Netinfo Security ›› 2015, Vol. 15 ›› Issue (3): 64-68.doi: 10.3969/j.issn.1671-1122.2015.03.013
Previous Articles Next Articles
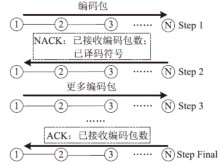
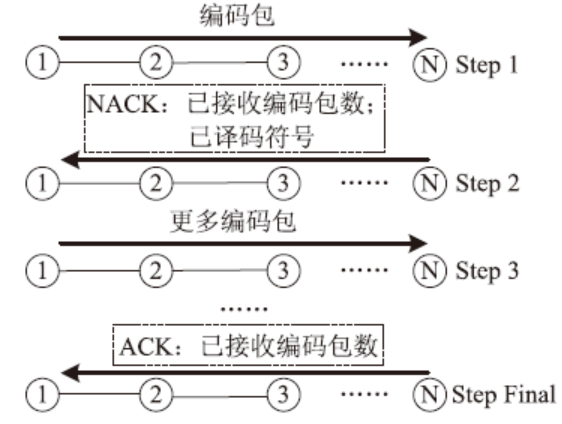
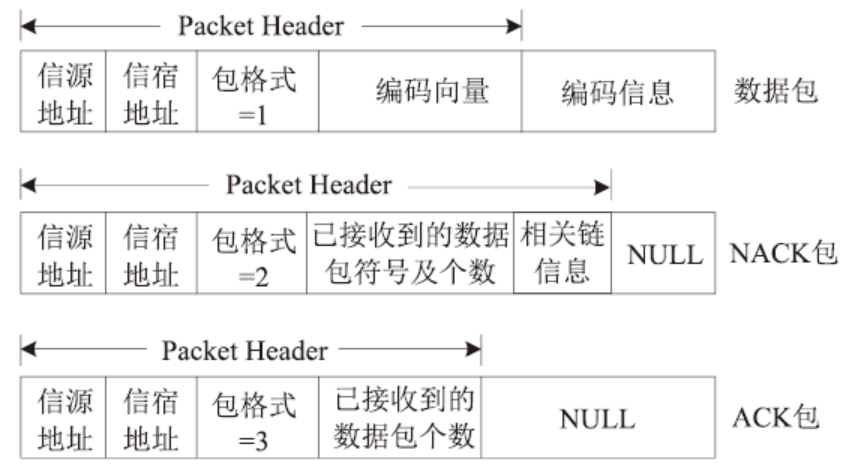
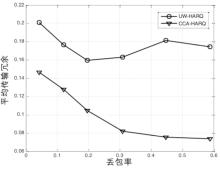
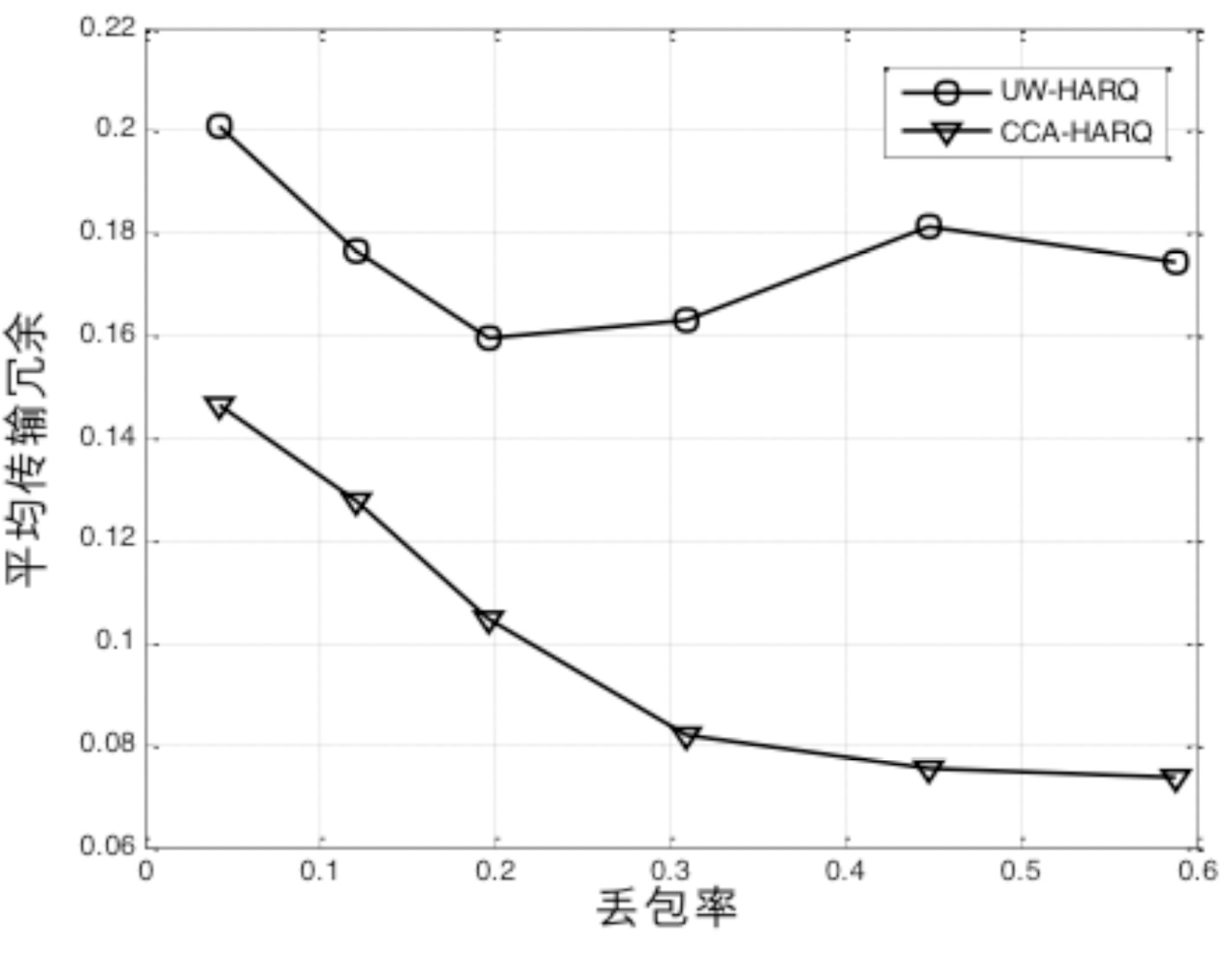
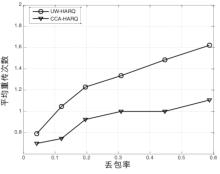
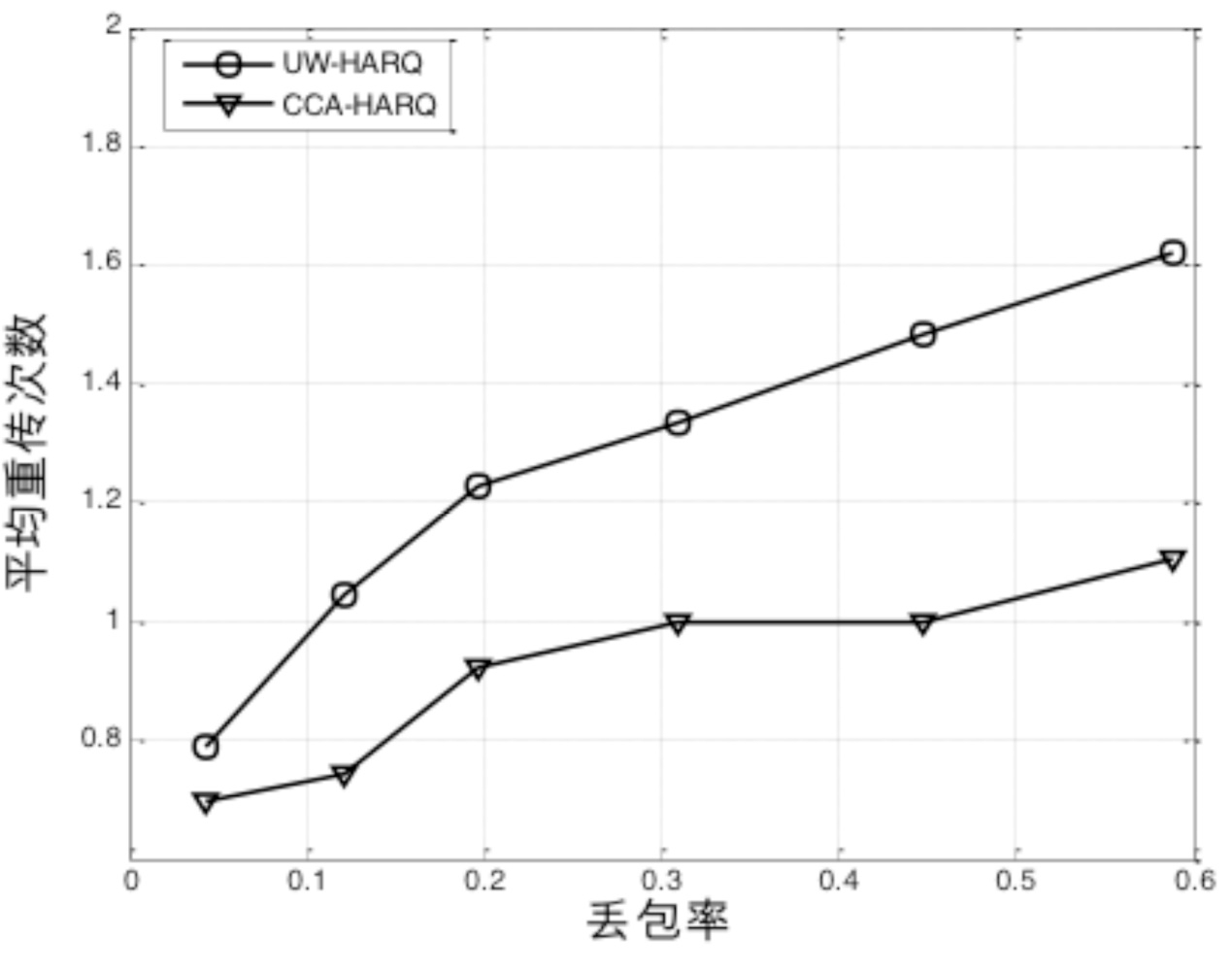
HARQ Protocol for Underwater Acoustic Sensor Networks Based on Fountain Codes Correlation Chain Abstraction
DUAN Jin-jue, ZHAO Dan-feng( ), LIANG Ming-shen
), LIANG Ming-shen
- College of Information and Communication Engineering, Harbin Engineering University, Harbin Heilongjiang 150001, China
-
Received:2015-01-21Online:2015-03-10Published:2015-05-08
CLC Number:
Cite this article
DUAN Jin-jue, ZHAO Dan-feng, LIANG Ming-shen. HARQ Protocol for Underwater Acoustic Sensor Networks Based on Fountain Codes Correlation Chain Abstraction[J]. Netinfo Security, 2015, 15(3): 64-68.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2015.03.013
| [1] | MAJID H, NOSRATALLAH F.A New Hierarchal and Scalable Architecture for Performance Enhancement of Large Scale Underwater Sensor Networks[C]//Symposium on Computers and Informatics, Kuala Lumpur: IEEE, 2011: 520-525. |
| [2] | ASTERJADHI A, CASARI P, GOETZ M.Underwater acoustic networking techniques[M]. Germany: Springer, 2012. |
| [3] | 赵旦峰,梁明珅,段晋珏. 水声网络中喷泉码的应用研究现状与发展前景[J].系统工程与电子技术,2014,(9):1838-1843. |
