信息网络安全 ›› 2022, Vol. 22 ›› Issue (7): 64-72.doi: 10.3969/j.issn.1671-1122.2022.07.008
一种基于字节波动特征的ROP流量静态检测方法
- 国防科技大学电子科学学院,长沙 410073
-
收稿日期:2022-03-30出版日期:2022-07-10发布日期:2022-08-17 -
通讯作者:王剑 E-mail:jwang@nudt.edu.cn -
作者简介:张梦杰(1995—),男,安徽,硕士研究生,主要研究方向为恶意流量检测|王剑(1975—),男,湖南,教授,博士,主要研究方向为网络空间安全、通信网络安全与对抗、漏洞攻击检测|黄恺杰(2000—),男,湖南,硕士研究生,主要研究方向为信息安全和恶意软件检测|杨刚(1993—),男,河北,博士研究生,主要研究方向为恶意软件分析和机器学习 -
基金资助:教育部-中国移动科研基金(2020)研发项目(MCM20200103)
A Static Detection Method of ROP Traffic Based on Bytes Fluctuation Characteristics
ZHANG Mengjie, WANG Jian( ), HUANG Kaijie, YANG Gang
), HUANG Kaijie, YANG Gang
- College of Electronic Science and Technology, National University of Defense Technology, Changsha 410073, China
-
Received:2022-03-30Online:2022-07-10Published:2022-08-17 -
Contact:WANG Jian E-mail:jwang@nudt.edu.cn
摘要:
