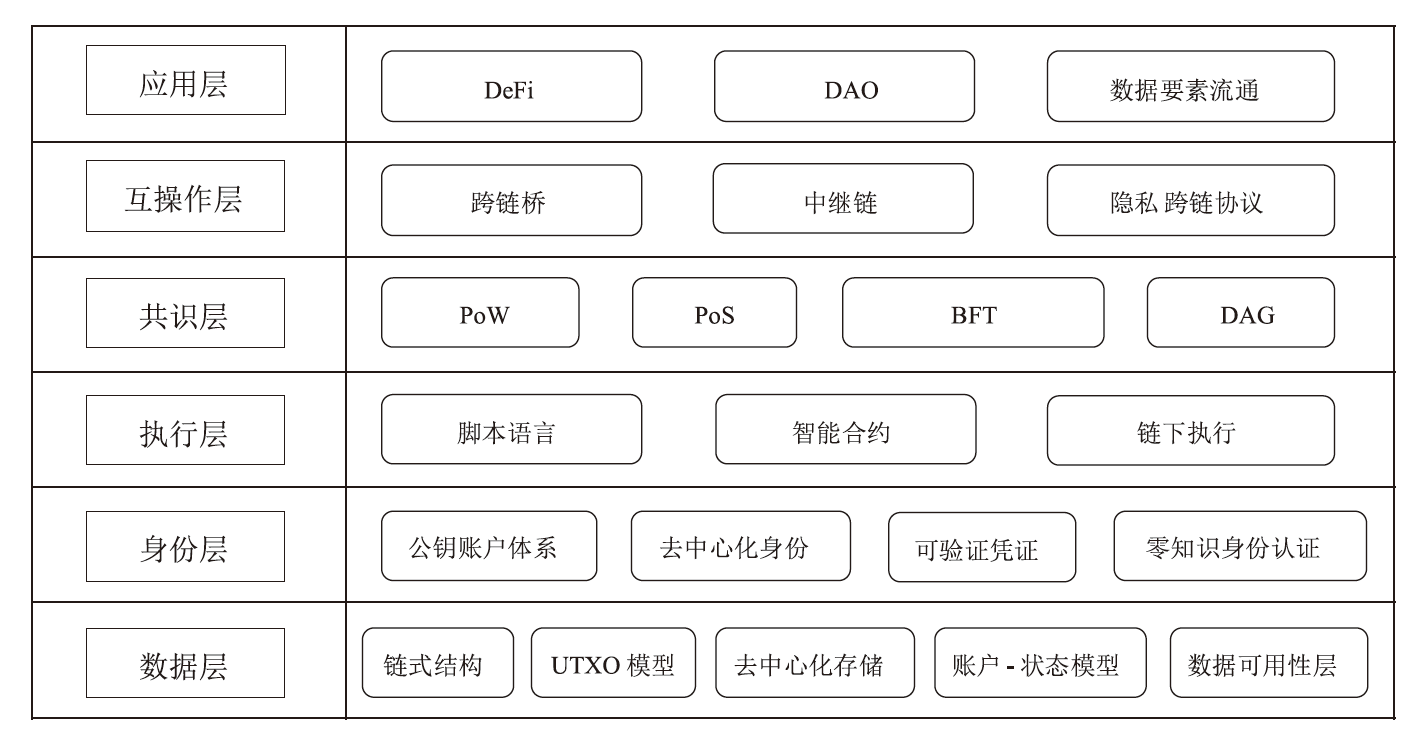
Netinfo Security ›› 2025, Vol. 25 ›› Issue (11): 1673-1690.doi: 10.3969/j.issn.1671-1122.2025.11.003
Previous Articles Next Articles
A Comprehensive Survey of Blockchain Technologies and Applications Based on Trusted Execution Environments
GUAN Zhi1, HU Jianbin2, LI Yue2( ), CHEN Zhong2
), CHEN Zhong2
1. National Engineering Research Center for Software Engineering ,Peking University Beijing 100871, China 2. School of Computer Science ,Peking University Beijing 100871, China
-
Received:2025-07-31Online:2025-11-10Published:2025-12-02
CLC Number:
Cite this article
GUAN Zhi, HU Jianbin, LI Yue, CHEN Zhong. A Comprehensive Survey of Blockchain Technologies and Applications Based on Trusted Execution Environments[J]. Netinfo Security, 2025, 25(11): 1673-1690.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.11.003
| [1] |
YUAN M J, HYNES N, LONG Ju. Confidential Ethereum Smart Contracts[J]. IT Professional, 2023, 24(6): 54-58.
