信息网络安全 ›› 2018, Vol. 18 ›› Issue (10): 51-61.doi: 10.3969/j.issn.1671-1122.2018.10.008
基于椭圆曲线密码的RFID系统安全认证协议研究
- 江西理工大学信息工程学院 ,江西赣州 341000
-
收稿日期:2018-08-30出版日期:2018-10-10发布日期:2020-05-11 -
作者简介:作者简介:张小红(1966—),女,河北,教授,博士,主要研究方向为非线性动力学、视频保密通信;郭焰辉(1993—),男,福建,硕士研究生,主要研究方向为密码学、物联网技术。
-
基金资助:国家自然科学基金[61763017];江西省自然科学基金[20161BAB202053,20161BAB206145];江西省研究生创新专项资金[YC2016-S318]
Research on RFID System Security Authentication Protocol Based on Elliptic Curve Cryptography
- School of Information Engineering, Jiangxi University of Science and Technology, Ganzhou Jiangxi 341000,China
-
Received:2018-08-30Online:2018-10-10Published:2020-05-11
摘要:
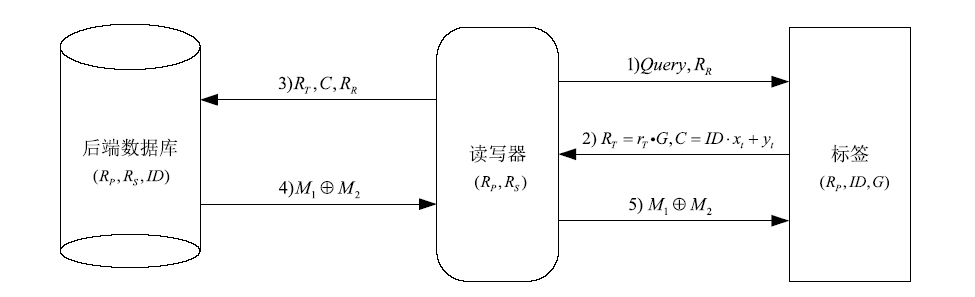
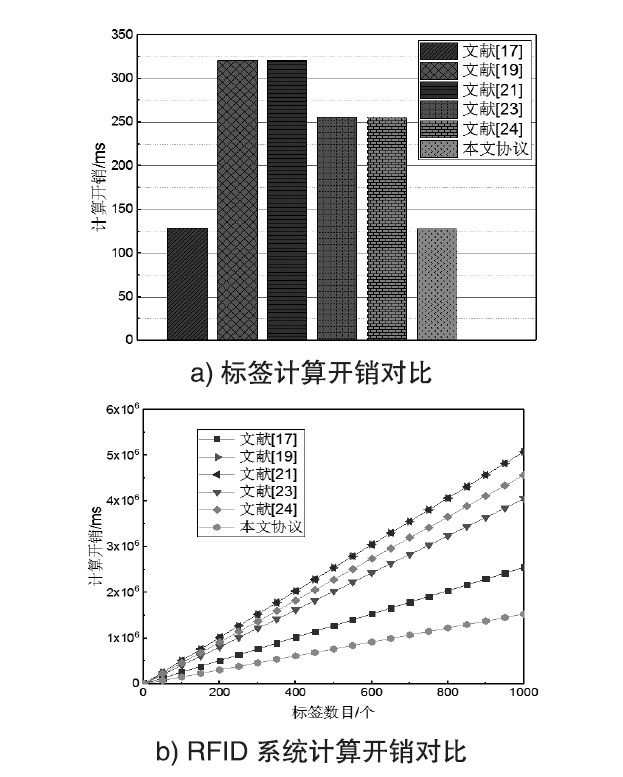
