信息网络安全 ›› 2025, Vol. 25 ›› Issue (11): 1658-1672.doi: 10.3969/j.issn.1671-1122.2025.11.002
异构CPU-GPU系统机密计算综述
1.哈尔滨工业大学网络空间安全学院 哈尔滨 150001 2.哈尔滨工业大学(深圳)计算机科学与技术学院 深圳 518055 3.鹏城实验室 深圳 518055
-
收稿日期:2025-07-20出版日期:2025-11-10发布日期:2025-12-02 -
通讯作者:李佳勇li18145606780@163.com -
作者简介:郝萌(1991—),男,山东,副教授,博士,CCF会员,主要研究方向为高性能计算、并行应用性能优化|李佳勇(2001—),男,江西,硕士研究生,主要研究方向为高性能计算|杨洪伟(1987—),男,黑龙江,助理研究员,博士,CCF会员,主要研究方向为数据挖掘、隐私计算、网络空间安全|张伟哲(1976—),男,黑龙江,教授,博士,CCF会员,主要研究方向为网络空间安全、数据安全、高性能计算 -
基金资助:国家自然科学基金(U22A2036);国家重点研发计划(2023YFB4503205)
Heterogeneous CPU-GPU System Confidential Computing Survey
HAO Meng1, LI Jiayong1( ), YANG Hongwei1, ZHANG Weizhe1,2,3
), YANG Hongwei1, ZHANG Weizhe1,2,3
1. School of Cyberspace Science ,Harbin Institute of Technology Harbin 150001, China 2. School of Computer Science and Technology ,Harbin Institute of Technology (Shenzhen) Shenzhen 518055, China 3. Peng Cheng Laboratory Shenzhen 518055, China