| [4] | ZHOU Z, MO H, ZHU Y B, et al.Fountain code based adaptive multi-hop reliable data transfer for underwater acoustic networks[C]//Communications (ICC), 2012 IEEE International Conference on, 2012: 6396-6400. |
| [5] | XIE P, CUI J H.SDRT: A Reliable data transport protocol for underwater sensor networks[J]. ADHOC NETWORKS, 2010, 8(7): 708-722. |
| [6] | CASARI P, ROSSI M, ZORZI M.Towards optimal broadcasting policies for HARQ based on fountain codes in underwater networks[C]//Fifth Annual Conference on Wireless On-Demand Network Systems and Service, Partenkirchen: IEEE, 2008: 11-19. |
| [7] | HAINING M, AHMET C M, HESHAM A.UW-HARQ: An Underwater Hybrid ARQ Scheme:Design, Implementation and Initial Test[C]//OCEANS 2012, Hampton Roads: IEEE, 2012: 1-5. |
| [8] | MACKAY D J C. Fountain codes[J]. IEEE Proceedings communications, 2005, 152(6): 1062-1068. |
| [9] | LUBY M.LT codes[C]//43rd Annual IEEE Symposium on Foundations of Computer Science, Ottawa:IEEE, 2002. 271-282. |
| [10] | SHOKROLLAHI A.Raptor codes[J]. IEEE Trans. on Information Theory, 2006, 52(36): 2551-2567. |
| [11] | 慕建君,焦晓鹏,曹训志. 数字喷泉码及其应用的研究进展与展望[J]. 电子学报,2009,37(7):1571-1577. |
| [12] | MIRREZAEI S M, FAEZ K, YOUSEFI S.Towards Fountain Codes[J]. Wiress Personal Communications, 2014, 77(2): 1-30. |
| [13] | TSAI P C, CHEN C M, CHEN Y P.Sparse Degrees Analysis for LT Codes Optimization[C]//2012 IEEE World Congress on Computational Intelligence, Brisbane: IEEE, 2012: 1-6. |