doi: 10.1109/MITP.2022.3175690 URL |
| [2] | YIN Hang, ZHOU Shunfan, JIANG Jun. Phala Network: A Confidential Smart Contract Network Based on Polkadot[EB/OL]. (2019-09-25)[2025-07-19]. https://www.semanticscholar.org/paper/Phala-Network%3A-A-Con%EF%AC%81dential-Smart-Contract-Network-Yin-Zhou/edbaeb9ebecbf344f38d47b192cd4666851db1ae. |
| [3] | WOETZEL C. Secret Network: A Privacy-Preserving Secret Contract & Decentralized Application Platform[EB/OL]. (2016-01-25)[2025-07-29]. https://scrt.network/. |
| [4] | NEARAI. Building User-Owned AI[EB/OL]. (2024-09-21)[2025-07-29]. https://near.ai/. |
| [5] | ROSCHER S, BONISCH V, LEE J, et al. Integrating Solutions on IBM Z with Secure Service Container[J]. IBM Journal of Research and Development, 2018, 62(2): 3-11. |
| [6] | DHANRAJ V, CHWARLA H, MANILA D, et al. Adaptive and Efficient Dynamic Memory Management for Hardware Enclaves[EB/OL]. (2025-09-08)[2025-07-19]. https://dl.acm.org/doi/pdf/10.1145/3757347.3759137. |
| [7] | MISONO M, STAVRAKAKIS D, SANTOS N, et al. Confidential VMs Explained: An Empirical Analysis of AMD SEV-SNP and Intel TDX[J]. Measurement and Analysis of Computing Systems, 2024, 8(3): 1-42. |
| [8] | LEE J, WANG Yongqin, RAJAT R, et al. Characterization of GPU TEE Overheads in Distributed Data Parallel ML Training[EB/OL]. (2025-01-20)[2025-07-19]. https://arxiv.org/abs/2501.11771v3. |
| [9] | OTT S, ORTHEN B, WEIDINGER A, et al. MultiTEE: Distributing Trusted Execution Environments[C]// ACM. The 19th ACM ASIA Conference on Computer and Communications Security. New York: ACM, 2024: 1617-1629. |
| [10] | KOHLBRENNER D, SHINDE S, LEE D, et al. Building Open Trusted Execution Environments[J]. IEEE Security & Privacy, 2020, 18(5): 47-56. |
| [11] | LAN Ying, GAO Jianbo, LI Yue, et al. TrustCross: Enabling Confidential Interoperability across Blockchains Using Trusted Hardware[C]// ACM. The 4th International Conference on Blockchain Technology and Applications (ICBTA’21). New York: ACM, 2022: 17-23. |
| [12] | LEE D, ANTONIO J, KHAN H. Privacy-Preserving Decentralized AI with Confidential Computing[EB/OL]. (2024-12-18)[2025-07-19]. https://arxiv.org/pdf/2410.13752. |
| [13] | JAVAID U. Blockchain Based Secure Group Data Collaboration in Cloud with Differentially Private Synthetic Data and Trusted Execution Environment[C]// IEEE.2022 IEEE International Conference on Big Data. New York: IEEE, 2022: 3919-3927. |
| [14] |
KIM S, BERNINGER S, KOCHER M, et al. Cross-Company Data Sharing Using Distributed Analytics[J]. Systems, 2025, 13(6): 418-429.
