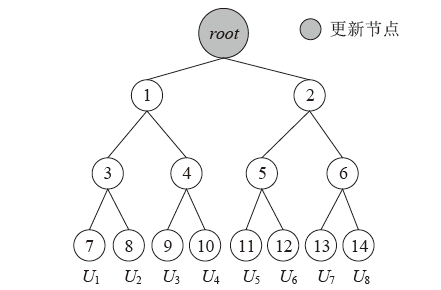
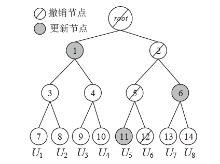
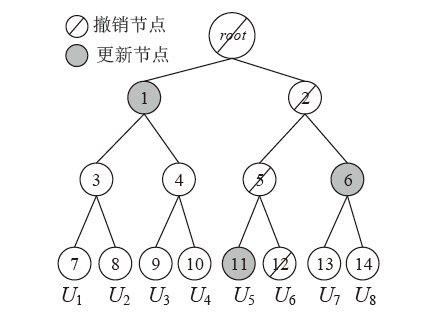
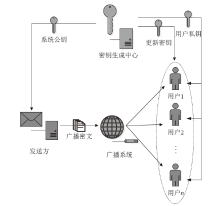
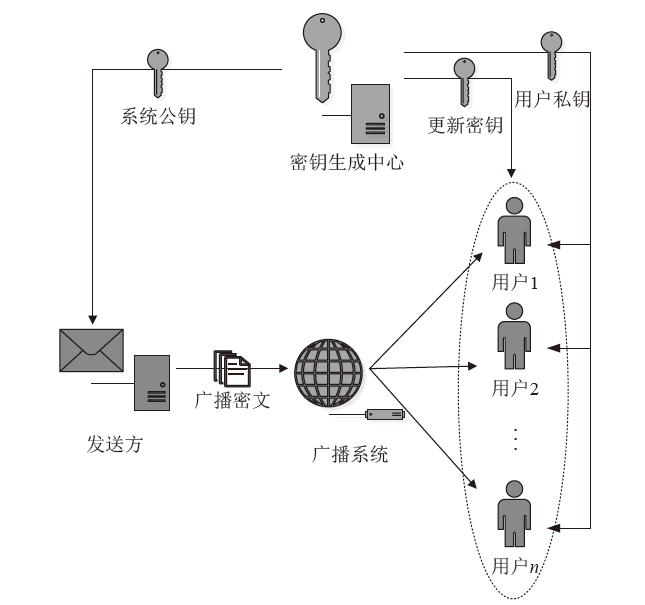
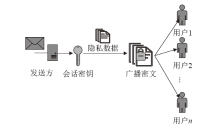
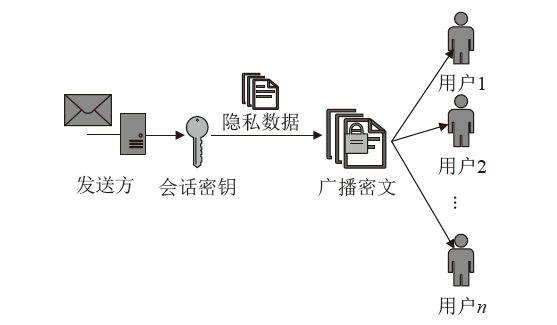
| [1] |
SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]//Springer. Advances in Cryptology-CRYPT0’84. Heidelberg:Springer, 1985: 47-53.
|
| [2] |
GM/T0044-2016 Information Security Technology-IdentityBased Cryptographic Algorithms SM9[S]. Beijing: Standards Press of China, 2016.
|
|
GM/T0044-2016 SM9标识密码算法[S]. 北京: 中国标准出版社, 2016.
|
| [3] |
CHENG Zhaohui. Security Analysis of SM9 Key Agreement and Encryption[C]// Springer. The 14th International Conference on Information Security and Cryptology. Heidelberg: Springer, 2018: 3-25
|
| [4] |
ZHANG Xuefeng, PENG Hua. Blind Signature Scheme Based on SM9 Algorithm[J]. Netinfo Security, 2019, 19(8): 61-67.
|
|
张雪锋, 彭华. 一种基于SM9算法的盲签名方案研究[J]. 信息网络安全, 2019, 19(8): 61-67.