| [14] | CASARI P, ROSSI M, ZORZI M.Fountain codes and their application to broadcasting in underwater networks: Performance modeling and relevant tradeoffs[C]//Proceedings of the 3rd ACM International Workshop on Underwater Networks, California:IEEE, 2008: 11-18. |
| [1] | HUANG Wangwang, ZHOU Hua, WANG Daiqiang, ZHAO Qi. Design of Reconfigurable Key Security Authentication Protocol for IoT Based on National Cryptography SM9 [J]. Netinfo Security, 2024, 24(7): 1006-1014. |
| [2] | ZHANG Xiaojun, ZHANG Nan, HAO Yunpu, WANG Zhouyang, XUE Jingting. Three-Factor Authentication and Key Agreement Protocol Based on Chaotic Map for Industrial Internet of Things Systems [J]. Netinfo Security, 2024, 24(7): 1015-1026. |
| [3] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [4] | ZHANG Liqiang, LU Mengjun, YAN Fei. A Cross-Contract Fuzzing Scheme Based on Function Dependencies [J]. Netinfo Security, 2024, 24(7): 1038-1049. |
| [5] | DONG Yunyun, ZHU Yuling, YAO Shaowen. High-Quality Full-Size Image Steganography Method Based on Improved U-Net and Hybrid Attention Mechanism [J]. Netinfo Security, 2024, 24(7): 1050-1061. |
| [6] | ZHOU Shucheng, LI Yang, LI Chuanrong, GUO Lulu, JIA Xinhong, YANG Xinghua. Context-Based Abnormal Root Cause Algorithm [J]. Netinfo Security, 2024, 24(7): 1062-1075. |
| [7] | REN Changyu, ZHANG Ling, JI Hangyuan, YANG Liqun. Research on TTP Extraction Method Based on Pre-Trained Language Model and Chinese-English Threat Intelligence [J]. Netinfo Security, 2024, 24(7): 1076-1087. |
