信息网络安全 ›› 2025, Vol. 25 ›› Issue (11): 1745-1761.doi: 10.3969/j.issn.1671-1122.2025.11.008
一种面向容器生命周期的多维安全度量架构
1.武汉大学国家网络安全学院 武汉 430072 2.空天信息安全与可信计算教育部重点实验室 武汉 430072
-
收稿日期:2025-06-11出版日期:2025-11-10发布日期:2025-12-02 -
通讯作者:赵波zhaobo@whu.edu.cn -
作者简介:赵波(1972—),男,山东,教授,博士,CCF高级会员,主要研究方向为系统安全、可信计算|吕佳敏(2001—),女,山西,硕士研究生,主要研究方向为系统安全、可信计算|王一琁(1994—),男,江苏,博士研究生,主要研究方向为网络安全、知识图谱 -
基金资助:国家自然科学基金(U1936122)
A Multidimensional Security Measurement Architecture for the Container Lifecycle
ZHAO Bo1,2( ), LYU Jiamin1,2, WANG Yixuan1,2
), LYU Jiamin1,2, WANG Yixuan1,2
1. School of Cyber Science and Engineering ,Wuhan University Wuhan 430072, China 2. Key Laboratory of Aerospace Information Security and Trusted Computing of Ministry of Education Wuhan 430072, China
-
Received:2025-06-11Online:2025-11-10Published:2025-12-02
摘要:
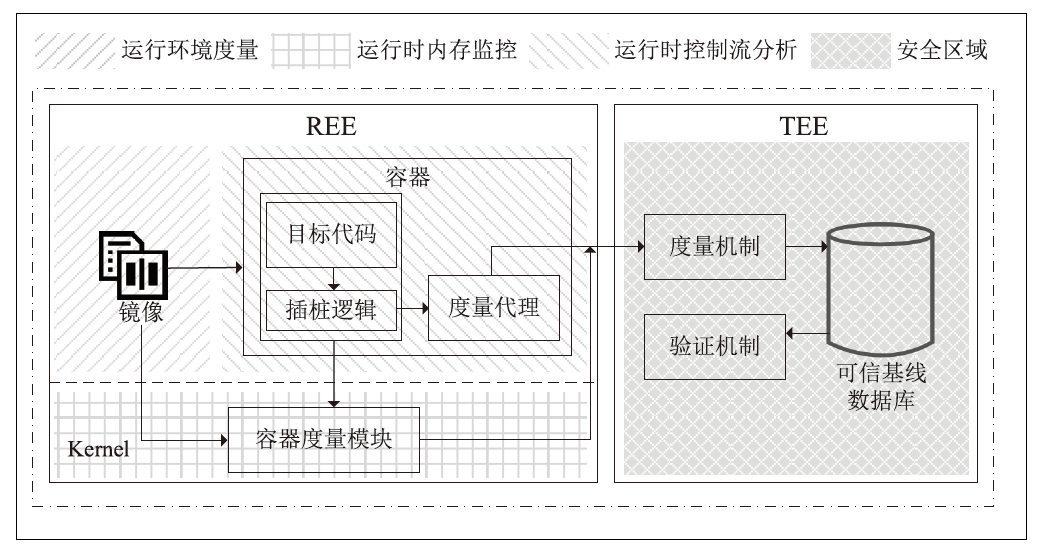
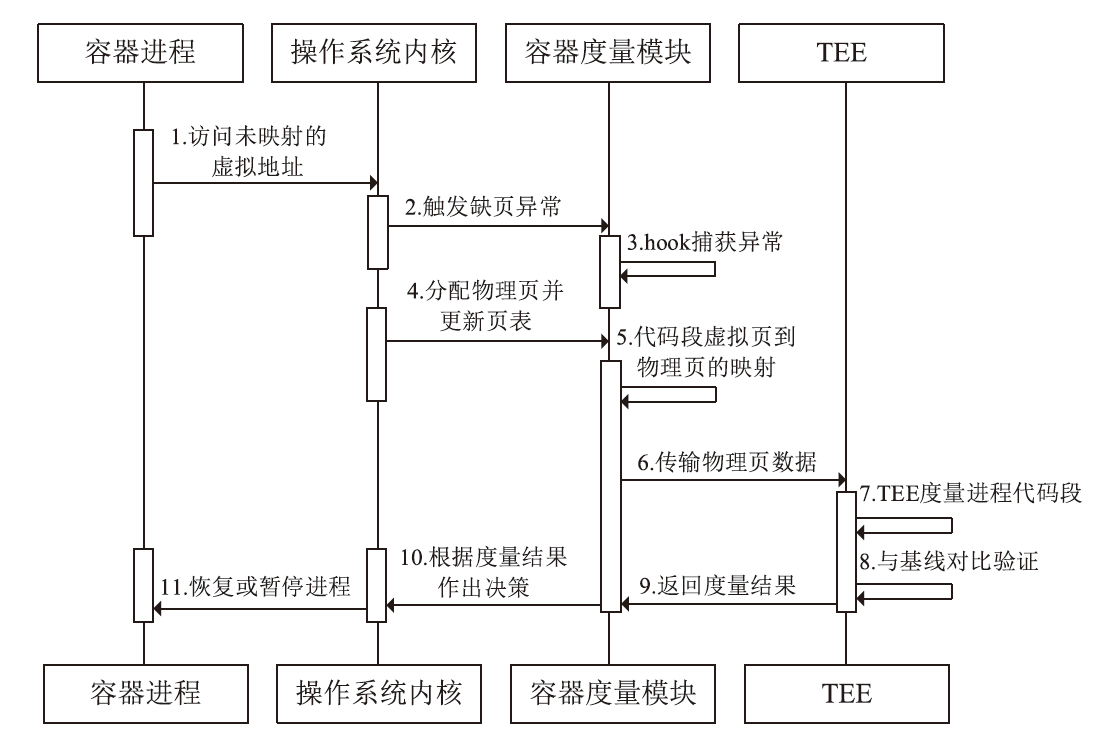
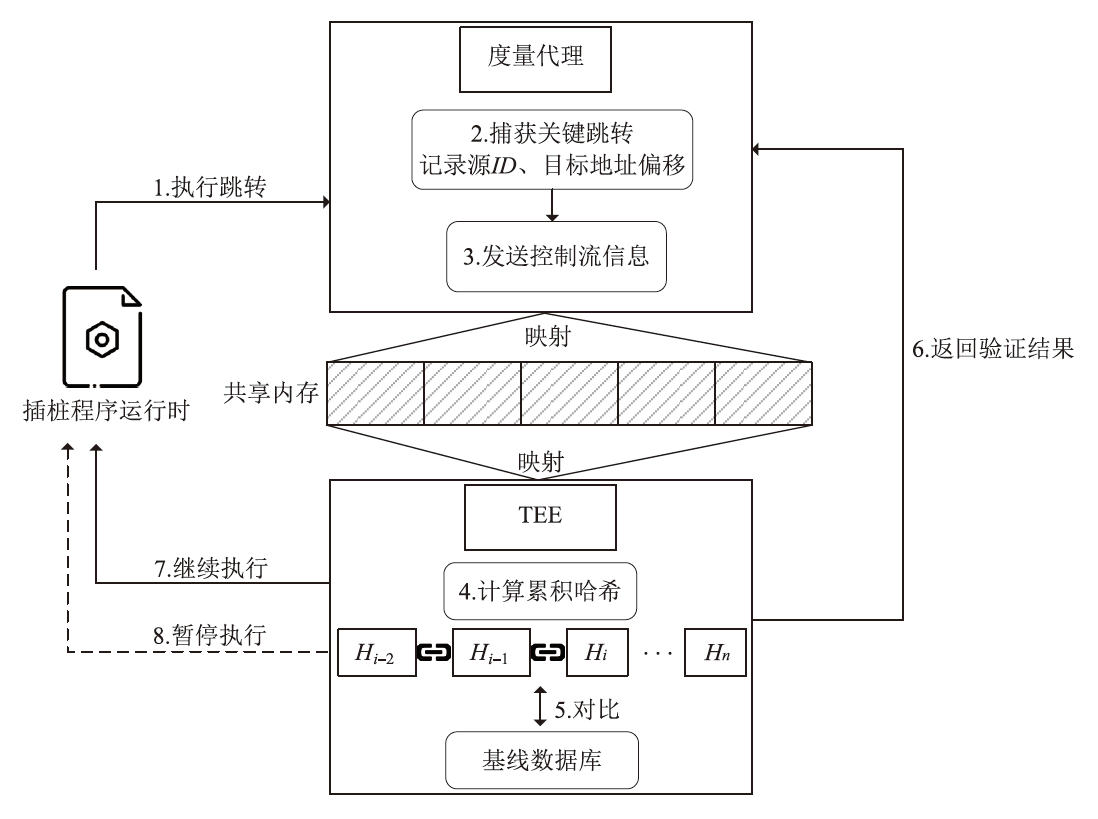
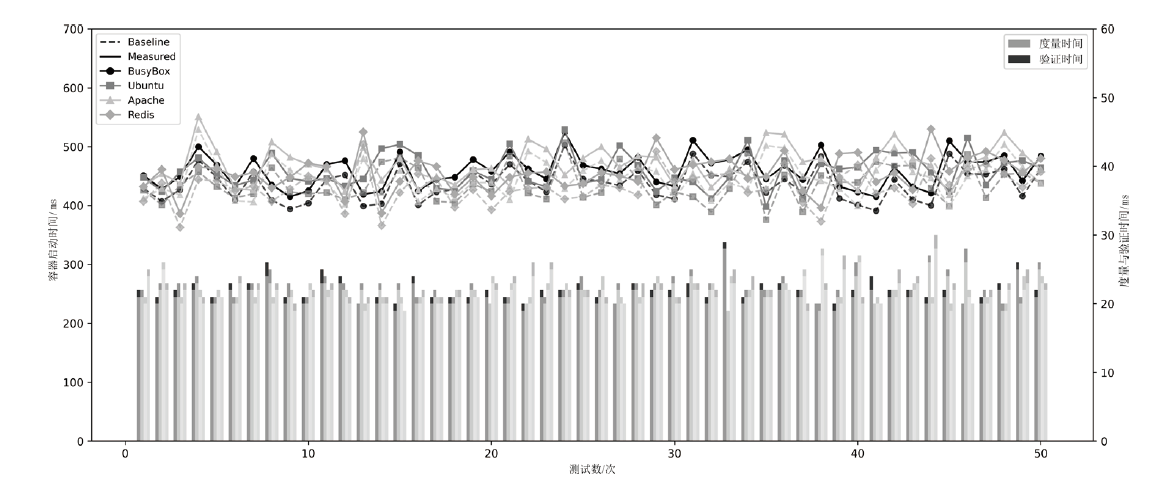
