信息网络安全 ›› 2025, Vol. 25 ›› Issue (11): 1732-1744.doi: 10.3969/j.issn.1671-1122.2025.11.007
基于物理不可克隆函数差异化模型的联盟链硬件认证机制
1.浙江大学计算机科学与技术学院 杭州 310027 2.杭州高新区(滨江)区块链与数据安全研究院 杭州 310051
-
收稿日期:2025-07-28出版日期:2025-11-10发布日期:2025-12-02 -
通讯作者:沈浩頲htshen@zju.edu.cn -
作者简介:沈浩頲(1982—),男,浙江,研究员,博士,主要研究方向为硬件安全、智能网联车安全|彭志刚(2002—),男,江苏,硕士研究生,主要研究方向为物理不可克隆函数|刘宇轩(2001—),男,山东,博士研究生,主要研究方向为物理不可克隆函数|王亚飞(1999—),男,河南,硕士研究生,主要研究方向为区块链 -
基金资助:国家重点研发计划(2022YFB2703200)
Hardware Authentication Mechanism for Consortium Blockchain Based on Differentiated Physical Unclonable Function Models
SHEN Haoting1,2( ), PENG Zhigang1, LIU Yuxuan1, WANG Yafei1
), PENG Zhigang1, LIU Yuxuan1, WANG Yafei1
