信息网络安全 ›› 2025, Vol. 25 ›› Issue (11): 1811-1823.doi: 10.3969/j.issn.1671-1122.2025.11.012
面向机密容器的统一远程证明机制研究
胡宇义1,2, 蔡炜1,2, 陈竞凡1,2, 刘莫寒1,2, 王鹃1,2( ), 何运3
), 何运3
1.空天信息安全与可信计算教育部重点实验室 武汉 430072 2.武汉大学国家网络安全学院 武汉 430072 3.京东集团 北京 100176
-
收稿日期:2025-07-28出版日期:2025-11-10发布日期:2025-12-02 -
通讯作者:王鹃jwang@whu.edu.cn -
作者简介:胡宇义(2001—),男,四川,硕士研究生,主要研究方向为可信计算、系统安全|蔡炜(2002—),男,吉林,硕士研究生,主要研究方向为可信计算、系统安全|陈竞凡(2001—),男,湖南,硕士研究生,主要研究方向为可信计算、系统安全|刘莫寒(2002—),男,北京,硕士研究生,主要研究方向为机密计算、系统安全|王鹃(1976—),女,湖北,教授,博士,CCF高级会员,主要研究方向为系统与可信计算、人工智能安全与漏洞挖掘|何运(1994—),男,贵州,工程师,博士,主要研究方向为机密计算、系统安全、隐私计算 -
基金资助:湖北省重点研发计划(2023BAB165);国家自然科学基金(61872430);智能电网国家科技重大专项(2024ZD0803000)