容器面临的安全威胁日益复杂,基于可信执行环境(TEE)的安全方案已成为提升容器可信性的有效手段。然而,现有方案多聚焦于启动阶段的静态度量,或仅监控运行时的局部行为,难以全面覆盖容器生命周期,尤其难以应对控制流劫持等复杂攻击。同时,TEE通信多采用同步交互,频繁传输易引发网络阻塞与性能瓶颈。因此,文章提出一种面向容器生命周期的多维安全度量架构,覆盖容器构建与运行阶段,实时监控内存变化与间接跳转、间接函数调用和函数返回等关键控制流行为,实现持续完整性保护。此外,文章设计了基于TrustZone的跨域通信机制,结合共享内存、环形缓冲区与信号量,实现了度量信息的高效安全传输。实验结果表明,文章所提架构在提升容器完整性度量能力的同时可以保持较低的性能开销,能够满足云原生环境和多租户平台的需求。
中图分类号:
引用本文
赵波, 吕佳敏, 王一琁. 一种面向容器生命周期的多维安全度量架构[J]. 信息网络安全, 2025, 25(11): 1745-1761.
ZHAO Bo, LYU Jiamin, WANG Yixuan. A Multidimensional Security Measurement Architecture for the Container Lifecycle[J]. Netinfo Security, 2025, 25(11): 1745-1761.
