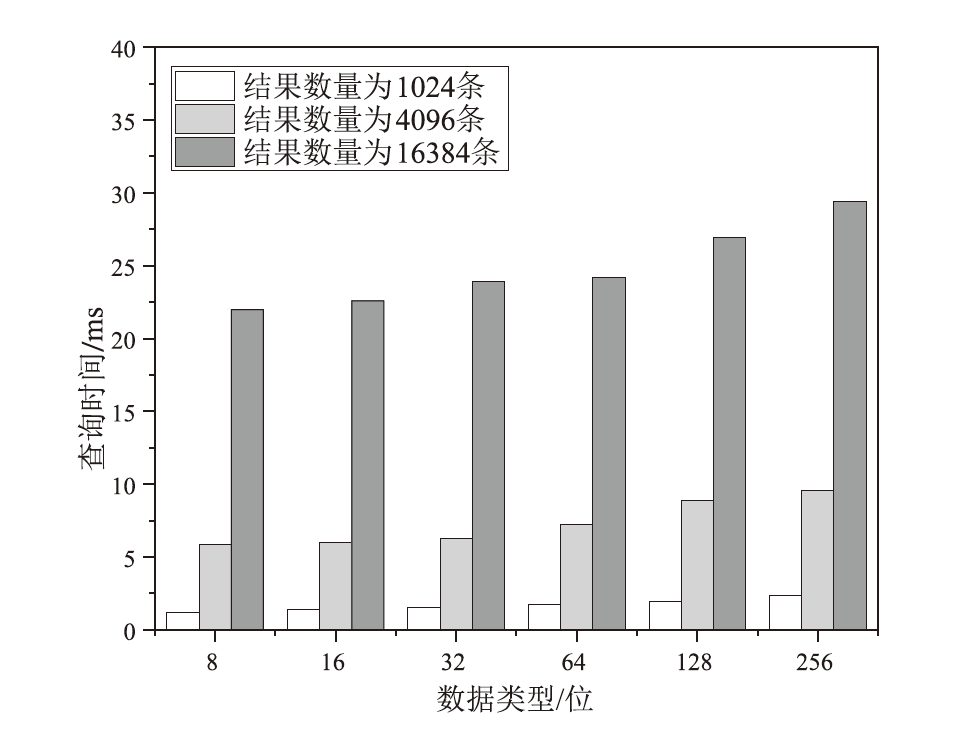
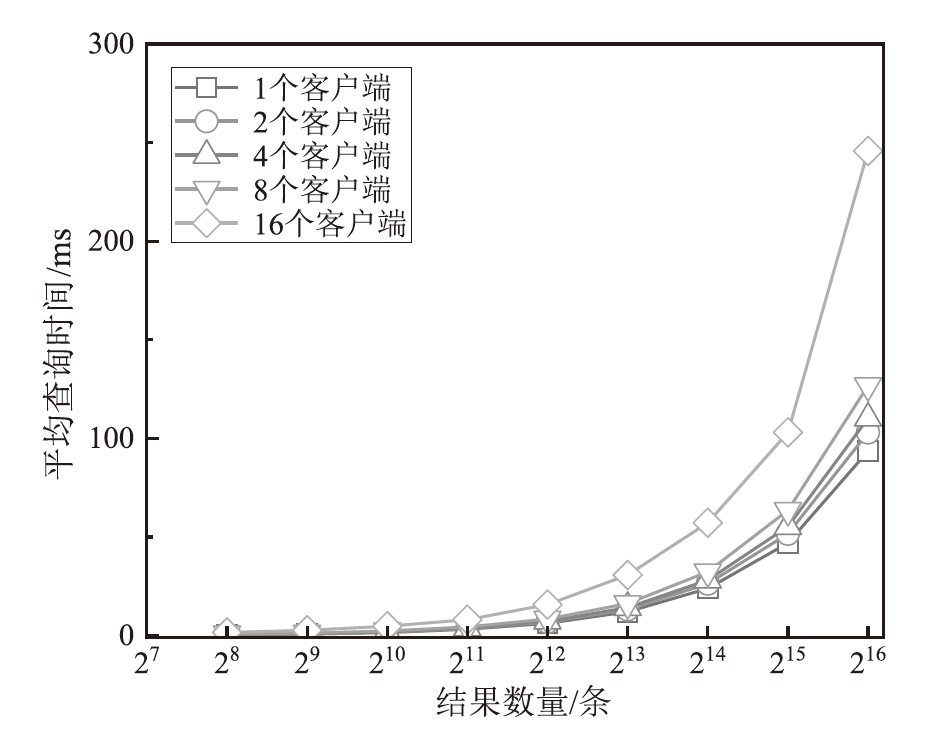
信息网络安全 ›› 2025, Vol. 25 ›› Issue (11): 1718-1731.doi: 10.3969/j.issn.1671-1122.2025.11.006
基于可信执行环境的加密数据库索引安全增强方案
1.中国科学技术大学网络空间安全学院 合肥 230026 2.中国科学技术大学网络信息中心 合肥 230026 3.鹏城实验室 深圳 518053
-
收稿日期:2025-04-01出版日期:2025-11-10发布日期:2025-12-02 -
