信息网络安全 ›› 2025, Vol. 25 ›› Issue (11): 1792-1810.doi: 10.3969/j.issn.1671-1122.2025.11.011
基于机密计算平台的TEE和TPM硬件可信信道构建方案
金娃1,2, 秦宇1( ), 刘菁润2, 尚科彤1, 贾梦涵1,2, 林江南1
), 刘菁润2, 尚科彤1, 贾梦涵1,2, 林江南1
1.中国科学院软件研究所可信计算与信息保障实验室 北京 100190 2.中国科学院大学 北京 100049
-
收稿日期:2025-07-08出版日期:2025-11-10发布日期:2025-12-02 -
通讯作者:秦宇qinyu@iscas.ac.cn -
作者简介:金娃(2001—),女,内蒙古,硕士研究生,主要研究方向为可信计算、机密计算|秦宇(1979—),男,重庆,正高级工程师,博士,主要研究方向为可信计算、机密计算|刘菁润(2000—),男,河南,硕士研究生,主要研究方向为可信计算、机密计算|尚科彤(1997—),女,内蒙古,助理工程师,硕士,主要研究方向为可信计算、机密计算|贾梦涵(2002—),女,山东,硕士研究生,主要研究方向为可信计算、机密计算|林江南(1996—),男,福建,助理工程师,硕士,主要研究方向为可信计算、机密计算 -
