Netinfo Security ›› 2025, Vol. 25 ›› Issue (11): 1658-1672.doi: 10.3969/j.issn.1671-1122.2025.11.002
Previous Articles Next Articles
Heterogeneous CPU-GPU System Confidential Computing Survey
HAO Meng1, LI Jiayong1( ), YANG Hongwei1, ZHANG Weizhe1,2,3
), YANG Hongwei1, ZHANG Weizhe1,2,3
1. School of Cyberspace Science ,Harbin Institute of Technology Harbin 150001, China 2. School of Computer Science and Technology ,Harbin Institute of Technology (Shenzhen) Shenzhen 518055, China 3. Peng Cheng Laboratory Shenzhen 518055, China
-
Received:2025-07-20Online:2025-11-10Published:2025-12-02
CLC Number:
Cite this article
HAO Meng, LI Jiayong, YANG Hongwei, ZHANG Weizhe. Heterogeneous CPU-GPU System Confidential Computing Survey[J]. Netinfo Security, 2025, 25(11): 1658-1672.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.11.002
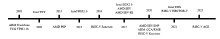
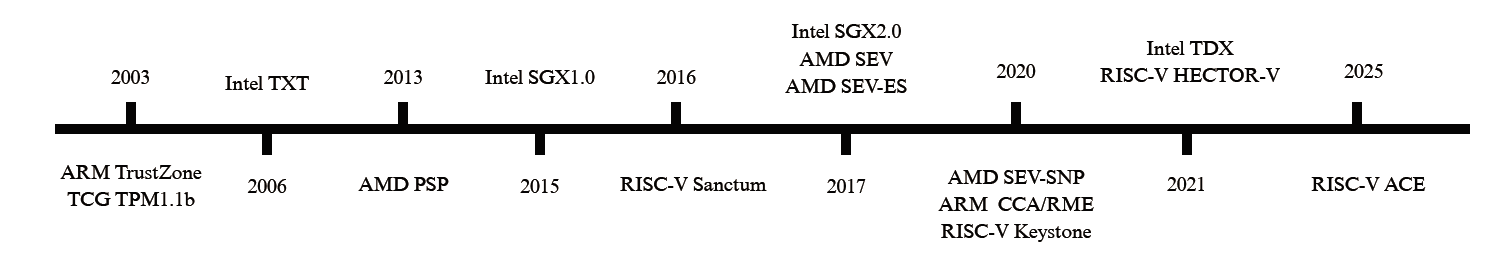
| 架构 | 技术 | 发布年份 | 隔离模型 | 核心硬件/机制 |
|---|---|---|---|---|
| x86 | TCG TPM 1.1b | 2003 | 静态测量信任根 | PCRs,CRTM,加密协处理器 |
| Intel TXT | 2006 | 动态测量信任根 | GETSEC指令,SINIT ACM,动态PCRs | |
| Intel SGX | 2015 | 应用程序飞地 | ENCLU/ENCLS指令,EPC,EPCM | |
| AMD SEV | 2017 | 机密虚拟机 | AMD-SP,内存控制器AES引擎 | |
| AMD SEV-SNP | 2020 | 机密虚拟机 | SEV机制 + RMP | |
| Intel TDX | 2021 | 机密虚拟机 | VMX,MKTME,SEAM模式,TDX模块 | |
| ARM | TrustZone | 2003 | 系统分区 | NS-bit,安全监视器,TZASC/TZPC |
| CCA / RME | 2020 | 机密虚拟机 | Realm/Root世界,GPT,RMM固件 | |
| RISC-V | Sanctum | 2016 | 应用程序飞地 | PMP |
| Keystone | 2020 | 应用程序飞地 (框架) | PMP,可定制的安全监视器(SM)和运行时(RT) | |
| HECTOR-V | 2021 | 协处理器 | 异构多核,专用的安全协处理器 | |
| ACE | 2025 | 机密虚拟机 | H-extension,PMP,形式化验证的TSM |
| 硬件依赖 | 性能开销(典型) | 保护方法 | |
|---|---|---|---|
| Graviton | 高(需改GPU) | 17%~33% | 修改GPU命令处理器;PMM |
| HIX StrongBox | 低(需改CPU/平台) 无(利用现有ARM特性) | 平均26% 4.7%~15.3% | CPU侧IOMMU/PCIe扩展;GPU飞地;ARM TrustZone;Stage-2地址翻译 |
| CAGE | 无(利用现有ARM特性) | 平均2.45% | ARM CCA;影子任务;双向隔离 |
| HETEE | 高(需专用HETEE Box) | 小于2.2% | 机架级PCIe物理隔离 |
| Honeycomb | 无(需CPU TEE) | 2%(大模型) | 静态二进制验证;双重监控器 |
| SAGE | 无(需CPU TEE) | 验证阶段开销;执行时无损 | 基于时间的执行证明 |
| H100 | 高(专用GPU) | — | 硬件防火墙;端到端PCIe加密 |
| [1] | KHOKHAR A A, PRASANNA V K, SHAABAN M E, et al. Heterogeneous Computing: Challenges and Opportunities[J]. Computer, 2002, 26(6): 18-27. |
| [2] | MITTAL S, VETTER J S. A Survey of CPU-GPU Heterogeneous Computing Techniques[J]. ACM Computing Surveys (CSUR), 2015, 47(4): 1-35. |
| [3] | WANG Wei, HU Yin, CHEN Lianmu, et al. Accelerating Fully Homomorphic Encryption Using GPU[C]// IEEE. 2012 IEEE Conference on High Performance Extreme Computing. New York: IEEE, 2012: 1-5. |
| [4] | KNOTT B, VENKATARAMAN S, HANNUN A, et al. Crypten: Secure Multi-Party Computation Meets Machine Learning[J]. Advances in Neural Information Processing Systems, 2021, 34: 4961-4973. |