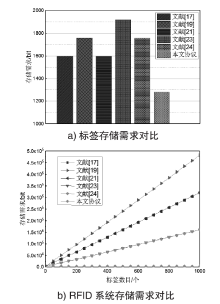
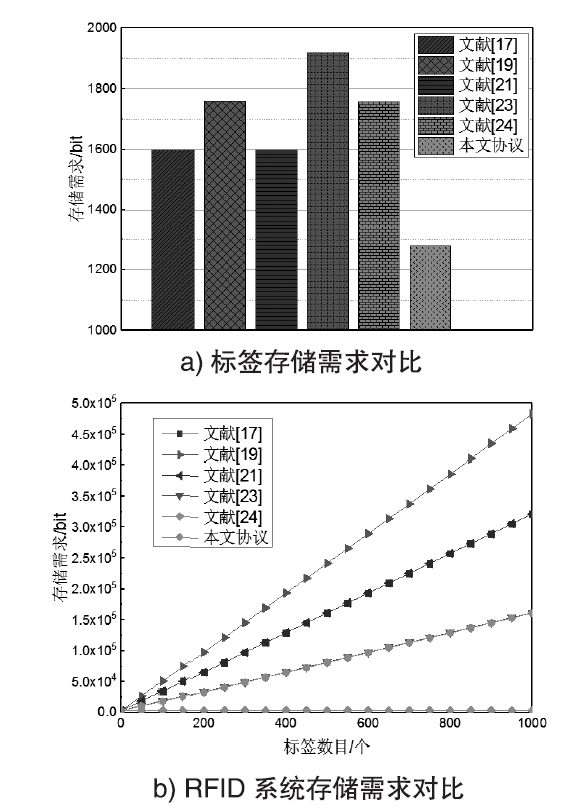
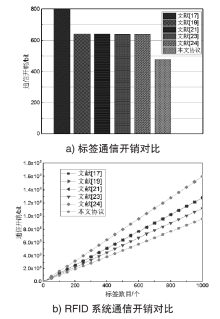
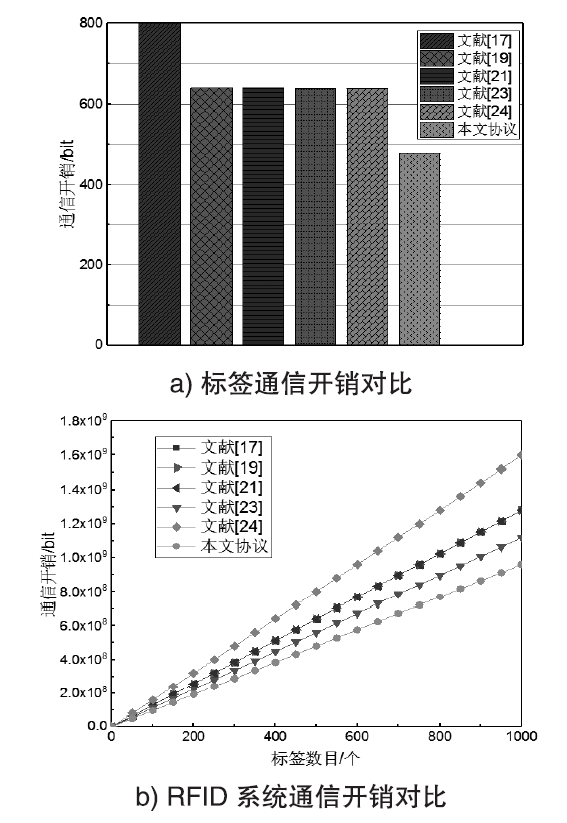
随着RFID技术在军事、金融、公共安全等领域的广泛应用,人们对RFID系统的安全性提出更高的要求。文章利用椭圆曲线密码(ECC)密钥短、安全性高且存储空间小的特点,设计了一种基于ECC的RFID系统双向认证协议,并用BAN逻辑形式化分析和证明了该协议能够达到预期的安全目标。与其他同类应用协议相比,该协议在抵抗跟踪攻击、拒绝服务攻击、重传攻击以及假冒攻击等方面均有较好的可信度,且能满足双向认证性、机密性、匿名性和前向安全性。该协议所需椭圆曲线点乘运算次数为3次,相比其他协议可减少60%的标签计算开销,RFID系统的执行效率可提高70%,可适用于军事物流管理及涉密文件保密等关键领域。
中图分类号:
引用本文
张小红, 郭焰辉. 基于椭圆曲线密码的RFID系统安全认证协议研究[J]. 信息网络安全, 2018, 18(10): 51-61.
Xiaohong ZHANG, Yanhui GUO. Research on RFID System Security Authentication Protocol Based on Elliptic Curve Cryptography[J]. Netinfo Security, 2018, 18(10): 51-61.
