信息网络安全 ›› 2019, Vol. 19 ›› Issue (12): 64-71.doi: 10.3969/j.issn.1671-1122.2019.12.008
基于椭圆曲线密码的RFID/NFC安全认证协议
- 1.武汉大学数学与统计学院,湖北武汉 430000
2.广州地铁设计研究院股份有限公司,广东广州 510010
-
收稿日期:2019-06-12出版日期:2019-12-10发布日期:2020-05-11 -
作者简介:作者简介:韦永霜(1994—),女,广西,硕士研究生,主要研究方向为密码与信息安全、认证协议;陈建华(1963—),男,湖北,教授,博士,主要研究方向为数论与密码、椭圆曲线密码、格密码理论等;韦永美(1987—),女,广西,工程师,硕士,主要研究方向为地下工程、BIM协同平台研究。
-
基金资助:国家重点研发计划[2017YFB1201102]
Security Authentication Protocol for RFID/NFC Based on Elliptic Curve Cryptography
Yongshuang WEI1( ), Jianhua CHEN1, Yongmei WEI2
), Jianhua CHEN1, Yongmei WEI2
- 1.School of Mathematics and Statistics, Wuhan University, Wuhan Hubei 430000, China
2. Guangzhou Metro Design and Research Institute Co., Ltd., Guangzhou Guangdong 510010, China
-
Received:2019-06-12Online:2019-12-10Published:2020-05-11
摘要:
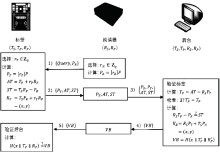
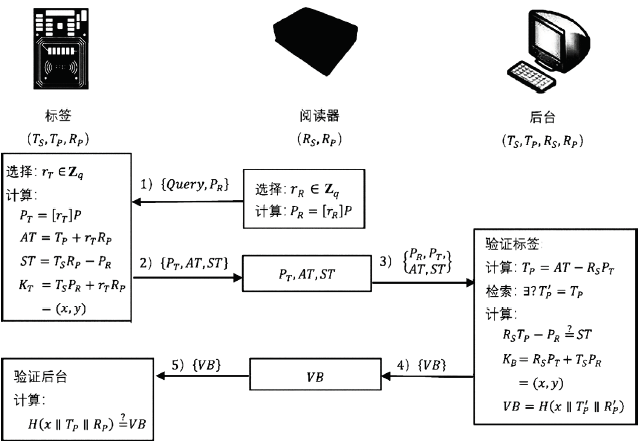
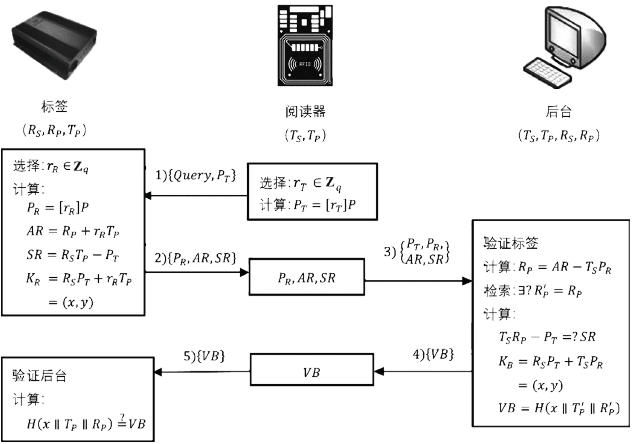
文章设计了一种基于椭圆曲线密码的RFID/NFC安全认证协议。该协议不仅满足RFID系统最基本的相互认证、机密性、匿名性等性质,且能抵抗跟踪攻击、假冒攻击、拒绝服务攻击等各类攻击。不同于绝大多数RFID认证协议,该协议实现了标签和阅读器都兼具读写功能以及点对点通信,因此也适用于由RFID技术和互联互通技术整合演变而来的NFC系统。除此之外,该协议协商出了为后续通信、读取、修改数据等提供保障的双方公共的秘密密钥。文章利用串空间模型从相互认证性和机密性两方面对协议进行了形式化证明。结果表明,文章协议是一个可用于通信的RFID/NFC系统的安全认证协议。
中图分类号:
引用本文
韦永霜, 陈建华, 韦永美. 基于椭圆曲线密码的RFID/NFC安全认证协议[J]. 信息网络安全, 2019, 19(12): 64-71.
