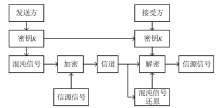
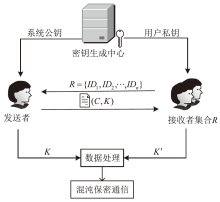
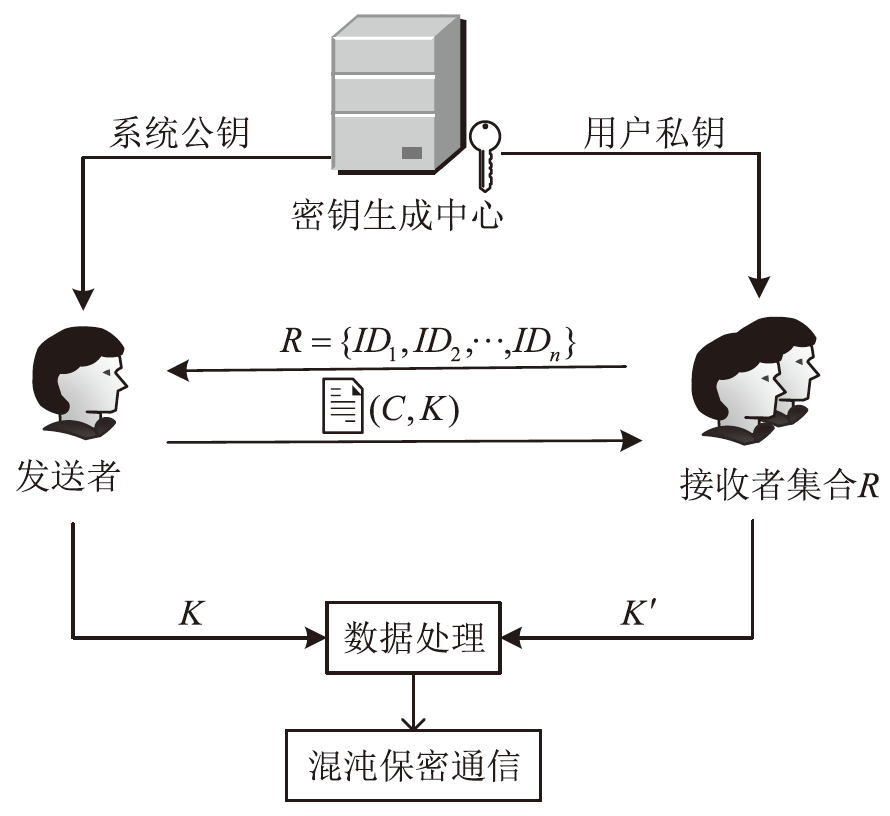
| [1] |
ZAREBNIA M, PAKMANESH H, PARVAZ R. A Fast Multiple-Image Encryption Algorithm Based on Hybrid Chaotic Systems for Gray Scale Images[J]. Optik, 2019, 179: 761-773.
|
| [2] |
ZHANG Xuefeng, WEI Kaili, JIANG Wen. A N-Dimensional Combined Chaotic Map and Its Performance Analysis[J]. Journal of Xi’an University of Posts and Telecommunications, 2020, 25(6): 52-62.
|
|
张雪锋, 卫凯莉, 姜文. 一种n维组合混沌映射及性能分析[J]. 西安邮电大学学报, 2020, 25(6): 52-62.
|
| [3] |
CHEN Mingqi, HONG Xuehai, WANG Wei, et al. The Development Trends of the Network Security and Information Technology[J]. Netinfo Security, 2015, 15(4): 1-4.
|
|
陈明奇, 洪学海, 王伟, 等. 关于网络安全和信息技术发展态势的思考[J]. 信息网络安全, 2015, 15(4): 1-4.
|
| [4] |
CHEN Huashan, PI Lan, LIU Feng, et al. Research on Frontier and Trends of Science of Cybersecurity[J]. Netinfo Security, 2015, 15(3): 1-5.
|
|
陈华山, 皮兰, 刘峰, 等. 网络空间安全科学基础的研究前沿及发展趋势[J]. 信息网络安全, 2015, 15(3): 1-5.
|
| [5] |
SHANNON C E. Communication Theory of Secrecy Systems[J]. The Bell System Technical Journal, 1949, 28(4): 656-715.
|
| [6] |
DIFFIE W, HELLMAN M. New Directions in Cryptography[J]. IEEE Transactions on Information Theory, 1976, 22(6): 644-654.
|
| [7] |
SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. Advances in Cryptology-CRYPT0’84. Heidelberg:Springer, 1985: 47-53.
|
| [8] |
BONEH D, FRANKLIN M. Identity-Based Encryption from the Weil Pairing[J]. SIAM Journal on Computing, 2003, 32(3): 213-229.