基金资助:国家重点研发计划(2024YFE0211100)
A Hardware Trusted Channel Construction Scheme Based on TEE and TPM for Confidential Computing Platforms
JIN Wa1,2, QIN Yu1( ), LIU Jingrun2, SHANG Ketong1, JIA Menghan1,2, LIN Jiangnan1
), LIU Jingrun2, SHANG Ketong1, JIA Menghan1,2, LIN Jiangnan1
1. Trusted Computing and Information Assurance Laboratory ,Institute of Software Chinese Academy of Sciences Beijing 100190, China 2. University of Chinese Academy of Sciences Beijing 100049, China
-
Received:2025-07-08Online:2025-11-10Published:2025-12-02
摘要:
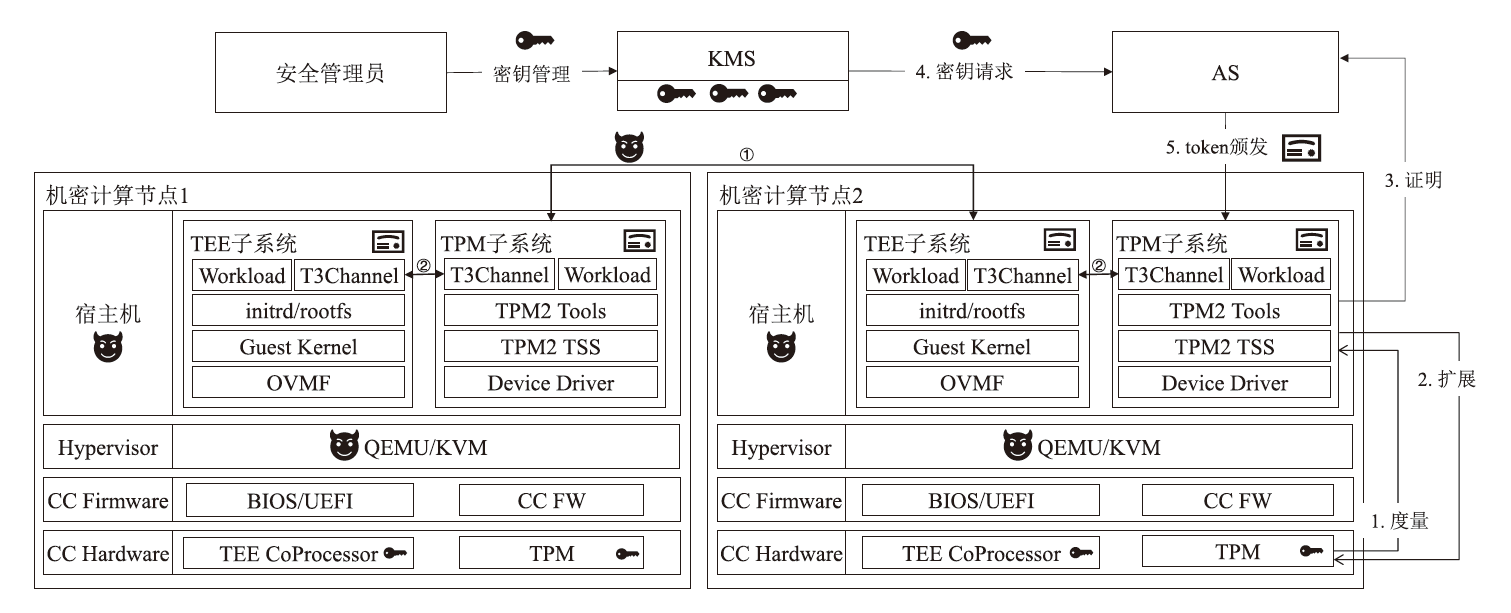
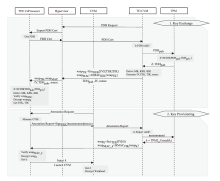
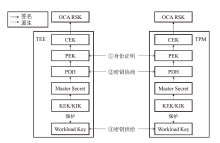
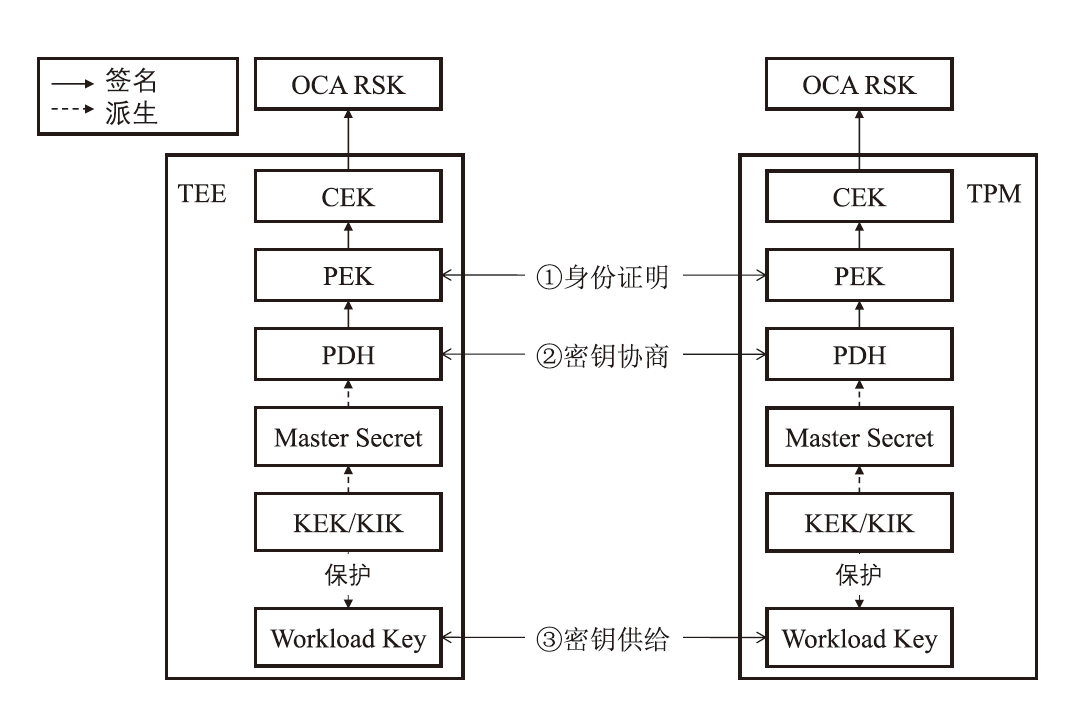
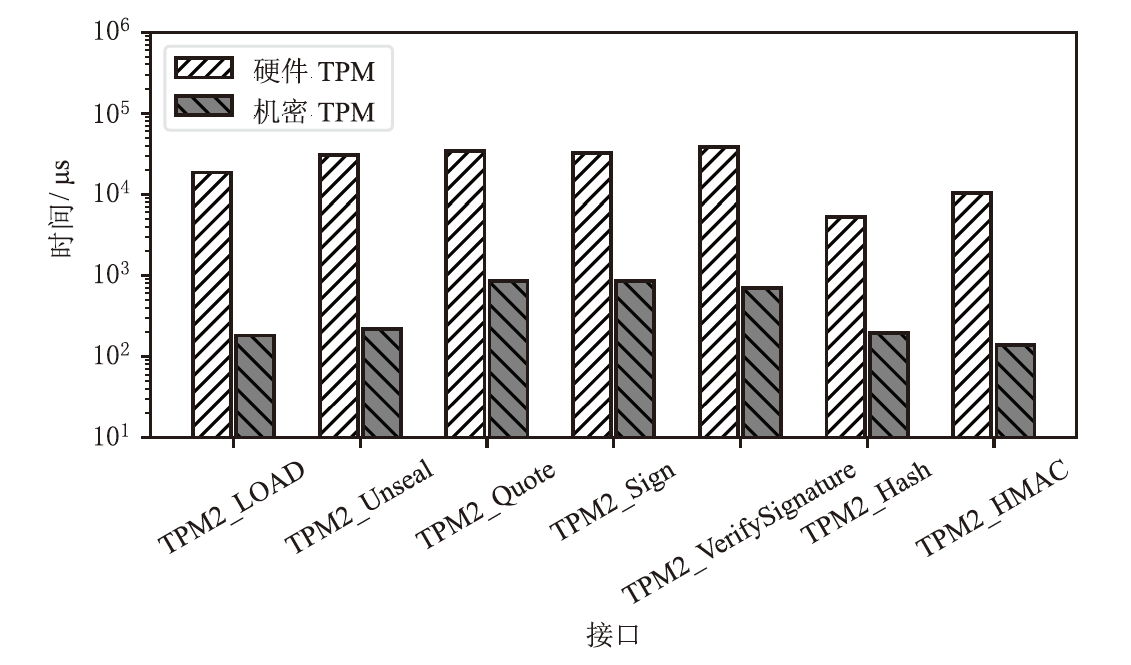
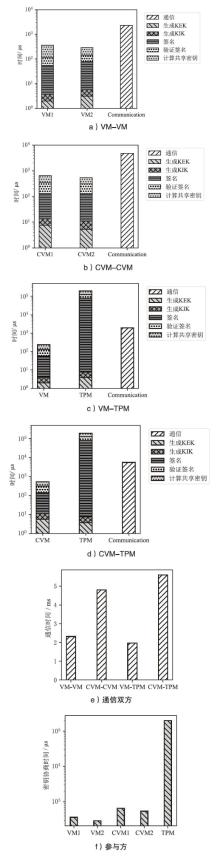
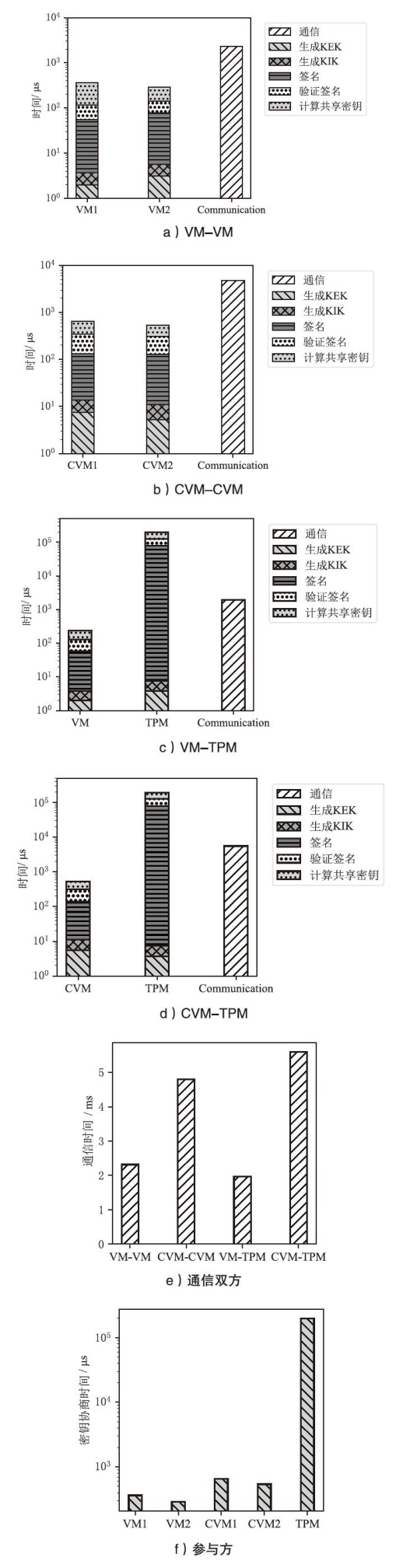
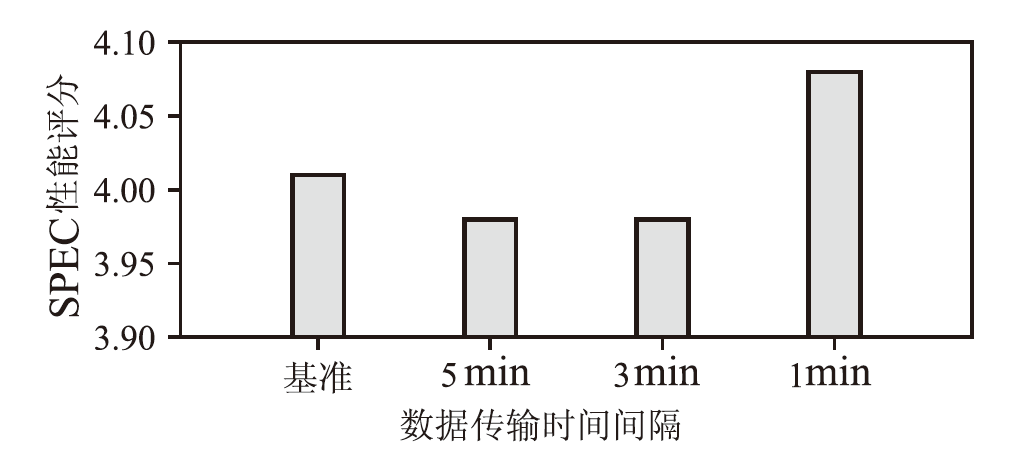
近年来,机密计算在保护用户隐私和数据安全方面发挥着越来越重要的作用。随着基于海量AI数据的机密计算平台应用需求增加,机密计算平台的可信信道构建和机密互联成为热点研究方向之一。针对机密计算平台的证明、数据可信传输和存储的安全需求,文章提出一种基于硬件密钥协商机制的可信执行环境(TEE)和可信平台模块(TPM)硬件的可信信道构建方案。