Netinfo Security ›› 2015, Vol. 15 ›› Issue (3): 33-37.doi: 10.3969/j.issn.1671-1122.2015.03.007
Previous Articles Next Articles
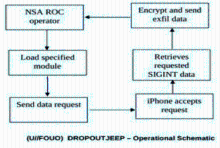
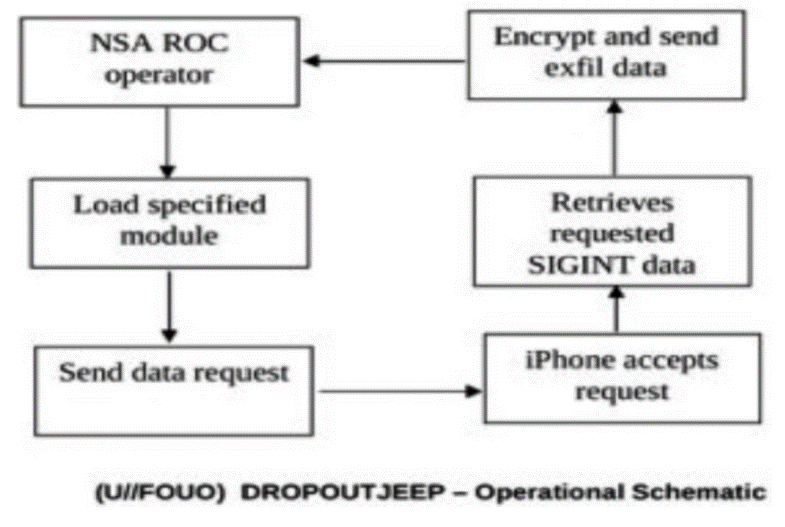
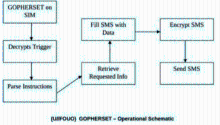
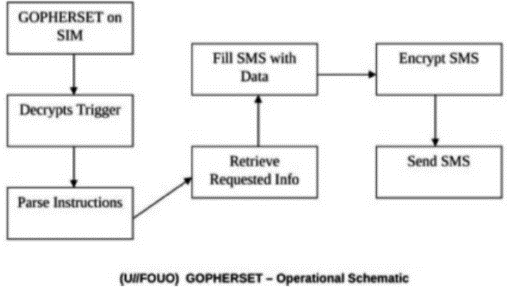
Research for APT Attack Technology
CHEN Chen1( ), WANG Yi-Jun1, HU Guang-jun1, GUO Yan-hui2
), WANG Yi-Jun1, HU Guang-jun1, GUO Yan-hui2
- 1.The First Research Institute of the Ministry of Public Security of P.R.C,Bejing 100048,China
2.School of Computer Science, Beijing University of Posts and Telecommunications, Beijing 100876, China