1. College of Computer Science and Technology ,Zhejiang University Hangzhou 310027, China 2. Hangzhou High-Tech Zone (Binjiang) Institute of Blockchain and Data Security Hangzhou 310051, China
-
Received:2025-07-28Online:2025-11-10Published:2025-12-02
摘要:
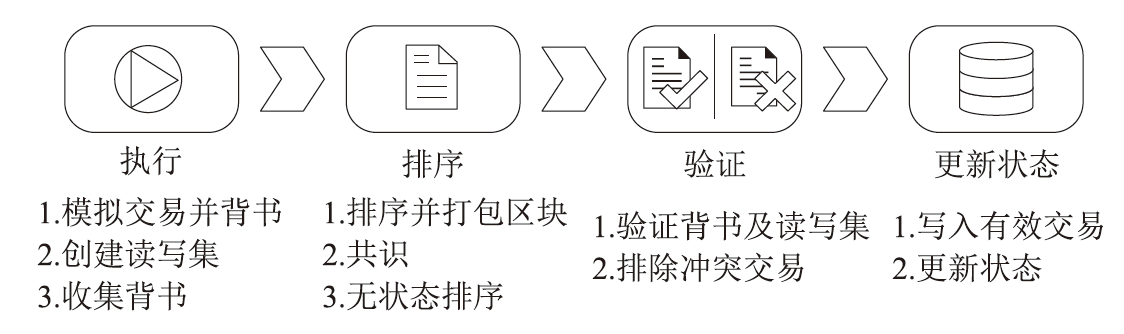
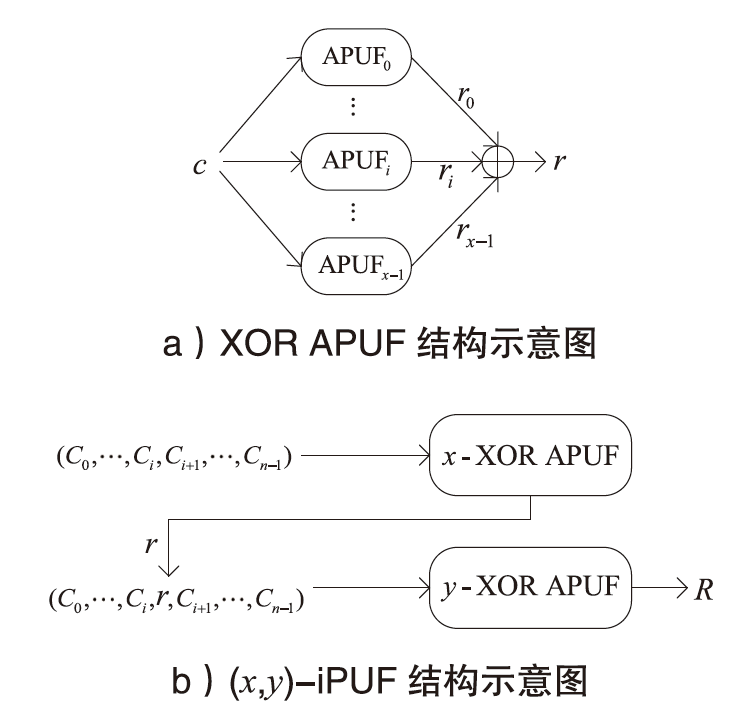
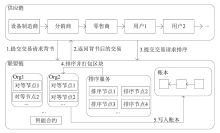
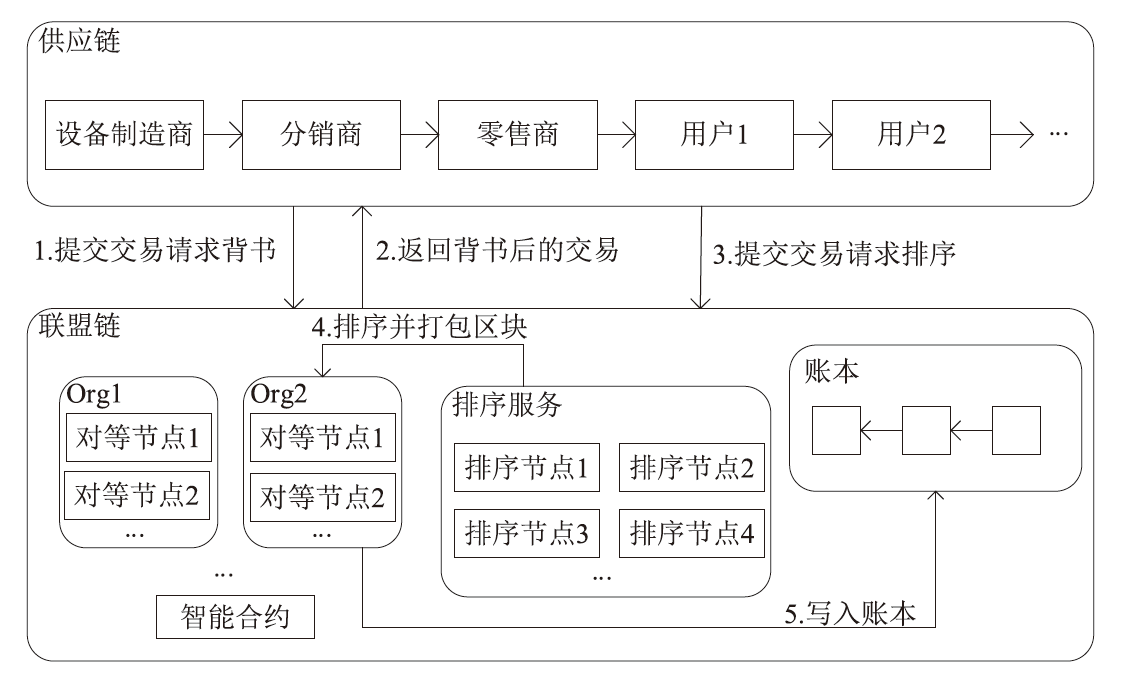
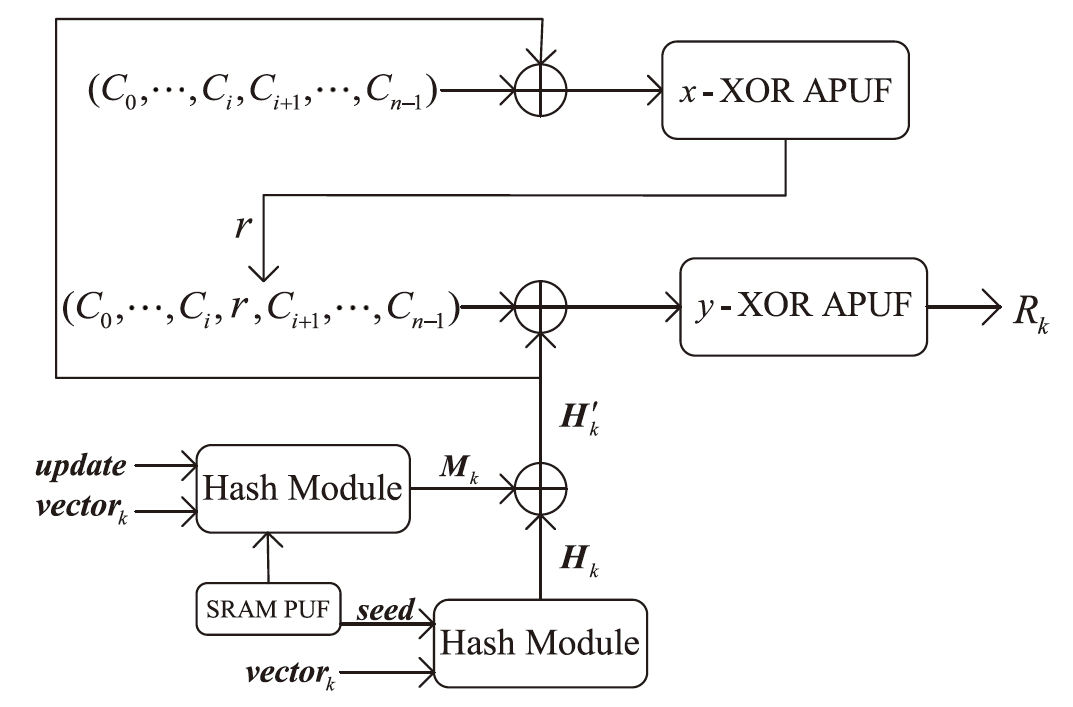
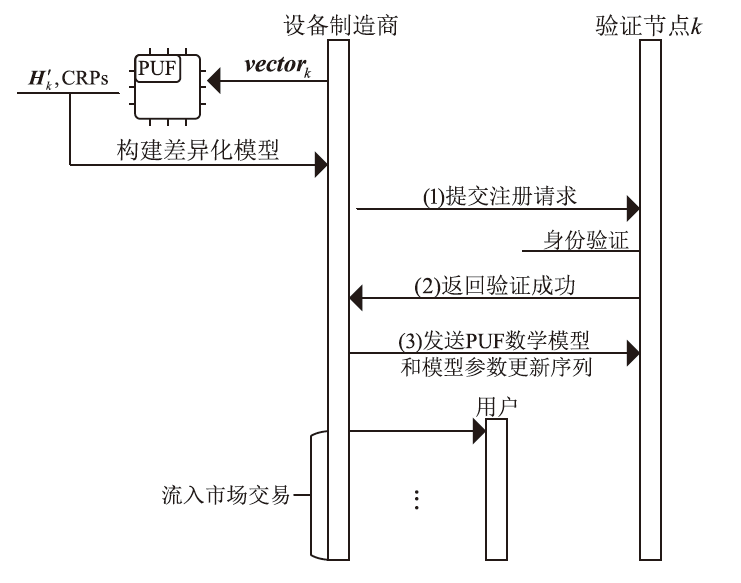
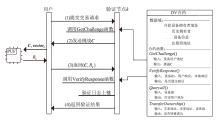
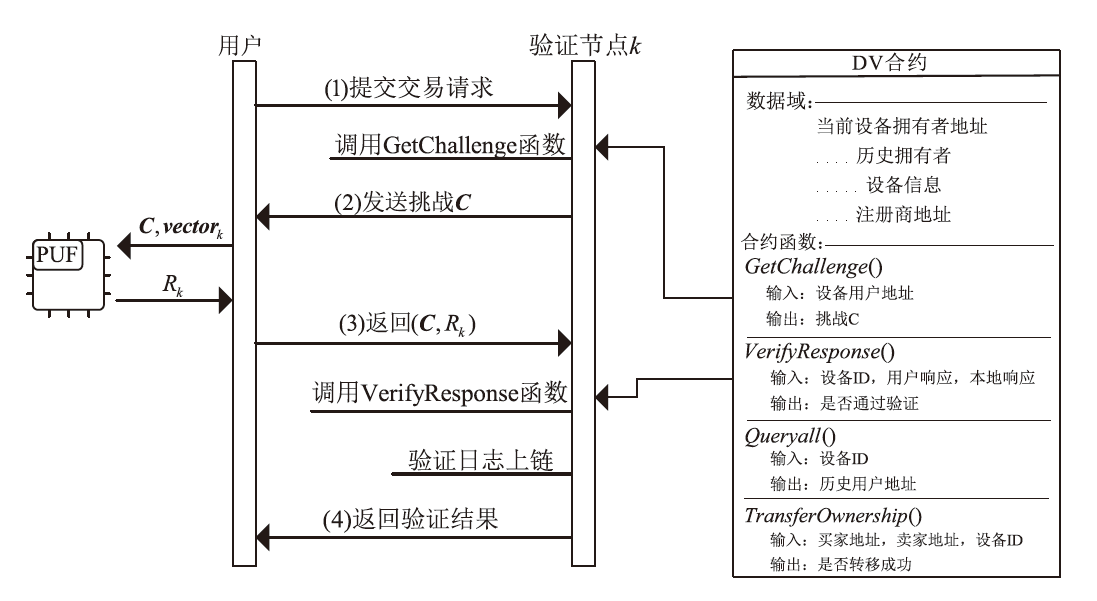
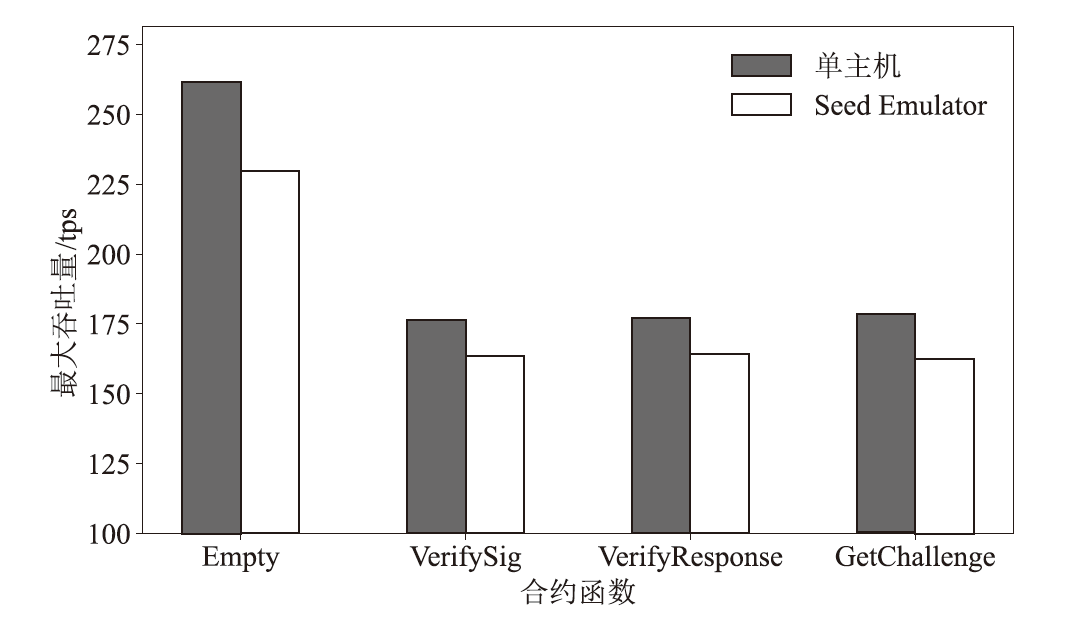
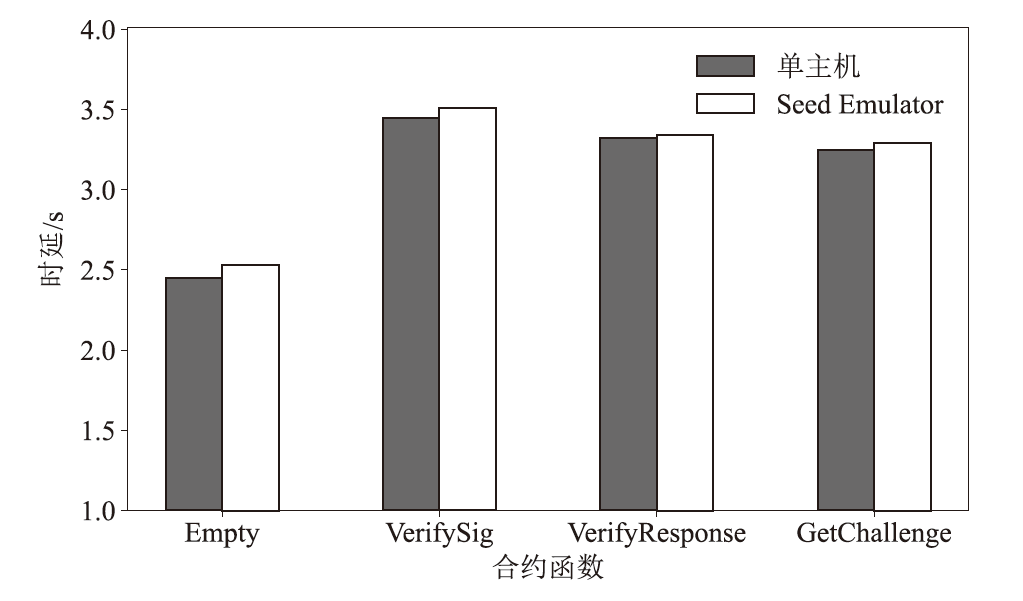