Research on Unified Remote Attestation Mechanism for Confidential Containers Devices
HU Yuyi1,2, CAI Wei1,2, CHEN Jingfan1,2, LIU Mohan1,2, WANG Juan1,2( ), HE Yun3
), HE Yun3
1. Key Laboratory of Aerospace Information Security and Trusted Computing ,Ministry of Education Wuhan 430072, China 2. School of Cyber Science and Engineering ,Wuhan University Wuhan 430072, China 3. JD.com Group Beijing 100176, China
-
Received:2025-07-28Online:2025-11-10Published:2025-12-02
摘要:
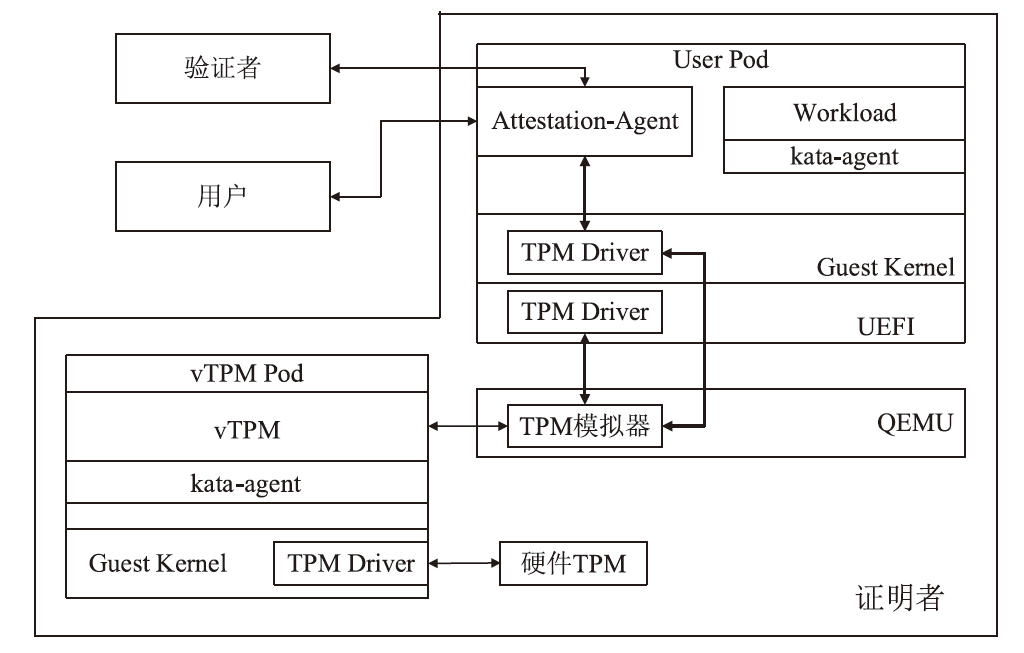
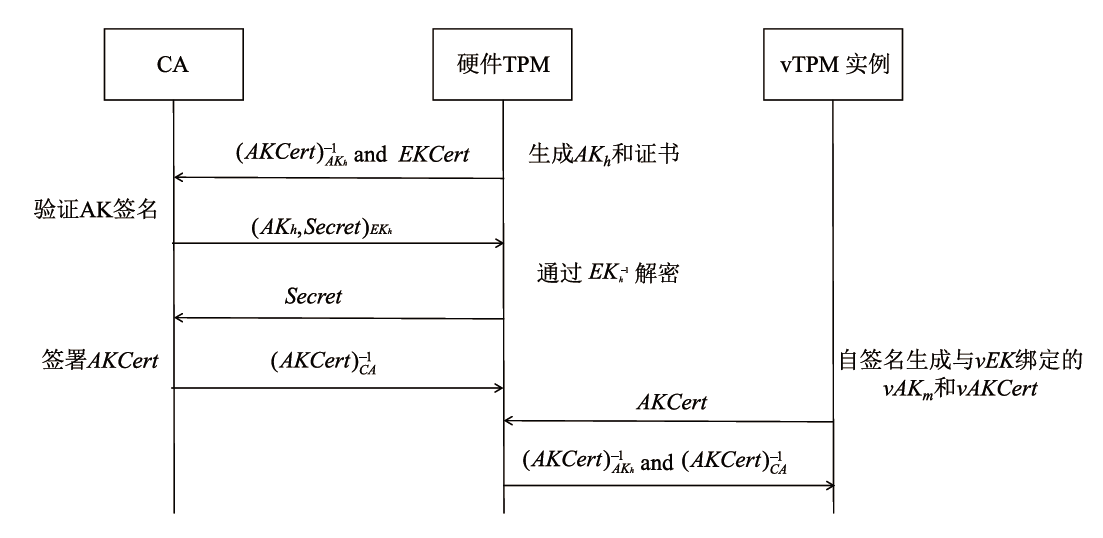
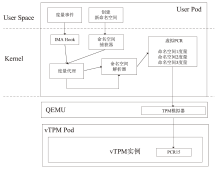
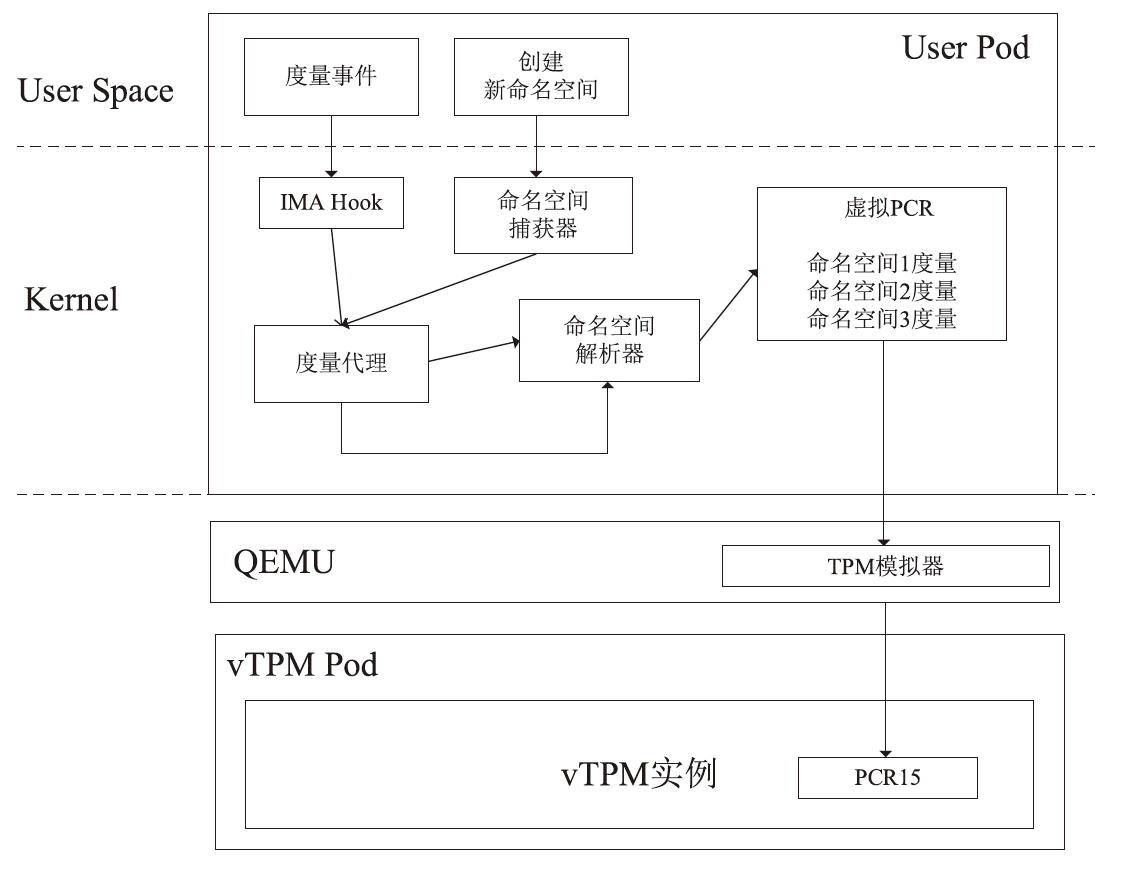
