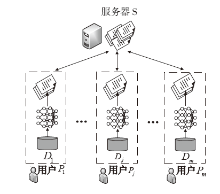
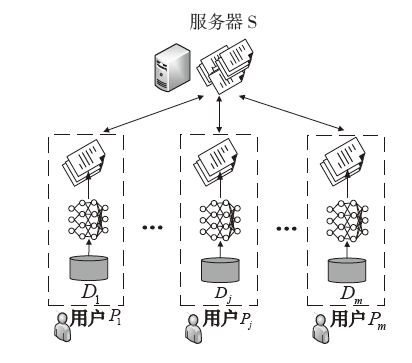
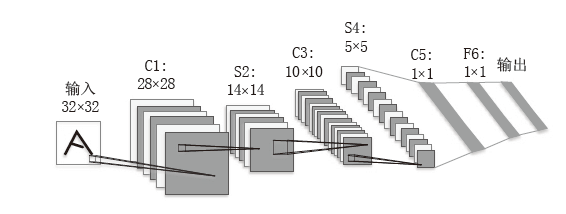
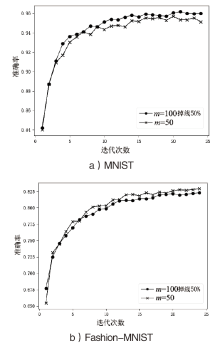
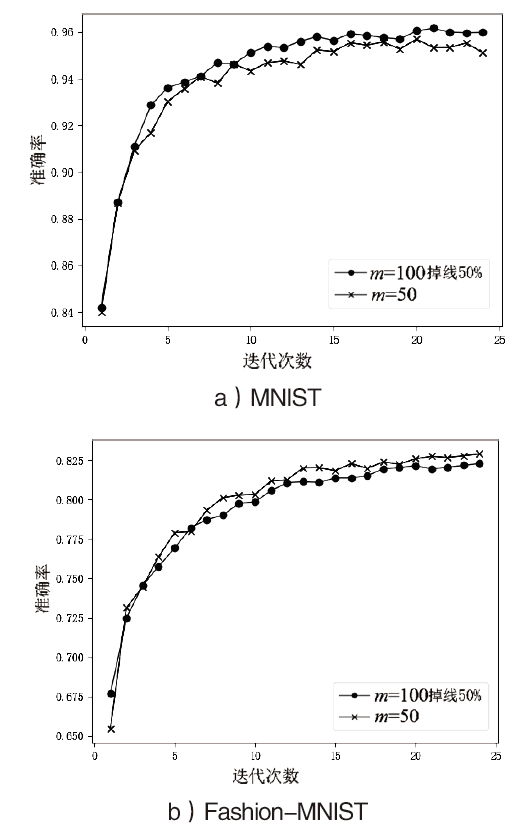
| [1] |
CUSTERS B, SEARS A M, DECHESNE F, et al. Information Technology and Law Series[M]. USA: Oxford University Press, 2019.
|
| [2] |
MCMAHAN B, MOORE E, RAMAGE D, et al. Communication-efficient Learning of Deep Networks from Decentralized Data [C]//JMLR. 20th International Conference on Artificial Intelligence and Statistics (AISTATS). April 20-22, 2017, Fort Lauderdale, FL, USA. New York: JMLR, 2017: 1273-1282.
|
| [3] |
YANG Wensi. Research on Credit Card Fraud Detection System Based on Federated Learning[D]. Shenzhen: University of Chinese Academy of Sciences (Shenzhen Institute of Advanced Technology, Chinese Academy of Sciences), 2020.
|
|
阳文斯. 基于联邦学习的信用卡欺诈检测系统研究[D].深圳:中国科学院大学(中国科学院深圳先进技术研究院), 2020.
|
| [4] |
CHEN Guorun, MU Meirong, ZHANG Rui, et al. Implementation of Communication Fraud Recognition Model Based on Federated Learning[J]. Telecommunications Science, 2020. 36(S1):304-310.