doi: 10.3390/systems13060418 URL |
| [15] |
XIE Hui, ZHENG Jun, HE Teng, et al. TEBDS: A Trusted Execution Environment-and-Blockchain-Supported IoT Data Sharing System[J]. Future Generation Computer Systems, 2023, 140: 321-330.
doi: 10.1016/j.future.2022.10.016 URL |
| [16] | WANG Sixiang, HUO Dongdong, ZHANG Hailong, et al. SSIDB: Secure Sharing of IoT Data on Blockchain with CP-ABE and Trusted Environment Assistance[C]// IEEE.International Symposium on Parallel and Distributed Processing with Applications (ISPA). New York: IEEE, 2024: 2022-2029. |
| [17] | KIM S, YUN S, JANG J. Secure User-Friendly Blockchain Modular Wallet Design Using Android & OP-TEE[EB/OL]. (2025-07-22)[2025-07-19]. https://arxiv.org/pdf/2506.17988. |
| [18] | KOSHIBA A. Trusted Heterogeneous Disaggregated Architectures[C]// ACM.Asia-Pacific Workshop on Systems. New York: ACM, 2023: 72-79. |
| [19] |
WANG Lianhai, LIU Xiaoqian, SHAO Wei, et al. A Blockchain-Based Privacy-Preserving Healthcare Data Sharing Scheme for Incremental Updates[J]. Symmetry, 2024, 16(1): 89-97.
doi: 10.3390/sym16010089 URL |
| [20] | XIAO Yang, ZHANG Ning, LI Jin, et al. PrivacyGuard: Enforcing Private Data Usage Control with Blockchain and Attested Off-Chain Contract Execution[EB/OL]. (2019-04-15)[2025-06-19]. https://arxiv.org/abs/1904.07275. |
| [21] | YAN Ying, WEI Changzheng, GUO Xuepeng, et al. Confidentiality Support over Financial Grade Consortium Blockchain[C]// ACM.The 2020 ACM SIGMOD International Conference on Management of Data. New York: ACM, 2020: 2227-2240. |
| [22] | HEISS J, BUSSE A, TAI S. Trustworthy Pre-Processing of Sensor Data in Data On-Chaining Workflows for Blockchain-Based IoT Applications[C]// Springer. Service-Oriented Computing-ICSOC 2021:Lecture Notes in Computer Science, Heidelberg:Springer, 2021: 133-149. |
| [23] |
WEN Xiaoqing, FENG Quanbi, LYU Hanzheng, et al. TeeRollup: Efficient Rollup Design Using Heterogeneous TEE[J]. IEEE Transactions on Computers, 2025, 74(10): 3546-3558.
doi: 10.1109/TC.2025.3596698 URL |
| [24] | XIAN Youquan, ZHOU Lianghaojie, JIANG Jianyong, et al. A Distributed Efficient Blockchain Oracle Scheme for Internet of Things[J]. IEICE Transactions on Communications, 2024, 107(9): 573-582. |
| [25] | PENNEKAMP J, ALDER F, MATZUTT R, et al. Secure End-to-End Sensing in Supply Chains[C]// IEEE.2020 IEEE Conference on Communications and Network Security. New York: IEEE, 2020: 1-6. |
| [26] | LIND J, NAOR O, EYAL I, et al. Teechain: A Secure Payment Network with Asynchronous Blockchain Access[C]// ACM.The 27th ACM Symposium on Operating Systems Principles. New York: ACM, 2019: 63-79. |
| [27] |
WANG Qinghao. SorTEE: Service-Oriented Routing for Payment Channel Networks with Scalability and Privacy Protection[J]. IEEE Transactions on Network and Service Management, 2022, 19(4): 3764-3780.
