Netinfo Security ›› 2025, Vol. 25 ›› Issue (12): 1901-1913.doi: 10.3969/j.issn.1671-1122.2025.12.006
Previous Articles Next Articles
A Proxy Ring Signature Scheme Based on SM9 Algorithm
- School of Cyberspace Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
-
Received:2025-03-03Online:2025-12-10Published:2026-01-06 -
Contact:WANG Kehang E-mail:wkh0503@163.com
CLC Number:
Cite this article
ZHANG Xuefeng, WANG Kehang. A Proxy Ring Signature Scheme Based on SM9 Algorithm[J]. Netinfo Security, 2025, 25(12): 1901-1913.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.12.006
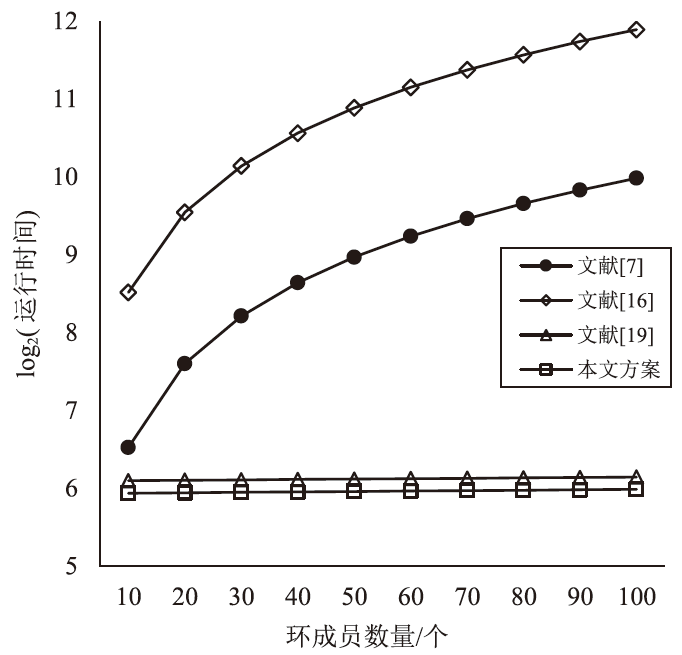
| 方案 | 代理委托 | 代理验证 | 签名 | 验证 |
|---|---|---|---|---|
| 文献[7] | — | — | (3n+1)MG1+(n-1)H | nMG1+2BP+nH |
| 文献[16] | — | — | (n+1)MG1+ (n-1)MG2+(n-1)MGT+ nBP+(n-1)EGT+ (2n-1)H | nMG2+nMGT+ nBP+2nH |
| 文献[19] | — | — | (n+4)MG1+MG2+ 2MGT+4BP+H | 2MG1+MG2+4MGT+ 4BP+3EGT+2H |
| 文献[23] | 2MG1+3EGT+ 2H | MG1+MG2+ 2BP+EGT+2H | MG1+EGT+H | 2MG1+MGT+ BP+EGT+4H |
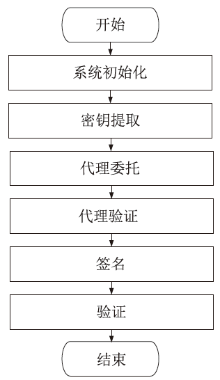
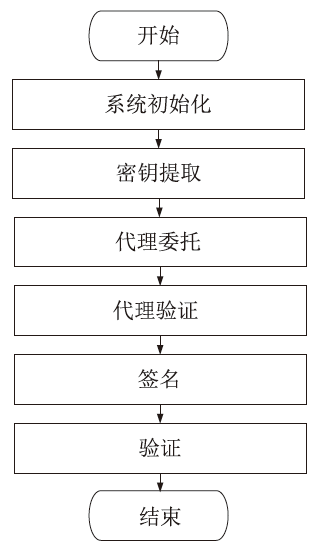
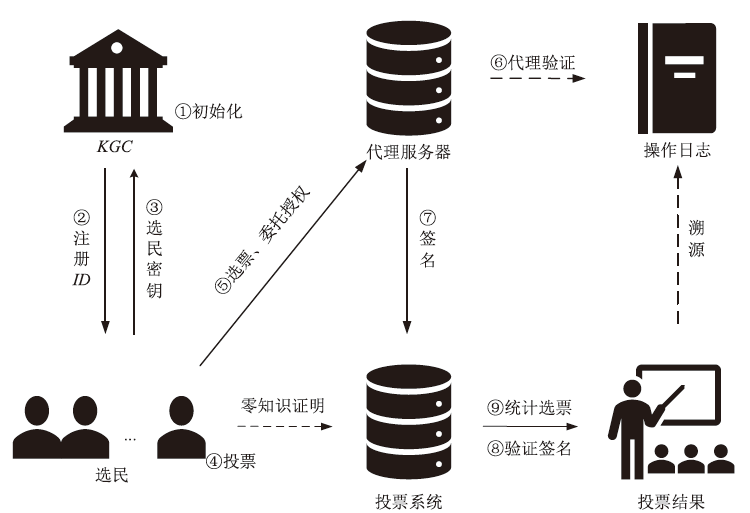
| 本文方案 | 3MG1+EGT+ H | MG2+MGT+ BP+EGT | (n+2)MG1+2MG2+ 3MGT+3BP+EGT+H | 2MG1+MG2+4MGT+ 2BP+2EGT+H |
| [1] |
DIFFIE W, HELLMAN M E. New Directions in Cryptography[J]. IEEE Transactions on Information Theory, 1976, 22(6): 644-654.
doi: 10.1109/TIT.1976.1055638 URL |
| [2] |
RIVEST R L, SHAMIR A, ADLEMAN L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems[J]. Communications of the ACM, 1978, 21(2): 120-126.
doi: 10.1145/359340.359342 URL |