-
Received:2025-07-20Online:2025-11-10Published:2025-12-02
摘要:
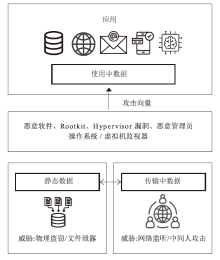
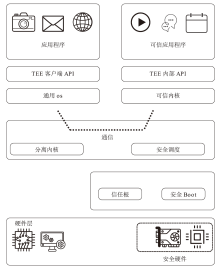
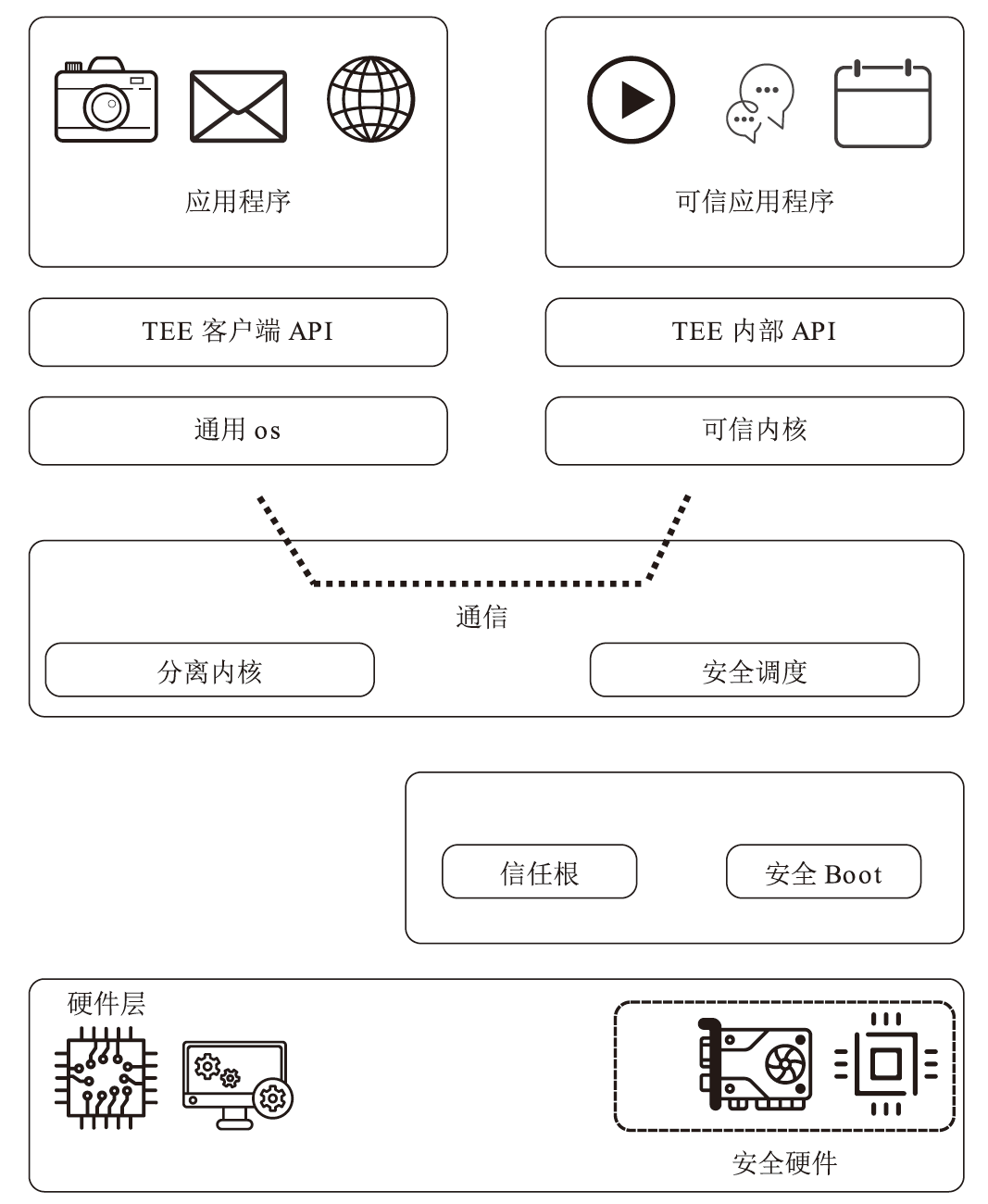
随着人工智能等数据密集型应用的普及,以CPU与GPU为核心的异构计算系统已成为关键基础设施。然而,在云和边缘等非可信环境中,敏感数据在处理阶段面临着严峻的安全威胁,传统加密方法对此无能为力。机密计算利用硬件可信执行环境(TEE)为保护使用中的数据提供了有效方案,但现有技术主要集中在CPU端。将TEE安全边界无缝扩展至计算引擎核心GPU,已成为当前学术界与工业界关注的焦点。文章对CPU-GPU异构系统中的机密计算技术进行系统性综述。首先,文章回顾了机密计算的基本概念并剖析了针对GPU的典型攻击向量。然后,对现有GPU机密计算方案进行分类,涵盖硬件辅助、软硬件协同及纯软件实现等技术范式。最后,文章总结了该领域面临的关键挑战,并展望了未来研究方向。
中图分类号:
引用本文
郝萌, 李佳勇, 杨洪伟, 张伟哲. 异构CPU-GPU系统机密计算综述[J]. 信息网络安全, 2025, 25(11): 1658-1672.
HAO Meng, LI Jiayong, YANG Hongwei, ZHANG Weizhe. Heterogeneous CPU-GPU System Confidential Computing Survey[J]. Netinfo Security, 2025, 25(11): 1658-1672.