该方案主要由3个安全通信协议构成。在子系统相互证明协议中,使用可信第三方为可信计算平台节点的子系统颁发可验证的证明令牌,实现基于多异构硬件信任根场景的统一证明。在硬件TEE和TPM密钥协商协议中,协商过程兼容于现有TEE技术规范和TPM密钥协商接口,并派生密钥保护传输中的机密数据。相较于应用软件通信,基于设备硬件建立的可信通信信道具备更高的安全性。在TEE密钥/秘密数据供给协议中,TPM将密钥/秘密数据通过可信信道供给TEE安全应用,提升TEE中数据存储保护的安全性。由安全性分析评估可得,文章方案能够有效防御攻击者对系统的伪造、欺骗、篡改等攻击。实现的原型系统实验评估结果表明,相较于传统虚拟机,TEE和TPM硬件密钥协商延时仅增加2%,基于文章方案密钥协商和持续传输数据的TEE运行时系统总体性能损失小于0.7%。综上所述,文章方案在提升机密计算平台通信安全性的同时,对系统运行和通信性能影响较小,具备良好的实用性与可扩展性。
中图分类号:
引用本文
金娃, 秦宇, 刘菁润, 尚科彤, 贾梦涵, 林江南. 基于机密计算平台的TEE和TPM硬件可信信道构建方案[J]. 信息网络安全, 2025, 25(11): 1792-1810.