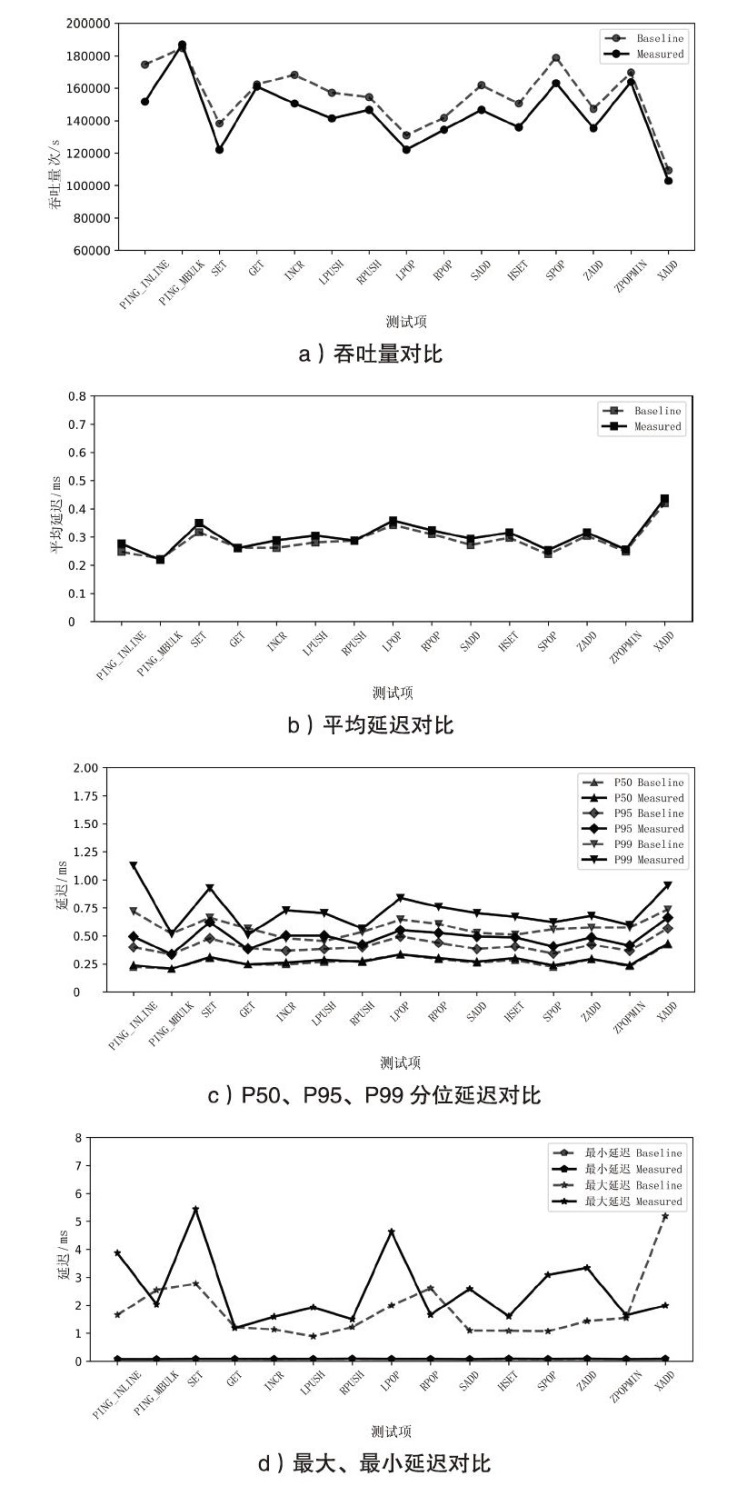
表3
Redis引入度量的延迟性能开销
| 测试项 | avg | min | P50 | P95 | P99 | max |
|---|---|---|---|---|---|---|
| PING_INLINE | 11.3% | 24.1 | 7.2% | 24.1% | 56.7% | 133.9% |
| PING_MBULK | -1.8% | 0 | 0 | 0 | 0 | -20.1% |
| SET | 10.1% | 30.1% | 2.6% | 30.1% | 39.8% | 96.0% |
| GET | -0.4% | -2.0% | 0 | -2.0% | -9.9% | -2.6% |
| INCR | 9.9% | 37.1% | 6.5% | 37.1% | 51.8% | 40.2% |
| LPUSH | 8.5% | 31.3% | 5.9% | 31.3% | 54.5% | 117.2% |
| RPUSH | 0 | 6.0% | -2.9% | 6.0% | 6.0% | 22.9% |
| LPOP | 4.4% | 11.3% | 0 | 11.3% | 29.7% | 132.6% |
| RPOP | 4.5% | 20.0% | 2.7% | 20.0% | 25.0% | -36.2% |
| SADD | 8.1% | 29.2% | 3.0% | 29.2% | 33.4% | 135.9% |
| HSET | 6.4% | 19.7% | 5.6% | 19.7% | 31.3% | 47.8% |
| SPOP | 6.3% | 18.7% | 7.2% | 18.7% | 11.4% | 188.2% |
| ZADD | 3.9% | 15.1% | 0 | 15.1% | 18.9% | 131.8% |
| ZPOPMIN | 2.8% | 13.1% | 3.5% | 13.1% | 4.2% | 6.2% |
| XADD | 3.8% | 16.9% | 1.9% | 16.9% | 29.4% | -61.7% |
| [1] | JARKAS O, KO R, DONG N, et al. A Container Security Survey: Exploits, Attacks, and Defenses[J]. ACM Computing Surveys, 2025, 57(7): 279-314. |
| [2] | ZHANG Xinyi, WU Zehui, JIA Qiong, et al. Demand-Driven Container Security Policy Automatic Generation Technology[J]. Journal of Chinese Computer Systems. 2024, 45(4): 951-959. |
| 张新义, 武泽慧, 贾琼, 等. 需求驱动的容器安全策略自动生成技术[J]. 小型微型计算机系统. 2024, 45(4): 951-959. | |
| [3] | VS D P, SETHURAMAN S C, KHAN M K. Container Security: Precaution Levels, Mitigation Strategies and Research Perspectives[EB/OL]. (2023-09-22)[2025-05-15]. https://www.sciencedirect.com/science/article/pii/S0167404823004005. |
| [4] | GAO Xing, GU Zhongshu, KAYAALP M, et al. Containerleaks: Emerging Security Threats of Information Leakages in Container Clouds[C]// IEEE. 2017 the 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). New York: IEEE, 2017: 237-248. |
| [5] |
LIU Ziwen, FENG Dengguo. Dynamic Integrity Measurement Architecture Based on Trusted Computing[J]. Journal of Electronics and Information Technology, 2010, 32(4):875-879.
doi: 10.3724/SP.J.1146.2009.00408 URL |