doi: 10.1109/TNSM.2022.3213559 URL |
| [28] | LIND J, EYAL I, PIETZUCH P, et al. Teechan: Payment Channels Using Trusted Execution Environments[EB/OL]. (2016-12-22)[2025-06-19]. https://arxiv.org/abs/1612.07766. |
| [29] | LI Peng, LUO Xiaofei, MIYAZAKI T, et al. Privacy-Preserving Payment Channel Networks Using Trusted Execution Environment[C]// IEEE.2020 IEEE International Conference on Communications. New York: IEEE, 2020: 1-6. |
| [30] | LEE J, KIM S, PARK S, et al. RouTEE: Secure, Scalable, and Efficient Off-Chain Payments Using Trusted Execution Environments[EB/OL]. (2025-03-18)[2025-06-19]. https://ieeexplore.ieee.org/document/10917388. |
| [31] |
XIE Yankai, LI Ruian, HUANG Yan, et al. A Monitoring-Free Bitcoin Payment Channel Scheme With Support for Real-Time Settlement[J]. IEEE Transactions on Services Computing, 2024, 17(5): 1924-1937.
doi: 10.1109/TSC.2024.3390396 URL |
| [32] | GRUNDMANN M, LEINWEBER M, HARTENSTEIN H. Banklaves: Concept for a Trustworthy Decentralized Payment Service for Bitcoin[EB/OL]. (2019-07-01)[2025-06-19]. https://ieeexplore.ieee.org/document/8751394. |
| [33] | TRAN M, LUU L, KANG M S, et al. Obscuro: A Bitcoin Mixer Using Trusted Execution Environments[EB/OL]. (2018-12-31)[2025-06-19]. https://eprint.iacr.org/2017/974.pdf. |
| [34] | XIE Yankai, WANG Qingtao, LI Songwei, et al. Secure and Efficient Decentralized Bitcoin Mixing Scheme Using Trusted Execution Environment[C]// IEEE.2022 IEEE International Conference on Communications. New York: IEEE, 2022: 4390-4395. |
| [35] | YANG Xiao, WU Libing, ZHANG Zhuangzhuang, et al. Survey on Blockchain-Based Integrity Validating for Cloud Data[J]. Journal of Chinese Computer Systems. 2023, 44(11): 2369-2376. |
| 杨潇, 吴黎兵, 张壮壮, 等. 基于区块链的云数据完整性验证研究综述[J]. 小型微型计算机系统. 2023, 44(11): 2369-2376. | |
| [36] |
YUAN Rui, XIA Yubin, CHEN Haibo, et al. ShadowEth: Private Smart Contract on Public Blockchain[J]. Journal of Computer Science and Technology, 2018, 33: 542-556.
doi: 10.1007/s11390-018-1839-y |
| [37] | CHENG R, ZHANG Fan, KOS J, et al. Ekiden: A Platform for Confidentiality-Preserving, Trustworthy, and Performant Smart Contracts[EB/OL]. (2019-07-17)[2025-06-19]. https://ieeexplore.org/document/8806762. |
| [38] | FRASSETTO T, JAUERNIG P, KOISSER D, et al. POSE: Practical Off-Chain Smart Contract Execution[EB/OL]. (2022-12-13)[2025-06-19]. https://arxiv.org/abs/2210.07110. |
| [39] |
LI Zecheng, XIAO Bin, GUO Songtao, et al. Securing Deployed Smart Contracts and DeFi With Distributed TEE Cluster[J]. IEEE Transactions on Parallel and Distributed Systems, 2023, 34(3): 828-842.
doi: 10.1109/TPDS.2022.3232548 URL |
| [40] | DAS P, ECKEY L, FRASSETTO T, et al. FastKitten: Practical Smart Contracts on Bitcoin[EB/OL]. (2019-08-16)[2025-06-19]. https://eprint.iacr.org/2019/154.pdf. |
| [41] | GADDAM S, KUMARESAN R, RAGHURAMAN S, et al. LucidiTEE: Scalable Policy-Based Multiparty Computation with Fairness[C]// Springer.Cryptology and Network Security. Heidelberg: Springer, 2023: 343-367. |
| [42] | XU Cheng, ZHANG Ce, XU Jianliang, et al. SlimChain: Scaling Blockchain Transactions through Off-Chain Storage and Parallel Processing[J]. VLDB Endowment, 2021, 14(11): 2314-2326. |
| [43] | WUST K, DIANA L, KOSTIAINEN K, et al. Bitcontracts: Supporting Smart Contracts in Legacy Blockchains[EB/OL]. (2019-01-25)[2025-06-19]. https://eprint.iacr.org/2019/857. |
| [44] | WUST K, MATETIC S, EGLI S, et al. ACE: Asynchronous and Concurrent Execution of Complex Smart Contracts[C]// ACM. The 2020 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2020: 587-600. |
| [45] | REN Qian, LIU Han, LI Yue, et al. Cloak: A Framework for Development of Confidential Blockchain Smart Contracts[EB/OL]. (2021-12-04)[2025-06-19]. https://ieeexplore.ieee.org/document/9546461. |
| [46] |
REN Qian, LI Yue, WU Yingjun, et al. DeCloak: Enable Secure and Cheap Multi-Party Transactions on Legacy Blockchains by a Minimally Trusted TEE Network[J]. IEEE Transactions on Information Forensics and Security, 2023, 19: 88-103.
