信息网络安全 ›› 2022, Vol. 22 ›› Issue (7): 73-83.doi: 10.3969/j.issn.1671-1122.2022.07.009
一种基于SGX的轻量Fabric链码可信执行环境构建方法
KELEKET GOMA Christy Junior Yannick1,2, 易文哲1,2, 王鹃1,2( )
)
- 1.武汉大学国家网络安全学院,武汉 430072
2.武汉大学空天信息安全与可信计算教育部重点实验室,武汉 430072
-
收稿日期:2022-03-05出版日期:2022-07-10发布日期:2022-08-17 -
通讯作者:王鹃 E-mail:jwang@whu.edu.cn -
作者简介:KELEKET GOMA Christy Junior Yannick(1986—),男,刚果共和国,硕士研究生,主要研究方向为区块链安全和可信计算|易文哲(2001—),男,湖北,硕士研究生,主要研究方向为区块链安全、可信计算、系统与网络安全|王鹃(1976—),女,湖北,教授,博士,主要研究方向为系统与软件安全、可信计算、人工智能应用、云计算、物联网安全 -
基金资助:国家自然科学基金(61872430);国家重点研发计划(2014CB340600);湖北省重点研发项目(2020BAB101)
A Lightweight Trusted Execution Environment Construction Method for Fabric Chaincode Based on SGX
