信息网络安全 ›› 2022, Vol. 22 ›› Issue (7): 55-63.doi: 10.3969/j.issn.1671-1122.2022.07.007
云环境中数据安全威胁与防护关键技术研究
- 1.中国工业互联网研究院,北京 100854
2.中国科学院信息工程研究所,北京 100093
3.中国科学院大学,北京100049
-
收稿日期:2022-03-16出版日期:2022-07-10发布日期:2022-08-17 -
通讯作者:贾世杰 E-mail:jiashijie@iie.ac.cn -
作者简介:于成丽(1989—),女,黑龙江,工程师,硕士,主要研究方向为数据安全、密码应用安全|张阳(1995—),女,河北,博士研究生,主要研究方向为云存储安全、可信硬件应用|贾世杰(1989—),男,山东,副研究员,博士,主要研究方向为密码应用安全、数据存储安全 -
基金资助:国家自然科学基金(61802395)
Research on Data Security Threats and Protection of Key Technologies in Cloud Environment
YU Chengli1, ZHANG Yang2,3, JIA Shijie2,3( )
)
- 1. China Academy or Industrial Internet, Beijing 100854, China
2. Institute of Information Engineering, University of Chinese Academy of Sciences, Beijing 100093, China
3. University of Chinese Academy of Sciences, Beijing 100049 China
-
Received:2022-03-16Online:2022-07-10Published:2022-08-17 -
Contact:JIA Shijie E-mail:jiashijie@iie.ac.cn
摘要:
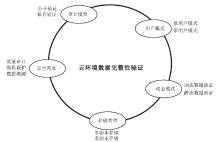
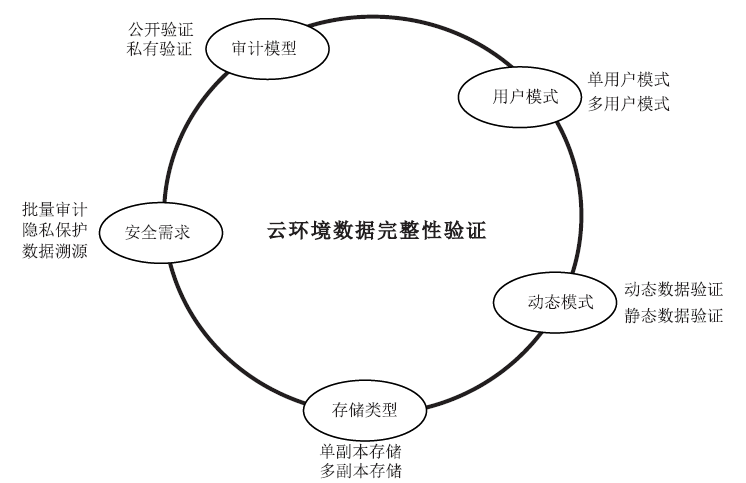
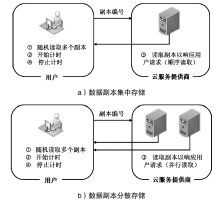
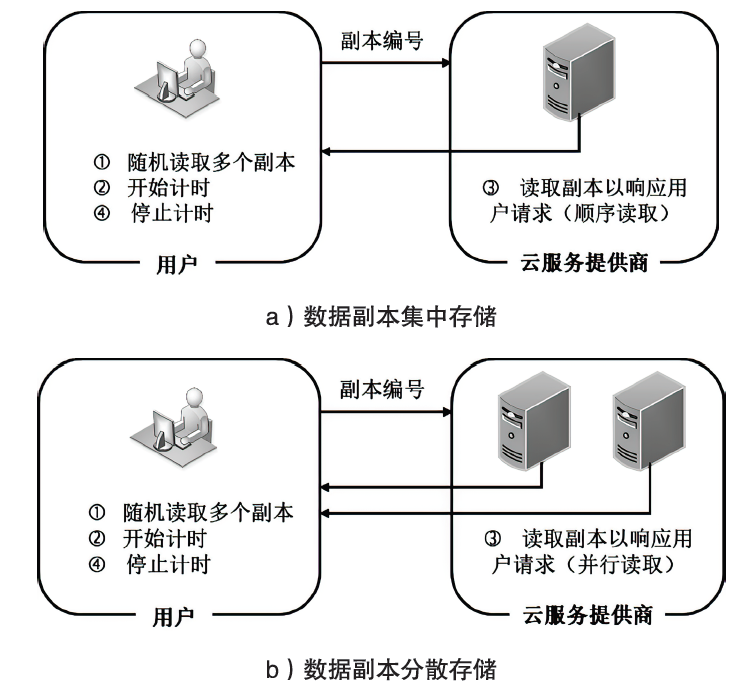
随着云计算技术的不断发展,云逐渐成为数据存储的主要方式之一。云拥有海量的存储空间,能够为用户提供数据存储和数据管理等服务,用户可以不受设备、地点等因素的限制,随时随地通过互联网访问云端数据。然而,当数据存储到云端后,用户便失去了对数据的物理控制权,数据安全成为制约云计算市场发展的关键。文章从云环境中数据所面临的安全威胁切入,分析数据安全需求,总结现有数据安全防护的关键技术,并探讨云环境中数据安全保护面临的主要挑战和未来研究趋势,推动云数据保护体系的完善和发展。
中图分类号:
引用本文
于成丽, 张阳, 贾世杰. 云环境中数据安全威胁与防护关键技术研究[J]. 信息网络安全, 2022, 22(7): 55-63.
YU Chengli, ZHANG Yang, JIA Shijie. Research on Data Security Threats and Protection of Key Technologies in Cloud Environment[J]. Netinfo Security, 2022, 22(7): 55-63.
表2
机密性证明方案对比
| 属性 | 基于RSA 编码[ | 基于 排列 编码[ | 基于 蝶形 编码[ | HU[ | FANG[ | 尤玮婧[ | |
|---|---|---|---|---|---|---|---|
| 用户端计算 开销 | 加密 | O(tm) | O(tm) | O(tm) | O(nm) | O(tm) | — |
| 数据 封装 | O(nm) RSA | O(nm) memory access | O(nmlogm) AES | O(n)C+ O(nm) memory access | O(n)C+ O(tm) memory access | — | |
| 生成 标签 | O(n)hash | O(n)hash | O(n)hash | O(nm)AES | O(n)hash+ O(n)AES | — | |
| 云端 计算 开销 | 加密 | O(nm) | O(nm) | O(nm) | — | O(nm) | O(nm) |
| 数据 封装 | — | O(nm) memory access | O(nmlogm) AES | — | O(n)C+ O(nm) memory access | — | |
| 生成 标签 | — | — | — | — | O(n)hash | O(n)hash+ O(nm) memory access | |
| 远程证明 计算开销 | — | — | — | — | — | Cr | |
| 磁盘介质 | — | 转动硬盘 驱动器 | — | — | — | — | |
| 硬件要求 | — | — | — | — | — | Intel SGX | |