JIN Wa, QIN Yu, LIU Jingrun, SHANG Ketong, JIA Menghan, LIN Jiangnan. A Hardware Trusted Channel Construction Scheme Based on TEE and TPM for Confidential Computing Platforms[J]. Netinfo Security, 2025, 25(11): 1792-1810.
表1
符号说明
| 符号 | 描述 |
|---|---|
| 非对称密钥对,其中,sk为私钥,pk为公钥 | |
| KDF(Z, info) | 密钥派生函数,用于在ECDH密钥协商中基于共享秘密值Z和信息info派生对称密钥 |
| token | AS颁发给可信设备的可验证凭据 |
| D=(q, FR,a,b,{SEED},G, n,h) | 生成EC密钥对使用的域参数 |
| 使用密钥k对消息m加密 | |
| 使用密钥k计算消息m的HMAC值 | |
| 使用密钥k对消息m签名 | |
| x||y | x和y的串联 |
| x·y | 整数x与整数y相乘 |
| [n]P | 整数n与点P相乘 |
| [1] |
FENG Dengguo, QIN Yu, FENG Wei, et al. Survey of Research on Confidential Computing[J]. IET Communications, 2024, 18(9): 535-556.
doi: 10.1049/cmu2.v18.9 URL |
| [2] | FENG Dengguo, QIN Yu. Confidential Computing: Progress and Prospects[J]. Communications of China Computer Federation, 2024, 20(12): 38-46. |
| 冯登国, 秦宇. 机密计算:进展与展望[J]. 中国计算机学会通讯, 2024, 20(12):38-46. | |
| [3] | Confidential Computing Consortium. A Technical Analysis of Confidential Computing[R]. San Francisco:Linux Foundation, v1.2, 2021. |
| [4] | TPM 2.0 Library Specification Revision 1.59 Part 1: Architecture[S]. Beaverton: Trusted Computing Group, 2019. |
| [5] | NVIDIA. Introduction to DGX A100[EB/OL]. (2024-10-16)[2025-07-04]. https://docs.nvidia.com/dgx/dgxa100-user-guide/introduction-to-dgxa100.html. |
| [6] | BERGER S, CACERES R, GOLDMAN K A, et al. vTPM: Virtualizing the Trusted Platform Module[C]// USENIX. The 15th USENIX Security Symposium. Berkeley: USENIX, 2006: 305-320. |
| [7] | Inclavare Containers. RATS-TLS Project[EB/OL]. (2025-04-21)[2025-07-07]. https://github.com/inclavare-containers/rats-tls. |
| [8] | HALDERMAN J A, SCHOEN S D, HENINGER N, et al. Lest We Remember: Cold Boot Attacks on Encryption Keys[C]// USENIX. 17th USENIX Security Symposium. Berkeley: USENIX, 2008: 68-78. |
| [9] | CHEN Weijie. Research on Side-Channel Defenses for Trusted Execution Environment Based on Real-Time Monitoring[D]. Wuhan: Huazhong University of Science and Technology, 2024. |
| 陈维杰. 基于实时监测的可信执行环境侧信道防御研究[D]. 武汉: 华中科技大学, 2024. | |
| [10] | FU Jianming, LIU Xiuwen, TANG Yi, et al. Survey of Memory Address Leakage and Its Defense[J]. Journal of Computer Research and Development, 2016, 53(8): 1829-1849. |
| 傅建明, 刘秀文, 汤毅, 等. 内存地址泄漏分析与防御[J]. 计算机研究与发展, 2016, 53(8):1829-1849. | |
| [11] | RFC 9334 Remote Attestation Procedures Architecture[S]. Internet Engineering Task Force (IETF), 2023. |
| [12] | Veraison Project. Veraison[EB/OL]. (2025-07-04)[2025-07-07]. https://github.com/veraison. |
| [13] | Intel. Intel® Enhanced Privacy ID (EPID) Security Technology[EB/OL]. (2021-07-13)[2025-07-04]. https://www.intel.com/content/www/us/en/developer/articles/technical/intel-enhanced-privacy-id-epid-security-technology.html. |