KELEKET GOMA Christy Junior Yannick1,2, YI Wenzhe1,2, WANG Juan1,2( )
)
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan 430072, China
2. Key Laboratory of Aerospace Information Security and Trusted Computing of Ministry of Education, Wuhan University, Wuhan 430072, China
-
Received:2022-03-05Online:2022-07-10Published:2022-08-17 -
Contact:WANG Juan E-mail:jwang@whu.edu.cn
摘要:
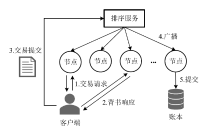
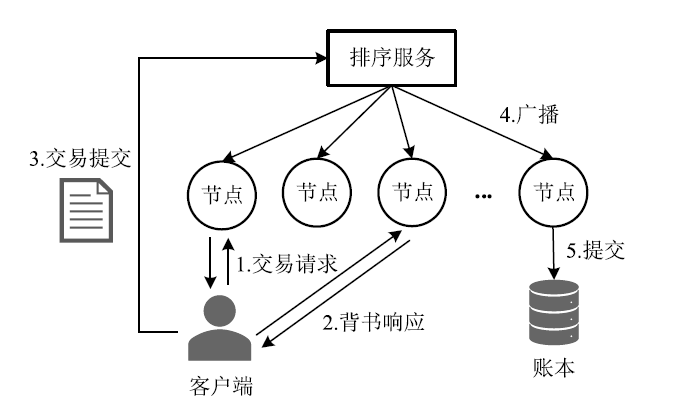
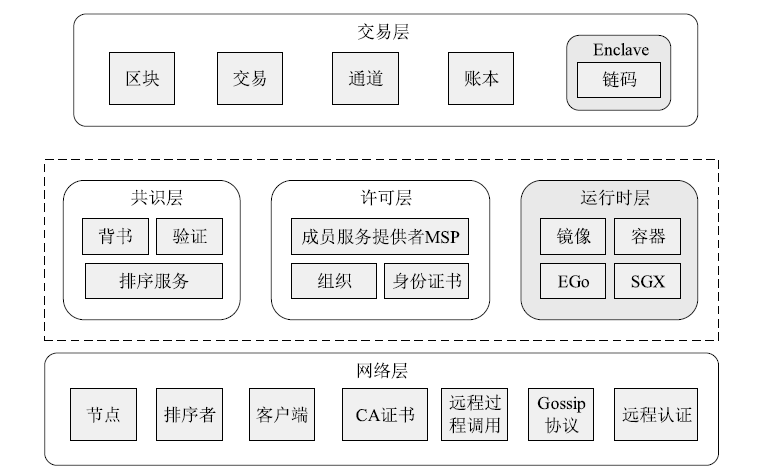
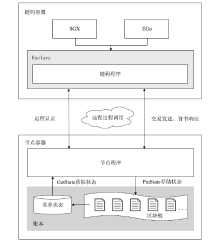
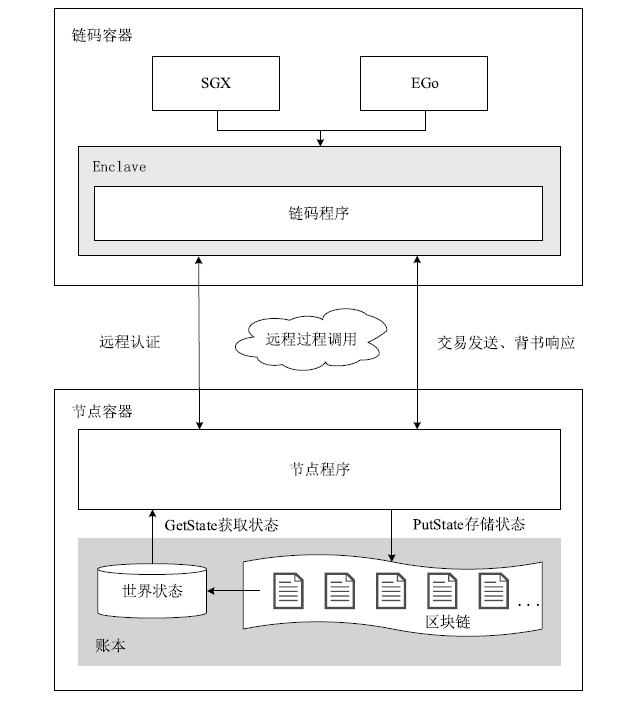
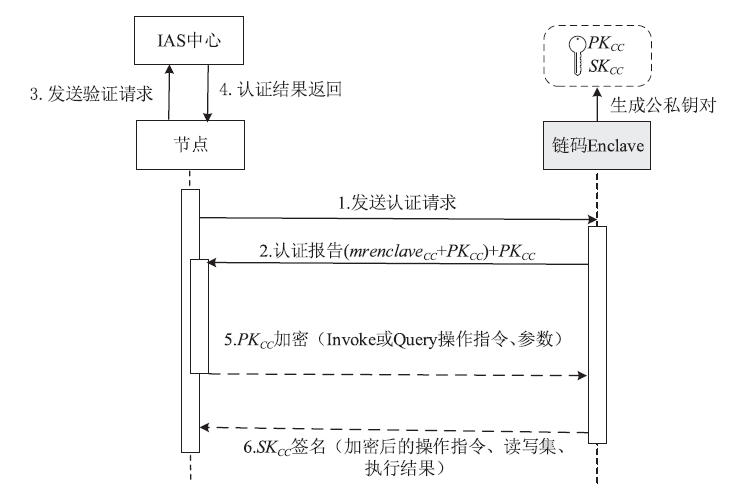
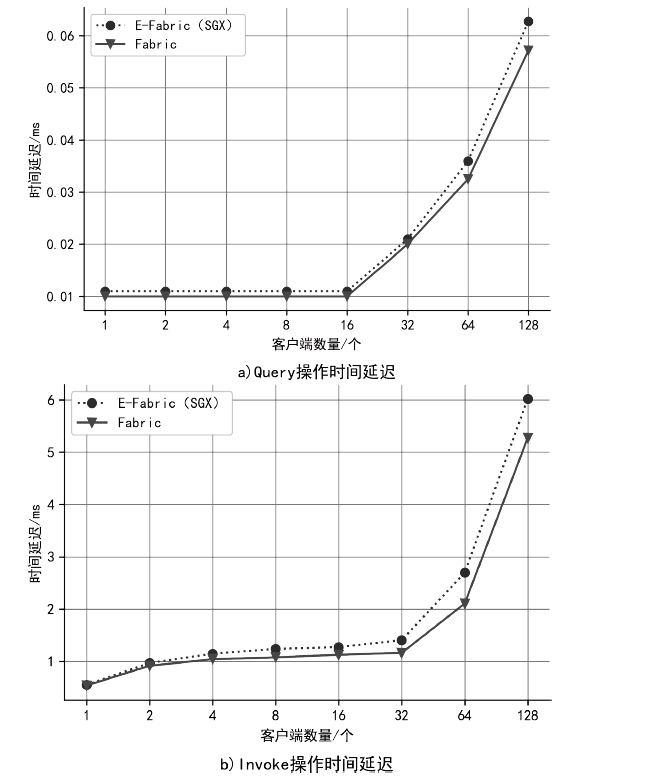