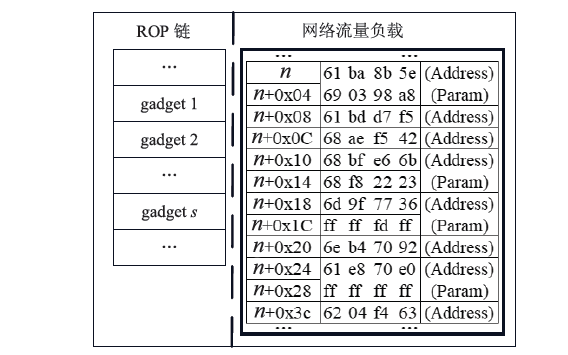
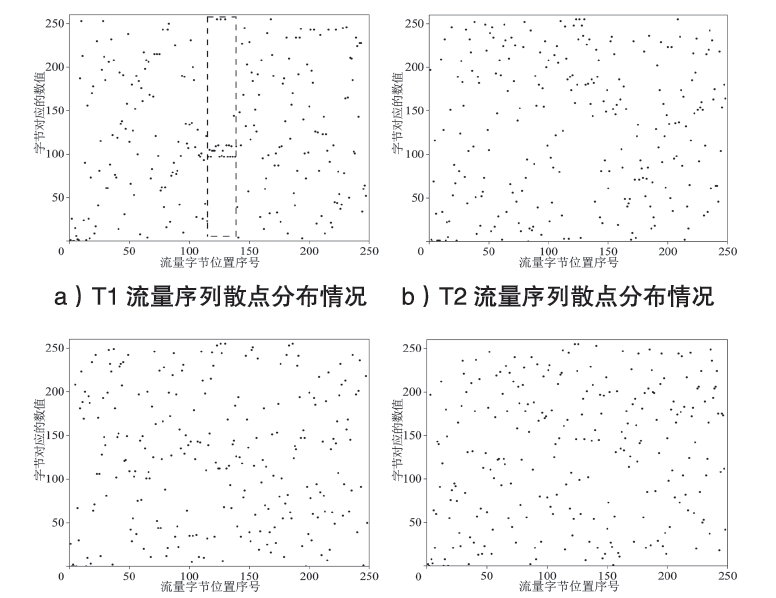
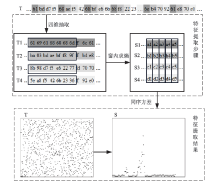
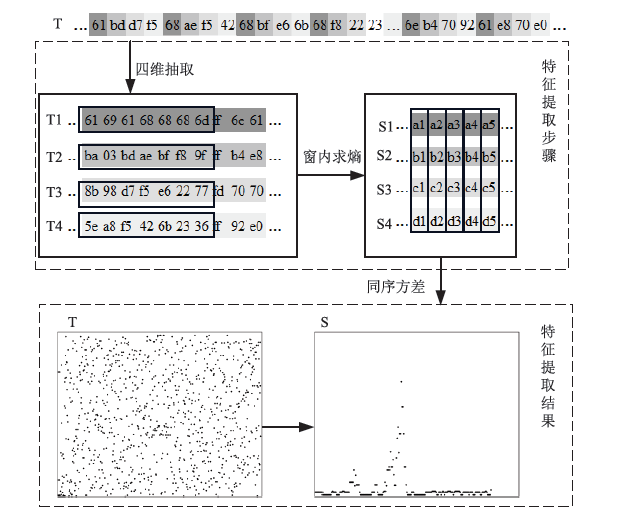
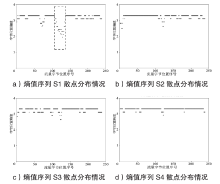
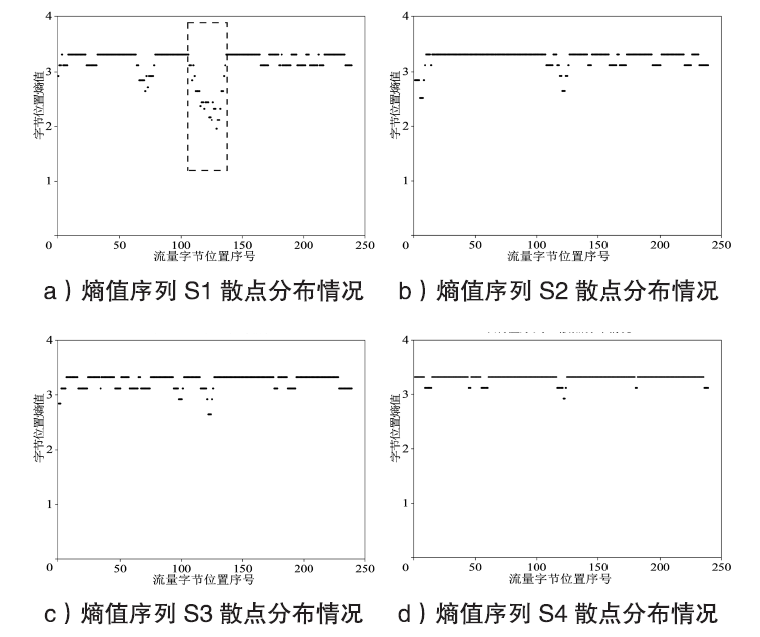
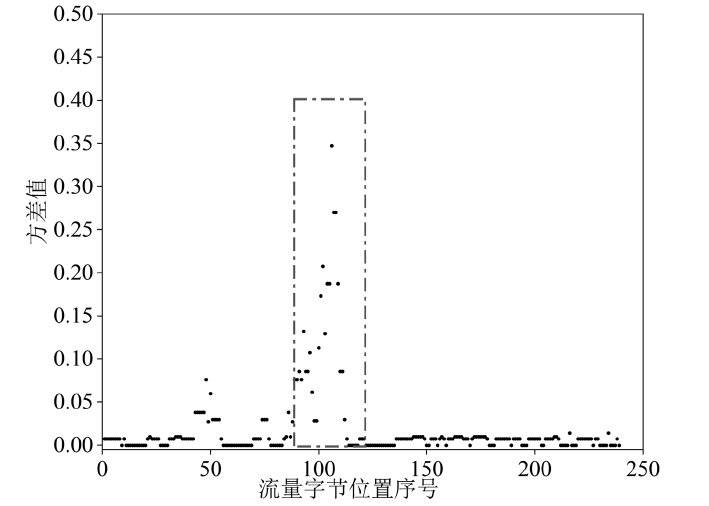
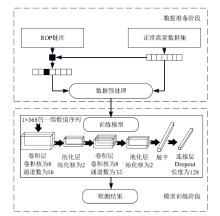
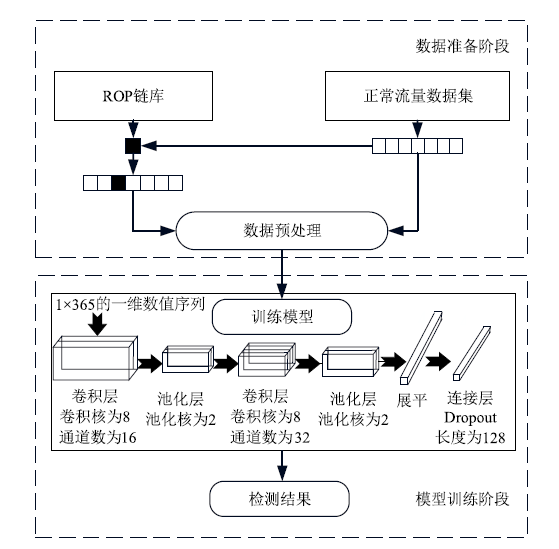
在现代计算机系统漏洞缓解机制的作用下,传统注入攻击方法无法实现攻击,面向返回编程(Return-Oriented Programming,ROP)技术成为漏洞攻击的关键,其利用多个代码片段(gadget)组成ROP链,从而实现任意操作执行。因此,网络流量中的ROP链检测对防御漏洞攻击具有重要作用。文章提出一种ROP流量静态检测方法,该方法结合信息熵和方差通过序列抽取方式完成对ROP链中字节波动特征的差异量化,并利用卷积神经网络(Convolutional Neural Network,CNN)捕捉特征,从而实现对网络流量中ROP链的静态检测。文章将真实ROP代码与正常流量进行随机混合,从而形成训练数据集,利用此数据集进行分类训练,模型的最高准确率可达99.6%,漏报率可控制在2%以下,误报率可控制在1%以下。实验结果表明,文章提出的方法实现了纯静态ROP流量检测,系统开销低,并且不依赖内存地址信息。
中图分类号:
引用本文
张梦杰, 王剑, 黄恺杰, 杨刚. 一种基于字节波动特征的ROP流量静态检测方法[J]. 信息网络安全, 2022, 22(7): 64-72.