| [5] | VOLOS S, VASWANI K, BRUNO R. Graviton: Trusted Execution Environments on GPUs[C]// USENIX. The 13th USENIX Symposium on Operating Systems Design and Implementation. Berkeley: USENIX, 2018: 681-696. |
| [6] | COSTAN V, DEVADAS S. Intel SGX Explained[EB/OL]. (2017-02-21)[2025-06-30]. https://eprint.iacr.org/2016/086.pdf. |
| [7] | AMD. AMD Secure Encrypted Virtualization (SEV)[EB/OL]. (2020-01-01) [2025-06-30]. https://www.amd.com/en/developer/sev.html. |
| [8] | Confidential Computing Consortium. A Technical Analysis of Confidential Computing[EB/OL]. (2023-03-10)[2025-06-30]. https://confidentialcomputing.io/wp-content/uploads/sites/10/2023/03/CCC-A-Technical-Analysis-of-Confidential-Computing-v1.3_unlocked.pdf. |
| [9] | Trusted Computing Group. TCPA_Main_TCG_Architecture[EB/OL]. (2002-02-22)[2025-06-30]. https://trustedcomputinggroup.org/wp-content/uploads/TCPA_Main_TCG_Architecture_v1_1b.pdf. |
| [10] | JAMES G. Intel Trusted Execution Technology: Hardware-Based Technology for Enhancing Server Platform Security[EB/OL]. (2009-06-12)[2025-06-30]. https://www.intel.com/content/dam/www/public/us/en/documents/white-papers/trusted-execution-technology-security-paper.pdf. |
| [11] | MCKEEN F, ALEXANDROVICH I, BERENZON A, et al. Innovative Instructions and Software Model for Isolated Execution[EB/OL]. (2013-06-23) [2025-06-30]. https://doi.org/10.1145/2487726.2488368. |
| [12] | Intel. Intel® 64 and IA-32 Architectures Software Developer’s Manual[EB/OL]. (2017-07-20)[2025-06-30]. https://ia600105.us.archive.org/6/items/Intel_64_and_IA-32_Architectures_Software_Developer_s_Manual_2017_07/325462-sdm-vol-1-2abcd-3abcd.pdf. |
| [13] | KAPLAN D, POWELL J, WOLLER T. AMD Memory Encryption[EB/OL]. (2021-10-18)[2025-06-30]. https://docs.amd.com/v/u/en-US/memory-encryption-white-paper. |
| [14] | AMD. AMD SEV-SNP: Strengthening VM Isolation with Integrity Protection and More[EB/OL]. (2020-01-01)[2025-06-30]. https://docs.amd.com/v/u/en-US/SEV-SNP-strengthening-vm-isolation-with-integrity-protection-and-more. |
| [15] | Intel. Intel® Trust Domain Extensions[EB/OL]. (2021-05-01) [2025-06-30]. https://cdrdv2.intel.com/v1/dl/getContent/690419. |
| [16] | ARM. ARM Security Technology Building a Secure System Using TrustZone Technology[EB/OL]. (2008-12-01)[2025-06-30]. https://developer.arm.com/documentation/PRD29-GENC-009492/latest/. |
| [17] | PINTO S, SANTOS N. Demystifying ARM Trustzone: A Comprehensive Survey[J]. ACM Computing Surveys (CSUR), 2019, 51(6): 1-36. |
| [18] | ARM. ARM CCA Will Put Confidential Compute in the Hands of Every Developer[EB/OL]. (2021-06-23)[2025-06-30]. https://newsroom.arm.com/news/arm-cca-will-put-confidential-compute-in-the-hands-of-every-developer. |