| [1] | MELL P, GRANCE T, et al. The NIST Definition of Cloud Computing, Special Publication (NIST SP)[M]. Gaithersburg: NIST, 2011. |
| [2] | LI Bohu, LI Bing. Introduction to Cloud Computing[M]. Beijing: China Machine Press, 2018. |
| 李伯虎, 李兵. 云计算导论[M]. 北京: 机械工业出版社, 2018. | |
| [3] | DIJK M V, JUELS A, OPREA A, et al. Hourglass Schemes: How to Prove that Cloud Files are Encrypted[C]// ACM. the 2012 ACM Conference on Computer and Communications Security. New York: ACM, 2012: 265-280. |
| [4] | HU Keji, ZHANG Wensheng. Efficient Verification of Data Encryption on Cloud Servers[C]// IEEE. 2014 Twelfth Annual International Conference on Privacy, Security and Trust. New York: IEEE, 2014: 314-321. |
| [5] | FANG Jinxia, LIU Limin, LIN Jingqiang. Practical Verification of Data Encryption for Cloud Storage Services[M]. Berlin: Springer, 2019. |
| [6] | YOU Weijing, LIU Limin, MA Yue, et al. An Intel SGX-Based Proof of Encryption in Clouds[J]. Netinfo Security, 2020, 20(12): 1-8. |
| 尤玮婧, 刘丽敏, 马悦, 等. 基于安全硬件的云端数据机密性验证方案[J]. 信息网络安全, 2020, 20(12): 1-8. | |
| [7] | ATENIESE G, BURNS R, CURTMOLA R, et al. Provable Data Possession at Untrusted Stores[C]// ACM. Proceedings of ACM CCS 2007. New York: ACM, 2007: 598-609. |
| [8] | JUELS A and KALISKI B S. PORs: Proofs of Retrievability for Large Files[C]// ACM. Proceedings of the 14th ACM conference on Computer and communications security. New York: ACM, 2007: 584-597. |
| [9] | SHACHAM H and WATER B. Compact Proofs of Retrievability[C]// Spring. Proceedings of 14th International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg: Springer, 2008: 90-107. |
| [10] | ATENIESE G, PIETRO, MANCINI L, et al. Scalable and Efficient Provable Data Possession[C]// ACM. 4th International ICST Conference on Security and Privacy in Communication Networks. New York: ACM, 2008: 1-10. |
| [11] | ERWAY C, KÜPÇÜ A, PAPAMANTHOU C, et al. Dynamic Provable Data Possession[C]// ACM. Proceedings of the 16th ACM Conference on Computer and Communications Security. New York: ACM, 2009: 213-222. |
| [12] |
WANG Qian, WANG Cong, REN Kui, et al. Enabling Public Auditability and Data Dynamics for Storage Security in Cloud Computing[J]. IEEE Transactions on Parallel and Distributed Systems, 2011, 22(5): 847-859.
doi: 10.1109/TPDS.2010.183 URL |
| [13] |