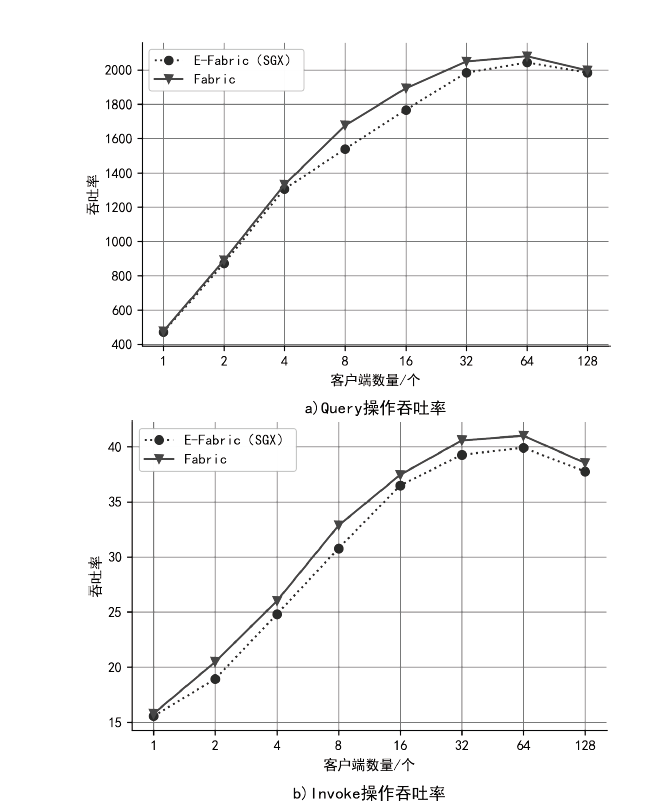
Hyperledger Fabric是一个开源分布式账本平台,其不仅拥有公有链防篡改、分布式记账的特点,还具有身份识别、数据保密、低延迟、高吞吐率等优点。传统Fabric架构中的链码缺乏安全执行环境,其容器执行环境会带来隐私泄露风险,而现有的智能合约隐私保护方案无法适用于Go语言链码架构,且性能开销较大。因此,文章提出一种基于SGX的轻量Fabric链码可信执行环境构建方法及E-Fabric架构,搭建支持原生Go语言的可信镜像和容器,为链码创建可信执行环境,并通过远程认证协议验证链码是否可信。理论评估和数据测试结果表明,SGX Enclave的构建会适当增加开销,与原Fabric架构相比,E-Fabric的延迟升高了8%左右,吞吐率下降了4%左右,但整体性能达到原网络的94%,并且具有较小的可信计算基和更好的安全性。
中图分类号:
引用本文
KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83.
KELEKET GOMA Christy Junior Yannick, YI Wenzhe, WANG Juan. A Lightweight Trusted Execution Environment Construction Method for Fabric Chaincode Based on SGX[J]. Netinfo Security, 2022, 22(7): 73-83.