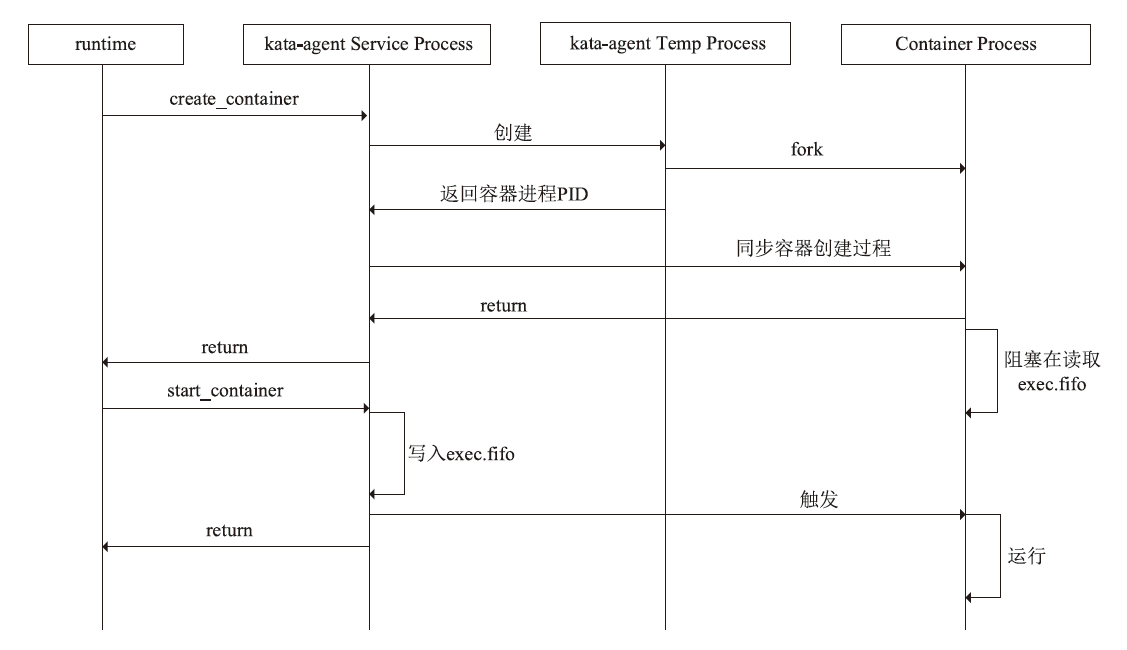
随着云原生技术的快速发展,机密计算已成为保障云端数据安全的重要手段。云服务提供商通过受硬件保护的可信执行环境(TEE)为用户提供数据计算过程中的安全保障。然而,现有TEE的远程证明方案在机密容器场景下面临新的挑战,不同硬件架构下的远程证明方案缺乏统一性,同时现有机密容器的远程证明度量范围局限于Pod操作系统内核层面,导致容器管理程序等应用层组件存在度量缺失,使得远程证明方案出现信任链断裂问题。鉴于此,文章提出了基于虚拟可信平台模块(vTPM)的统一远程证明框架和机密容器度量拓展方法。该统一远程证明框架通过机密容器保障虚拟可信平台模块的安全性,并利用硬件TPM的不可导出密钥为虚拟可信平台模块颁发认证密钥证书,构建从权威机构到远程证明报告的全链可信验证体系;机密容器度量拓展方法则基于内核命名空间机制,实现从启动代码到操作系统内核再到容器管理程序的完整信任链扩展。为验证所提方法的有效性,文章基于Kata Container开源框架在CSV平台上进行了功能测试和性能测试。实验结果表明,该统一远程证明框架的性能开销相比软件TPM约增加了10%,修改后的完整性度量架构所带来的额外开销不足1%,充分验证了文章所提方法的实用性与高效性。
中图分类号:
引用本文
胡宇义, 蔡炜, 陈竞凡, 刘莫寒, 王鹃, 何运. 面向机密容器的统一远程证明机制研究[J]. 信息网络安全, 2025, 25(11): 1811-1823.