| 刘孜文, 冯登国. 基于可信计算的动态完整性度量架构[J]. 电子与信息学报, 2010, 32(4):875-879. | |
| [6] | HUA Zhichao, YU Yang, GU Jingyu, et al. TZ-Container: Protecting Container from Untrusted OS with ARM TrustZone[J]. China Information Sciences, 2021, 64(9): 192101-192117. |
| [7] | SONG Liantao, DING Yan, GUO Yong, et al. Dimac: Dynamic Integrity Measurement Architecture for Containers with ARM TrustZone[C]// IEEE. 2024 IEEE International Conference on Web Services (ICWS). New York: IEEE, 2024: 844-852. |
| [8] | HAN Yufei, LI Chao, ZHANG Jianbiao, et al. DMSCTS: Dynamic Measurement Scheme for the Containers-Hybrid-Deployment Based on Trusted Subsystem[EB/OL]. (2024-10-16)[2025-04-21]. https://www.sciencedirect.com/science/article/pii/S0167404824004632. |
| [9] | Intel. Intel® Trust Domain Extensions[EB/OL]. (2023-01-10)[2025-05-15]. https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/documentation.html. |
| [10] | Advanced Micro Devices. AMD SEV-SNP: Strengthening VM Isolation with Integrity Protection and More[EB/OL]. (2020-01-30)[2025-05-15]. https://www.amd.com/content/dam/amd/en/documents/epyc-business-docs/white-papers/SEV-SNP-strengthening-vm-isolation-with-integrity-protection-and-more.pdf |
| [11] | ARM. ARM Confidential Compute Architecture[EB/OL]. (2021-07-23)[2025-05-15]. https://www.arm.com/architecture/security-features/arm-confidential-compute-architecture. |
| [12] | MERKEL D. Docker: Lightweight Linux Containers for Consistent Development and Deployment[J]. Linux Journal, 2014, 239(2): 76-91. |
| [13] | MORABITO R, KJALLMAN J, KOMU M. Hypervisors vs. Lightweight Virtualization: A Performance Comparison[C]// IEEE. 2015 IEEE International Conference on Cloud Engineering. New York: IEEE, 2015: 386-393. |
| [14] | SOLTESZ S, POTZL H, FIUCZYNSKI M E, et al. Container-Based Operating System Virtualization: A Scalable, High-Performance Alternative to Hypervisors[J]. ACM SIGOPS Operating Systems Review, 2007, 42(3): 275-287. |
| [15] |
SULTAN S, AHMAD I, DIMITRIOU T. Container Security: Issues, Challenges and the Road Ahead[J]. IEEE Access, 2019, 7: 52976-52996.