| [14] | Intel. Intel Software Guard Extensions Data Center Attestation Primitives Quick Install Guide[EB/OL]. (2024-05-13)[2025-07-04]. https://www.intel.com/content/www/us/en/developer/articles/guide/intel-software-guard-extensions-data-center-attestation-primitives-quick-install-guide.html. |
| [15] | CHEN Guoxing, ZHANG Yinqian, LAI T H. Opera: Open Remote Attestation for Intel’s Secure Enclaves[C]// ACM. The 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 2317-2331. |
| [16] | CHEN Guoxing, ZHANG Yinqian. MAGE: Mutual Attestation for a Group of Enclaves without Trusted Third Parties[C]// USENIX. The 31st USENIX Security Symposium. Berkeley: USENIX, 2022: 4095-4110. |
| [17] | DHAR A, PUDDU I, KOSTIAINEN K, et al. ProximiTEE: Hardened SGX Attestation by Proximity Verification[C]// ACM. The 10th ACM Conference on Data and Application Security and Privacy. New York: ACM, 2020: 5-16. |
| [18] |
WANG Juan, HONG Zhi, ZHANG Yuhan, et al. Enabling Security-Enhanced Attestation with Intel SGX for Remote Terminal and IoT[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2017, 37(1): 88-96.
doi: 10.1109/TCAD.2017.2750067 URL |
| [19] | ZHOU Lei, ZHANG Fengwei, WANG Guojun. Using Asynchronous Collaborative Attestation to Build a Trusted Computing Environment for Mobile Applications[C]// IEEE. The 2017 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI). New York: IEEE, 2017: 1-6. |
| [20] | KUCAB M, BORYLO P, CHOLDA P. Remote Attestation and Integrity Measurements with Intel SGX for Virtual Machines[EB/OL]. (2021-07-01)[2025-07-04]. https://doi.org/10.1016/j.cose.2021.102300. |
| [21] | WALSH K, MANFERDELLI J. Mechanisms for Mutual Attested Microservice Communication[C]// ACM. Proceedings of the 10th International Conference on Utility and Cloud Computing (UCC’17 Companion). New York: ACM, 2017: 59-64. |
| [22] | HAMIDY G M, YULIANTI S, PHILIPPAERTS P, et al. TC4SE: A High-Performance Trusted Channel Mechanism for Secure Enclave-Based Trusted Execution Environments[C]// Springer. Information Security, ISC 2023. Heidelberg: Springer, 2023: 225-244. |
| [23] | KNAUTH T, STEINER M, CHAKRABARTI S, et al. Integrating Remote Attestation with Transport Layer Security[EB/OL]. (2019-07-26)[2025-07-04]. https://doi.org/10.48550/arXiv.1801.05863. |
| [24] | WALTHER R, WEINHOLD C, ROITZSCH M. RATLS: Integrating Transport Layer Security with Remote Attestation[C]// Springer. Applied Cryptography and Network Security Workshops(ACNS 2022). Heidelberg: Springer, 2022: 319-338. |
| [25] | NIEMI A, POP V A B, EKBERG J. Trusted Sockets Layer: A TLS 1.3 Based Trusted Channel Protocol[C]// Springer. Secure IT Systems:26th Nordic Conference(NordSec 2021). Heidelberg: Springer, 2021: 175-191. |
| [26] | KING G, WANG H. HTTPA: HTTPS Attestable Protocol[C]// Springer. The 2023 Future of Information and Communication Conference. Heidelberg: Springer, 2023: 811-823. |