Yongshuang WEI, Jianhua CHEN, Yongmei WEI. Security Authentication Protocol for RFID/NFC Based on Elliptic Curve Cryptography[J]. Netinfo Security, 2019, 19(12): 64-71.
使用本文
| [1] | SHEN Han, SHEN Jian, MUHAMMAD K K, et al.Efficient RFID Authentication Using Elliptic Curve Cryptography for the Internet of Things[J]. Wireless Personal Communications, 2017, 96(4): 5253-5266. |
| [2] | HUO Weiguang, DONG Qingkuan, CHENG Yuan.ECC-based RFID/NFC Mutual Authentication Protocol[C]//IWMECS. 2nd International Workshop on Materials Engineering and Computer Sciences(IWMECS 2015), October 10-11, 2015, Jinan, China. Paris:IWMECS, 2015: 169-177. |
| [3] | PAN Yaomin, SHAN Zheng, DAI Qing, et al.CPK-ECC-based Mutual Authentication Protocol for Large-scale RFID System[J]. Journal on Communications, 2017, 38(8): 165-171. |
| 潘耀民,单征,戴青,等.大规模RFID系统中基于CPK-ECC的双向认证协议[J].通信学报,2017,38(8):165-171. | |
| [4] | BATINA L, GUAJARDO J, KERINS T, et al.Public-key Cryptography for RFID-tags[C]//IEEE. Fifth Annual IEEE International Conference on Pervasive Computing and Communications Workshops(PerComW’7), March 19-23, 2007, White Plains, NY, USA. NJ: IEEE, 2007: 217-222. |
| [5] | LEE Y K, BATINA L, VERBAUWHEDE I.EC-RAC(ECDLP-based Randomized Access Control): Provably Secure RFID Authentication Protocol[C]//IEEE. 2008 IEEE International Conference on RFID, April 16-17, 2008, Las Vegas, NV, USA. NJ: IEEE, 2008: 97-104. |
| [6] | ZHANG Xinglei, LI Linsen, WU Yue, et al.An ECDLP-based Randomized Key RFID Authentication Protocol[C]//IEEE. 2011 International Conference on Network Computer and Computing and Information Security(NCIS), May 14-15, 2011, Guilin, China. NJ: IEEE, 2011: 146-149. |
| [7] | MOOSAVI S R, NIGUSSIE E, VIRTANEN S, et al.An Elliptic Curve-based Mutual Authentication Scheme for RFID Implant Systems[J]. Procedia Computer Science, 2014, 32: 198-206. |
| [8] | LIAO Yipin, HSIAO C M.A Secure ECC-based RFID Authentication Scheme Integrated with ID-verifier Transfer Protocol[J]. Ad Hoc Networks, 2014, 18: 133-146. |
| [9] | RYU E K, KIM D S, YOO KY.On Elliptic Curve Based Untraceable RFID Authentication Protocols[C]//ACM. The 3rd ACM Workshop in Information Hiding and Multimedia Security, June 17-19, 2015, Portland, Oregon, USA. New York: ACM, 2015: 147-153. |
| [10] | KANG Hongyan.Analysis and Improvement of Grouping-proof Protocol for RFID Based on ECC[J]. International Journal of Control and Automation. 2013, 39(1): 153-156, 163. |
| 康鸿雁. 基于ECC的RFID组证明协议分析及改进[J].计算机工程,2013,39(1):153-156,163. | |
| [11] | ALAMR A A, KAUSAR F, KIM J, et al.A Secure ECC-based RFID Mutual Authentication Protocol for Internet of Things[J]. Journal of Supercomputing, 2018, 74(9): 4281-4294. |