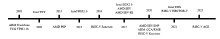
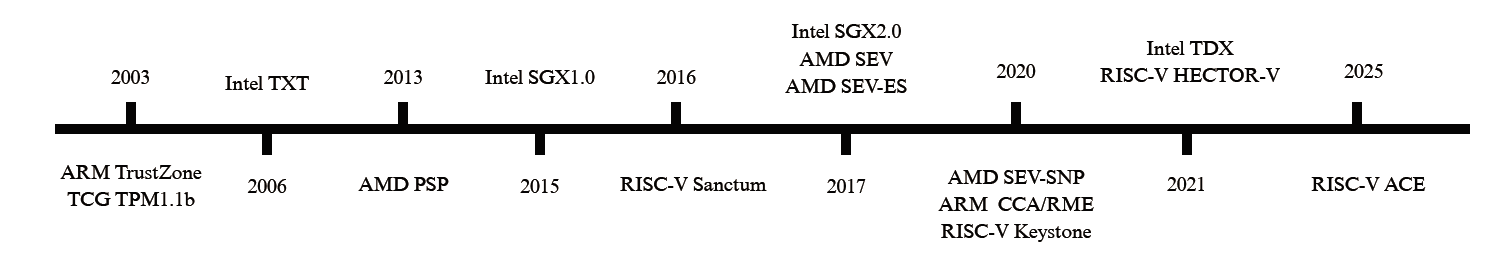
表1
各指令集架构的TEE演进
| 架构 | 技术 | 发布年份 | 隔离模型 | 核心硬件/机制 |
|---|---|---|---|---|
| x86 | TCG TPM 1.1b | 2003 | 静态测量信任根 | PCRs,CRTM,加密协处理器 |
| Intel TXT | 2006 | 动态测量信任根 | GETSEC指令,SINIT ACM,动态PCRs | |
| Intel SGX | 2015 | 应用程序飞地 | ENCLU/ENCLS指令,EPC,EPCM | |
| AMD SEV | 2017 | 机密虚拟机 | AMD-SP,内存控制器AES引擎 | |
| AMD SEV-SNP | 2020 | 机密虚拟机 | SEV机制 + RMP | |
| Intel TDX | 2021 | 机密虚拟机 | VMX,MKTME,SEAM模式,TDX模块 | |
| ARM | TrustZone | 2003 | 系统分区 | NS-bit,安全监视器,TZASC/TZPC |
| CCA / RME | 2020 | 机密虚拟机 | Realm/Root世界,GPT,RMM固件 | |
| RISC-V | Sanctum | 2016 | 应用程序飞地 | PMP |
| Keystone | 2020 | 应用程序飞地 (框架) | PMP,可定制的安全监视器(SM)和运行时(RT) | |
| HECTOR-V | 2021 | 协处理器 | 异构多核,专用的安全协处理器 | |
| ACE | 2025 | 机密虚拟机 | H-extension,PMP,形式化验证的TSM |
表2
异构CPU-CPU系统TEE比较
| 硬件依赖 | 性能开销(典型) | 保护方法 | |
|---|---|---|---|
| Graviton | 高(需改GPU) | 17%~33% | 修改GPU命令处理器;PMM |
| HIX StrongBox | 低(需改CPU/平台) 无(利用现有ARM特性) | 平均26% 4.7%~15.3% | CPU侧IOMMU/PCIe扩展;GPU飞地;ARM TrustZone;Stage-2地址翻译 |
| CAGE | 无(利用现有ARM特性) | 平均2.45% | ARM CCA;影子任务;双向隔离 |
| HETEE | 高(需专用HETEE Box) | 小于2.2% | 机架级PCIe物理隔离 |
| Honeycomb | 无(需CPU TEE) | 2%(大模型) | 静态二进制验证;双重监控器 |
| SAGE | 无(需CPU TEE) | 验证阶段开销;执行时无损 | 基于时间的执行证明 |
| H100 | 高(专用GPU) | — | 硬件防火墙;端到端PCIe加密 |
| [1] | KHOKHAR A A, PRASANNA V K, SHAABAN M E, et al. Heterogeneous Computing: Challenges and Opportunities[J]. Computer, 2002, 26(6): 18-27. |
| [2] | MITTAL S, VETTER J S. A Survey of CPU-GPU Heterogeneous Computing Techniques[J]. ACM Computing Surveys (CSUR), 2015, 47(4): 1-35. |
| [3] | WANG Wei, HU Yin, CHEN Lianmu, et al. Accelerating Fully Homomorphic Encryption Using GPU[C]// IEEE. 2012 IEEE Conference on High Performance Extreme Computing. New York: IEEE, 2012: 1-5. |
| [4] | KNOTT B, VENKATARAMAN S, HANNUN A, et al. Crypten: Secure Multi-Party Computation Meets Machine Learning[J]. Advances in Neural Information Processing Systems, 2021, 34: 4961-4973. |
| [5] | VOLOS S, VASWANI K, BRUNO R. Graviton: Trusted Execution Environments on GPUs[C]// USENIX. The 13th USENIX Symposium on Operating Systems Design and Implementation. Berkeley: USENIX, 2018: 681-696. |
| [6] | COSTAN V, DEVADAS S. Intel SGX Explained[EB/OL]. (2017-02-21)[2025-06-30]. https://eprint.iacr.org/2016/086.pdf. |
| [7] | AMD. AMD Secure Encrypted Virtualization (SEV)[EB/OL]. (2020-01-01) [2025-06-30]. https://www.amd.com/en/developer/sev.html. |
| [8] | Confidential Computing Consortium. A Technical Analysis of Confidential Computing[EB/OL]. (2023-03-10)[2025-06-30]. https://confidentialcomputing.io/wp-content/uploads/sites/10/2023/03/CCC-A-Technical-Analysis-of-Confidential-Computing-v1.3_unlocked.pdf. |
| [9] | Trusted Computing Group. TCPA_Main_TCG_Architecture[EB/OL]. (2002-02-22)[2025-06-30]. https://trustedcomputinggroup.org/wp-content/uploads/TCPA_Main_TCG_Architecture_v1_1b.pdf. |