在涉及硬件数据采集的弱中心化体系中,支持多方验证的硬件级设备身份认证、可信计算和数据溯源技术是保证数据全链路安全的关键要素。物理不可克隆函数(PUF)作为一种安全性高、成本可控的硬件安全原语,被广泛应用于设备认证和数据可信领域。然而,传统PUF验证方案在多节点环境中更易泄露PUF敏感信息,进而引发验证失效的风险。因此,文章提出了一种基于PUF验证信息分发差异化和PUF模型可配置的设备验证方案,并以硬件供应链为典型应用场景,设计了相应的硬件模块、验证协议和智能合约。基于Hyperledger Fabric联盟链平台的实验结果表明,文章所提方案可以在保持系统认证效率的同时,显著提升系统对验证信息泄露的抵抗能力,并能有效防御针对PUF的机器学习建模攻击。
中图分类号:
引用本文
沈浩頲, 彭志刚, 刘宇轩, 王亚飞. 基于物理不可克隆函数差异化模型的联盟链硬件认证机制[J]. 信息网络安全, 2025, 25(11): 1732-1744.
SHEN Haoting, PENG Zhigang, LIU Yuxuan, WANG Yafei. Hardware Authentication Mechanism for Consortium Blockchain Based on Differentiated Physical Unclonable Function Models[J]. Netinfo Security, 2025, 25(11): 1732-1744.
表1
DDC-PUF建模结果
| DDC-(x, y)-PUF类型 | 训练所用CRPs数量/对 | 预测准确率 | 训练时间/s |
|---|---|---|---|
| DDC-(1,1)-PUF | 4000 | 76.15% | 4.22 |
| 5600 | 87.01% | 9.93 | |
| 16000 | 98.05% | 21.42 | |