ZHANG Mengjie, WANG Jian, HUANG Kaijie, YANG Gang. A Static Detection Method of ROP Traffic Based on Bytes Fluctuation Characteristics[J]. Netinfo Security, 2022, 22(7): 64-72.
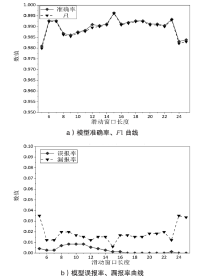
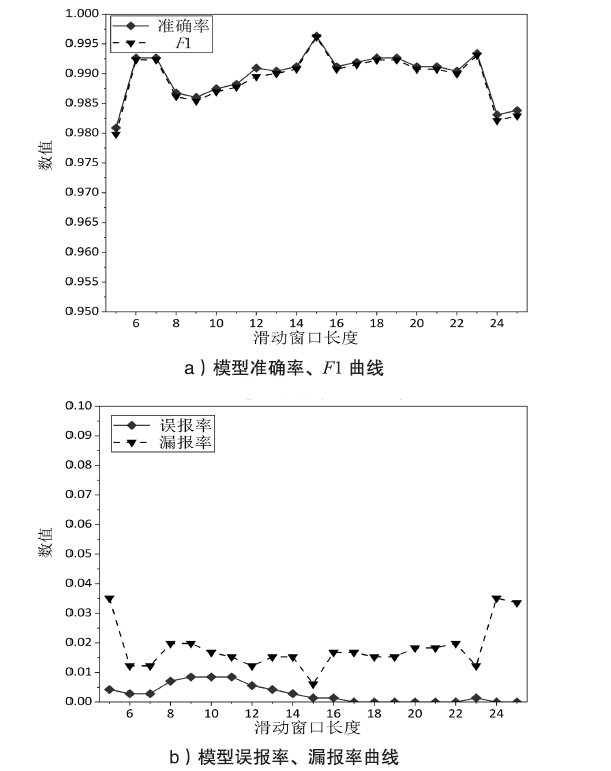
表2
不同滑动窗口长度的模型性能数据
| 长度 | 准确率 | 误报率 | 漏报率 | 查准率 | 查全率 | F1 |
|---|---|---|---|---|---|---|
| 5 | 0.9809 | 0.0042 | 0.0351 | 0.9953 | 0.9649 | 0.9798 |
| 6 | 0.9927 | 0.0028 | 0.0122 | 0.9969 | 0.9878 | 0.9923 |
| 7 | 0.9927 | 0.0028 | 0.0122 | 0.9969 | 0.9878 | 0.9923 |
| 8 | 0.9868 | 0.0071 | 0.0198 | 0.9923 | 0.9802 | 0.9862 |
| 9 | 0.9860 | 0.0085 | 0.0198 | 0.9907 | 0.9802 | 0.9854 |
| 10 | 0.9875 | 0.0085 | 0.0168 | 0.9908 | 0.9832 | 0.9870 |
| 11 | 0.9882 | 0.0085 | 0.0153 | 0.9908 | 0.9847 | 0.9877 |
| 12 | 0.9909 | 0.0056 | 0.0122 | 0.9913 | 0.9878 | 0.9895 |
| 13 | 0.9904 | 0.0042 | 0.0153 | 0.9954 | 0.9847 | 0.9900 |
| 14 | 0.9912 | 0.0028 | 0.0153 | 0.9969 | 0.9847 | 0.9908 |
| 15 | 0.9963 | 0.0014 | 0.0061 | 0.9985 | 0.9939 | 0.9962 |
| 16 | 0.9912 | 0.0014 | 0.0168 | 0.9984 | 0.9832 | 0.9908 |
| 17 | 0.9919 | 0.0000 | 0.0168 | 1.0000 | 0.9832 | 0.9915 |
| 18 | 0.9927 | 0.0000 | 0.0153 | 1.0000 | 0.9847 | 0.9923 |
| 19 | 0.9927 | 0.0000 | 0.0153 | 1.0000 | 0.9847 | 0.9923 |
| 20 | 0.9912 | 0.0000 | 0.0183 | 1.0000 | 0.9817 | 0.9908 |
| 21 | 0.9912 | 0.0000 | 0.0183 | 1.0000 | 0.9817 | 0.9908 |
| 22 | 0.9904 | 0.0000 | 0.0198 | 1.0000 | 0.9802 | 0.9900 |
| 23 | 0.9934 | 0.0014 | 0.0122 | 0.9985 | 0.9878 | 0.9931 |
| 24 | 0.9831 | 0.0000 | 0.0351 | 1.0000 | 0.9649 | 0.9821 |
| 25 | 0.9838 | 0.0000 | 0.0336 | 1.0000 | 0.9664 | 0.9829 |
| [1] | ANDERSEN S. Changes to Functionality in Microsoft Windows XP Service Pack 2: Part 3: Memory Protection Technologies[EB/OL]. (2004-11-04)[2021-12-22]. https://oriolrius.cat/article_fitxers/1901/winsock2.pdf. |
| [2] | BLETSCH T, JIANG Xuxian, FREEH V W, et al. Jump-Oriented Programming: A New Class of Code-Reuse Attack[C]// ACM. 6th ACM Symposium on Information, Computer and Communications Security. New York: ACM, 2011: 30-40. |
| [3] | CHECKOWAY S, DAVI L, DMITRIENKO A, et al. Return-Oriented Programming without Returns[C]// ACM. 17th ACM Conference on Computer and Communications Security. New York: ACM, 2010: 559-572. |
| [4] | ROEMER R, BUCHANAN E, SHACHAM H, et al. Return-Oriented Programming: Systems, Languages, and Applications[J]. ACM Transactions on Information and System Security (TISSEC), 2012, 15(1): 1-34. |