| [1] | KUANG Guofang, SUN Zhaofeng.The Application of Management Information System in Internet of Things Based on RFID Technology[J]. Sensors & Transducers, 2013, 154(7): 103-112. |
| [2] | ZHANG Yuting, YAN Chenghua.Research on RFID Authentication Technology Based on Two-way Authentication Protocol[J].Netinfo Security, 2016, 16(1): 64-69. |
| 张玉婷, 严承华. 一种基于双向认证协议的RFID标签认证技术研究[J]. 信息网络安全, 2016, 16(1): 64-69. | |
| [3] | QI Saiyu, ZHENG Yuanqing, LI Mo, et al.Secure and Private RFID-enabled Third-party Supply Chain Systems[J]. IEEE Transactions on Computers, 2016, 65(11): 3413-3426. |
| [4] | JIANG Zhengjun, TIAN Haibo, ZHANG Fangguo.Survey on PUF-based RFID Anti-counterfeiting Techniques[J].Netinfo Security, 2016 ,16(4): 38-43. |
| 蒋政君, 田海博, 张方国. 基于PUF的RFID防伪技术研究综述[J]. 信息网络安全, 2016 , 16(4): 38-43. | |
| [5] | LEI Miao.Research on RFID System Security Protocol[D]. Beijing:Beijing University Of Posts and Telecommunications, 2015. |
| 雷淼. RFID系统安全协议研究[D]. 北京:北京邮电大学, 2015. | |
| [6] | MA Qing, GUO Yajun, ZENG Qingjiang, et al.A New Ultra-lightweight RFID Mutual Authentication Protocol[J].Netinfo Security, 2016, 16(5): 44-50. |
| 马庆, 郭亚军,曾庆江, 等. 一种新的超轻量级RFID双向认证协议[J]. 信息网络安全, 2016 ,16(5): 44-50. | |
| [7] | KOBLITZ N.Elliptic Curve Crypto Systems[J]. Mathematics of Computation, 1987, 48(177): 203-209. |
| [8] | MILLER V S.Use of Elliptic Curves in Cryptography[J]. Lecture Notes in Computer Science, 1985, 218(1): 417-426. |
| [9] | CHEN Wei.Design and Hardware Implementation of ECC Algorithm Based on Jacobi Projective Coordinate System[D]. Xi’an: Xidian University,2016. |
| 陈威. 基于雅可比加重射影坐标系的ECC算法设计及硬件实现[D]. 西安:西安电子科技大学, 2016. | |
| [10] | CHEN Junjie.Research and Design of ECC Encryption and Decryption Algorithm Based on FPGA[D]. Xi’an: Xi’an University of Posts & Telecommunications, 2016. |
| 陈俊杰. 基于FPGA的ECC加解密算法研究及设计[D]. 西安:西安邮电大学, 2016. | |
| [11] | TUYLS P, BATINA L.RFID-Tags for Anti-counterfeiting[C]// RSA. The 2006 Cryptographers' Track at the RSA Conference on Topics in Cryptology, February 13 - 17, 2006, San Jose, CA,USA. Heidelberg: Springer-Verlag Berlin, 2006: 115-131. |
| [12] | SCHNORR C P.Efficient Identification and Signatures for Smart Cards[M]// Springer: Advances in Cryptology — EUROCRYPT ’89. Heidelberg : Springer, Berlin, Heidelberg ,1990: 239-252. |
| [13] | BATINA L, GUAJARDO J, KERINS T, et al.Public-key Cryptography for RFID-tags[C]//IEEE. The Fifth Annual IEEE International Conference on Pervasive Computing and Communications Workshops, March 19-23,2007, White Plains, NY, USA.NJ:IEEE, 2007: 217-222. |
| [14] | OKAMOTO T. Provably Secure and Practical Identification Schemes and Corresponding Signature Schemes[EB/OL]. |
| [15] | LEE Y K, BATINA L, VERBAUWHEDE I.EC-RAC (ECDLP-based Randomized Access Control): Provably Secure RFID Authentication Protocol[C]//IEEE. 2018 IEEE International Conference on RFID, April 16-17, 2008, Las Vegas, NV, USA.NJ:IEEE, 2008: 97-104. |
| [16] | ZHANG Xinglei, LI Linsen, WU Yue, et al.An ECDLP-based Randomized Key RFID Authentication protocol[C]//IEEE. 2011 International Conference on Network Computing and Information Security, May 14-15, Guilin, China. NJ:IEEE, 2011: 146-149. |