|
| [5] |
YANG Yatao, CAI Juliang, ZHANG Xiaowei, et al. Privacy Preserving Scheme in Block Chain with Provably Secure Based on SM9 Algorithm[J]. Journal of Software, 2019, 30(6): 1692-1704.
|
|
杨亚涛, 蔡居良, 张筱薇, 等. 基于SM9算法可证明安全的区块链隐私保护方案[J]. 软件学报, 2019, 30(6):1692-1704.
|
| [6] |
LAI Jianchang, HUANG Xinyi, HE Debiao. An Efficient Identity-Based Broadcast Encryption Scheme Based on SM9[J]. Chinese Journal of Computers, 2021, 44(5): 897-907.
|
|
赖建昌, 黄欣沂, 何德彪. 一种基于商密SM9的高效标识广播加密方案[J]. 计算机学报, 2021, 44(5):897-907.
|
| [7] |
ZHANG Chao, PENG Changgen, DING Hongfa, et al. Searchable Encryption Scheme Based on China State Cryptography Standard SM9[J]. Computer Engineering, 2022, 48(7): 159-167.
|
|
张超, 彭长根, 丁红发, 等. 基于国密SM9的可搜索加密方案[J]. 计算机工程, 2022, 48(7):159-167.
|
| [8] |
ZHANG Boxin, GENG Shengling, QIN Baodong. Efficient Revocable SM9 Identity-Based Signature Algorithm[J]. Application Research of Computers, 2022, 39(9): 2837-2842, 2849.
|
|
张博鑫, 耿生玲, 秦宝东. 高效的可撤销SM9标识签名算法[J]. 计算机应用研究, 2022, 39(9):2837-2842,2849.
|
| [9] |
ZHAO Chenyang, KE Pinhui, LIN Changlu. SM9 Identity-Based Encryption Algorithm with Deniable Authenticatison[EB/OL]. (2022-10-26)[2022-11-08]. http://kns.cnki.net/kcms/detail/11.5602.TP.20221025.1814.006.html.
|
|
赵晨阳, 柯品惠, 林昌露. 具有否认认证的SM9标识加密算法[EB/OL]. (2022-10-26)[2022-11-08]. http://kns.cnki.net/kcms/detail/11.5602.TP.20221025.1814.006.html.
|
| [10] |
ZHU Liufu, LI Jiguo, LAI Jianchang, et al. Attribute-Based Online/Offline Signature Scheme Based on SM9[EB/OL]. (2022-10-28)[2022-11-08]. http://kns.cnki.net/kcms/detail/11.1777.TP.20221027.1044.006.html.
|
|
朱留富, 李继国, 赖建昌, 等. 基于商密SM9的属性基在线/离线签名方案[EB/OL]. (2022-10-28)[2022-11-08]. http://kns.cnki.net/kcms/detail/11.1777.TP.20221027.1044.006.html.
|
| [11] |
BONEH D, FRANKLIN M. Identity-Based Encryption from the Weil Pairing[J]. SIAM Journal on Computing, 2003, 32(3): 213-229.
|
| [12] |
BOLDYREVA A, GOYAL V, KUMAR V. Identity-Based Encryption with Efficient Revocation[C]// ACM. The 15th ACM Conference on Computer and Communications Security. New York: ACM, 2008: 417-426.
|
| [13] |
SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// Springer. The 11th Advances in Cryptology-Eurocrypt. Heidelberg: Springer, 2005: 457-473.
|
| [14] |
FIAT A, NAOR M. Broadcast Encryption[J]. Lecture Notes in Computer Science, 1994, 773(1): 480-491.
|
| [15] |
NAOR D, NAOR M, LOTSPIECH J. Revocation and Tracing Schemes for Stateless Receivers[C]// Springer. Advances in Cryptology-CRYPTO 2001. Heidelberg: Springer, 2001: 41-62.
|
| [16] |
DELERABLEE C. Identity-Based Broadcast Encryption with Constant Size Ciphertexts and Private Keys[C]// Springer. Advances in Cryptology-ASIACRYPT 2007. Heidelberg: Springer, 2007: 200-215.
|
| [17] |
JIANG Peng, GUO Fuchun, MU Yi. Efficient Identity-Based Broadcast Encryption with Keyword Search Against Insider Attacks for Database Systems[J]. Theoretical Computer Science, 2019, 767: 51-72.
doi: 10.1016/j.tcs.2018.09.030
URL
|