doi: 10.1109/TIFS.2023.3318935 URL |
| [47] | MATETIC S, WUST K, SCHNEIDER M, et al. BITE: Bitcoin Lightweight Client Privacy Using Trusted Execution[C]// USENIX.28th USENIX Security Symposium. Berkeley: USENIX, 2019: 783-800. |
| [48] | WUST K, MATETIC S, SCHNEIDER M, et al. ZLiTE: Lightweight Clients for Shielded Zcash Transactions Using Trusted Execution[EB/OL]. (2018-11-19)[2025-06-19]. https://eprint.iacr.org/2018/1024. |
| [49] | LI Suozai, HUANG Ming, WANG Qinghao, et al. T-PPA: A Privacy-Preserving Decentralized Payment System with Efficient Auditability Based on TEE[C]// IEEE. 2022 IEEE 8th International Conference on Computer and Communications (ICCC). New York: IEEE, 2022: 1255-1263. |
| [50] | JEAN-LOUIS N, LI Yunqi, JI Yan, et al. SGXonerated: Finding (and Partially Fixing) Privacy Flaws in TEE-Based Smart Contract Platforms Without Breaking the TEE[EB/OL]. (2023-11-09)[2025-06-19]. https://eprint.iacr.org/2023/378.pdf. |
| [51] | FENG Liaoliao, DING Yan, TAN Yusong, et al. Trusted-Committee-Based Secure and Scalable BFT Consensus for Consortium Blockchain[C]// IEEE.2022 the 18th International Conference on Mobility, Sensing and Networking. New York: IEEE, 2022: 363-370. |
| [52] |
LIU Jian, LI Wenting, KARAME G O, et al. Scalable Byzantine Consensus via Hardware-Assisted Secret Sharing[J]. IEEE Transactions on Computers, 2018, 68(1): 139-151.
doi: 10.1109/TC.2018.2860009 URL |
| [53] |
WANG Ran, MA Fuqiang, TANG Sisui, et al. Parallel Byzantine Fault Tolerance Consensus Based on Trusted Execution Environments[J]. Peer-to-Peer Networking and Applications, 2025, 18(1): 31-42.