| [10] | JAMES G. Intel Trusted Execution Technology: Hardware-Based Technology for Enhancing Server Platform Security[EB/OL]. (2009-06-12)[2025-06-30]. https://www.intel.com/content/dam/www/public/us/en/documents/white-papers/trusted-execution-technology-security-paper.pdf. |
| [11] | MCKEEN F, ALEXANDROVICH I, BERENZON A, et al. Innovative Instructions and Software Model for Isolated Execution[EB/OL]. (2013-06-23) [2025-06-30]. https://doi.org/10.1145/2487726.2488368. |
| [12] | Intel. Intel® 64 and IA-32 Architectures Software Developer’s Manual[EB/OL]. (2017-07-20)[2025-06-30]. https://ia600105.us.archive.org/6/items/Intel_64_and_IA-32_Architectures_Software_Developer_s_Manual_2017_07/325462-sdm-vol-1-2abcd-3abcd.pdf. |
| [13] | KAPLAN D, POWELL J, WOLLER T. AMD Memory Encryption[EB/OL]. (2021-10-18)[2025-06-30]. https://docs.amd.com/v/u/en-US/memory-encryption-white-paper. |
| [14] | AMD. AMD SEV-SNP: Strengthening VM Isolation with Integrity Protection and More[EB/OL]. (2020-01-01)[2025-06-30]. https://docs.amd.com/v/u/en-US/SEV-SNP-strengthening-vm-isolation-with-integrity-protection-and-more. |
| [15] | Intel. Intel® Trust Domain Extensions[EB/OL]. (2021-05-01) [2025-06-30]. https://cdrdv2.intel.com/v1/dl/getContent/690419. |
| [16] | ARM. ARM Security Technology Building a Secure System Using TrustZone Technology[EB/OL]. (2008-12-01)[2025-06-30]. https://developer.arm.com/documentation/PRD29-GENC-009492/latest/. |
| [17] | PINTO S, SANTOS N. Demystifying ARM Trustzone: A Comprehensive Survey[J]. ACM Computing Surveys (CSUR), 2019, 51(6): 1-36. |
| [18] | ARM. ARM CCA Will Put Confidential Compute in the Hands of Every Developer[EB/OL]. (2021-06-23)[2025-06-30]. https://newsroom.arm.com/news/arm-cca-will-put-confidential-compute-in-the-hands-of-every-developer. |
| [19] | ARM. ARM Realm Management Extension(RME) System Architecture[EB/OL]. (2021-06-23)[2025-06-30]. https://developer.arm.com/documentation/den0129/latest/. |
| [20] | TF-HAFNIUM. Hafnium Is the Secure Partition Manager(SPM) Reference Implementation[EB/OL]. (2018-06-28)[2025-06-30]. https://github.com/TF-Hafnium/hafnium. |
| [21] | COSTAN V, LEBEDEV I, DEVADAS S. Sanctum: Minimal Hardware Extensions for Strong Software Isolation[C]// USENIX. The 25th USENIX Security Symposium. Berkeley: USENIX, 2016: 857-874. |
| [22] | LEE D, KOHLBRENNER D, SHINDE S, et al. Keystone: An Open Framework for Architecting Trusted Execution Environments[C]// ACM. The Fifteenth European Conference on Computer Systems. New York: ACM, 2020: 1-16. |
| [23] | NASAHL P, SCHILLING R, WERNER M, et al. HECTOR-V: A Heterogeneous CPU Architecture for a Secure RISC-V Execution Environment[C]// ACM. The 2021 ACM Asia Conference on Computer and Communications Security. New York: ACM, 2021: 187-199. |