doi: 10.1109/Access.6287639 URL |
| [16] | Microsoft. Secure the Windows Boot Process[EB/OL]. (2024-02-18)[2025-04-21]. https://learn.microsoft.com/en-us/windows/security/operating-system-security/system-security/secure-the-windows-10-boot-process. |
| [17] | TAO Zhe, RASTOGI A, GUPTA N, et al. DICE*: A Formally Verified Implementation of DICE Measured Boot[C]// USENIX. The 30th USENIX Security Symposium (USENIX Security 21). Berkeley: USENIX, 2021: 1091-1107. |
| [18] | STEFFEN A. The Linux Integrity Measurement Architecture and TPM-Based Network Endpoint Assessment[C]// Linux Foundation. Linux Security Summit. San Diego: Linux Foundation, 2012: 1-12. |
| [19] | LUO Wu, SHEN Qingni, XIA Yuyang, et al. Container-IMA: A Privacy-Preserving Integrity Measurement Architecture for Containers[C]// USENIX. The 22nd International Symposium on Research in Attacks, Intrusions and Defenses (RAID 2019). Berkeley: USENIX, 2019: 487-500. |
| [20] | SUN Yuqiong, SAFFORD D, ZOHAR M, et al. Security Namespace: Making Linux Security Frameworks Available to Containers[C]// USENIX. The 27th USENIX Security Symposium (USENIX Security 18). Berkeley: USENIX, 2018: 1423-1439. |
| [21] | MCKEEN F, ALEXANDROVICH I, BERENZON A, et al. Innovative Instructions and Software Model for Isolated Execution[C]// ACM. The 2nd International Workshop on Hardware and Architectural Support for Security and Privacy (HASP 2013). New York: ACM, 2013: 73-81. |
| [22] | ARM. ARM TrustZone Technology[EB/OL]. (2019-02-05)[2025-05-19]. https://developer.arm.com/documentation/100690/0201/?lang=en. |
| [23] | HUA Zhichao, YU Yang, GU Jinyu, et al. TZ-Container: Protecting Container from Untrusted OS with ARM TrustZone[EB/OL]. (2021-08-19)[2025-05-15]. https://link.springer.com/article/10.1007/s11432-019-2707-6. |
| [24] | Confidential Containers Community. Enclave-CC: Process-Based Confidential Container Solution Leveraging Intel SGX[EB/OL]. (2022-01-13)[2025-05-15]. https://github.com/confidential-containers/enclave-cc. |
| [25] | Alibaba Cloud and CNCF. Inclavare Containers Overview[EB/OL]. (2022-06-30)[2025-05-15]. https://openanolis-downloads.oss-cn-beijing.aliyuncs.com/meetup/Inclavare-Containers_Overview_rev11.pdf. |
| [26] | BIONDO A, CONTI M, DAVI L, et al. The Guard’s Dilemma: Efficient Code-Reuse Attacks against Intel SGX[C]// USENIX. The 27th USENIX Security Symposium (USENIX Security 18). Berkeley: USENIX, 2018: 1213-1227. |
| [27] | ERLINGSSON M, JIGATTI J. Control-Flow Integrity[C]// ACM. The 12th ACM Conference on Computer and Communications Security. New York: ACM, 2005: 340-353. |
| [28] | BUCHANAN E, ROEMER R, SHACHAM H, et al. When Good Instructions Go Bad: Generalizing Return-Oriented Programming to RISC[C]// ACM. The 15th ACM Conference on Computer and Communications Security. New York: ACM, 2008: 27-38. |
| [29] | BLETSCH T, JIANG Xuxian, FREEH V W, et al. Jump-Oriented Programming: A New Class of Code-Reuse Attack[C]// ACM. The 6th ACM Symposium on Information, Computer and Communications Security. New York: ACM, 2011: 30-40. |