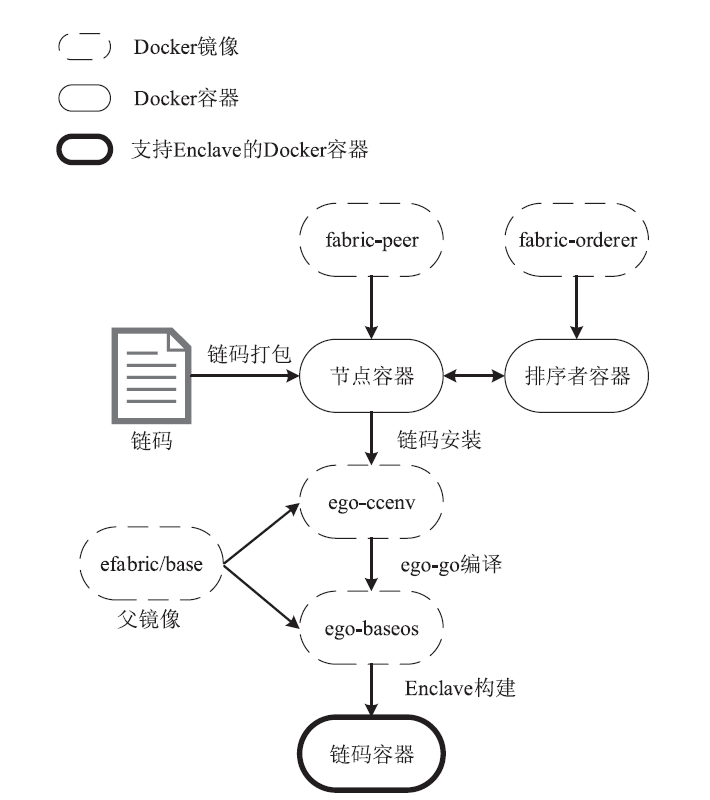
表1
E-Fabric核心镜像
| 镜像名称 | 父镜像 | 基本功能 |
|---|---|---|
| fabric-peer | alpine:3.10 | peer节点镜像,安装peer相关文件,用于生成peer运行容器 |
| fabric-orderer | alpine:3.10 | 排序节点镜像,安装orderer相关文件,用于生成orderer运行容器 |
| efabric/base | ubuntu:20.04 | E-Fabric可信基础镜像,作为链码编译、运行的父镜像 |
| ego-baseos | efabric/base:0.1 | Go链码可信运行镜像,用于生成链码运行容器 |
| ego-ccenv | efabric/base:0.1 | Go链码可信编译镜像,在链码实例化过程中作为默认编译环境将链码编译为二进制文件 |
表2
E-Fabric可信接口
| API名称 | 功能 |
|---|---|
| func AskAttestation(chaincodeAddr string)(Report, error) | 向指定地址的链码发送认证请求 |
| func SendAttestation(peerAddr string, Report struct)(error) | 将身份认证报告发送给指定地址peer节点 |
| func VerifyAttestation(IASAddr string, Report struct)(Result,error) | peer节点向IAS中心发送验证请求 |
| func EncryptOperation(operation struct, key string)(enOperation,error) | 加密操作指令(Invoke或Query) |
| func DecryptOperation(enOperation struct, key string)(deOperation,error) | 解密操作指令 |
| func SignResult(result struct, key string)(siResult,error) | 签名操作指令 |
| [1] | NOFER M, GOMBER P, HINZ O, et al. Blockchain[J]. Business & Information Systems Engineering, 2017, 59(3): 183-187. |
| [2] |
ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. Blockchain Challenges and Opportunities: A Survey[J]. International Journal of Web and Grid Services, 2018, 14(4): 352-375.
