信息网络安全 ›› 2016, Vol. 16 ›› Issue (4): 38-43.doi: 10.3969/j.issn.1671-1122.2016.04.006
基于PUF的RFID防伪技术研究综述
- 1.中山大学数据科学与计算机学院,广东广州 510006
2.广东省信息安全技术重点实验室,广东广州 510006
-
收稿日期:2015-12-26出版日期:2016-04-20发布日期:2020-05-13 -
作者简介:作者简介: 蒋政君(1993—),男,江西,硕士研究生,主要研究方向为密码学与信息安全;田海博(1979—),男,河北,副教授,博士,主要研究方向为安全协议设计与分析;张方国(1972—),男,山东,教授,博士,主要研究方向为密码学与信息安全。
-
基金资助:国家自然科学基金[61379154]
Survey on PUF-based RFID Anti-counterfeiting Techniques
Zhengjun JIANG1,2, Haibo TIAN1,2, Fangguo ZHANG1,2( )
)
- 1. School of Data and Computer Science, Sun Yat-sen University, Guangzhou Guangdong 510006, China
2. Guangdong Provincial Key Laboratory of Information Security, Guangzhou Guangdong 510006, China
-
Received:2015-12-26Online:2016-04-20Published:2020-05-13
摘要:
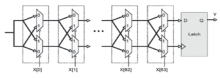
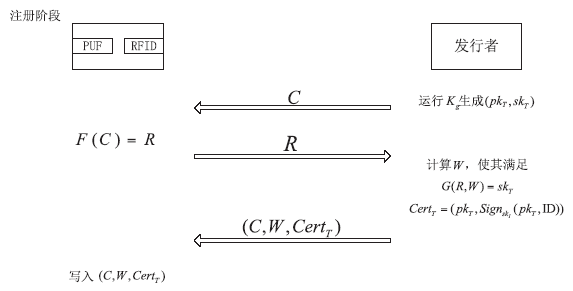
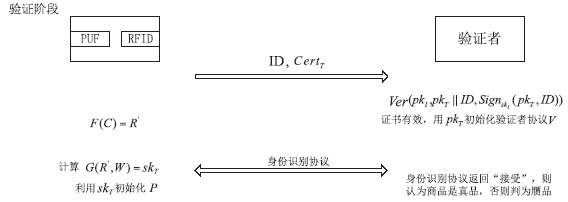
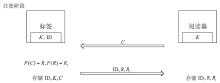
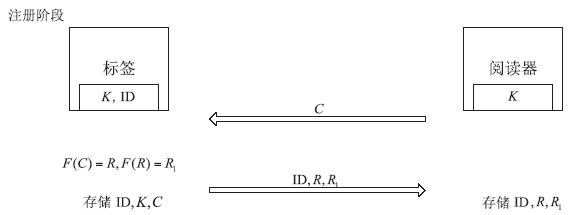
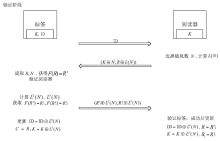
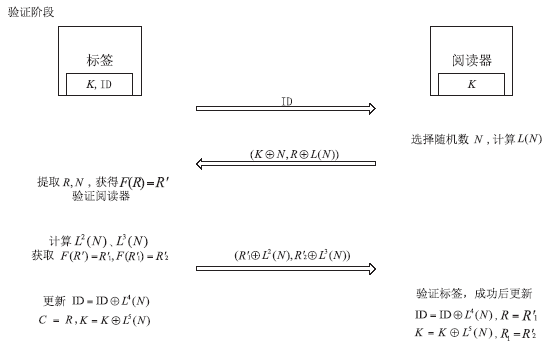
随着信息科学与技术的快速发展,射频识别(RFID)技术被应用到越来越多的场合,给人们带来了诸多便利。但是,RFID技术存在一些安全隐患。例如,攻击者可以窃取RFID系统通信过程中的重要信息,进行克隆等攻击。物理不可克隆函数(PUF)是解决克隆问题的有效技术手段,基于PUF的RFID系统可以很好地达到防伪要求。文章首先对目前RFID系统存在的伪造情况进行概述和分析,进而提出防伪的必要性。然后从公钥密码技术和私钥密码技术两个方面对目前基于PUF的RFID主要防伪技术做了一个比较全面的综述,总结不同方案的优缺点。
中图分类号:
引用本文
蒋政君, 田海博, 张方国. 基于PUF的RFID防伪技术研究综述[J]. 信息网络安全, 2016, 16(4): 38-43.
Zhengjun JIANG, Haibo TIAN, Fangguo ZHANG. Survey on PUF-based RFID Anti-counterfeiting Techniques[J]. Netinfo Security, 2016, 16(4): 38-43.