doi: 10.1007/s12083-024-01830-8 |
| [54] | NIU Jianyu, WEN Xiaoqing, WU Guanlong, et al. Achilles: Efficient TEE-Assisted BFT Consensus via Rollback Resilient Recovery[C]// ACM. The European Conference on Computer Systems. New York: ACM, 2025: 193-210. |
| [55] | ZHANG Jiashuo, GAO Jianbo, WANG Ke, et al. TBFT: Efficient Byzantine Fault Tolerance Using Trusted Execution Environment[C]// IEEE.IEEE International Conference on Communications. New York: IEEE, 2022: 1004-1009. |
| [56] | XIE Shaokang, KANG Dakai, LYU Hanzheng, et al. Fides: Scalable Censorship-Resistant DAG Consensus via Trusted Components[EB/OL]. (2025-01-02)[2025-06-19]. https://arxiv.org/abs/2501.01062. |
| [57] | FU Xiang, WANG Huaimin, SHI Peichang, et al. Teegraph: A Blockchain Consensus Algorithm Based on TEE and DAG for Data Sharing in IoT[J]. Journal of Systems Architecture, 2022, 122(1): 344-352. |
| [58] | LIU Lifeng, LI Jian, YUAN T T. TEE-Based Mutual Proofs of Transmission Services in Decentralized Systems[C]// IEEE. INFOCOM 2020-IEEE Conference on Computer Communications Workshops. New York: IEEE, 2020: 754-759. |
| [59] | YANG Wenzhe, HAO Yuanke, ZHAO Changsheng, et al. Data Sharing Trusted Data Lake Platform Based on Object Deputy[J]. Journal of Chinese Computer Systems, 2023, 44(6):1324-1328. |
| 杨文哲, 郝渊科, 赵常胜, 等. 基于对象代理的大数据共享可信数据湖平台[J]. 小型微型计算机系统, 2023, 44(6):1324-1328. | |
| [60] | MILUTINOVIC M, HE W, WU H, et al. Proof of Luck: An Efficient Blockchain Consensus Protocol[C]// ACM. The 1st Workshop on System Software for Trusted Execution. New York: ACM, 2016: 1-6. |
| [61] | LEINWEBER M, HARTENSTEIN H. Not EXactly Byzantine: Efficient and Resilient TEE-Based State Machine Replication[EB/OL]. (2025-01-19)[2025-06-19]. https://arxiv.org/abs/2501.11051. |
| [62] | BRANDENBURGER M, CACHIN C, KAPITZA R, et al. Trusted Computing Meets Blockchain: Rollback Attacks and a Solution for Hyperledger Fabric[C]// IEEE.The 38th Symposium on Reliable Distributed Systems. New York: IEEE, 2019: 324-332. |
| [63] | LEW C C, TORRES C F, SHINDE S, et al. Revisiting Rollbacks on Smart Contracts in TEE-Protected Private Blockchains[C]// IEEE.2024 IEEE European Symposium on Security and Privacy Workshops. New York: IEEE, 2024: 217-224. |
| [64] |
LU Xin, ZHANG Zijian, MA Teng, et al. Trusted Execution Environment with Rollback Protection for Smart Contract-Based IoT Data Trading[J]. IEEE Internet of Things Journal, 2024, 11(20): 32901-32909.
doi: 10.1109/JIOT.2024.3422005 URL |
| [65] |
YIN Zeyuan, ZHANG Bingsheng, XU Jingzhong, et al. Bool Network: An Open, Distributed, Secure Cross-Chain Notary Platform[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 3465-3478.
doi: 10.1109/TIFS.2022.3209546 URL |
| [66] | WEN Xiaoqing, FENG Quanbi, NIU Jianyu, et al. MECURY: Practical Cross-Chain Exchange via Trusted Hardware[EB/OL]. (2024-09-23)[2025-06-19]. https://arxiv.org/abs/2409.14640. |
| [67] | WANG Yichuan, TIE Jianhuan, HEI Xinhong, et al. A Trusted Privacy-Preserving Model for Cross-Chain Transactions Based on Zk-SNARKs[C]// IEEE.2023 International Conference on Networking and Network Applications. New York: IEEE, 2023: 187-192. |
| [68] | WANG Gang, NIXON M. InterTrust: Towards an Efficient Blockchain Interoperability Architecture with Trusted Services[C]// IEEE. 2021 IEEE International Conference on Blockchain. New York: IEEE, 2021: 150-159. |
| [69] | LI Ming, WENG Jian, WENG Jiasi, et al. IvyCross: A Privacy-Preserving and Concurrency Control Framework for Blockchain Interoperability[EB/OL]. (2023-03-03)[2025-06-19]. https://ieeexplore.ieee.org/document/10971953. |
| [70] |
ZHANG Jianting, CHEN Wuhui, HONG Zicong, et al. Efficient Execution of Arbitrarily Complex Cross-Shard Contracts for Blockchain Sharding[J]. IEEE Transactions on Computers, 2024, 73(5): 1190-1205.