|
|
陈国润, 母美荣, 张蕊, 等. 基于联邦学习的通信诈骗识别模型的实现[J]. 电信科学, 2020. 36(S1):304-310.
|
| [5] |
SHOKRI R, STRONATI M, SONG C, et al. Membership Inference Attacks Against Machine Learning Models [C]//IEEE. IEEE Symposium on Security and Privacy, May 22-26, 2017, San Jose, CA, USA. New Jersey: IEEE, 2017: 3-18.
|
| [6] |
FREDRIKSON M, JHA S, RISTENPART T. Model Inversion Attacks that Exploit Confidence Information and Basic Countermeasures [C]//ACM. Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, October 12-16, 2015, Denver, CO, USA. New York: ACM, 2015: 1322-1333.
|
| [7] |
WU X, FREDRIKSON M, JHA S, et al. A Methodology for Formalizing Model-inversion Attacks [C]// IEEE. IEEE 29th Computer Security Foundations Symposium (CSF), June 27-July 1, 2016, Lisbon, Portugal. New Jersey: IEEE, 2016: 355-370.
|
| [8] |
DWORK C. Differential Privacy: A Survey of Results [C]//Springer. Theory and Applications of Models of Computation, 5th International Conference, TAMC, April 25-29, 2008, Xi'an, China. Heidelberg: Springer, 2008: 1-19.
|
| [9] |
PATHAK M A, RANE S, RAJ B. Multiparty Differential Privacy via Aggregation of Locally Trained Classifiers[C]//MIT Press. Advances in Neural Information Processing Systems 23: 24th Annual Conference on Neural Information Processing Systems 2010, December 6-9, 2010, Vancouver, British Columbia, Canada. Cambridge: MIT Press, 2010: 1876-1884.
|
| [10] |
DWORK C. Calibrating Noise to Sensitivity in Private Data Analysis [C]//Springer. Theory of Cryptography, Third Theory of Cryptography Conference, March 4-7, 2006, New York, USA. Berlin: Springer, 2006: 265-284.
|
| [11] |
ROBIN C G, TASSILO K, MOIN N. Differentially Private Federated Learning: A Client Level Perspective[C]//MIT Press. Neural Information Processing Systems, December 8, 2017, Long Beach, USA. Cambridge: MIT Press, 2017: 1-7.
|
| [12] |
PHONG L T, AONO Y, HAYASHI T, et al. Privacy-preserving Deep Learning via Additively Homomorphic Encryption[J]. IEEE Transactions on Information Forensics and Security, 2018,13(5):1333-1345.
|
| [13] |
KANG Wei, LI Jun, MING Ding, et al. Federated Learning with Differential Privacy: Algorithms and Performance Analysis[EB/OL]. https://doi.org/10.1109/TIFS.2020.2988575, 2021-01-04.
|
| [14] |
SUN Lichao, QIAN Jianwei, CHEN Xun, et al. LDP-FL: Practical Private Aggregation in Federated Learning with Local Differential Privacy[EB/OL]. https://arxiv.org/abs/2007.15789, 2020-08-03.
|
| [15] |
DWORK C, ROTH A. The Algorithmic Foundations of Differential Privacy[J]. Found Trends Theor Comput Sci, 2014,9(3-4):211-407.
|
| [16] |
MCSHERRY F, TALWAR K. Mechanism Design via Differential Privacy [C]//IEEE. 48th Annual IEEE Symposium on Foundations of Computer Science (FOCS'07), October 20-23, 2007, Providence, RI, USA. New Jersey: IEEE, 2007: 94-103.
|
| [17] |
MCSHERRY F. Privacy Integrated Queries: An Extensible Platform for Privacy-preserving Data Analysis [C]//ACM. Proceedings of the 2009 ACM SIGMOD International Conference on Management of Data, June 29-July 2, 2009, Providence, Rhode Island, USA. New York: ACM, 2009: 19-30.
|
| [18] |
ABADI M, CHU A, GOODFELLOW I J, et al. Deep Learning with Differential Privacy [C]//ACM. Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, October 24-28, 2016. Vienna, Austria. New York: ACM, 2016: 308-318.
|