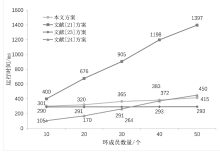
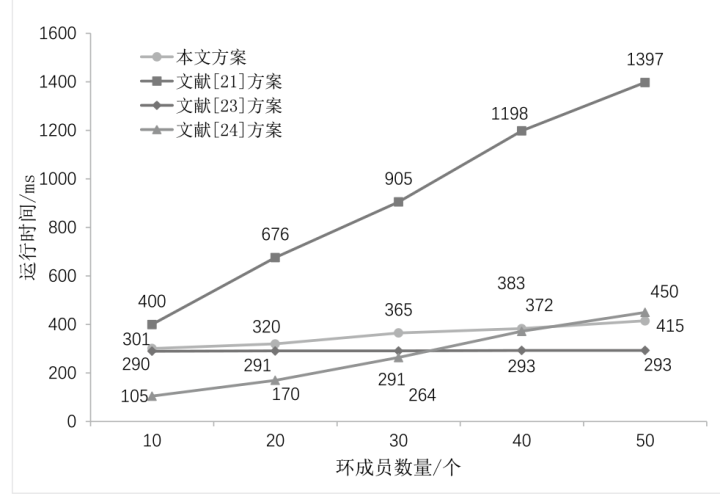
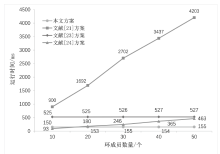
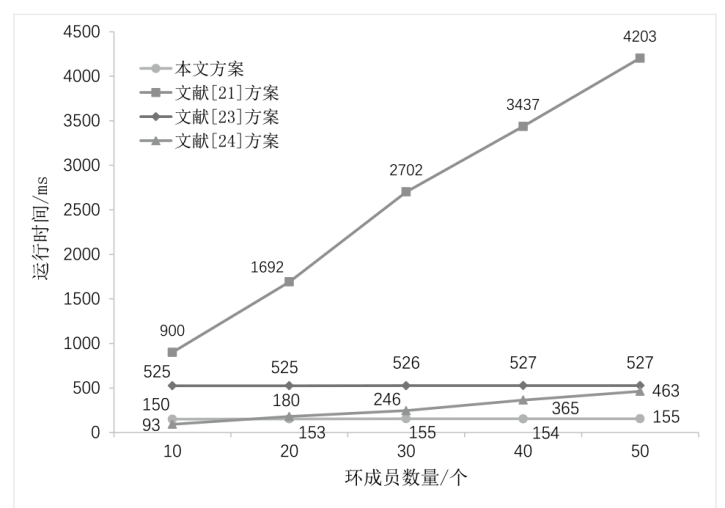
Netinfo Security ›› 2024, Vol. 24 ›› Issue (6): 893-902.doi: 10.3969/j.issn.1671-1122.2024.06.007
Previous Articles Next Articles
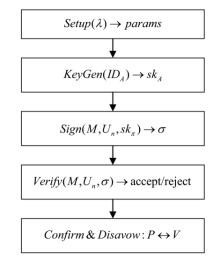
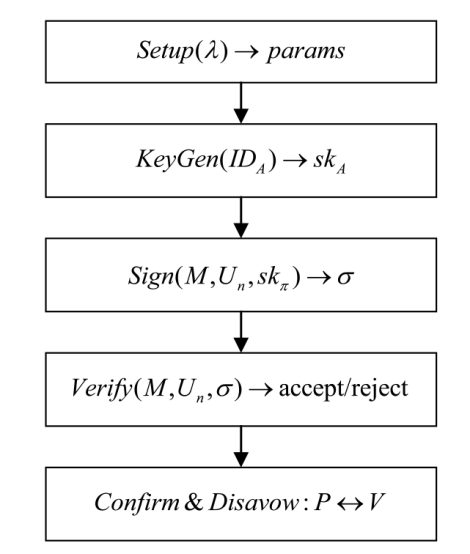
An Identity-Based Deniable Ring Signature Scheme Based on SM9 Signature Algorithm
DING Yong1,2, LUO Shidong1,2, YANG Changsong1,2( ), LIANG Hai1,2
), LIANG Hai1,2
- 1. Guangxi Key Laboratory of Cryptography and Information Security, Guilin University of Electronic Technology, Guilin 541004, China
2. Guangxi Engineering Research Center of Industrial Internet Security and Blockchain, Guilin University of Electronic Technology, Guilin 541004, China
-
Received:2024-04-20Online:2024-06-10Published:2024-07-05
CLC Number:
Cite this article
DING Yong, LUO Shidong, YANG Changsong, LIANG Hai. An Identity-Based Deniable Ring Signature Scheme Based on SM9 Signature Algorithm[J]. Netinfo Security, 2024, 24(6): 893-902.