| [19] | ARM. ARM Realm Management Extension(RME) System Architecture[EB/OL]. (2021-06-23)[2025-06-30]. https://developer.arm.com/documentation/den0129/latest/. |
| [20] | TF-HAFNIUM. Hafnium Is the Secure Partition Manager(SPM) Reference Implementation[EB/OL]. (2018-06-28)[2025-06-30]. https://github.com/TF-Hafnium/hafnium. |
| [21] | COSTAN V, LEBEDEV I, DEVADAS S. Sanctum: Minimal Hardware Extensions for Strong Software Isolation[C]// USENIX. The 25th USENIX Security Symposium. Berkeley: USENIX, 2016: 857-874. |
| [22] | LEE D, KOHLBRENNER D, SHINDE S, et al. Keystone: An Open Framework for Architecting Trusted Execution Environments[C]// ACM. The Fifteenth European Conference on Computer Systems. New York: ACM, 2020: 1-16. |
| [23] | NASAHL P, SCHILLING R, WERNER M, et al. HECTOR-V: A Heterogeneous CPU Architecture for a Secure RISC-V Execution Environment[C]// ACM. The 2021 ACM Asia Conference on Computer and Communications Security. New York: ACM, 2021: 187-199. |
| [24] | OZGA W, HUNT G D H, LE M V, et al. ACE: Confidential Computing for Embedded RISC-V Systems[EB/OL]. (2025-05-19) [2025-06-30]. https://arxiv.org/abs/2505.12995. |
| [25] | DUTTA S B, NAGHIBIJOUYBARI H, ABU-GHAZALEH N, et al. Leaky Buddies: Cross-Component Covert Channels on Integrated CPU-GPU Systems[C]// IEEE. 2021 ACM/IEEE 48th Annual International Symposium on Computer Architecture (ISCA). New York: IEEE, 2021: 972-984. |
| [26] | NAGHIBIJOUYBARI H, KHASAWNEH K N, ABU-GHAZALEH N. Constructing and Characterizing Covert Channels on GPGPUs[C]// ACM. The 50th Annual IEEE/ACM International Symposium on Microarchitecture. New York: ACM, 2017: 354-366. |
| [27] | AHN J, KIM J, KASAN H, et al. Network-on-Chip Microarchitecture-Based Covert Channel in GPUs[C]// ACM. The 54th Annual IEEE/ACM International Symposium on Microarchitecture. New York: ACM, 2021: 565-577. |
| [28] | DUTTA S B, NAGHIBIJOUYBARI H, GUPTA A, et al. Spy in the GPU-Box: Covert and Side Channel Attacks on Multi-GPU Systems[C]// ACM. The 50th Annual International Symposium on Computer Architecture. New York: ACM, 2023: 1-13. |
| [29] | ZHANG Zhenkai, ALLEN T, YAO Fan, et al. Tunnels for Bootlegging: Fully Reverse-Engineering GPU TLBs for Challenging Isolation Guarantees of NVIDIA MIG[C]// ACM. The 2023 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2023: 960-974. |
| [30] | ZHU Yuankun, CHENG Yueqiang, ZHOU Husheng, et al. Hermes Attack: Steal DNN Models With Lossless Inference Accuracy[C]// USENIX. The 30th USENIX Security Symposium. Berkeley: USENIX, 2021: 889-906. |
| [31] | HU Xing, LIANG Ling, LI Shuangchen, et al. Deepsniffer: A DNN Model Extraction Framework Based on Learning Architectural Hints[C]// ACM. The 25th International Conference on Architectural Support for Programming Languages and Operating Systems. New York: ACM, 2020: 385-399. |