| [12] | ZHENG Lijuan, XUE Yujuan, ZHANG Linhao, et al.Mutual Authentication Protocol for RFID-based on ECC[C]//IEEE. 20th IEEE International Conference on Computational Science and Engineering(CSE) and/ 15th IEEE/IFIP International Conference on Embedded and Ubiquitous Computing(EUC), July 21-24, 2017, Guangzhou, China. NJ: IEEE, 2017: 320-323. |
| [13] | WANG Huanbao, ZHANG Yousheng, HOU Zhengfeng.Strand Space Model to Prove the Security of Cryptographic Protocols[J]. Journal of Hefei University of Technology(Natural Science), 2005, 28(5): 449-455. |
| 王焕宝,张佑生,侯整风.用于密码协议安全性证明的串空间模型[J]. 合肥工业大学学报(自然科学版),2005,28(5):449-455. | |
| [14] | DING Mengwei, ZHOU Qinglei, ZHAO Dongming.Strand Space Model of Yahalom-Paulson Protocol and Its Analysis[J]. Computer Engineering and Applications, 2008, 44(22): 97-99, 103. |
| 丁萌伟,周清雷,赵东明. Yahalom-Paulson协议的串空间模型与分析[J].计算机工程与应用,2008,44(22):97-99,103. | |
| [15] | TAN Lili, LIU Jing, XIE Hongbo, et al.Theory and Application of Strand Spaces Model[J]. Journal of Computer Applications, 2005, 25(8): 1747-1749, 1752. |
| 谭立力,刘璟,谢鸿波,等.串空间模型的原理与应用[J].计算机应用,2005,25(8):1747-1749,1752. | |
| [16] | THAYER F J, HERZOG J C, GUTTMAN J D.Strand Spaces: Honest Ideals on Strand Spaces[C]//IEEE. The 11th IEEE Workshop on Computer Security Foundations, June 9-11, 1998, Rockport, MA, USA. New York: ACM, 1998: 66-77. |
| [17] | ZHAO Zhengguo.A Secure RFID Authentication Protocol for Healthcare Environments Using Elliptic Curve Cryptosystem[J]. Journal of Medical Systems, 2014, 38(5): 46. |
| [18] | LIU Guoliang, ZHANG Huichuan, KONG Fanyue, et al.A Novel Authentication Management RFID Protocol Based on Elliptic Curve Cryptography[J]. Wireless Personal Communications, 2018, 101(3): 1445-1455. |
| [1] | 郝文江, 宋斐, 万月亮. 可穿戴单警装备安全认证协议研究[J]. 信息网络安全, 2018, 18(9): 25-29. |
| [2] | 周志彬, 张少波, 罗恩韬, 李超良. 一种无可信第三方的批量RFID所有权转移协议[J]. 信息网络安全, 2018, 18(6): 18-27. |
| [3] | 张小红, 郭焰辉. 基于椭圆曲线密码的RFID系统安全认证协议研究[J]. 信息网络安全, 2018, 18(10): 51-61. |
| [4] | 贾徽徽, 王潮, 顾健, 陆臻. 基于Grover量子中间相遇搜索算法的ECC攻击错误bit的修正[J]. 信息网络安全, 2016, 16(6): 28-34. |
| [5] | 张言胜, 汪学明, 仇各各. 一种新的动态门限数字签名方案研究[J]. 信息网络安全, 2016, 16(6): 62-67. |
| [6] | 陈宇航, 贾徽徽, 姜丽莹, 王潮. 基于Grover算法的ECC扫描式攻击[J]. 信息网络安全, 2016, 16(2): 28-32. |
| [7] | 段然, 徐乃阳, 胡爱群. 基于形式化分析工具的认证协议安全性研究[J]. 信息网络安全, 2015, 15(7): 71-76. |
| [8] | 仇各各, 汪学明, 张言胜. 基于HECC的WSN身份认证协议研究[J]. 信息网络安全, 2015, 15(12): 54-58. |
| [9] | . 轻量级RFID双向通信认证协议优化方案[J]. , 2014, 14(2): 58-. |
| [10] | 夏戈明;史立哲;周文;沈恒丰. 轻量级RFID双向通信认证协议优化方案[J]. , 2014, 14(2): 0-0. |
| [11] | 李明;王赛;李亮;严文涛. 边信道攻击防范措施的研究[J]. , 2013, 13(Z): 0-0. |
| [12] | 秦文仙;王琼宵;高能;王跃武. 对SIP认证协议的安全性分析与改进[J]. , 2013, 13(10): 0-0. |
| [13] | 黄世中;羊红光. NAF编码方法的分析与应用[J]. , 2012, 12(5): 0-0. |
| [14] | 向永谦;陈建华. 一种基于身份的三方认证密钥交换协议[J]. , 2012, 12(11): 0-0. |
| [15] | 蒋天发;王维虎;蒋巍. 基于TCP/IP应用层密码认证协议的研究[J]. , 2011, 11(5): 0-0. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 593
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 646
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||