| DDC-(2,2)-PUF | 4800 | 78.23% | 5.13 |
| 8000 | 89.12% | 10.10 | |
| 32000 | 97.45% | 48.77 | |
| DDC-(3,3)-PUF | 64000 | 78.16% | 72.57 |
| 128000 | 89.57% | 148.09 | |
| 288000 | 97.34% | 437.01 | |
| DDC-(4,4)-PUF | 120000 | 75.83% | 142.23 |
| 160000 | 87.82% | 423.11 | |
| 400000 | 96.02% | 899.12 |
| [1] |
POWER D. Supply Chain Management Integration and Implementation: A Literature Review[J]. Supply Chain Management: An International Journal, 2005, 10(4): 252-263.
doi: 10.1108/13598540510612721 URL |
| [2] |
MALIK P K, SHARMA R, SINGH R, et al. Industrial Internet of Things and Its Applications in Industry 4.0: State of the Art[J]. Computer Communications, 2021, 166: 125-139.
doi: 10.1016/j.comcom.2020.11.016 URL |
| [3] |
ELKINS P, BAKER T. Carbon Taxes and Carbon Emissions Trading[J]. Journal of Economic Surveys, 2001, 15(3): 325-376.
doi: 10.1111/joes.2001.15.issue-3 URL |
| [4] |
CHRISTIDIS K, DEVETSIKIOTIS M. Blockchains and Smart Contracts for the Internet of Things[J]. IEEE Access, 2016, 4: 2292-2303.
doi: 10.1109/ACCESS.2016.2566339 URL |
| [5] | LI Zhetao, KANG Jiawen, YU Rong, et al. Consortium Blockchain for Secure Energy Trading in Industrial Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2017, 14(8): 3690-3700. |
| [6] |
DIJESH P, BABU S S, VIJAYALAKSHMI Y. Enhancement of E-Commerce Security through Asymmetric Key Algorithm[J]. Computer Communications, 2020, 153: 125-134.