doi: 10.1504/IJWGS.2018.095647 URL |
| [3] | YAGA D, MELL P, ROBY N, et al. Blockchain Technology Overview[EB/OL]. (2019-06-26)[2021-10-13]. https://arxiv.org/abs/1906.11078. |
| [4] | YAJI S, BANGERA K, NEELIMA B. Privacy Preserving in Blockchain Based on Partial Homomorphic Encryption System for AI Applications[C]// IEEE. 2018 IEEE 25th International Conference on High Performance Computing Workshops (HiPCW). New York: IEEE, 2018: 81-85. |
| [5] | SUN Xiaoqiang, YU F R, ZHANG Peng, et al. A Survey on Zero-Knowledge Proof in Blockchain[J]. IEEE Network, 2021, 35(4): 198-205. |
| [6] | YE Shaochen. Research on Verifiable Byzantine Fault Tolerant Consensus Mechanism Based on Secure Multi-Party Computing in Blockchain[D]. Beijing: Beijing University of Posts and Telecommunications, 2021. |
| 叶少宸. 区块链中基于安全多方计算的可验证拜占庭容错共识机制的研究[D]. 北京: 北京邮电大学, 2021. | |
| [7] | WANG Cuihan, ZHAO Chen, XU Xiaogang, et al. Distributed Paralel Computing Environment: MPI[J]. Computer Science, 2003, 30(1): 25-26. |
| 王萃寒, 赵晨, 许小刚, 等. 分布式并行计算环境:MPI[J]. 计算机科学, 2003, 30(1): 25-26. | |
| [8] | COSTAN V, DEVADAS S. Intel SGX Explained[EB/OL]. (2016-08-06)[2021-09-13]. http://css.csail.mit.edu/6.858/2020/readings/costan-sgx.pdf. |
| [9] | Intel Corporation. Intel(R) Software Guard Extensions Developer Guide[EB/OL]. (2021-11-02)[2021-12-20]. https://download.01.org/intel-sgx/sgx-linux/2.15.1/docs/Intel_SGX_Developer_Guide.pdf. |
| [10] | KOSBA A, MILLER A, SHI E, et al. Hawk: The Blockchain Model of Cryptography and Privacy-Preserving Smart Contracts[C]// IEEE. 2016 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2016: 839-858. |
| [11] | RUSSINOVICH M, ASHTON E, AVANESSIANS C, et al. CCF: A Framework for Building Confidential Verifiable Replicated Services[EB/OL]. (2019-09-24)[2021-12-03]. https://www.microsoft.com/en-us/research/publication/ccf-a-framework-for-building-confidential-verifiable-replicated-services/. |
| [12] | CHENG R, ZHANG Fan, KOS J, et al. Ekiden: A Platform for Confidentiality-Preserving, Trustworthy, and Performant Smart Contracts[C]// IEEE. 2019 IEEE European Symposium on Security and Privacy (EuroS&P). New York: IEEE, 2019: 185-200. |
| [13] | BRANDENBURGER M, CACHIN C, KAPITZA R, et al. Trusted Computing Meets Blockchain: Rollback Attacks and a Solution for Hyperledger Fabric[C]// IEEE. 2019 38th Symposium on Reliable Distributed Systems (SRDS). New York: IEEE, 2019: 324-329. |
| [14] | ANDROULAKI E, BARGER A, BORTNIKOV V, et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains[C]// ACM. Proceedings of the Thirteenth EuroSys Conference. New York: ACM, 2018: 1-15. |
| [15] | CACHIN C. Architecture of the Hyperledger Blockchain Fabric[EB/OL]. (2016-06-04)[2021-12-26]. https://www.zurich.ibm.com/dccl/papers/cachin_dccl.pdf. |
| [16] | CUI Pinchen, UMPHRESS D. Perturbing Smart Contract Execution through the Underlying Runtime[C]// Springer. International Conference on Security and Privacy in Communication Systems. Heidelberg: Springer, 2020: 336-349. |
| [17] | Edgeless Systems GmbH. Build Confidential Go Apps with Ease[EB/OL]. (2021-10-06)[2021-12-20]. https://www.ego.dev. |
| [18] | WANG Juan, FAN Chengyang, CHENG Yueqiang, et al. Analysis and Research on SGX Technology[J]. Journal of Software, 2018, 29(9): 2778-2798. |