| [3] | MAMBO M, USUDA K, OKAMOTO E. Proxy Signatures for Delegating Signing Operation[C]// ACM.The 3rd ACM Conference on Computer and Communications Security. New York: ACM,1996: 48-57. |
| [4] | RIVEST R L, SHAMIR A, TAUMAN Y. How to Leak a Secret[C]// Springer.Advances in Cryptology—ASIACRYPT 2001: The 7th International Conference on the Theory and Application of Cryptology and Information Security Gold Coast. Heidelberg:Springer, 2001: 552-565. |
| [5] | ZHANG Fangguo, SAFAVI-NAINI R, LIN C Y. New Proxy Signature, Proxy Blind Signature and Proxy Ring Signature Schemes from Bilinear Pairing[EB/OL].(2003-11-02) [2025-03-01]. https://eprint.iacr.org/2003/104.pdf. |
| [6] | CHENG Wenqing, LANG Weimin, YANG Zongkai, et al. An Identity-Based Proxy Ring Signature Scheme from Bilinear Pairings[C]// IEEE. The 9th International Symposium on Computers and Communications. New York: IEEE, 2004: 424-429. |
| [7] |
YU Yong, YANG Bo, LI Fagen, et al. An Efficient Proxy Ring Signature Scheme[J]. Journal of Beijing University of Posts and Telecommunications, 2007, 30(3):23-26.
doi: 10.13190/jbupt.200703.23.yuy |
|
禹勇, 杨波, 李发根, 等. 一个有效的代理环签名方案[J]. 北京邮电大学学报, 2007, 30(3):23-26.
doi: 10.13190/jbupt.200703.23.yuy |
|
| [8] | CHEN Ke, MIAO Fuyou, XIONG Yan. RSA-Based Proxy Ring Signature Scheme[J]. Computer Science, 2009, 36(2):132-136. |
| 陈珂, 苗付友, 熊焰. 基于RSA的代理环签名方案[J]. 计算机科学, 2009, 36(2):132-136. | |
| [9] |
ASAAR M R, SALMASIZADEH M, SUSILO W. A Provably Secure Identity‐Based Proxy Ring Signature Based on RSA[J]. Security and Communication Networks, 2015, 8(7): 1223-1236.