ZHU Yan, WANG Huai, HU Zexing, et al. Dynamic Audit Services for Outsourced Storage in Clouds[J]. IEEE Transactions on Services Computing, 2013, 6(2), 227-238.
doi: 10.1109/TSC.2011.51 URL |
| [14] |
TIAN Hui, CHEN Yuxiang, CHANG ChinChen, et al. Dynamic-Hash-Table Based Public Auditing for Secure Cloud Storage[J]. IEEE Transactions on Services Computing, 2017, 10(5): 701-714.
doi: 10.1109/TSC.2015.2512589 URL |
| [15] | WANG Cong, WANG Qian, REN Kui, et al. Ensuring Data Storage Security in Cloud Computing[C]// IEEE. Proceedings of 17th International Workshop on Quality of Service (IWQOS). New York:IEEE, 2009: 1-9. |
| [16] | CHEN Bo, CURTMOLA R. Robust Dynamic Remote Data Checking for Public Clouds[C]// ACM. Proceedings of the 2012 ACM Conference on Computer and Communications Security (CCS 2012). New York: ACM, 2012: 1043-1045. |
| [17] | CASH D, KÜPCÜ A, WICHS D. Dynamic Proofs of Retrievability via Oblivious RAM[C]// Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2013: 279-295. |
| [18] | ANTHOINE G, DUMAS J, JONGHE M, et al. Dynamic Proofs of Retrievability with Low Server Storage[C]// USENIX. 30th USENIX Security Symposium, USENIX Security 2021. Berkeley: USENIX, 2021: 537-554. |
| [19] | WANG Boyang, LI Baochun, LI Hui. Oruta: Privacy-Preserving Public Auditing for Shared Data in the Cloud[C]// IEEE. Proceedings of the 5th IEEE International Conference on Cloud Computing. New York: IEEE, 2012: 295-302. |
| [20] | WANG Boyang, LI Baochun, LI Hui. Knox: Privacy-Preserving Auditing for Shared Data with Large Groups in the Cloud[J]. Applied Cryptography and Network Security, 2012, 7341: 507-525. |
| [21] | ATENIESE G, BURNS R C, CURTMOLA R, et al. Provable Data Possession at Untrusted Stores[C]// ACM. Proceedings of the 2007 ACM Conference on Computer and Communications Security(CCS 2007). New York: ACM, 2007: 598-609. |
| [22] | CURTMOLA R, KHAN O, BURNS R C, et al. MR-PDP: Multiple-Replica Provable Data Possession[C]// IEEE. 28th IEEE International Conference on Distributed Computing Systems (ICDCS 2008). New York: IEEE, 2008: 411-420. |
| [23] | LI Limin, YANG Yahui, WU Zhonghai. FMR-PDP: Flexible Multiple-Replica Provable Data Possession in Cloud Storage[C]// IEEE. 2017 IEEE Symposium on Computers and Communications (ISCC 2017). New York: IEEE, 2017: 1115-1121. |
| [24] |