HU Yuyi, CAI Wei, CHEN Jingfan, LIU Mohan, WANG Juan, HE Yun. Research on Unified Remote Attestation Mechanism for Confidential Containers Devices[J]. Netinfo Security, 2025, 25(11): 1811-1823.
| [1] | FENG Dengguo. Progress and Prospects of Confidential Computing[EB/OL]. (2025-01-07)[2025-07-20]. https://www.secrss.com/article/74435. |
| 冯登国. 机密计算的进展与展望[EB/OL]. (2025-01-07)[2025-07-20]. https://www.secrss.com/article/74435. | |
| [2] | WANG Juan, FAN Chengyang, CHENG Yueqiang, et al. Analysis and Research on SGX Technology[J]. Journal of Software, 2018, 29(9): 2778-2798. |
| 王鹃, 樊成阳, 程越强, 等. SGX技术的分析和研究[J]. 软件学报, 2018, 29(9):2778-2798. | |
| [3] | KAMMEL F, YLINEN M, FELDMAN-FITZRTHUM T. Confidential Kubernetes: Use Confidential Virtual Machines and Enclaves to Improve Your Cluster Security[EB/OL]. (2023-07-06)[2025-07-20]. https://kubernetes.io/zh-cn/blog/2023/07/06/confidential-kubernetes/. |
| [4] | BIRKHOLZ H, THALER D, RICHARDSON M, et al. Remote Attestation Procedures (RATS) Architecture:RFC 9334[EB/OL]. [2025-07-27]. https://www.rfc-editor.org/rfc/rfc9334. |
| [5] | Trusted Computing Group. Welcome to Trusted Computing Group[EB/OL]. [2025-07-20]. https://trustedcomputinggroup.org/. |
| [6] | FENG Dengguo, QIN Yu, WANG Dan, et al. Research on Trusted Computing Technology[J]. Journal of Computer Research and Development, 2011, 48(8): 1332-1349. |
| 冯登国, 秦宇, 汪丹, 等. 可信计算技术研究[J]. 计算机研究与发展, 2011, 48(8):1332-1349. | |
| [7] | BERGER S, CÁCERES R, GOLDMAN K A, et al. vTPM: Virtualizing the Trusted Platform Module[C]// USENIX. The 15th USENIX Security Symposium. Berkely: USENIX, 2006: 305-320. |
| [8] | RAJ H, SAROIU S, WOLMAN A, et al. fTPM: A Software-Only Implementation of a TPM Chip[C]// USENIX. The 25th USENIX Security Symposium. Berkely: USENIX, 2016: 841-856. |
| [9] | ARM. TrustZone for Cortex-A[EB/OL]. [2025-09-20]. https://www.arm.com/zh-TW/technologies/trustzone-for-cortex-a. |
| [10] | SUN Haonan, HE Rongyu, ZHANG Yong, et al. eTPM: A Trusted Cloud Platform Enclave TPM Scheme Based on Intel SGX Technology[EB/OL]. (2018-11-06)[2015-07-20]. https://doi.org/10.3390/s18113807. |
| [11] |
WANG Juan, WANG Jie, FAN Chengyang, et al. SvTPM: SGX-Based Virtual Trusted Platform Modules for Cloud Computing[J]. IEEE Transactions on Cloud Computing, 2023, 11(3): 2936-2953.