| 王鹃, 樊成阳, 程越强, 等. SGX 技术的分析和研究[J]. 软件学报, 2018, 29(9): 2778-2798. | |
| [19] | Intel Corporation. Introduction to Intel® SGX Sealing[EB/OL]. (2016-05-04)[2021-11-20]. https://www.intel.com/content/www/us/en/developer/articles/technical/introduction-to-intel-sgx-sealing.html. |
| [20] | Intel Corporation. Innovative Technology for CPU Based Attestation and Sealing[EB/OL]. (2013-08-14)[2021-11-20]. https://www.intel.com/content/www/us/en/developer/articles/technical/innovative-technology-for-cpu-based-attestation-and-sealing.html. |
| [21] | SSLab. SGX101 Attestation[EB/OL]. (2019-11-17)[2021-11-20]. https://sgx101.gitbook.io/sgx101/sgx-bootstrap/attestation. |
| [22] | ZHANG Rui, XUE Rui, LIU Ling. Security and Privacy on Blockchain[J]. ACM Computing Surveys (CSUR), 2019, 52(3): 1-34. |
| [23] | MEIKLEJOHN S, POMAROLE M, JORDAN G, et al. A Fistful of Bitcoins: Characterizing Payments among Men with No Names[C]// ACM. 2013 Conference on Internet Measurement Conference. New York: ACM, 2013: 127-140. |
| [24] |
MÖSER M, BÖHME R. The Price of Anonymity: Empirical Evidence from a Market for Bitcoin Anonymization[J]. Journal of Cybersecurity, 2017, 3(2): 127-135.
doi: 10.1093/cybsec/tyx007 URL |
| [25] | REID F, HARRIGAN M. An Analysis of Anonymity in the Bitcoin System[C]// Springer. Security and Privacy in Social Networks. Heidelberg: Springer, 2013: 197-223. |
| [26] | RON D, SHAMIR A. Quantitative Analysis of the Full Bitcoin Transaction Graph[C]// Springer. International Conference on Financial Cryptography and Data Security. Heidelberg: Springer, 2013: 6-24. |
| [27] | IBM. MSP Implementation with Identity Mixer[EB/OL]. (2017-11-23)[2021-11-21]. https://hyperledger-fabric.readthedocs.io/en/release-1.2/idemix.html. |
| [28] |
YUAN Rui, XIA Yubin, CHEN Haibo, et al. Shadoweth: Private Smart Contract on Public Blockchain[J]. Journal of Computer Science and Technology, 2018, 33(3): 542-556.
doi: 10.1007/s11390-018-1839-y URL |
| [29] | Docker. Base Image for Applications Using the Official Intel SGX SDK[EB/OL]. (2021-02-11)[2021-12-22]. https://registry.hub.docker.com/r/ffosilva/sgx. |
| [30] | Felix Schuster. EGo: Effortlessly Build Confidential Apps in Go[EB/OL]. (2021-02-21)[2021-12-22]. https://blog.edgeless.systems/ego-effortlessly-build-confidential-apps-in-go-dc2b1460e1bf. |
| [31] | IBM. Hyperledger Caliper Documentation[EB/OL]. (2021-04-16)[2021-12-15]. https://hyperledger.github.io/caliper/v0.4.2/getting-started/. |
| [32] | CAI Chengjun, XU Lei, ZHOU Anxin, et al. EncELC: Hardening and Enriching Ethereum Light Clients with Trusted Enclaves[C]// IEEE. IEEE INFOCOM 2020-IEEE Conference on Computer Communications. New York: IEEE, 2020: 1887-1896. |
| [33] | HEARN M, BROWN R G. Corda: A Distributed Ledger[J]. (2016-11-29)[2021-10-11]. https://www.corda.net/content/corda-technical-whitepaper.pdf. |
| [34] | ZHONG Yuhan. Design and Development of Trusted Computing Platform Based on Blockchain and TEE[D]. Hangzhou: Zhejiang University, 2021. |
| 钟雨涵. 基于区块链和TEE的可信计算平台设计与开发[D]. 杭州: 浙江大学, 2021. | |
| [35] |
ZHANG Xuewang, YIN Zijie, FENG Jiaqi, et al. Data Trading Scheme Based on Blockchain and Trusted Computing[J]. Journal of Computer Applications, 2021, 41(4): 939-944.