| [5] | SNOW K Z, MONROSE F, DAVI L, et al. Just-in-Time Code Reuse: on the Effectiveness of Fine-Grained Address Space Layout Randomization[C]// IEEE. 2013 IEEE Symposium on Security and Privacy. New York: IEEE, 2013: 574-588. |
| [6] | CHEN Ping, XIAO Hai, SHEN Xiaobin, et al. DROP: Detecting Return-Oriented Programming Malicious Code[C]// Springer. International Conference on Information Systems Security. Heidelberg: Springer, 2009: 163-177. |
| [7] | PAPPAS V, POLYCHRONAKIS M, KEROMYTIS A D. Transparent ROP Exploit Mitigation Using Indirect Branch Tracing[C]// USENIX. 22nd USENIX Security Symposium. Berkeley: USENIX, 2013: 447-462. |
| [8] | CHENG Yueqiang, ZHOU Zongwei, MIAO Yu, et al. ROPecker: A Generic and Practical Approach for Defending against ROP Attack[EB/OL]. (2014-02-23)[2021-11-26]. https://ink.library.smu.edu.sg/cgi/viewcontent.cgi?article=2972&context=sis_research. |
| [9] | ELSABAGH M, BARBARA D, FLECK D, et al. Detecting ROP with Statistical Learning of Program Characteristics[C]// ACM. 7th ACM on Conference on Data and Application Security and Privacy. New York: ACM, 2017: 219-226. |
| [10] | PFAFF D, HACK S, HAMMER C. Learning How to Prevent Return-Oriented Programming Efficiently[C]// Springer. International Symposium on Engineering Secure Software and Systems. Heidelberg: Springer, 2015: 68-85. |
| [11] | POLYCHRONAKIS M, KEROMYTIS A D. ROP Payload Detection Using Speculative Code Execution[C]// IEEE. 2011 6th International Conference on Malicious and Unwanted Software. New York: IEEE, 2011: 58-65. |
| [12] | USUI T, IKUSE T, OTSUKI Y, et al. ROPminer: Learning-Based Static Detection of ROP Chain Considering Linkability of ROP Gadgets[J]. IEICE Transactions on Information and Systems, 2020, 103(7): 1476-1492. |
| [13] | JÄMTHAGEN C, KARLSSON L, STANKOVSKI P, et al. EavesROP: Listening for ROP Payloads in Data Streams[C]// Springer. International Conference on Information Security. Heidelberg: Springer, 2014: 413-424. |
| [14] | TANAKA Y, GOTO A. N-ROPdetector: Proposal of a Method to Detect the ROP Attack Code on the Network[C]// ACM. 2014 Workshop on Cyber Security Analytics, Intelligence and Automation. New York: ACM, 2014: 33-36. |
| [15] | STANCILL B, SNOW K Z, OTTERNESS N, et al. Check My Profile: Leveraging Static Analysis for Fast and Accurate Detection of ROP Gadgets[C]// Springer. International Workshop on Recent Advances in Intrusion Detection. Heidelberg: Springer, 2013: 62-81. |
| [16] |
LI Xusheng, HU Zhisheng, WANG Haizhou, et al. DeepReturn: A Deep Neural Network Can Learn How to Detect Previously-Unseen ROP Payloads without Using Any Heuristics[J]. Journal of Computer Security, 2020, 28(5): 499-523.