doi: 10.1002/sec.v8.7 URL |
| [10] | XU Zhang, YANG Xiaoyuan, WEI Kang. Identity-Based Proxy Ring Signature on Lattice in the Standard Model[J]. Journal of Shandong University (Natural Science), 2015, 50(11):40-46. |
| 许章, 杨晓元, 魏康. 在标准模型下格上基于身份的代理环签名[J]. 山东大学学报(理学版), 2015, 50(11):40-46. | |
| [11] | LIU Lianhai, WANG Yujue, ZHANG Jingwei, et al. Efficient Proxy Ring Signature for VANET[J]. The Journal of Engineering, 2019(9): 5449-5454. |
| [12] | YUAN Yuqi, LIU Ning, ZHANG Yanshuo. Design of Identity-Based Proxy Ring Signature Scheme on ISRSAC[J]. Journal of Beijing Electronic Science and Technology Institute, 2023, 31(3):62-77. |
| 袁煜淇, 刘宁, 张艳硕. ISRSAC上基于身份的代理环签名方案设计[J]. 北京电子科技学院学报, 2023, 31(3):62-77. | |
| [13] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer.Cryptology-CRYPTO 1984. Heidelberg:Springer, 1984: 47-53. |
| [14] | GM/T0044-2016 Information Security Technology-Identity Based Cryptographic Algorithms SM9[S]. Beijing: Standards Press of China, 2016. |
| GM/T0044-2016 SM9标识密码算法[S]. 北京: 中国标准出版社, 2016. | |
| [15] | CHENG Zhaohui. Security Analysis of SM9 Key Agreement and Encryption[C]// Springer.Information Security and Cryptology:The 14th International Conference. Heidelberg:Springer, 2019: 3-25. |
| [16] | PENG Cong, HE Debiao, LUO Min, et al. An Identity-Based Ring Signature Scheme for SM9 Algorithm[J]. Journal of Cryptologic Research, 2021, 8(4):724-734. |
| 彭聪, 何德彪, 罗敏, 等. 基于SM9标识密码算法的环签名方案[J]. 密码学报, 2021, 8(4):724-734. | |
| [17] | LAI Jianchang, HUANG Xinyi, HE Debiao, et al. An Efficient Identity-Based Signcryption Scheme Based on SM9[J]. Journal of Cryptologic Research, 2021, 8(2):314-329. |
|
赖建昌, 黄欣沂, 何德彪, 等. 基于商密SM9的高效标识签密[J]. 密码学报, 2021, 8(2):314-329.
doi: 10.13868/j.cnki.jcr.000440 |
|
| [18] |
ZHANG Chao, PENG Changgen, DING Hongfa, et al. Searchable Encryption Scheme Based on China State Cryptography Standard SM9[J]. Computer Engineering, 2022, 48(7): 159-167.
doi: 10.19678/j.issn.1000-3428.0062771 |
|
张超, 彭长根, 丁红发, 等. 基于国密SM9的可搜索加密方案[J]. 计算机工程, 2022, 48(7):159-167.