share this article
| [1] | RIVEST R L, SHAMIR A, TAUMAN Y. How to Leak a Secret[C]// Springer. Advances in Cryptology—ASIACRYPT 2001: 7th International Conference on the Theory and Application of Cryptology and Information Security Gold Coast. Heidelberg: Springer, 2001: 552-565. |
| [2] | QIU Chi, ZHANG Shibin, CHANG Yan, et al. Electronic Voting Scheme Based on a Quantum Ring Signature[J]. International Journal of Theoretical Physics, 2021, 60: 1550-1555. |
| [3] | KOMANO Y, OHTA K, SHIMBO A, et al. Toward the Fair Anonymous Signatures: Deniable Ring Signatures[C]// Springer. Cryptographers’ Track at the RSA Conference. Heidelberg: Springer, 2006: 174-191. |
| [4] | WU Qianhong, SUSILO W, MU Yi, et al. Ad Hoc Group Signatures[C]// Springer. International Workshop on Security. Heidelberg: Springer, 2006: 120-135. |
| [5] | CAMENISCH J, MICHELS M. A Group Signature Scheme Based on an RSA-Variant[J]. BRICS Report Series, 1998, 5(27): 160-174. |
| [6] | BENALOH J, DE M M. One-Way Accumulators: A Decentralized Alternative to Digital Signatures[C]// Springer. Workshop on the Theory and Application of Cryptographic Techniques. Heidelberg: Springer, 1993: 274-285. |
| [7] | LIU D Y W, LIU J K, MU Yi, et al. Revocable Ring Signature[J]. Journal of Computer Science and Technology, 2007, 22: 785-794. |
| [8] | ZENG Shengke, JIANG Shaoquan, QIN Zhiguang. An Efficient Conditionally Anonymous Ring Signature in the Random Oracle Model[J]. Theoretical Computer Science, 2012, 461: 106-114. |
| [9] | ZENG Shengke, LI Qinyi, QIN Zhiguang, et al. Non-Interactive Deniable Ring Signature without Random Oracles[J]. Security and Communication Networks, 2016, 9(12): 1810-1819. |
| [10] | GAO Wen, CHEN Liqun, HU Yupu, et al. Lattice-Based Deniable Ring Signatures[J]. International Journal of Information Security, 2019, 18: 355-370. |
| [11] | PARK S, SEALFON A. It Wasn’t Me! Repudiability and Claimability of Ring Signatures[C]// Springer. Advances in Cryptology-CRYPTO 2019: 39th Annual International Cryptology Conference. Heidelberg: Springer, 2019: 159-190. |
| [12] | JIA Huiwen, TANG Chunming, ZHANG Yanhua. Lattice-Based Logarithmic-Size Non-Interactive Deniable Ring Signatures[J]. Entropy, 2021, 23(8): 980. |
| [13] | LIN Hao, WANG Mingqiang. Repudiable Ring Signature: Stronger Security and Logarithmic-Size[EB/OL]. (2022-03-01)[2024-04-15]. https://api.semanticscholar.org/CorpusID:207988596. |
| [14] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. Advances in Cryptology:Proceedings of CRYPTO 84 4. Heidelberg: Springer, 1985: 47-53. |
| [15] | ZHANG Fangguo, KIM K. ID-Based Blind Signature and Ring Signature from Pairings[C]// Springer. Advances in Cryptology-ASIACRYPT 2002. Heidelberg: Springer, 2002: 533-547. |
| [16] | LIN C Y, WU T C. An Identity-Based Ring Signature Scheme from Bilinear Pairings[C]// IEEE. 18th International Conference on Advanced Information Networking and Applications. New York: IEEE, 2004: 182-185. |
| [17] | CHOW S S M, YIU S M, HUI L C K. Efficient Identity Based Ring Signature[C]// Springer. Applied Cryptography and Network Security. Heidelberg: Springer, 2005: 499-512. |
| [18] | AU M H, LIU J K, SUSILO W, et al. Constant-Size ID-Based Linkable and Revocable-iff-Linked Ring Signature[C]// Springer. Progress in Cryptology-INDOCRYPT 2006. Heidelberg: Springer, 2006: 364-378. |
| [19] | XIE Zongxiao, DONG Kunxiang, ZHEN Jie. International Standardization of Domestic Commercial Cryptographic Algorithms and Their Corresponding Relations[J]. China Quality and Standards Review, 2021(5): 20-23, 29. |
| 谢宗晓, 董坤祥, 甄杰. 国产商用密码算法的国际标准化及其对应关系[J]. 中国质量与标准导报, 2021(5): 20-23,29. | |
| [20] | FAN Qing, HE Debiao, LUO Min, et al. Ring Signature Schemes Based on SM2 Digital Signature Algorithm[J]. Journal of Cryptologic Research, 2021, 8(4): 710-723. |
| 范青, 何德彪, 罗敏, 等. 基于SM2数字签名算法的环签名方案[J]. 密码学报, 2021, 8(4):710-723. | |
| [21] | PENG Cong, HE Debiao, LUO Min, et al. An Identity-Based Ring Signature Scheme for SM9 Algorithm[J]. Journal of Cryptologic Research, 2021, 8(4): 724-734. |
| 彭聪, 何德彪, 罗敏, 等. 基于SM9标识密码算法的环签名方案[J]. 密码学报, 2021, 8(4):724-734. | |
| [22] |
RAO Jintao, CUI Zhe. Secure E-Voting Protocol Based on SM9 Blind Signature and Ring Signature[J]. Computer Engineering, 2023, 49(6): 13-23, 33.