doi: 10.11772/j.issn.1001-9081.2020111723 |
|
张学旺, 殷梓杰, 冯家琦, 等. 基于区块链与可信计算的数据交易方案[J]. 计算机应用, 2021, 41(4):939-944.
doi: 10.11772/j.issn.1001-9081.2020111723 |
|
| [36] | LIU Qianren, XUE Miao, REN Mengxuan, et al. Application and Research of Blockchain in Data Sharing and Trusted Computing[J]. Designing Techniques of Posts and Telecommunications, 2020(11): 18-23. |
| 刘千仞, 薛淼, 任梦璇, 等. 基于区块链的数据共享与可信计算应用与研究[J]. 邮电设计技术, 2020(11): 18-23. |
| [1] | 王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. |
| [2] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [3] | 冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29. |
| [4] | 刘嘉微, 马兆丰, 王姝爽, 罗守山. 基于区块链的隐私信用数据受限共享技术研究[J]. 信息网络安全, 2022, 22(5): 54-63. |
| [5] | 崔皓宇, 马利民, 王佳慧, 张伟. 基于区块链的属性加密多授权机构安全模型研究[J]. 信息网络安全, 2022, 22(5): 84-93. |
| [6] | 石润华, 王树豪, 李坤昌. V2G中一种轻量级的跨域双向认证方案[J]. 信息网络安全, 2022, 23(3): 20-28. |
| [7] | 陈彬杰, 魏福山, 顾纯祥. 基于KNN的具有隐私保护功能的区块链异常交易检测[J]. 信息网络安全, 2022, 23(3): 78-84. |
| [8] | 王健, 张蕴嘉, 刘吉强, 陈志浩. 基于区块链的司法数据管理及电子证据存储机制[J]. 信息网络安全, 2022, 22(2): 21-31. |
| [9] | 刘峰, 杨成意, 於欣澄, 齐佳音. 面向去中心化双重差分隐私的谱图卷积神经网络[J]. 信息网络安全, 2022, 22(2): 39-46. |
| [10] | 侯雨桐, 马兆丰, 罗守山. 基于区块链的数据安全共享与受控分发技术研究与实现[J]. 信息网络安全, 2022, 22(2): 55-63. |
| [11] | 刘忻, 王家寅, 杨浩睿, 张瑞生. 一种基于区块链和secGear框架的车联网认证协议[J]. 信息网络安全, 2022, 22(1): 27-36. |
| [12] | 冯景瑜, 汪涛, 于婷婷, 张文波. 基于多云多链协同的医疗数据安全共享机制[J]. 信息网络安全, 2022, 22(1): 9-18. |
| [13] | 孙力. 区块链+在线教育资源联盟信息保护机制研究与应用[J]. 信息网络安全, 2021, 21(9): 32-39. |
| [14] | 陈凯杰, 熊焰, 黄文超, 武建双. 一种基于拜占庭容错的PoS共识协议形式化分析方法[J]. 信息网络安全, 2021, 21(8): 35-42. |
| [15] | 任涛, 金若辰, 罗咏梅. 融合区块链与联邦学习的网络入侵检测算法[J]. 信息网络安全, 2021, 21(7): 27-34. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||