| [32] | LUO Chao, FEI Yunsi, LUO Pei, et al. Side-Channel Power Analysis of a GPU AES Implementation[C]// IEEE. 2015 33rd IEEE International Conference on Computer Design (ICCD). New York: IEEE, 2015: 281-288. |
| [33] | GAO Yiwen, ZHANG Hailong, CHENG Wei, et al. Electro-Magnetic Analysis of GPU-Based AES Implementation[C]// ACM. The 55th Annual Design Automation Conference. New York: ACM, 2018: 1-6. |
| [34] | ZHAN Zihao, ZHANG Zhenkai, LIANG Sisheng, et al. Graphics Peeping Unit: Exploiting EM Side-Channel Information of GPUs to Eavesdrop on Your Neighbors[C]// IEEE. 2022 IEEE Symposium on Security and Privacy. New York: IEEE, 2022: 1440-1457. |
| [35] | JANG I, TANG A, KIM T, et al. Heterogeneous Isolated Execution for Commodity GPUs[C]// ACM. The 24th International Conference on Architectural Support for Programming Languages and Operating Systems. New York: ACM, 2019: 455-468. |
| [36] | DENG Yunjie, WANG Chenxu, YU Shunchang, et al. Strongbox: A GPU TEE on ARM Endpoints[C]// ACM. The 2022 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2022: 769-783. |
| [37] | WANG Chenxu, ZHANG Fengwei, DENG Yunjie, et al. CAGE: Complementing Arm CCA With GPU Extensions[EB/OL]. (2024-02-27)[2025-06-30]. https://www.ndss-symposium.org/wp-content/uploads/2024-763-paper.pdf. |
| [38] | MAI Haohui, ZHAO Jiacheng, ZHENG Hongren, et al. Honeycomb: Secure and Efficient GPU Executions via Static Validation[C]// USENIX. The 17th USENIX Symposium on Operating Systems Design and Implementation. Berkeley: USENIX, 2023: 155-172. |
| [39] | IVANOV A, ROTHENBERGER B, DETHISE A, et al. SAGE: Software-Based Attestation for GPU Execution[C]// USENIX. 2023 USENIX Annual Technical Conference. Berkeley: USENIX, 2023: 485-499. |
| [40] | ZHU Jianping, HOU Rui, WANG Xiaofeng, et al. Enabling Rack-Scale Confidential Computing Using Heterogeneous Trusted Execution Environment[C]// IEEE. 2020 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2020: 1450-1465. |
| [41] | NVIDIA. NVIDIA Confidential Computing[EB/OL]. (2022-04-25) [2025-06-30]. https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/. |
| [42] | GU Zhongshu, VALDEZ E, AHMED S, et al. NVIDIA GPU Confidential Computing Demystified[EB/OL]. (2025-07-03)[2025-07-15]. https://arxiv.org/abs/2507.02770. |
| [43] | XU Tao, KONG Shuaidi, LIU Caihua, et al. A Review of Heterogeneous Confidential Computing[J]. Journal of Jilin University (Engineering Edition), 2025, 55(3): 755-770. |
| 徐涛, 孔帅迪, 刘才华, 等. 异构机密计算综述[J]. 吉林大学学报(工学版), 2025, 55(3):755-770. |
| [1] | SHI Yijuan, ZHOU Danping, FAN Lei, LIU Yin. Secure Multi-Party Computation Protocol Based on Trusted Execution Environment [J]. Netinfo Security, 2025, 25(9): 1439-1446. |