| [24] | OZGA W, HUNT G D H, LE M V, et al. ACE: Confidential Computing for Embedded RISC-V Systems[EB/OL]. (2025-05-19) [2025-06-30]. https://arxiv.org/abs/2505.12995. |
| [25] | DUTTA S B, NAGHIBIJOUYBARI H, ABU-GHAZALEH N, et al. Leaky Buddies: Cross-Component Covert Channels on Integrated CPU-GPU Systems[C]// IEEE. 2021 ACM/IEEE 48th Annual International Symposium on Computer Architecture (ISCA). New York: IEEE, 2021: 972-984. |
| [26] | NAGHIBIJOUYBARI H, KHASAWNEH K N, ABU-GHAZALEH N. Constructing and Characterizing Covert Channels on GPGPUs[C]// ACM. The 50th Annual IEEE/ACM International Symposium on Microarchitecture. New York: ACM, 2017: 354-366. |
| [27] | AHN J, KIM J, KASAN H, et al. Network-on-Chip Microarchitecture-Based Covert Channel in GPUs[C]// ACM. The 54th Annual IEEE/ACM International Symposium on Microarchitecture. New York: ACM, 2021: 565-577. |
| [28] | DUTTA S B, NAGHIBIJOUYBARI H, GUPTA A, et al. Spy in the GPU-Box: Covert and Side Channel Attacks on Multi-GPU Systems[C]// ACM. The 50th Annual International Symposium on Computer Architecture. New York: ACM, 2023: 1-13. |
| [29] | ZHANG Zhenkai, ALLEN T, YAO Fan, et al. Tunnels for Bootlegging: Fully Reverse-Engineering GPU TLBs for Challenging Isolation Guarantees of NVIDIA MIG[C]// ACM. The 2023 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2023: 960-974. |
| [30] | ZHU Yuankun, CHENG Yueqiang, ZHOU Husheng, et al. Hermes Attack: Steal DNN Models With Lossless Inference Accuracy[C]// USENIX. The 30th USENIX Security Symposium. Berkeley: USENIX, 2021: 889-906. |
| [31] | HU Xing, LIANG Ling, LI Shuangchen, et al. Deepsniffer: A DNN Model Extraction Framework Based on Learning Architectural Hints[C]// ACM. The 25th International Conference on Architectural Support for Programming Languages and Operating Systems. New York: ACM, 2020: 385-399. |
| [32] | LUO Chao, FEI Yunsi, LUO Pei, et al. Side-Channel Power Analysis of a GPU AES Implementation[C]// IEEE. 2015 33rd IEEE International Conference on Computer Design (ICCD). New York: IEEE, 2015: 281-288. |
| [33] | GAO Yiwen, ZHANG Hailong, CHENG Wei, et al. Electro-Magnetic Analysis of GPU-Based AES Implementation[C]// ACM. The 55th Annual Design Automation Conference. New York: ACM, 2018: 1-6. |
| [34] | ZHAN Zihao, ZHANG Zhenkai, LIANG Sisheng, et al. Graphics Peeping Unit: Exploiting EM Side-Channel Information of GPUs to Eavesdrop on Your Neighbors[C]// IEEE. 2022 IEEE Symposium on Security and Privacy. New York: IEEE, 2022: 1440-1457. |
| [35] | JANG I, TANG A, KIM T, et al. Heterogeneous Isolated Execution for Commodity GPUs[C]// ACM. The 24th International Conference on Architectural Support for Programming Languages and Operating Systems. New York: ACM, 2019: 455-468. |