使用本文
| [1] | BERNARDI P, GANDINO F, LAMBERTI F, et al.An Anti-counterfeit Mechanism for the Application Layer in Low-cost RFID Devices[C]// IEEE.Circuits and Systems for Communications, 2008. ECCSC 2008. 4th European Conference on, July 10-11,2008. Bucharest, Romania.NJ:IEEE, 2008: 227-231. |
| [2] | PAPPU R, RECHT B, TAYLOR J, et al.Physical One-way Functions[J]. Science, 2002, 297(5589): 2026-2030. |
| [3] | DEVADAS S, SUH E, PARAL S, et al.Design and Implementation of PUF-based" unclonable" RFID ICs for Anti-counterfeiting and Security Applications[C]// IEEE.RFID, 2008 IEEE International Conference on,April 16-17,2008. Las Vegas, NV,USA.NJ:IEEE, 2008: 58-64. |
| [4] | TUYLS P, SCHRIJEN G J, ŠKORIĆ B, et al.Read-proof Hardware from Protective Coatings[J]. Ches, 2006 (4249):369-383. |
| [5] | KUMAR S S, GUAJARDO J, MAES R, et al.The Butterfly PUF Protecting IP on Every FPGA[C]// IEEE.Hardware-Oriented Security and Trust, 2008. HOST 2008. IEEE International Workshop on, June 9-9,2008. Anaheim, CA,USA.NJ:IEEE, 2008: 67-70. |
| [6] | CHEN Z, ZENG Y, HEFFERMAN G.FiberID: Molecular-level Secret for Identification of Things[C]// IEEE.Parallel Computing Technologies (Parcomptech), 2015 National Conference on, December 3-5,2014.Atlanta, GA,USA.NJ:IEEE, 2015: 84-88. |
| [7] | LEE Y K, BATINA L, SINGELEE D, et al. Anti-counterfeiting, Untraceability and Other Security Challenges for RFID Systems: Public-key-based Protocols and Hardware[EB/OL]. , 2010-10-12. |
| [8] | OZTIIRK E, HAMMOURI G, SUNAR B.Towards Robust Low Cost Authentication for Pervasive Devices[C]// IEEE.PERCOM '08 Proceedings of the 2008 Sixth Annual IEEE International Conference on Pervasive Computing and Communications, March 17-21, 2008. Hong Kong ,China. Washington:IEEE, 2008: 170-178. |
| [9] | BATINA L, GUAJARDO J, KERINS T, et al.Public-key Cryptography for RFID-Tags[C]// IEEE.Pervasive Computing and Communications Workshops, 2007. PerCom Workshops' 07. Fifth Annual IEEE International Conference on, March 19-23,2007. White Plains, NY,USA. Washington:IEEE, 2007: 217-222. |
| [10] | TUYLS P, BATINA L. RFID-tags for Anti-Counterfeiting[EB/OL]. ,2015-12-1. |
| [11] | JIANG D, CHONG C N.Anti-counterfeiting Using Phosphor PUF[C]//IEEE.Anti-counterfeiting, Security and Identification, 2008. ASID 2008. 2nd International Conference on,August 20-23,2008. Guiyang,China.NJ:IEEE, 2008: 59-62. |
| [12] | CHONG C N, JIANG D, ZHANG J, et al.Anti-counterfeiting with a Random Pattern[C]// IEEE.Emerging Security Information, Systems and Technologies, 2008. SECURWARE'08. Second International Conference on, August.25-31,2008. Cap Esterel,France. Washington:IEEE, 2008: 146-153. |
| [13] | 张紫楠, 刘威, 郭渊博. 物理不可克隆函数综述[J]. 计算机应用, 2012, 32(11): 3115-3120. |
| [14] | JIN Yongming, XIN Wei , SUN Huiping ,et al .PUF-based RFID Authentication Protocol against Secret Key Leakage[EB/OL]. ,2015-12-1. |
| [15] | DIORIO C J, COOPER S A. RFID Tag Authentication with Public-key Cryptography: U.S. Patent 8,941,469[P].2015-1-27. |
| [16] | MOLNAR D, WAGNER D.Privacy and Security in Library RFID: Issues, Practices, and Architectures[C]//ACM.Proceedings of the 11th ACM Conference on Computer and Communications Security,October 25-29,2004. Washington,DC,USA.New York:ACM, 2004: 210-219. |
| [17] | JUELS A.RFID Security and Privacy: A research Survey[J]. Selected Areas in Communications, 2006, 24(2): 381-394. |
| [18] | XU Xuguang, OU Yuyi, JIE Ling, et al.Lightweight RFID Secure Authentication Protocol Based on PUF[J]. Computer Applications and Software, 2014(11): 78. |