| [27] | KING G, WANG H. HTTPA/2: A Trusted End-to-End Protocol for Web Services[EB/OL]. (2022-09-25)[2025-07-04]. https://doi.org/10.48550/arXiv.2205.01052. |
| [28] | SCHUSTER F, COSTA M, FOURNET C, et al. VC3: Trustworthy Data Analytics in the Cloud Using SGX[C]// IEEE. 2015 IEEE Symposium on Security and Privacy. New York: IEEE, 2015: 38-54. |
| [29] | BHARDWAJ K, SHIH M W, GAVRILOVSKA A, et al. SPX: Preserving End-to-End Security for Edge Computing[EB/OL]. (2018-09-24)[2025-07-04]. https://doi.org/10.48550/arXiv.1809.09038. |
| [30] | CHALKIADAKIS N, DEYANNIS D, KARNIKIS D, et al. The Million Dollar Handshake: Secure and Attested Communications in the Cloud[C]// IEEE. 2020 IEEE 13th International Conference on Cloud Computing. New York: IEEE, 2020: 63-70. |
| [31] | GREVELER U, JUSTUS B, LOHR D. Mutual Remote Attestation: Enabling System Cloning for TPM Based Platforms[C]// Springer. The 7th International Conference on Security and Trust Management. Heidelberg: Springer, 2011: 193-206. |
| [32] | WAGNER P G, BIRNSTILL P, BEYERER J. Establishing Secure Communication Channels Using Remote Attestation with TPM 2.0[C]// Springer. Security and Trust Management. Heidelberg: Springer, 2020: 53-67. |
| [33] | AKRAM R N, MARKANTONAKIS K, MAYES K, et al. An Efficient, Secure and Trusted Channel Protocol for Avionics Wireless Networks[C]// IEEE. IEEE/AIAA 35th Digital Avionics Systems Conference. New York: IEEE, 2016: 1-10. |
| [34] | OTT S, ORTHEN B, WEIDINGER A, et al. MultiTEE: Distributing Trusted Execution Environments[C]// ACM. The 19th ACM Asia Conference on Computer and Communications Security. New York: ACM, 2024: 1617-1629. |
| [35] | SHEPHERD C, AKRAM R N, MARKANTONAKIS K. Establishing Mutually Trusted Channels for Remote Sensing Devices with Trusted Execution Environments[C]// ACM. The 12th International Conference on Availability, Reliability and Security. New York: ACM, 2017: 1-10. |
| [36] | CHEN Jian, DAI Bo, WANG Yanbo, et al. SecTube: SGX-Based Trusted Transmission System[C]// Springer. Smart Computing and Communication. Heidelberg: Springer, 2018: 231-238. |
| [37] | WILL N C, HEINRICH T, VIESCINSKI A B, et al. Trusted Inter-Process Communication Using Hardware Enclaves[C]// IEEE. IEEE International Systems Conference. New York: IEEE, 2021: 1-7. |
| [38] |
JANG J, KANG B B. Securing a Communication Channel for the Trusted Execution Environment[J]. Computers & Security, 2019, 83: 79-92.
doi: 10.1016/j.cose.2019.01.012 URL |
| [39] | JANG J, KONG S, KIM M, et al. SeCReT: Secure Channel between Rich Execution Environment and Trusted Execution Environment[EB/OL]. (2015-02-08)[2025-07-04]. https://www.ndss-symposium.org/wp-content/uploads/2017/09/03_3_2.pdf. |
| [40] | WAGNER P G, BIRNSTILL P, BEYERER J. DDS Security+: Enhancing the Data Distribution Service with TPM-Based Remote Attestation[C]// ACM. The 19th International Conference on Availability, Reliability and Security. New York: ACM, 2024: 1-11. |