doi: 10.1109/TCC.2023.3243891 URL |
| [12] | Intel. Rust-Vtpm-Td[EB/OL]. [2025-07-20]. https://github.com/intel/vtpm-td. |
| [13] | NARAYANAN V, CARVALHO C, RUOCCO A, et al. Remote Attestation of Confidential VMs Using Ephemeral vTPMs[C]// ACM. The 39th Annual Computer Security Applications Conference. New York: ACM, 2023: 732-743 |
| [14] | PECHOLT J, WESSEL S. CoCoTPM: Trusted Platform Modules for Virtual Machines in Confidential Computing Environments[C]// ACM. The 38th Annual Computer Security Applications Conference. New York: ACM, 2022: 989-998. |
| [15] | CONSORTIUM C C. Why is Attestation Required for Confidential Computing?[EB/OL]. (2023-04-06)[2025-07-20]. https://confidentialcomputing.io/2023/04/06/why-is-attestation-required-for-confidential-computing/. |
| [16] | MÉNÉTREY J, GÖTTEL C, KHURSHID A, et al. Attestation Mechanisms for Trusted Execution Environments Demystified[C]// Springer. Distributed Applications and Interoperable Systems. Heidelberg: Springer, 2022: 95-113. |
| [17] | CHEN Guoxing, ZHANG Yinqian, LAI T. OPERA: Open Remote Attestation for Intel’s Secure Enclaves[C]// ACM. The 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 2317-2331. |
| [18] | CHEN Guoxing, ZHANG Yinqian. MAGE: Mutual Attestation for a Group of Enclaves without Trusted Third Parties[C]// USENIX. The 31st USENIX Security Symposium. Berkely: USENIX, 2022: 4095-4110. |
| [19] | GREVELER U, JUSTUS B, LÖHR D. Mutual Remote Attestation: Enabling System Cloning for TPM Based Platforms[C]// Springer. Security and Trust Management(STM 2011). Heidelberg: Springer, 2011: 193-206. |
| [20] | SCHEAR N, CABLE II P T, MOYER T M, et al. Bootstrapping and Maintaining Trust in the Cloud[C]// ACM. The 32nd Annual Computer Security Applications Conference (ACSAC 2016). New York: ACM, 2016: 65-77. |
| [21] | OTT S, KAMHUBER M, PECHOLT J, et al. Universal Remote Attestation for Cloud and Edge Platforms[C]// ACM. The 18th International Conference on Availability, Reliability and Security. New York: ACM, 2023: 1-11. |
| [22] | ZHANG Xiaolin, QIN Kailun, QU Shipei, et al. Teamwork Makes TEE Work: Open and Resilient Remote Attestation on Decentralized Trust[EB/OL]. (2024-08-09)[2025-07-20]. https://doi.org/10.48550/arXiv.2402.08908. |
| [23] | KARANJAI R, GAO Zhimin, CHEN Lin, et al. DHTee: Decentralized Infrastructure for Heterogeneous TEEs[C]// IEEE. 2023 IEEE International Conference on Blockchain and Cryptocurrency (ICBC). New York: IEEE, 2023: 1-3. |
| [24] | PAULIN D, HENNEBERT C, FRANCO-RONDISSON T, et al. HistoTrust: Ethereum-Based Attestation of a Data History Built with OP-TEE and TPM[C]// Springer. Foundations and Practice of Security(FPS 2021). Heidelberg: Springer, 2021: 130-145. |
| [25] | ANKERGÅRD S F J J, DUSHKU E, DRAGONI N. PERMANENT: Publicly Verifiable Remote Attestation for Internet of Things Through Blockchain[C]// Springer. Foundations and Practice of Security(FPS 2021). Heidelberg: Springer, 2021: 218-234. |
| [26] | LI Peixi, LI Xiang, FANG Liming. DMA: Mutual Attestation Framework for Distributed Enclaves[C]// Springer. Information and Communications Security(ICICS 2024). Heidelberg: Springer, 2024: 145-164. |
| [27] | SAILER R, ZHANG Xiaolan, JAEGER T, et al. Design and Implementation of a TCG-Based Integrity Measurement Architecture[C]// USENIX. The 13th USENIX Security Symposium. Berkeley: USENIX, 2004: 223-238. |
| [28] | SU Tao. Trust and Integrity in Distributed Systems[D]. Turin: Polytechnic University of Turin, 2017. |
| [29] |
BENEDICTIS M D, LIOY A. Integrity Verification of Docker Containers for a Lightweight Cloud Environment[J]. Future Generation Computer Systems, 2019, 97: 236-246.