| [19] | HE Z, ZOU L.High-efficient Rfid Authentication Protocol Based on Physical Unclonable Function[C]// IEEE.Wireless Communications, Networking and Mobile Computing (WiCOM), 2012 8th International Conference on, September 21-23,2012. Shanghai ,China.NJ:IEEE, 2012: 1-4. |
| [20] | LEE Y S, KIM T Y, LEE H J.Mutual Authentication Protocol for Enhanced RFID Security and Anti-counterfeiting[C]// IEEE.Advanced Information Networking and Applications Workshops (WAINA), 2012 26th International Conference on, March 26-29,2012. Fukuoka,Japan. Washington:IEEE, 2012: 558-563. |
| [21] | XU Y, HE Z.Design of a Security Protocol for Low-cost Rfid[C]// IEEE.Wireless Communications, Networking and Mobile Computing (WiCOM), 2012 8th International Conference on, September 21-23,2012. Shanghai, China .NJ:IEEE, 2012: 1-3. |
| [22] | KARDAŞ S L, ÇELIK S, YILDIZ M, et al.PUF-enhanced Offline RFID Security and Privacy[J]. Journal of Network and Computer Applications, 2012, 35(6): 2059-2067. |
| [23] | LEE Y K, BATINA L, VERBAUWHEDE I. EC-RAC (ECDLP Based Randomized Access Control): Provably Secure RFID Authentication Protocol[C]// IEEE.RFID, 2008 IEEE International Conference on, April 16-17,2008. Las Vegas, NV,USA.NJ: IEEE, 2008: 97-104. |
| [24] | BRINGER J, CHABANNE H, ICART T. Cryptanalysis of EC-RAC, a RFID Identification Protocol[EB/OL].,2015-12-1. |
| [25] | MEHMANDOUST S, ATANI R E.Application of PUF-enabled RFID Tags in Electronic Banking[J]. International Journal of Computer Science & Information Technology, 2011, 3(2): 191-202. |
| [26] | BASSIL R, EL-BEAINO W, ITANI W, et al.PUMAP: A PUF-based Ultra-lightweight Mutual-authentication RFID Protocol[J]. International Journal of RFID Security and Cryptography, 2012, 1(1/2): 58-66. |
| [27] | SAFKHANI M, BAGHERI N, NADERI M.Security Analysis of a PUF-based RFID Authentication Protocol[J]. IACR Cryptology ePrint Archive, 2011(2011):704. |
| [28] | RAY B, CHOWDHURY M, ABAWAIY J.PUF-based Secure Checker Protocol for Networked RFID Systems[C]// IEEE.Open Systems (ICOS), 2014 IEEE Conference on, October 26-28,2014. Subang,Malaysia.NJ: IEEE, 2014: 78-83. |
| [1] | 刘晓芬, 陈晓峰, 连桂仁, 林崧. 基于d级单粒子的可认证多方量子秘密共享协议[J]. 信息网络安全, 2020, 20(3): 51-55. |
| [2] | 侯林, 冯达, 玄鹏开, 周福才. 基于认证树的外包数据库连接查询验证方案[J]. 信息网络安全, 2020, 20(2): 91-97. |
| [3] | 胡蝶, 马东堂, 龚旻, 马召. 一种基于PUF的物理层安全认证方法[J]. 信息网络安全, 2020, 20(1): 61-66. |
| [4] | 张富友, 王琼霄, 宋利. 基于生物特征识别的统一身份认证系统研究[J]. 信息网络安全, 2019, 19(9): 86-90. |
| [5] | 侯林, 李明洁, 徐剑, 周福才. 基于变长认证跳表的分布式动态数据持有证明模型[J]. 信息网络安全, 2019, 19(7): 67-74. |
| [6] | 亢保元, 颉明明, 司林. 基于生物识别技术的多云服务器认证方案研究[J]. 信息网络安全, 2019, 19(6): 45-52. |
| [7] | 陈瑞滢, 陈泽茂, 王浩. 工业控制系统安全监控协议的设计与优化研究[J]. 信息网络安全, 2019, 19(2): 60-69. |
| [8] | 韦永霜, 陈建华, 韦永美. 基于椭圆曲线密码的RFID/NFC安全认证协议[J]. 信息网络安全, 2019, 19(12): 64-71. |
| [9] | 张顺, 陈张凯, 梁风雨, 石润华. 基于Bell态的量子双向身份认证协议[J]. 信息网络安全, 2019, 19(11): 43-48. |
| [10] | 张敏, 许春香, 黄闽英. 远程医疗环境下面向多服务器的轻量级多因子身份认证协议研究[J]. 信息网络安全, 2019, 19(10): 42-49. |
| [11] | 姚萌萌, 朱正超, 刘明达. 一种改进的基于认证测试的形式化分析方法[J]. 信息网络安全, 2019, 19(1): 27-33. |
| [12] | 郝文江, 宋斐, 万月亮. 可穿戴单警装备安全认证协议研究[J]. 信息网络安全, 2018, 18(9): 25-29. |
| [13] | 段琼琼, 项定华, 史红周. 基于区块链的智能物件认证技术方案设计[J]. 信息网络安全, 2018, 18(9): 95-101. |
| [14] | 胡卫, 吴邱涵, 刘胜利, 付伟. 基于国密算法和区块链的移动端安全eID及认证协议设计[J]. 信息网络安全, 2018, 18(7): 7-9. |
| [15] | 叶阿勇, 李晴, 金俊林, 孟铃玉. 无线网络接入中用户身份和位置的双重隐身机制研究[J]. 信息网络安全, 2018, 18(7): 29-35. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 256
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 450
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||