| [41] | Confidential 6G Project. Confidential 6G[EB/OL]. (2024-03-15)[2025-07-04]. https://confidential6g.eu/. |
| [42] | DOLEV D, YAO A C. On the Security of Public Key Protocols[EB/OL]. (1981-10-28)[2025-07-04]. https://www.cs.huji.ac.il/-dolev/pubs/dolev-yao-ieee-01056650.pdf. |
| [43] | SHEN Pei, LIU Fulong, SANG Haiwei. Research on Malicious Code Detection[J]. Journal of Chongqing University of Technology (Natural Science Edition), 2022, 36(11): 212-218. |
| 申培, 刘福龙, 桑海伟. 恶意代码检测研究综述[J]. 重庆理工大学学报(自然科学版), 2022, 36(11):212-218. | |
| [44] | KIM Y, SUH H, MUTLU O, et al. Flipping Bits in Memory without Accessing Them: An Experimental Study of DRAM Disturbance Errors[C]// IEEE. 2014 International Symposium on Computer Architecture (ISCA). New York: IEEE, 2014: 361-372. |
| [45] | CASLEY C, TSAFRIR D, GUPTA V, et al. Cuckoo Attacks on Device Authenticated Key Exchange[C]// ACM. ACM Conference on Security and Privacy in Wireless & Mobile Networks (WiSec). New York: ACM, 2013: 1-12. |
| [46] | NIST SP 800-56A Recommendation for Pair-Wise Key Establishment Schemes Using Discrete Logarithm Cryptography[S]. Gaithersburg: National Institute of Standards and Technology, 2013. |
| [47] | ZHAO Shijun, ZHANG Qianying, QIN Yu, et al. SecTEE: A Software Based Approach to Secure Enclave Architecture Using TEE[C]// ACM. The 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 1723-1740. |
| [1] | 杨昱坤, 肖为恩, 梁博轩, 黄鑫. 面向物联网场景的动态三因素认证密钥协商协议[J]. 信息网络安全, 2025, 25(9): 1407-1417. |
| [2] | 拾以娟, 周丹平, 范磊, 刘茵. 基于可信执行环境的安全多方计算协议[J]. 信息网络安全, 2025, 25(9): 1439-1446. |
| [3] | 王梅, 杨潇然, 李增鹏. 简洁低交互的物联网设备认证协议研究[J]. 信息网络安全, 2025, 25(7): 1032-1043. |
| [4] | 郝萌, 李佳勇, 杨洪伟, 张伟哲. 异构CPU-GPU系统机密计算综述[J]. 信息网络安全, 2025, 25(11): 1658-1672. |
| [5] | 关志, 胡建斌, 李悦, 陈钟. 基于可信执行环境的区块链技术与应用综述[J]. 信息网络安全, 2025, 25(11): 1673-1690. |
| [6] | 薛开平, 张淳一, 柳枫, 王峰. 基于可信执行环境的加密数据库索引安全增强方案[J]. 信息网络安全, 2025, 25(11): 1718-1731. |
| [7] | 赵波, 吕佳敏, 王一琁. 一种面向容器生命周期的多维安全度量架构[J]. 信息网络安全, 2025, 25(11): 1745-1761. |
| [8] | 王亚杰, 陆锦标, 李宇航, 范青, 张子剑, 祝烈煌. 基于可信执行环境的联邦学习分层动态防护算法[J]. 信息网络安全, 2025, 25(11): 1762-1773. |
| [9] | 卢笛, 刘玉佳, 吕超越, 孙梦娜, 张清文, 杨力. 一种云原生TEE服务共享机制[J]. 信息网络安全, 2025, 25(11): 1774-1791. |
| [10] | 胡宇义, 蔡炜, 陈竞凡, 刘莫寒, 王鹃, 何运. 面向机密容器的统一远程证明机制研究[J]. 信息网络安全, 2025, 25(11): 1811-1823. |
| [11] | 余发江, 王朝州. TrustZone半虚拟化与容器化实现机制[J]. 信息网络安全, 2025, 25(10): 1523-1536. |
| [12] | 何业锋, 蔡明月, 梁熙媛. 基于逻辑$\chi $态的三方半量子密钥协商协议[J]. 信息网络安全, 2025, 25(1): 27-35. |
| [13] | 张晓均, 张楠, 郝云溥, 王周阳, 薛婧婷. 工业物联网系统基于混沌映射三因素认证与密钥协商协议[J]. 信息网络安全, 2024, 24(7): 1015-1026. |
| [14] | 刘一丹, 马永柳, 杜宜宾, 程庆丰. 一种车联网中的无证书匿名认证密钥协商协议[J]. 信息网络安全, 2024, 24(7): 983-992. |
| [15] | 孙钰, 熊高剑, 刘潇, 李燕. 基于可信执行环境的安全推理研究进展[J]. 信息网络安全, 2024, 24(12): 1799-1818. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||