| [36] | DENG Yunjie, WANG Chenxu, YU Shunchang, et al. Strongbox: A GPU TEE on ARM Endpoints[C]// ACM. The 2022 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2022: 769-783. |
| [37] | WANG Chenxu, ZHANG Fengwei, DENG Yunjie, et al. CAGE: Complementing Arm CCA With GPU Extensions[EB/OL]. (2024-02-27)[2025-06-30]. https://www.ndss-symposium.org/wp-content/uploads/2024-763-paper.pdf. |
| [38] | MAI Haohui, ZHAO Jiacheng, ZHENG Hongren, et al. Honeycomb: Secure and Efficient GPU Executions via Static Validation[C]// USENIX. The 17th USENIX Symposium on Operating Systems Design and Implementation. Berkeley: USENIX, 2023: 155-172. |
| [39] | IVANOV A, ROTHENBERGER B, DETHISE A, et al. SAGE: Software-Based Attestation for GPU Execution[C]// USENIX. 2023 USENIX Annual Technical Conference. Berkeley: USENIX, 2023: 485-499. |
| [40] | ZHU Jianping, HOU Rui, WANG Xiaofeng, et al. Enabling Rack-Scale Confidential Computing Using Heterogeneous Trusted Execution Environment[C]// IEEE. 2020 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2020: 1450-1465. |
| [41] | NVIDIA. NVIDIA Confidential Computing[EB/OL]. (2022-04-25) [2025-06-30]. https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/. |
| [42] | GU Zhongshu, VALDEZ E, AHMED S, et al. NVIDIA GPU Confidential Computing Demystified[EB/OL]. (2025-07-03)[2025-07-15]. https://arxiv.org/abs/2507.02770. |
| [43] | XU Tao, KONG Shuaidi, LIU Caihua, et al. A Review of Heterogeneous Confidential Computing[J]. Journal of Jilin University (Engineering Edition), 2025, 55(3): 755-770. |
| 徐涛, 孔帅迪, 刘才华, 等. 异构机密计算综述[J]. 吉林大学学报(工学版), 2025, 55(3):755-770. |
| [1] | 拾以娟, 周丹平, 范磊, 刘茵. 基于可信执行环境的安全多方计算协议[J]. 信息网络安全, 2025, 25(9): 1439-1446. |
| [2] | 朱辉, 方云依, 王枫为, 许伟. 融合机密计算的数据安全处理研究进展[J]. 信息网络安全, 2025, 25(11): 1643-1657. |
| [3] | 关志, 胡建斌, 李悦, 陈钟. 基于可信执行环境的区块链技术与应用综述[J]. 信息网络安全, 2025, 25(11): 1673-1690. |
| [4] | 任丰原, 张馨月, 雷卓祎, 刘忻. 基于机密计算的键值数据存储与操作优化方法研究[J]. 信息网络安全, 2025, 25(11): 1707-1717. |
| [5] | 薛开平, 张淳一, 柳枫, 王峰. 基于可信执行环境的加密数据库索引安全增强方案[J]. 信息网络安全, 2025, 25(11): 1718-1731. |
| [6] | 赵波, 吕佳敏, 王一琁. 一种面向容器生命周期的多维安全度量架构[J]. 信息网络安全, 2025, 25(11): 1745-1761. |
| [7] | 王亚杰, 陆锦标, 李宇航, 范青, 张子剑, 祝烈煌. 基于可信执行环境的联邦学习分层动态防护算法[J]. 信息网络安全, 2025, 25(11): 1762-1773. |
| [8] | 卢笛, 刘玉佳, 吕超越, 孙梦娜, 张清文, 杨力. 一种云原生TEE服务共享机制[J]. 信息网络安全, 2025, 25(11): 1774-1791. |
| [9] | 金娃, 秦宇, 刘菁润, 尚科彤, 贾梦涵, 林江南. 基于机密计算平台的TEE和TPM硬件可信信道构建方案[J]. 信息网络安全, 2025, 25(11): 1792-1810. |
| [10] | 胡宇义, 蔡炜, 陈竞凡, 刘莫寒, 王鹃, 何运. 面向机密容器的统一远程证明机制研究[J]. 信息网络安全, 2025, 25(11): 1811-1823. |
| [11] | 余发江, 王朝州. TrustZone半虚拟化与容器化实现机制[J]. 信息网络安全, 2025, 25(10): 1523-1536. |
| [12] | 孙钰, 熊高剑, 刘潇, 李燕. 基于可信执行环境的安全推理研究进展[J]. 信息网络安全, 2024, 24(12): 1799-1818. |
| [13] | 唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65. |
| [14] | 刘忻, 李韵宜, 王淼. 一种基于机密计算的联邦学习节点轻量级身份认证协议[J]. 信息网络安全, 2022, 22(7): 37-45. |
| [15] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||