doi: 10.1016/j.future.2019.02.026 URL |
| [30] | LUO Wu, SHEN Qingni, XIA Yutang, et al. Container-IMA: A Privacy-Preserving Integrity Measurement Architecture for Containers[C]// USENIX. The 22nd International Symposium on Research in Attacks, Intrusions and Defenses. Berkely: USENIX, 2019: 487-500. |
| [31] | SONG Liantao, DING Yan, DONG Pan, et al. TZ-IMA: Supporting Integrity Measurement for Applications with ARM Trustzone[C]// Springer. Information and Communications Security(ICICS 2022). Heidelberg: Springer, 2022: 342-358. |
| [32] | Intel. Runtime Integrity Measurement and Attestation in a Trust Domain[EB/OL]. (2025-04-09)[2025-07-20]. https://www.intel.cn/content/www/cn/zh/developer/articles/community/runtime-integrity-measure-and-attest-trust-domain.html. |
| [33] | Tpm2-Software Community. Remote Attestation with Tpm2 Tools[EB/OL]. (2020-06-12)[2025-07-20]. https://tpm2-software.github.io/2020/06/12/Remote-Attestation-With-tpm2-tools.html. |
| [34] |
DIFFIE W, HELLMAN M E. New Directions in Cryptography[J]. IEEE Transactions on Information Theory, 1976, 22(6): 644-654.
doi: 10.1109/TIT.1976.1055638 URL |
| [35] | ARYAN, KUMAR C, DURAI R V P M. Enhanced Diffie-Hellman Algorithm for Reliable Key Exchange[EB/OL]. [2025-07-20]. https://iopscience.iop.org/article/10.1088/1757-899X/263/4/042015. |
| [36] | FERRO L. Container Attestation with Linux IMA Namespaces[D]. Turin: Polytechnic University of Turin, 2023. |
| [1] | 拾以娟, 周丹平, 范磊, 刘茵. 基于可信执行环境的安全多方计算协议[J]. 信息网络安全, 2025, 25(9): 1439-1446. |
| [2] | 黄轲, 李璇, 周庆飞, 尚科彤, 秦宇. 基于eBPF的容器运行时可信监控方案[J]. 信息网络安全, 2025, 25(2): 306-326. |
| [3] | 郝萌, 李佳勇, 杨洪伟, 张伟哲. 异构CPU-GPU系统机密计算综述[J]. 信息网络安全, 2025, 25(11): 1658-1672. |
| [4] | 关志, 胡建斌, 李悦, 陈钟. 基于可信执行环境的区块链技术与应用综述[J]. 信息网络安全, 2025, 25(11): 1673-1690. |
| [5] | 薛开平, 张淳一, 柳枫, 王峰. 基于可信执行环境的加密数据库索引安全增强方案[J]. 信息网络安全, 2025, 25(11): 1718-1731. |
| [6] | 赵波, 吕佳敏, 王一琁. 一种面向容器生命周期的多维安全度量架构[J]. 信息网络安全, 2025, 25(11): 1745-1761. |
| [7] | 王亚杰, 陆锦标, 李宇航, 范青, 张子剑, 祝烈煌. 基于可信执行环境的联邦学习分层动态防护算法[J]. 信息网络安全, 2025, 25(11): 1762-1773. |
| [8] | 卢笛, 刘玉佳, 吕超越, 孙梦娜, 张清文, 杨力. 一种云原生TEE服务共享机制[J]. 信息网络安全, 2025, 25(11): 1774-1791. |
| [9] | 金娃, 秦宇, 刘菁润, 尚科彤, 贾梦涵, 林江南. 基于机密计算平台的TEE和TPM硬件可信信道构建方案[J]. 信息网络安全, 2025, 25(11): 1792-1810. |
| [10] | 余发江, 王朝州. TrustZone半虚拟化与容器化实现机制[J]. 信息网络安全, 2025, 25(10): 1523-1536. |
| [11] | 孙钰, 熊高剑, 刘潇, 李燕. 基于可信执行环境的安全推理研究进展[J]. 信息网络安全, 2024, 24(12): 1799-1818. |
| [12] | 唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65. |
| [13] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [14] | 尤玮婧, 刘丽敏, 马悦, 韩东. 基于安全硬件的云端数据机密性验证方案[J]. 信息网络安全, 2020, 20(12): 1-8. |
| [15] | 王晋, 喻潇, 刘畅, 赵波. 智能电网环境下一种基于SDKey的智能移动终端远程证明方案[J]. 信息网络安全, 2018, 18(7): 1-6. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||