doi: 10.19678/j.issn.1000-3428.0066576 |
|
饶金涛, 崔喆. 基于SM9盲签名与环签名的安全电子选举协议[J]. 计算机工程, 2023, 49(6):13-23,33.
doi: 10.19678/j.issn.1000-3428.0066576 |
|
| [23] | AN Haoyang, HE Debiao, BAO Zijian, et al. Ring Signature Based on the SM9 Digital Signature and Its Application in Blockchain Privacy Protection[J]. Journal of Computer Research and Development, 2023, 60(11): 2545-2554. |
| 安浩杨, 何德彪, 包子健, 等. 基于SM9数字签名的环签名及其在区块链隐私保护中的应用[J]. 计算机研究与发展, 2023, 60(11):2545-2554. | |
| [24] | BAO Zijian, HE Debiao, PENG Cong, et al. Deniable Ring Signature Scheme Based on SM2 Digital Signature Algorithm[J]. Journal of Cryptologic Research, 2023, 10(2): 264-275. |
| 包子健, 何德彪, 彭聪, 等. 基于SM2数字签名算法的可否认环签名[J]. 密码学报, 2023, 10(2):264-275. | |
| [25] | HERRANZ J, SÁEZ G. Forking Lemmas for Ring Signature Schemes[C]// Springer. International Conference on Cryptology. Heidelberg: Springer, 2003: 266-279. |
| [26] | BARRETO P S L M, LIBERT B, MCCULLAGH N, et al. Efficient and Provably-Secure Identity-Based Signatures and Signcryption from Bilinear Maps[C]// Springer. Advances in Cryptology-ASIACRYPT 2005. Heidelberg: Springer, 2005: 515-532. |
| [27] | PEREIRA G C C F, SIMPLÍCIO J M A, NAEHRIG M, et al. A Family of Implementation-Friendly BN Elliptic Curves[J]. Journal of Systems and Software, 2011, 84(8): 1319-1326. |
| [1] | OUYANG Mengdi, SUN Qinshuo, LI Fagen. Subversion Attacks and Countermeasures of SM9 Encryption [J]. Netinfo Security, 2024, 24(6): 831-842. |
| [2] | ZHANG Xuefeng, CHEN Tingting, MIAO Meixia, CHENG Yexia. Multi-Receiver Chaotic Key Generation Scheme Based on SM9 [J]. Netinfo Security, 2024, 24(4): 555-563. |
| [3] | ZHANG Yanshuo, YUAN Yuqi, LI Liqiu, YANG Yatao, QIN Xiaohong. Periodically Deniable Ring Signature Scheme Based on SM2 Digital Signature Algorithm [J]. Netinfo Security, 2024, 24(4): 564-573. |
| [4] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [5] | ZHU Guocheng, HE Debiao, AN Haoyang, PENG Cong. The Proxy Voting Scheme Based on the Blockchain and SM9 Digital Signature [J]. Netinfo Security, 2024, 24(1): 36-47. |
| [6] | ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption [J]. Netinfo Security, 2023, 23(9): 37-46. |
| [7] | AN Haoyang, HE Debiao, BAO Zijian, PENG Cong. A Certificate-Based Digital Signature Scheme [J]. Netinfo Security, 2023, 23(3): 13-21. |
| [8] | ZHANG Xuefeng, HU Yixiu. A Revocable Identity-Based Broadcast Encryption Scheme Based on SM9 [J]. Netinfo Security, 2023, 23(1): 28-35. |
| [9] | WANG Shengwen, HU Aiqun. Design of E-mail Encryption System Based on SM9 Algorithm [J]. Netinfo Security, 2022, 22(6): 53-60. |
| [10] | YI Zhengge, YUAN Wenyong, LI Ruifeng, YANG Xiaoyuan. Identity-based and Dynamic Operating Solution for Cloud Storage [J]. Netinfo Security, 2022, 22(2): 86-95. |
| [11] | WU Kehe, CHENG Rui, ZHENG Bihuang, CUI Wenchao. Research on Security Communication Protocol of Power Internet of Things [J]. Netinfo Security, 2021, 21(9): 8-15. |
| [12] | ZHANG Yu, SUN Guangmin, LI Yu. Research on Mobile Internet Authentication Scheme Based on SM9 Algorithm [J]. Netinfo Security, 2021, 21(4): 1-9. |
| [13] | Yihua ZHOU, Zhuqing LV, Yuguang YANG, Weimin SHI. Data Deposit Management System Based on Blockchain Technology [J]. Netinfo Security, 2019, 19(8): 8-14. |
| [14] | Xuefeng ZHANG, Hua PENG. Blind Signature Scheme Based on SM9 Algorithm [J]. Netinfo Security, 2019, 19(8): 61-67. |
| [15] | Huifang YU, Xinzhe GAO. Homomorphic Ring Signature Scheme Technology for Multi-source Network Coding [J]. Netinfo Security, 2019, 19(2): 36-42. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||