| [30] | NETO A J, NUNES I D O. ISC-FLAT: On the Conflict between Control Flow Attestation and Real-Time Operations[C]// IEEE. 2023 IEEE 29th Real-Time and Embedded Technology and Applications Symposium (RTAS). New York: IEEE, 2023: 133-146. |
| [31] | BIONDO A, CONTI M, DAVI L, et al. Modular Control-Flow Integrity[C]// ACM. The 2014 ACM Conference on Computer and Communications Security (CCS’14). New York: ACM, 2014: 577-587. |
| [32] | BAUER M, GRISHCHENKO I, ROSSOW C. TyPro: Forward CFI for C-Style Indirect Function Calls Using Type Propagation[C]// ACM. Annual Computer Security Applications Conference (ACSAC 2022). New York: ACM, 2022: 346-360. |
| [33] | ZHOU Jie, DU Yingqi, SHEN Zhi, et al. Silhouette: Efficient Protected Shadow Stacks for Embedded Systems[C]// USENIX.The 29th USENIX Security Symposium (USENIX Security 20). Berkeley: USENIX, 2020: 1219-1236. |
| [34] | WANG Jinwen, WANG Yujie, LI Ao, et al. ARI: Attestation of Real-Time Mission Execution Integrity[C]// USENIX. The 32nd USENIX Security Symposium (USENIX Security 23). Berkeley: USENIX, 2023: 2761-2778. |
| [35] | SUN Zhichuang, FENG Bo, LU Long, et al. OAT: Attesting Operation Integrity of Embedded Devices[C]// IEEE. 2020 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2020: 1433-1449. |
| [36] | CAULFIELD A, RATTANAVIPANON N, NUNES I D O. ACFA: Secure Runtime Auditing & Guaranteed Device Healing via Active Control Flow Attestation[C]// USENIX. The 32nd USENIX Security Symposium (USENIX Security 23). Berkeley: USENIX, 2023: 5827-5844. |
| [1] | 拾以娟, 周丹平, 范磊, 刘茵. 基于可信执行环境的安全多方计算协议[J]. 信息网络安全, 2025, 25(9): 1439-1446. |
| [2] | 路新喜, 郭建伟, 苑立娟, 柳燕, 徐彬彬, 刘杨. 基于命名空间与文件系统代理的容器安全框架研究[J]. 信息网络安全, 2025, 25(8): 1196-1207. |
| [3] | 黄轲, 李璇, 周庆飞, 尚科彤, 秦宇. 基于eBPF的容器运行时可信监控方案[J]. 信息网络安全, 2025, 25(2): 306-326. |
| [4] | 郝萌, 李佳勇, 杨洪伟, 张伟哲. 异构CPU-GPU系统机密计算综述[J]. 信息网络安全, 2025, 25(11): 1658-1672. |
| [5] | 关志, 胡建斌, 李悦, 陈钟. 基于可信执行环境的区块链技术与应用综述[J]. 信息网络安全, 2025, 25(11): 1673-1690. |
| [6] | 薛开平, 张淳一, 柳枫, 王峰. 基于可信执行环境的加密数据库索引安全增强方案[J]. 信息网络安全, 2025, 25(11): 1718-1731. |
| [7] | 王亚杰, 陆锦标, 李宇航, 范青, 张子剑, 祝烈煌. 基于可信执行环境的联邦学习分层动态防护算法[J]. 信息网络安全, 2025, 25(11): 1762-1773. |
| [8] | 卢笛, 刘玉佳, 吕超越, 孙梦娜, 张清文, 杨力. 一种云原生TEE服务共享机制[J]. 信息网络安全, 2025, 25(11): 1774-1791. |
| [9] | 金娃, 秦宇, 刘菁润, 尚科彤, 贾梦涵, 林江南. 基于机密计算平台的TEE和TPM硬件可信信道构建方案[J]. 信息网络安全, 2025, 25(11): 1792-1810. |
| [10] | 胡宇义, 蔡炜, 陈竞凡, 刘莫寒, 王鹃, 何运. 面向机密容器的统一远程证明机制研究[J]. 信息网络安全, 2025, 25(11): 1811-1823. |
| [11] | 余发江, 王朝州. TrustZone半虚拟化与容器化实现机制[J]. 信息网络安全, 2025, 25(10): 1523-1536. |
| [12] | 孙钰, 熊高剑, 刘潇, 李燕. 基于可信执行环境的安全推理研究进展[J]. 信息网络安全, 2024, 24(12): 1799-1818. |
| [13] | 唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65. |
| [14] | 夏懿航, 张志龙, 王木子, 陈力波. 基于依赖关系的容器供应链脆弱性检测方法[J]. 信息网络安全, 2023, 23(2): 76-84. |
| [15] | 吴圣麟, 刘汪根, 严明, 吴杰. 基于无监督系统调用规则生成的容器云实时异常检测系统[J]. 信息网络安全, 2023, 23(12): 91-102. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||