doi: 10.1109/TC.2024.3365929 URL |
| [71] | ZENG Ping, ZHANG Liwen, ZHAO Geng, et al. TEE-Based Oracle Cross-Chain Data Secure Transmission Protocol[J]. Computer Simulation, 2024, 41(6): 486-492. |
| 曾萍, 张沥文, 赵耿, 等. 基于TEE预言机的区块跨链数据安全传输协议[J]. 计算机仿真, 2024, 41(6): 486-492. | |
| [72] | HUANG Junqin, KONG Linghe, CHENG Guanjie, et al. Advancing Web 3.0: Making Smart Contracts Smarter on Blockchain[EB/OL]. (2024-05-13)[2025-06-19]. https://dl.acm.org/doi/10.1145/3589334.3645319. |
| [73] | NEARAI. Private and Verifiable AI[EB/OL]. (2025-06-29)[2025-07-29]. https://dl.acm.org/doi/10.1145/3589334.3645319. |
| [74] |
KALAPAAKING A P, KHALIL I, RAHMAN M S, et al. Blockchain-Based Federated Learning with Secure Aggregation in Trusted Execution Environment for Internet-of-Things[J]. IEEE Transactions on Industrial Informatics, 2022, 19(2): 1703-1714.
doi: 10.1109/TII.2022.3170348 URL |
| [75] | WANG Hao, CAI Yichen, WANG Jun, et al. Voltran: Unlocking Trust and Confidentiality in Decentralized Federated Learning Aggregation[EB/OL]. (2024-03-29)[2025-06-19]. https://ieeexplore.ieee.org/document/10703116. |
| [76] |
WANG Ran, XU Cheng, ZHANG Shuhao, et al. Swarm Transfer Learning Driven Materials Computation for Secure Big Data Sharing[J]. Nature Communications, 2024, 15(1): 9290-9298.
doi: 10.1038/s41467-024-53431-x |
| [77] |
LIU Bingyu, XIE Shangyu, YANG Yuanzhou, et al. Privacy Preserving Divisible Double Auction with a Hybridized TEE-Blockchain System[J]. Cybersecurity, 2021, 4: 1-14.
doi: 10.1186/s42400-020-00065-3 |
| [78] |
SHARADQH A A M, HATAMLEH H A M, ALNASER A M A, et al. Hybrid Chain: Blockchain Enabled Framework for Bi-Level Intrusion Detection and Graph-Based Mitigation for Security Provisioning in Edge Assisted IoT Environment[J]. IEEE Access, 2023, 11: 27433-27449.
doi: 10.1109/ACCESS.2023.3256277 URL |
| [79] | YULIANTO S, WARNARS H L H S, PRABOWO H, et al. Security Risks and Best Practices for Blockchain and Smart Contracts: A Systematic Literature Review[C]// IEEE.2023 International Conference on Information Management and Technology (ICIMTech). New York: IEEE, 2023: 1-6. |
| [80] | SENDNER C, PETZI L, STANG J, et al. Vulnerability Scanners for Ethereum Smart Contracts: A Large-Scale Study[EB/OL]. (2025-03-03)[2025-06-19]. https://doi.org/10.48550/ARXIV.2312.16533. |
| [81] | JOY A, SOH B, ZHANG Zhi, et al. Physical and Software Based Fault Injection Attacks Against TEEs in Mobile Devices: A Systemisation of Knowledge[EB/OL]. (2024-11-22)[2025-06-19]. https://arxiv.org/abs/2411.14878. |
| [82] | AUGUSTO A, BELCHIOR R, CORREIA M, et al. SoK: Security and Privacy of Blockchain Interoperability[C]// IEEE.2024 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2024: 3840-3865. |
| [83] | LIU Zekai, LI Xiaoqi. SoK: Security Analysis of Blockchain-Based Cryptocurrency[EB/OL]. (2025-04-30)[2025-06-19]. https://www.computer.org/csdl/proceedings-article/sp/2024/313000a234/1WPcYVyZLWw. |
| [84] |
CAI Yize. Assessing and Neutralizing Multi-Tiered Security Threats in Blockchain Systems[J]. Applied and Computational Engineering, 2024, 49: 65-74.