YI Mingxu, WEI Jinxia, SONG Lingwei. Efficient Integrity Verification of Replicated Data in Cloud Computing System[J]. Computers and Security, 2017, 65(3): 202-212.
doi: 10.1016/j.cose.2016.11.003 URL |
| [25] | ARMKNECHT F, BARMAN L, BOHLI J, et al. Mirror: Enabling Proofs of Data Replication and Retrievability in the Cloud[C]// USENIX. 25th USENIX Security Symposium, USENIX Security 16. Berkeley: USENIX, 2016: 1051-1068. |
| [26] | BOWERS K D, VAN DIJK M, JUELS A, et al. How to Tell if Your Cloud Files are Vulnerable to Drive Crashes[C]// ACM. Proceedings of the 18th ACM Conference on Computer and Communications Security (CCS 2011). New York: ACM, 2011: 501-514. |
| [27] | WANG Z, SUN K, JAJODIA S, et al. Disk Storage Isolation and Verification in Cloud[C]// IEEE. 2012 IEEE Global Communications Conference (GLOBECOM 2012). New York: IEEE, 2012: 771-776. |
| [28] | YOU Weijing. Research on Data Security Attribute Verification in Cloud Storage Environment[D]. Beijing: University of Chinese Academy of Sciences, 2021. |
| 尤玮婧. 云存储环境下的数据安全属性验证研究[D]. 北京: 中国科学院大学, 2021. | |
| [29] | Protocol Labs. Filecoin: A Decentralized Storage Network[EB/OL]. (2017-07-12)[2022-03-11]. https://filecoin.io/filecoin.pdf. |
| [30] | Protocol Labs. Proof of Replication[EB/OL]. (2017-07-27)[2022-03-11]. https://filecoin.io/proof-of-replication.pdf. |
| [31] | DAMGARD I, GANESH C, ORLANDI C. Proofs of Replicated Storage without Timing Assumptions[C]// Springer. Advances in Cryptology- CRYPTO 2019:39th Annual International Cryptology Conference. Berlin: Springer, 2019: 355-380. |
| [32] | PERLMAN R. File System Design with Assured Delete[C]// IEEE. 3rd International IEEE Security in Storage Workshop (SISW’05). New York: IEEE, 2005: 76-88. |
| [33] | GEAMBASU R, KOHNO T, LEVY A A. et al. Vanish: Increasing Data Privacy with Self-Destructing Data[C]// USENIX. In USENIX Security Symposium. Berkeley: USENIX, 2009: 299-315. |
| [34] | XIONG Jinbo, LIU Ximeng, YAO Zhiqiang, et al. A Secure Data Self-Destructing Scheme in Cloud Computing[J]. IEEE Transactions on Cloud Computing, 2014, 2(4): 448-458. |
| [35] |
TANG Yang, LEE P P, LUI J C, et al. Secure Overlay Cloud Storage with Access Control and Assured Deletion[J]. IEEE Transactions on Dependable and Secure Computing, 2012, 9(6): 903-916.