doi: 10.19678/j.issn.1000-3428.0062771 |
|
| [19] | DING Yong, LUO Shidong, YANG Changsong, et al. An Identity-Based Deniable Ring Signature Scheme Based on SM9 Signature Algorithm[J]. Netinfo Security, 2024, 24(6):893-902. |
| 丁勇, 罗世东, 杨昌松, 等. 基于SM9标识密码算法的可否认环签名方案[J]. 信息网络安全, 2024, 24(6):893-902. | |
| [20] | SHAO Qing, ZHANG Leijun. Transaction Privacy Protection Scheme for Consortium Blockchain Utilizing SM9 and Blind Signature[J]. Journal of Chinese Computer Systems, 2025, 46(1):217-224. |
| 邵清, 张磊军. 结合SM9和盲签名的联盟链交易隐私保护方案[J]. 小型微型计算机系统, 2025, 46(1):217-224. | |
| [21] | HERRANZ J, SAEZ G. Forking Lemmas for Ring Signature Schemes[C]// Springer.International Conference on Cryptology (Indocrypt' 03). Heidelberg: Springer, 2003: 266-279. |
| [22] | BARRETO P S L M, LIBERT B, MCCULLAGH N, et al. Efficient and Provably-Secure Identity-Based Signatures and Signcryption from Bilinear Maps[C]// Springer. The 11th International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg:Springer, 2005: 515-532. |
| [23] | YUAN Sen. Research on Signature Scheme Based on SM Cryptographic Algorithm and Its Application[D]. Lanzhou: Northwest Normal University, 2022. |
| 袁森. 基于国密算法的签名方案及应用研究[D]. 兰州: 西北师范大学, 2022. |
| [1] | HUANG Wangwang, ZHOU Hua, WANG Daiqiang, ZHAO Qi. Design of Reconfigurable Key Security Authentication Protocol for IoT Based on National Cryptography SM9 [J]. Netinfo Security, 2024, 24(7): 1006-1014. |
| [2] | OUYANG Mengdi, SUN Qinshuo, LI Fagen. Subversion Attacks and Countermeasures of SM9 Encryption [J]. Netinfo Security, 2024, 24(6): 831-842. |
| [3] | DING Yong, LUO Shidong, YANG Changsong, LIANG Hai. An Identity-Based Deniable Ring Signature Scheme Based on SM9 Signature Algorithm [J]. Netinfo Security, 2024, 24(6): 893-902. |
| [4] | GUO Jiansheng, GUAN Feiting, LI Zhihui. A Dynamic (t,n) Threshold Quantum Secret Sharing Scheme with Cheating Identification [J]. Netinfo Security, 2024, 24(5): 745-755. |
| [5] | ZHANG Xuefeng, CHEN Tingting, MIAO Meixia, CHENG Yexia. Multi-Receiver Chaotic Key Generation Scheme Based on SM9 [J]. Netinfo Security, 2024, 24(4): 555-563. |
| [6] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [7] | YAN Hailong, WANG Shulan. Design and Implementation of Integrated Service Platform for Real Estate Registration Based on Domestic Cryptographic Technology [J]. Netinfo Security, 2024, 24(2): 303-308. |
| [8] | ZHU Guocheng, HE Debiao, AN Haoyang, PENG Cong. The Proxy Voting Scheme Based on the Blockchain and SM9 Digital Signature [J]. Netinfo Security, 2024, 24(1): 36-47. |
| [9] | ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption [J]. Netinfo Security, 2023, 23(9): 37-46. |
| [10] | AN Haoyang, HE Debiao, BAO Zijian, PENG Cong. A Certificate-Based Digital Signature Scheme [J]. Netinfo Security, 2023, 23(3): 13-21. |
| [11] | ZHANG Xuefeng, HU Yixiu. A Revocable Identity-Based Broadcast Encryption Scheme Based on SM9 [J]. Netinfo Security, 2023, 23(1): 28-35. |
| [12] | WANG Shengwen, HU Aiqun. Design of E-mail Encryption System Based on SM9 Algorithm [J]. Netinfo Security, 2022, 22(6): 53-60. |
| [13] | LI Li, BAI Lu, TU Hang, ZHANG Biao. Eff icient Implementation Scheme of Batch Verif ication Based on SM2 Signatures [J]. Netinfo Security, 2022, 22(5): 1-10. |
| [14] | WU Kehe, CHENG Rui, ZHENG Bihuang, CUI Wenchao. Research on Security Communication Protocol of Power Internet of Things [J]. Netinfo Security, 2021, 21(9): 8-15. |
| [15] | ZHANG Yu, SUN Guangmin, LI Yu. Research on Mobile Internet Authentication Scheme Based on SM9 Algorithm [J]. Netinfo Security, 2021, 21(4): 1-9. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||