| [17] | CHOU J S.An Efficient Mutual Authentication RFID Scheme Based on Elliptic Curve Ccryptography[J].Journal of Supercomputing, 2014, 70(1): 75-94. |
| [18] | ZHANG Zezhong, QI Qingqing.An Efficient RFID Authentication Protocol to Enhance Patient Medication Safety Using Elliptic Curve Cryptography[J]. Journal of Medical Systems, 2014, 38(5): 47. |
| [19] | LIAO Yipin, HSIAO C M.A Secure ECC-based RFID Authentication Scheme Integrated with ID-verifier Transfer Protocol[J]. Ad Hoc Networks, 2014, 18(7): 133-146. |
| [20] | ZHAO Zhenguo.A Secure RFID Authentication Protocol for Healthcare Environments Using Elliptic Curve Cryptosystem[J]. Journal of Medical Systems, 2014, 38(5): 46. |
| [21] | HE Debiao, KUMAR N, CHILAMKURTI N, et al.Lightweight ECC-based RFID Authentication Integrated with an ID Verifier Transfer Protocol[J]. Journal of Medical Systems, 2014, 38(10): 1-6. |
| [22] | LEE C I, CHIEN H Y.An Elliptic Curve Cryptography-based RFID Authentication Securing E-health System[J]. International Journal of Distributed Sensor Networks, 2015, 2015(5): 1-7. |
| [23] | JIN Chunhua, XU Chunxiang, ZHANG Xiaojun, et al.A Secure RFID Mutual Authentication Protocol for Healthcare Environments Using Elliptic Curve Cryptography[J]. Journal of Medical Systems, 2015, 39(3): 24. |
| [24] | ALAMR A A, KAUSAR F, KIM J, et al.A Secure ECC-based RFID Mutual Authentication Protocol for Internet of Things[J]. Journal of Supercomputing, 2018,74(9): 4281-4294. |
| [25] | Qian Q, Jia Y L, Zhang R.A lightweight RFID security protocol based on elliptic curve cryptography[J]. International Journal of Network Security, 2016, 18(2): 354-361. |
| [26] | GÓDOR G, GICZI N, IMRE S. Elliptic Curve Cryptography-based Mutual Authentication Protocol for Low Computational Capacity RFID Systems-performance Analysis by Simulations[C]//IEEE. 2010 IEEE International Conference on Wireless Communications, Networking and Information Security, June 25-27, 2010, Beijing, China. NJ:IEEE, 2010: 650-657. |
| [1] | 韦永霜, 陈建华, 韦永美. 基于椭圆曲线密码的RFID/NFC安全认证协议[J]. 信息网络安全, 2019, 19(12): 64-71. |
| [2] | 马利民, 张伟, 宋莹. 一种基于一次性口令的增强Kerberos协议方法及其形式化分析[J]. 信息网络安全, 2019, 19(10): 57-64. |
| [3] | 郝文江, 宋斐, 万月亮. 可穿戴单警装备安全认证协议研究[J]. 信息网络安全, 2018, 18(9): 25-29. |
| [4] | 周志彬, 张少波, 罗恩韬, 李超良. 一种无可信第三方的批量RFID所有权转移协议[J]. 信息网络安全, 2018, 0(6): 18-27. |
| [5] | 李智聪, 周治平. 物联网中增强安全的RFID认证协议[J]. 信息网络安全, 2018, 0(1): 80-87. |
| [6] | 王萍, 周治平. 一种基于云的RFID所有权转移协议的改进[J]. 信息网络安全, 2017, 17(8): 60-68. |
| [7] | 杨玉龙, 彭长根, 郑少波, 朱义杰. 基于移动智能终端的超轻量级移动RFID安全认证协议[J]. 信息网络安全, 2017, 17(5): 22-27. |
| [8] | 贾徽徽, 王潮, 顾健, 陆臻. 基于Grover量子中间相遇搜索算法的ECC攻击错误bit的修正[J]. 信息网络安全, 2016, 16(6): 28-34. |
| [9] | 张言胜, 汪学明, 仇各各. 一种新的动态门限数字签名方案研究[J]. 信息网络安全, 2016, 16(6): 62-67. |
| [10] | 马庆, 郭亚军, 曾庆江, 徐铎. 一种新的超轻量级RFID双向认证协议[J]. 信息网络安全, 2016, 16(5): 44-50. |
| [11] | 陈宇航, 贾徽徽, 姜丽莹, 王潮. 基于Grover算法的ECC扫描式攻击[J]. 信息网络安全, 2016, 16(2): 28-32. |
| [12] | 张玉婷, 严承华. 一种基于双向认证协议的RFID标签认证技术研究[J]. 信息网络安全, 2016, 16(1): 64-69. |
| [13] | 杨元原, 陆臻, 顾健. RFID安全协议追踪攻击的形式化分析[J]. 信息网络安全, 2015, 15(9): 25-28. |
| [14] | 吴潇, 常成, 覃文杰, 程久军. 基于RFID和数字水印技术的标签防伪验证方法[J]. 信息网络安全, 2015, 15(8): 26-34. |
| [15] | 段然, 徐乃阳, 胡爱群. 基于形式化分析工具的认证协议安全性研究[J]. 信息网络安全, 2015, 15(7): 71-76. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||