|
| [9] |
DELERABLEE C. Identity-Based Broadcast Encryption with Constant Size Ciphertexts and Private Keys[C]// Springer. Advances in Cryptology-ASIACRYPT 2007. Heidelberg: Springer, 2007: 200-215.
|
| [10] |
LIU Xiao, LIU Weiran, WU Qianhong, et al. Chosen Ciphertext Secure Identity-Based Broadcast Encryption[J]. Journal of Cryptologic Research, 2015(1): 66-76.
|
|
刘潇, 刘巍然, 伍前红, 等. 选择密文安全的基于身份的广播加密方案[J]. 密码学报, 2015 (1): 66-76.
doi: 10.13868/j.cnki.jcr.000061
|
| [11] |
GM/T0044-2016 Information Security Technology-Identity Based Cryptographic Algorithms SM9[S]. Beijing: Standards Press of China, 2016.
|
|
GM/T0044-2016 SM9 标识密码算法[S]. 北京: 中国标准出版社, 2016.
|
| [12] |
ZHANG Xuefeng, PENG Hua. Blind Signature Scheme Based on SM9 Algorithm[J]. Netinfo Security, 2019, 19(8): 61-67.
|
|
张雪锋, 彭华. 一种基于 SM9 算法的盲签名方案研究[J]. 信息网络安全, 2019, 19(8): 61-67.
|
| [13] |
PENG Cong, HE Debiao, LUO Min, et al. An Identity-Based Ring Signature Scheme for SM9 Algorithm[J]. Journal of Cryptologic Research, 2021, 8(4): 724-734.
|
|
彭聪, 何德彪, 罗敏, 等. 基于SM9 标识密码算法的环签名方案[J]. 密码学报, 2021, 8(4): 724-734.
|
| [14] |
LAI Jianchang, HUANG Xinyi, HE Debiao, et al. An Efficient Identity-Based Signcryption Scheme Based on SM9[J]. Journal of Cryptologic Research, 2021, 8(2): 314-329.
|
|
赖建昌, 黄欣沂, 何德彪, 等. 基于商密 SM9 的高效标识签密[J]. 密码学报, 2021, 8(2): 314-329.
doi: 10.13868/j.cnki.jcr.000440
|
| [15] |
ZHANG Chao, PENG Changgen, DING Hongfa, et al. Searchable Encryption Scheme Based on China State Cryptography Standard SM9[J]. Computer Engineering, 2022, 48(7): 159-167.
doi: 10.19678/j.issn.1000-3428.0062771
|
|
张超, 彭长根, 丁红发, 等. 基于国密SM9的可搜索加密方案[J]. 计算机工程, 2022, 48 (7): 159-167.
doi: 10.19678/j.issn.1000-3428.0062771
|
| [16] |
CAMPAGNA M, PETCHER A. Security of Hybrid Key Encapsulation[J]. Cryptology ePrint Archive, 2020, 1364-1379.
|
| [17] |
SMART N P. Efficient Key Encapsulation to Multiple Parties[C]// Springer. International Conference on Security in Communication Networks. Heidelberg: Springer, 2004: 208-219.
|
| [18] |
BARBOSA M, FARSHIM P. Efficient Identity-Based Key Encapsulation to Multiple Parties[C]// Springer. IMA’05. Heidelberg:Springer, 2005: 428-441.
|
| [19] |
FU Xiaotong, XUE Peng. Identity-Based Privacy-Preserving Multi-Receiver Key Encapsulation[J]. Journal of Xidian University, 2014, 41(5): 7-12.
|
|
傅晓彤, 薛鹏. 一种匿名的多接收者密钥封装机制[J]. 西安电子科技大学学报, 2014, 41(5): 7-12.
|
| [20] |
KIM J, CAMTEPE S, SUSILO W, et al. Identity-Based Broadcast Encryption with Outsourced Partial Decryption for Hybrid Security Models in Edge Computing[C]// ACM. Asia CCS’19. New York:ACM, 2019: 55-66.
|
| [21] |
BARRETO P, LIBERT B, MCCULLAGH N, et al. Efficient and Provably-Secure Identity-Based Signatures and Signcryption from Bilinear Maps[C]// Springer. Advances in Cryptology-ASIACRYPT 2005. Heidelberg: Springer, 2005: 515-532.
|
| [22] |
DENG Hua, QIN Zheng, WU Qianhong, et al. Identity-Based Encryption Transformation for Flexible Sharing of Encrypted Data in Public Cloud[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 3168-3180.
|
 ), MIAO Meixia1, CHENG Yexia2
), MIAO Meixia1, CHENG Yexia2