| [8] | CAI Manchun, XI Rongkang, ZHU Yi, ZHAO Zhongbin. A Fingerprint Identification Method of Multi-Page and Multi-Tag Targeting Tor Website [J]. Netinfo Security, 2024, 24(7): 1088-1097. |
| [9] | XIANG Hui, XUE Yunhao, HAO Lingxin. Large Language Model-Generated Text Detection Based on Linguistic Feature Ensemble Learning [J]. Netinfo Security, 2024, 24(7): 1098-1109. |
| [10] | SHEN Xiuyu, JI Weifeng. Optimization of Cost of Edge-Cloud Collaborative Computing Offloading Considering Security [J]. Netinfo Security, 2024, 24(7): 1110-1121. |
| [11] | ZHAO Xinqiang, FAN Bo, ZHANG Dongju. Research on APT Attack Defense System Based on Threat Discovery [J]. Netinfo Security, 2024, 24(7): 1122-1128. |
| [12] | WEN Wen, LIU Qinju, KUANG Lin, REN Xuejing. Research and Scheme Design of Cyber Threat Intelligence Sharing under Privacy Protection System [J]. Netinfo Security, 2024, 24(7): 1129-1137. |
| [13] | LIU Yidan, MA Yongliu, DU Yibin, CHENG Qingfeng. A Certificateless Anonymous Authentication Key Agreement Protocol for VANET [J]. Netinfo Security, 2024, 24(7): 983-992. |
| [14] | LUO Ming, ZHAN Qibang, QIU Minrong. A Heterogeneous Cross-Domain Conditional Privacy Protection Ring Signcryption Scheme for V2I Communication [J]. Netinfo Security, 2024, 24(7): 993-1005. |
| [15] | LI Zengpeng, WANG Siyang, WANG Mei. Research of Privacy-Preserving Proximity Test [J]. Netinfo Security, 2024, 24(6): 817-830. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||