| [2] | ZHU Hui, FANG Yunyi, WANG Fengwei, XU Wei. Research Progress on Data Security Processing Integrating Confidential Computing [J]. Netinfo Security, 2025, 25(11): 1643-1657. |
| [3] | GUAN Zhi, HU Jianbin, LI Yue, CHEN Zhong. A Comprehensive Survey of Blockchain Technologies and Applications Based on Trusted Execution Environments [J]. Netinfo Security, 2025, 25(11): 1673-1690. |
| [4] | REN Fengyuan, ZHANG Xinyue, LEI Zhuoyi, LIU Xin. Research on Key-Value Data Storage and Operation Optimization Method Based on Confidential Computing [J]. Netinfo Security, 2025, 25(11): 1707-1717. |
| [5] | XUE Kaiping, ZHANG Chunyi, LIU Feng, WANG Feng. Security-Enhanced Index Scheme in Encrypted Database Based on Trusted Execution Environment [J]. Netinfo Security, 2025, 25(11): 1718-1731. |
| [6] | ZHAO Bo, LYU Jiamin, WANG Yixuan. A Multidimensional Security Measurement Architecture for the Container Lifecycle [J]. Netinfo Security, 2025, 25(11): 1745-1761. |
| [7] | WANG Yajie, LU Jinbiao, LI Yuhang, FAN Qing, ZHANG Zijian, ZHU Liehuang. Hierarchical Dynamic Protection Algorithm for Federated Learning Based on Trusted Execution Environment [J]. Netinfo Security, 2025, 25(11): 1762-1773. |
| [8] | LU Di, LIU Yujia, LYU Chaoyue, SUN Mengna, ZHANG Qingwen, YANG Li. Cloud-Native TEE Service Sharing Mechanism for Secure Edge Computing [J]. Netinfo Security, 2025, 25(11): 1774-1791. |
| [9] | HU Yuyi, CAI Wei, CHEN Jingfan, LIU Mohan, WANG Juan, HE Yun. Research on Unified Remote Attestation Mechanism for Confidential Containers Devices [J]. Netinfo Security, 2025, 25(11): 1811-1823. |
| [10] | YU Fajiang, WANG Chaozhou. Implementation Mechanism for TrustZone Paravirtualization and Containerization [J]. Netinfo Security, 2025, 25(10): 1523-1536. |
| [11] | SUN Yu, XIONG Gaojian, LIU Xiao, LI Yan. A Survey on Trusted Execution Environment Based Secure Inference [J]. Netinfo Security, 2024, 24(12): 1799-1818. |
| [12] | TANG Yu, ZHANG Chi. A Privacy Protection Scheme for Information-Centric Networking Based on Intel SGX [J]. Netinfo Security, 2023, 23(6): 55-65. |
| [13] | LIU Xin, LI Yunyi, WANG Miao. A Lightweight Authentication Protocol Based on Confidential Computing for Federated Learning Nodes [J]. Netinfo Security, 2022, 22(7): 37-45. |
| [14] | KELEKET GOMA Christy Junior Yannick, YI Wenzhe, WANG Juan. A Lightweight Trusted Execution Environment Construction Method for Fabric Chaincode Based on SGX [J]. Netinfo Security, 2022, 22(7): 73-83. |
| [15] | LIU Xin, WANG Jiayin, YANG Haorui, ZHANG Ruisheng. An Internet of Vehicles Authentication Protocol Based on Blockchain and secGear Framework [J]. Netinfo Security, 2022, 22(1): 27-36. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||