doi: 10.1016/j.comcom.2020.01.033 URL |
| [7] | JAIN A K, GUPTA N, GUPTA B B. A Survey on Scalable Consensus Algorithms for Blockchain Technology[EB/OL]. (2024-07-08)[2025-07-20]. https://doi.org/10.1016/j.csa.2024.100065. |
| [8] | XU Qiang, ZHENG Rong, SAAD W, et al. Device Fingerprinting in Wireless Networks: Challenges and Opportunities[J]. IEEE Communications Surveys & Tutorials, 2015, 18(1): 94-104. |
| [9] | OSBORN J D, CHALLENER D C. Trusted Platform Module Evolution[J]. Johns Hopkins APL Technical Digest (Applied Physics Laboratory), 2013, 32(2): 536-543. |
| [10] |
HERDER C, YU M D, KOUSHANFAR F, et al. Physical Unclonable Functions and Applications: A Tutorial[J]. Proceedings of the IEEE, 2014, 102(8): 1126-1141.
doi: 10.1109/JPROC.2014.2320516 URL |
| [11] |
ZHANG Jiliang, SHEN Chaoqun. Set-Based Obfuscation for Strong PUFs against Machine Learning Attacks[J]. IEEE Transactions on Circuits and Systems I: Regular Papers, 2020, 68(1): 288-300.
doi: 10.1109/TCSI.8919 URL |
| [12] | SUH G E, DEVADAS S. Physical Unclonable Functions for Device Authentication and Secret Key Generation[C]// ACM. 2007 44th ACM/IEEE Design Automation Conference. New York: ACM, 2007: 9-14. |
| [13] | RÜHRMAIR U, SEHNKE F, SÖLTER J, et al. Modeling Attacks on Physical Unclonable Functions[C]// ACM. The 17th ACM Conference on Computer and Communications Security. New York: ACM, 2010: 237-249. |
| [14] | DU Wenliang, ZHENG Honghao, WON K. SEED Emulator: An Internet Emulator for Research and Education[C]// ACM. The 21st ACM Workshop on Hot Topics in Networks (HotNets). New York: ACM, 2022: 101-107. |
| [15] | ANDROULAKI E, BARGER A, BORTNIKOV V, et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains[C]// ACM. The 13th ACM European Conference on Computer Systems (EuroSys). New York: ACM, 2018: 1-15. |
| [16] | GASSEND B, CLARKE D, VAN D M, et al. Silicon Physical Random Functions[C]// ACM. The 9th ACM Conference on Computer and Communications Security. New York: ACM, 2002: 148-160. |
| [17] |
PAPPU R, RECHT B, TAYLOR J, et al. Physical One-Way Functions[J]. Science, 2002, 297(5589): 2026-2030.
pmid: 12242435 |
| [18] | HALAK B, ZWOLINSKI M, MISPAN M S. Overview of PUF-Based Hardware Security Solutions for the Internet of Things[C]// IEEE. 2016 IEEE 59th International Midwest Symposium on Circuits and Systems. New York: IEEE, 2016: 1-4. |
| [19] |
DAS B P, AMRUTUR B, JAMADAGNI H S, et al. Within-Die Gate Delay Variability Measurement Using Reconfigurable Ring Oscillator[J]. IEEE Transactions on Semiconductor Manufacturing, 2009, 22(2): 256-267.
doi: 10.1109/TSM.2009.2017662 URL |
| [20] |
LIM D, LEE J W, GASSEND B, et al. Extracting Secret Keys from Integrated Circuits[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 2005, 13(10): 1200-1205.
doi: 10.1109/TVLSI.2005.859470 URL |
| [21] | NGUYEN P H, SAHOO D P, JIN Chenglu, et al. The Interpose PUF: Secure PUF Design against State-of-the-Art Machine Learning Attacks[J]. IACR Transactions on Cryptographic Hardware and Embedded Systems, 2019, 2019(4): 243-290. |
| [22] | ISLAM M N, KUNDU S. Enabling IC Traceability via Blockchain Pegged to Embedded PUF[J]. ACM Transactions on Design Automation of Electronic Systems, 2019, 24(3): 1-23. |
| [23] |
ASIF R, GHANEM K, IRVINE J. Proof-of-PUF Enabled Blockchain: Concurrent Data and Device Security for Internet-of-Energy[J]. Sensors, 2020, 21(1): 1-32.
doi: 10.3390/s21010001 URL |
| [24] | LI Dawei, CHEN Ruonan, LIU Di, et al. Blockchain-Based Authentication for IIoT Devices with PUF[EB/OL]. (2022-07-07)[2025-07-25]. https://doi.org/10.1016/j.sysarc.2022.102638. |
| [25] |
ROSTAMI M, MAJZOOBI M, KOUSHANFAR F, et al. Robust and Reverse-Engineering Resilient PUF Authentication and Key-Exchange by Substring Matching[J]. IEEE Transactions on Emerging Topics in Computing, 2014, 2(1): 37-49.