doi: 10.1109/TDSC.2012.49 URL |
| [36] |
YU Yong, XUE Liang, LI Yannan, et al. Assured Data Deletion with Fine-Grained Access Control for Fog-Based Industrial Applications[J]. IEEE Transactions on Industrial Informatics, 2018, 14 (10): 4538-4547.
doi: 10.1109/TII.2018.2841047 URL |
| [37] |
XUE Liang, YU Yong, LI Yannan, et al. Efficient Attribute-Based Encryption with Attribute Revocation for Assured Data Deletion[J]. Information Sciences, 2019, 479: 640-650.
doi: 10.1016/j.ins.2018.02.015 |
| [38] | GREEN M D, MIERS I. Forward Secure Asynchronous Messaging from Puncturable Encryption[C]// IEEE. In 2015 IEEE Symposium on Security and Privacy. New York: IEEE, 2015: 305-320. |
| [39] |
TIAN Junfeng, WANG Ziwei. Cloud Data Assured Deletion Scheme Based on Dynamic Sliding Window[J]. Peer to Peer Networking and Applications, 2022, 15: 1817-1833.
doi: 10.1007/s12083-022-01318-3 URL |
| [1] | 游文婷, 张乐友, 叶亚迪, 李晖. 多用户通信机制中支持隐私保护的属性基动态广播加密[J]. 信息网络安全, 2021, 21(4): 21-30. |
| [2] | 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. |
| [3] | 边曼琳, 王利明. 云环境下Docker容器隔离脆弱性分析与研究[J]. 信息网络安全, 2020, 20(7): 85-95. |
| [4] | 刘渊, 乔巍. 云环境下基于Kubernetes集群系统的容器网络研究与优化[J]. 信息网络安全, 2020, 20(3): 36-44. |
| [5] | 白嘉萌, 寇英帅, 刘泽艺, 查达仁. 云计算平台基于角色的权限管理系统设计与实现[J]. 信息网络安全, 2020, 20(1): 75-82. |
| [6] | 任良钦, 王伟, 王琼霄, 鲁琳俪. 一种新型云密码计算平台架构及实现[J]. 信息网络安全, 2019, 19(9): 91-95. |
| [7] | 余奕, 吕良双, 李肖坚, 王天博. 面向移动云计算场景的动态网络拓扑描述语言[J]. 信息网络安全, 2019, 19(9): 120-124. |
| [8] | 王紫璇, 吕良双, 李肖坚, 王天博. 基于共享存储的OpenStack虚拟机应用分发策略[J]. 信息网络安全, 2019, 19(9): 125-129. |
| [9] | 崔艳鹏, 冯璐铭, 闫峥, 蔺华庆. 基于程序切片技术的云计算软件安全模型研究[J]. 信息网络安全, 2019, 19(7): 31-41. |
| [10] | 葛新瑞, 崔巍, 郝蓉, 于佳. 加密云数据上支持可验证的关键词排序搜索方案[J]. 信息网络安全, 2019, 19(7): 82-89. |
| [11] | 田春岐, 李静, 王伟, 张礼庆. 一种基于机器学习的Spark容器集群性能提升方法[J]. 信息网络安全, 2019, 19(4): 11-19. |
| [12] | 赵谱, 崔巍, 郝蓉, 于佳. 一种针对El-Gamal数字签名生成的安全外包计算方案[J]. 信息网络安全, 2019, 19(3): 81-86. |
| [13] | 张振峰, 张志文, 王睿超. 网络安全等级保护2.0云计算安全合规能力模型[J]. 信息网络安全, 2019, 19(11): 1-7. |
| [14] | 冯新扬, 沈建京. 一种基于Yarn云计算平台与NMF的大数据聚类算法[J]. 信息网络安全, 2018, 18(8): 43-49. |
| [15] | 陶源, 黄涛, 张墨涵, 黎水林. 网络安全态势感知关键技术研究及发展趋势分析[J]. 信息网络安全, 2018, 18(8): 79-85. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||