doi: 10.3233/JCS-191368 URL |
| [17] | RONG Zelin, XIE Peidai, WANG Jingyuan, et al. Clean the Scratch Registers: A Way to Mitigate Return-Oriented Programming Attacks[C]// IEEE. 2018 IEEE 29th International Conference on Application-Specific Systems, Architectures and Processors (ASAP). New York: IEEE, 2018: 1-8. |
| [18] | WANG Wei, ZHU Ming, ZENG Xuewen, et al. Malware Traffic Classification Using Convolutional Neural Network for Representation Learning[C]// IEEE. 2017 International Conference on Information Networking (ICOIN). New York: IEEE, 2017: 712-717. |
| [1] | 张兴兰, 付娟娟. 基于辅助熵减的神经常微分方程入侵检测模型[J]. 信息网络安全, 2022, 22(6): 1-8. |
| [2] | 唐明, 黎聪, 李永波, 岳天羽. RISC-V架构上的时间侧信道静态检测研究[J]. 信息网络安全, 2022, 22(4): 7-19. |
| [3] | 林义钧, 吴渝, 李红波. 基于Affinity Propagation算法的半监督微博水军识别[J]. 信息网络安全, 2022, 23(3): 85-96. |
| [4] | 尹梦梦, 王磊, 姚昌华, 武欣嵘. 基于VIKOR模型的复杂网络节点重要度评估[J]. 信息网络安全, 2022, 22(1): 87-94. |
| [5] | 刘奕, 李建华, 张一瑫, 孟涛. 基于特征属性信息熵的网络异常流量检测方法[J]. 信息网络安全, 2021, 21(2): 78-86. |
| [6] | 谭杨, 刘嘉勇, 张磊. 基于混合特征的深度自编码器的恶意软件家族分类[J]. 信息网络安全, 2020, 20(12): 72-82. |
| [7] | 徐洋, 陈燚, 何锐, 谢晓尧. SDN中DDoS检测及多层防御方法研究[J]. 信息网络安全, 2017, 17(12): 22-28. |
| [8] | 蔡林, 陈铁明. Android移动恶意代码检测的研究概述与展望[J]. 信息网络安全, 2016, 16(9): 218-222. |
| [9] | 徐鑫, 张松年, 胡建伟. 基于任意函数地址的ASLR绕过技术研究[J]. 信息网络安全, 2016, 16(7): 47-52. |
| [10] | 尹心明, 胡正梁, 陈国梁, 黄海晔. 基于设备指纹决策树分类的IP视频专网入网检测方案研究[J]. 信息网络安全, 2016, 16(12): 68-73. |
| [11] | (中国人民银行济南分行, 山东济南250021). 基于G1法和熵值法的人民银行IT应急能力评估模型及验证研究[J]. 信息网络安全, 2015, 15(11): 84-89. |
| [12] | 沈长达, 尤俊生, 钱镜洁. TrueCrypt加密容器快速检测技术[J]. 信息网络安全, 2014, 14(9): 220-222. |
| [13] | . 基于信息熵的网络流量信息结构特征研究[J]. , 2014, 14(3): 28-. |
| [14] | 严承华;程晋;樊攀星. 基于信息熵的网络流量信息结构特征研究[J]. , 2014, 14(3): 0-0. |
| [15] | 王小鸥;李琳. 计算机网络中Markov信息熵的证明[J]. , 2012, 12(5): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||