doi: 10.1109/TETC.6245516 URL |
| [26] | TUN N W, MAMBO M. Secure PUF-Based Authentication Systems[EB/OL]. (2024-08-15)[2025-07-25]. https://doi.org/10.3390/s24165295. |
| [27] |
MALL P, AMIN R, DAS A K, et al. PUF-Based Authentication and Key Agreement Protocols for IoT, WSNs, and Smart Grids: A Comprehensive Survey[J]. IEEE Internet of Things Journal, 2022, 9(11): 8205-8228.
doi: 10.1109/JIOT.2022.3142084 URL |
| [28] | GASSEND B, DIJK M V, CLARKE D, et al. Controlled Physical Random Functions and Applications[J]. ACM Transactions on Information and System Security (TISSEC), 2008, 10(4): 1-22. |
| [29] | MAJZOOBI M, ROSTAMI M, KOUSHANFAR F, et al. Slender PUF Protocol:A Lightweight, Robust, and Secure Authentication by Substring Matching[C]// IEEE. 2012 IEEE Symposium on Security and Privacy Workshops. New York: IEEE, 2012: 33-44. |
| [30] |
YAN Wei, TEHRANIPOOR F, CHANDY J A. PUF-Based Fuzzy Authentication without Error Correcting Codes[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2016, 36(9): 1445-1457.
doi: 10.1109/TCAD.2016.2638445 URL |
| [1] | 袁征, 张跃飞, 冯笑, 乔雅馨. 基于PUF的电力物联网智能终端认证协议[J]. 信息网络安全, 2025, 25(1): 13-26. |
| [2] | 彭翰中, 张珠君, 闫理跃, 胡成林. 联盟链下基于联邦学习聚合算法的入侵检测机制优化研究[J]. 信息网络安全, 2023, 23(8): 76-85. |
| [3] | 俞惠芳, 乔一凡, 孟茹. 面向区块链金融的抗量子属性基门限环签密方案[J]. 信息网络安全, 2023, 23(7): 44-52. |
| [4] | 张学旺, 张豪, 姚亚宁, 付佳丽. 基于群签名和同态加密的联盟链隐私保护方案[J]. 信息网络安全, 2023, 23(3): 56-61. |
| [5] | 谭伟杰, 杨雨婷, 牛坤, 彭长根. 基于MI-PUF的V2X车联网通信安全认证协议[J]. 信息网络安全, 2023, 23(12): 38-48. |
| [6] | 李莉, 李泽群, 李雪梅, 史国振. 基于交叉耦合电路的物理不可克隆函数FPGA实现[J]. 信息网络安全, 2022, 22(3): 53-61. |
| [7] | 陈彬杰, 魏福山, 顾纯祥. 基于KNN的具有隐私保护功能的区块链异常交易检测[J]. 信息网络安全, 2022, 22(3): 78-84. |
| [8] | 张学旺, 姚亚宁, 黎志鸿, 张豪. 基于联盟链和Asmuth-Bloom秘密共享算法的数据共享方案[J]. 信息网络安全, 2022, 22(11): 17-23. |
| [9] | 王利, 李二霞, 纪宇晨, 李小勇. 基于PUF的抗物理克隆RFID安全认证协议[J]. 信息网络安全, 2020, 20(8): 89-97. |
| [10] | 张正, 查达仁, 柳亚男, 方旭明. 基于物理不可克隆函数的Kerberos扩展协议及其形式化分析[J]. 信息网络安全, 2020, 20(12): 91-97. |
| [11] | 胡蝶, 马东堂, 龚旻, 马召. 一种基于PUF的物理层安全认证方法[J]. 信息网络安全, 2020, 20(1): 61-66. |
| [12] | 郑敏, 王虹, 刘洪, 谭冲. 区块链共识算法研究综述[J]. 信息网络安全, 2019, 19(7): 8-24. |
| [13] | 邹红霞, 齐斌, 王宇, 李冀兴. 基于联盟链和DNA编码的局域网加密技术[J]. 信息网络安全, 2018, 18(12): 31-37. |
| [14] | 蒋政君, 田海博, 张方国. 基于PUF的RFID防伪技术研究综述[J]. 信息网络安全, 2016, 16(4): 38-43. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||