doi: 10.54254/2755-2721/49/20241063 URL |
| [85] | SURAWEERA S. IoT Security: A Comprehensive Review of Challenges, Solutions and Future Directions[EB/OL]. (2025-02-07)[2025-06-19]. https://www.techrxiv.org/inst/26407. |
| [86] | COSTAN V, DEVADAS S. Intel SGX Explained[EB/OL]. (2017-02-21)[2025-06-19]. http://eprint.iacr.org/2016/086. |
| [1] | YANG Jianxin, WANG Xiaoding, LIN Hui. Improved Consensus Algorithm Based on HotStuff and Multi-Ary Trees [J]. Netinfo Security, 2025, 25(9): 1447-1455. |
| [2] | SHE Wei, MA Tianxiang, FENG Haige, LIU Wei. Tracing-Free Blockchain Covert Communication Method Based on RBF Mechanism [J]. Netinfo Security, 2025, 25(8): 1302-1312. |
| [3] | LIU Feng, HUANG Hao. A Decentralized Regulatory Architecture Based on Smart Contracts and Prophecy Machines with Active Sensor Networks [J]. Netinfo Security, 2025, 25(6): 898-909. |
| [4] | YE Jiajun, GAO Cuifeng, XUE Yinxing. Research on Price Oracle Manipulation Source Code Detection Method Based on Static Analysis [J]. Netinfo Security, 2025, 25(5): 732-746. |
| [5] | QIN Jinlei, KANG Yimin, LI Zheng. Lightweight Fine-Grained Multi-Dimensional Multi-Subset Privacy-Preserving Data Aggregation for Smart Grid [J]. Netinfo Security, 2025, 25(5): 747-757. |
| [6] | ZHU Xiaoqiang, ZHANG Haowen, LIN Yanzi, LIU Jiqiang. Lightweight Distributed Authentication Scheme Based on Trusted Digital Identity [J]. Netinfo Security, 2025, 25(5): 817-827. |
| [7] | YANG Yatao, DING Yucheng, LIU Peihe, SANG Peng. Research on Blockchain-Based Privacy Preservation and Digital Authentication [J]. Netinfo Security, 2025, 25(4): 640-653. |
| [8] | ZHANG Yuxuan, HUANG Cheng, LIU Rong, LENG Tao. Smart Contract Vulnerability Detection Method Combining Prompt Tuning [J]. Netinfo Security, 2025, 25(4): 664-673. |
| [9] | SHEN Haoting, PENG Zhigang, LIU Yuxuan, WANG Yafei. Hardware Authentication Mechanism for Consortium Blockchain Based on Differentiated Physical Unclonable Function Models [J]. Netinfo Security, 2025, 25(11): 1732-1744. |
| [10] | WANG Yong, WU Yifan, WAN Qiancheng. Research on Redactable Blockchain Scheme Based on the Chinese Remainder Theorem [J]. Netinfo Security, 2025, 25(1): 36-47. |
| [11] | YU Lisu, LI Biao, YAO Yuanzhi, WEN Jiajin, LI Zipeng, WANG Zhen. Performance Optimization of Blockchain-Assisted Unmanned Aerial Vehicle Mobile Edge Computing System [J]. Netinfo Security, 2024, 24(9): 1432-1443. |
| [12] | LYU Qiuyun, ZHOU Lingfei, REN Yizhi, ZHOU Shifei, SHENG Chunjie. A Lifecycle-Manageable Public Data Sharing Scheme [J]. Netinfo Security, 2024, 24(8): 1291-1305. |
| [13] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [14] | GUO Rui, YANG Xin, WANG Junming. Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2024, 24(6): 863-878. |
| [15] | LING Zhi, YANG Ming, YU Jiangyin. Research on Power Security Trading Platform Based on IPFS and Blockchain Technology [J]. Netinfo Security, 2024, 24(6): 968-976. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||