通讯作者:王峰wf0229@ustc.edu.cn -
作者简介:薛开平(1980—),男,江苏,教授,博士,CCF会员,主要研究方向为下一代网络体系结构、网络安全|张淳一(2000—),男,河南,硕士研究生,主要研究方向为网络安全、应用密码学|柳枫(1995—),男,安徽,助理研究员,博士,主要研究方向为网络安全、应用密码学|王峰(1989—),男,陕西,实验师,硕士,主要研究方向为身份认证、访问控制、区块链 -
基金资助:国家自然科学基金(62372425);中国科学院青年创新促进会优秀会员支持项目(Y202093)
Security-Enhanced Index Scheme in Encrypted Database Based on Trusted Execution Environment
XUE Kaiping1,2, ZHANG Chunyi1, LIU Feng3, WANG Feng2( )
)
1. School of Cyber Science and Technology ,University of Science and Technology of China Hefei 230026, China 2. Network and Information Center ,University of Science and Technology of China Hefei 230026, China 3. Pengcheng Laboratory Shenzhen 518053, China
-
Received:2025-04-01Online:2025-11-10Published:2025-12-02
摘要:
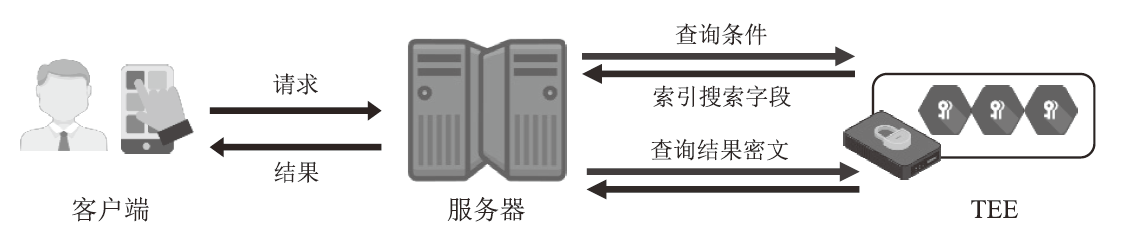
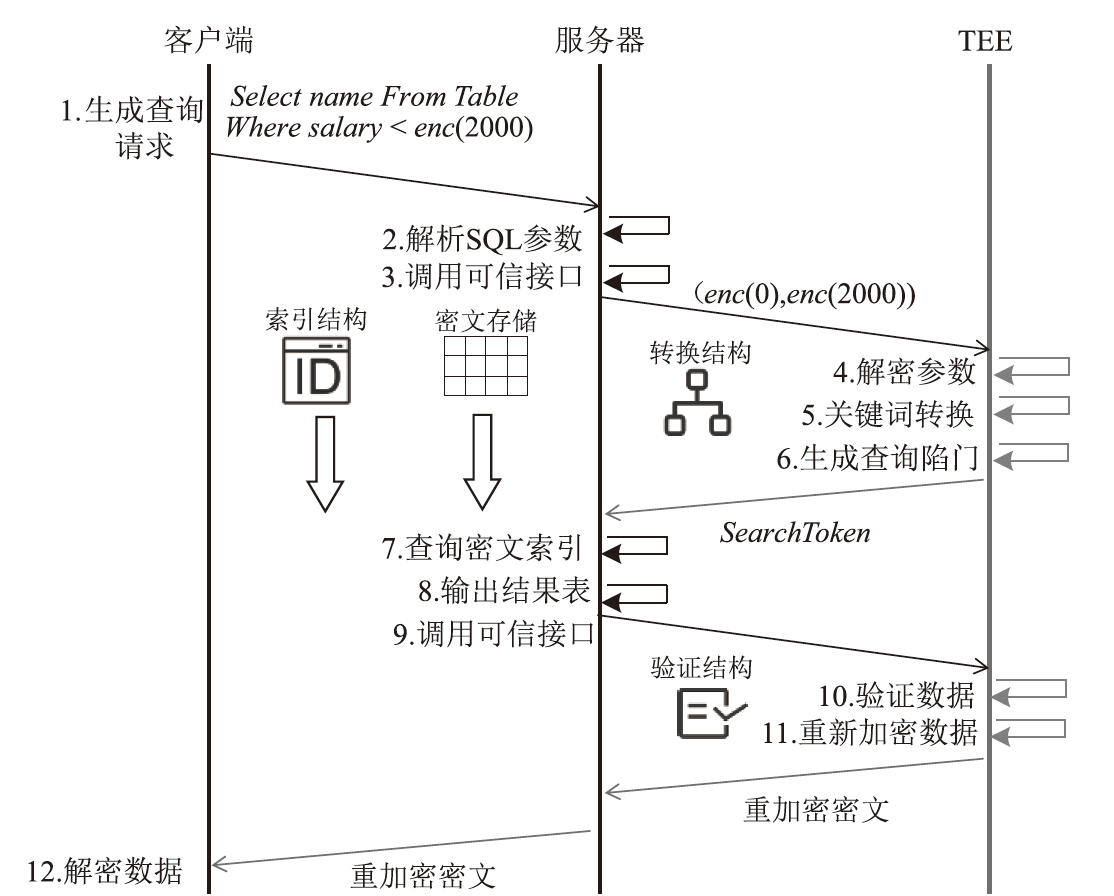
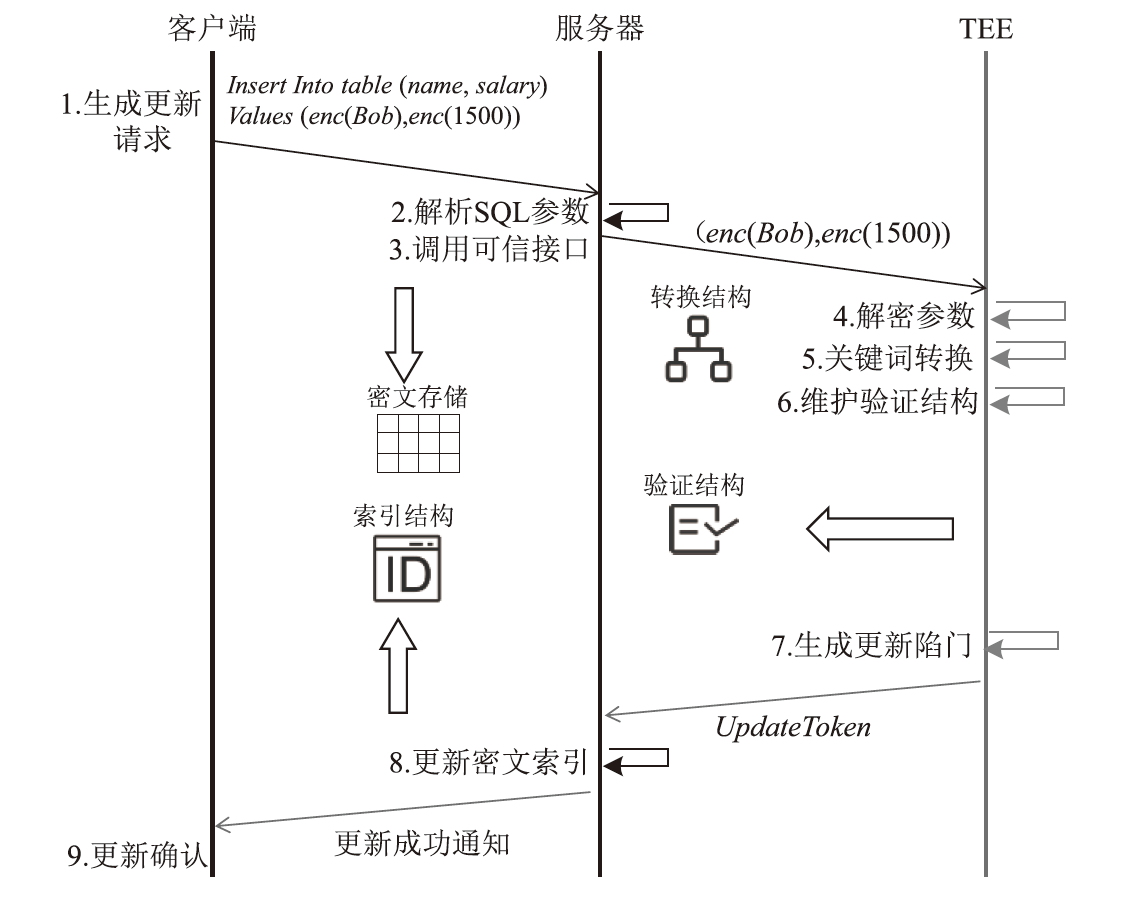
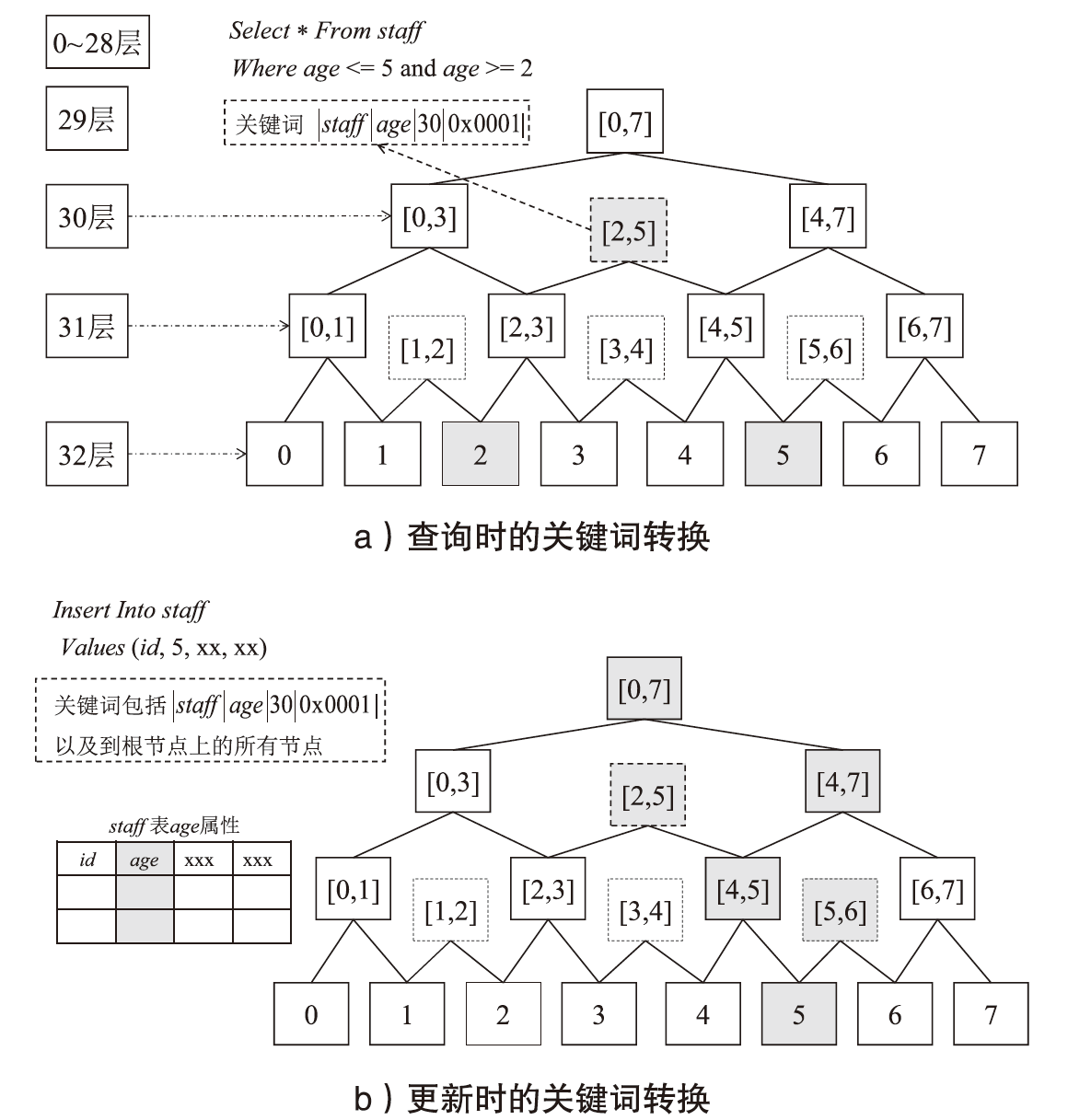
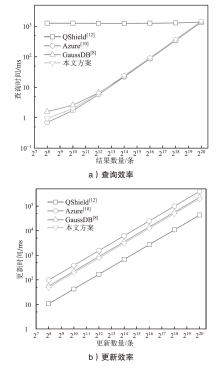
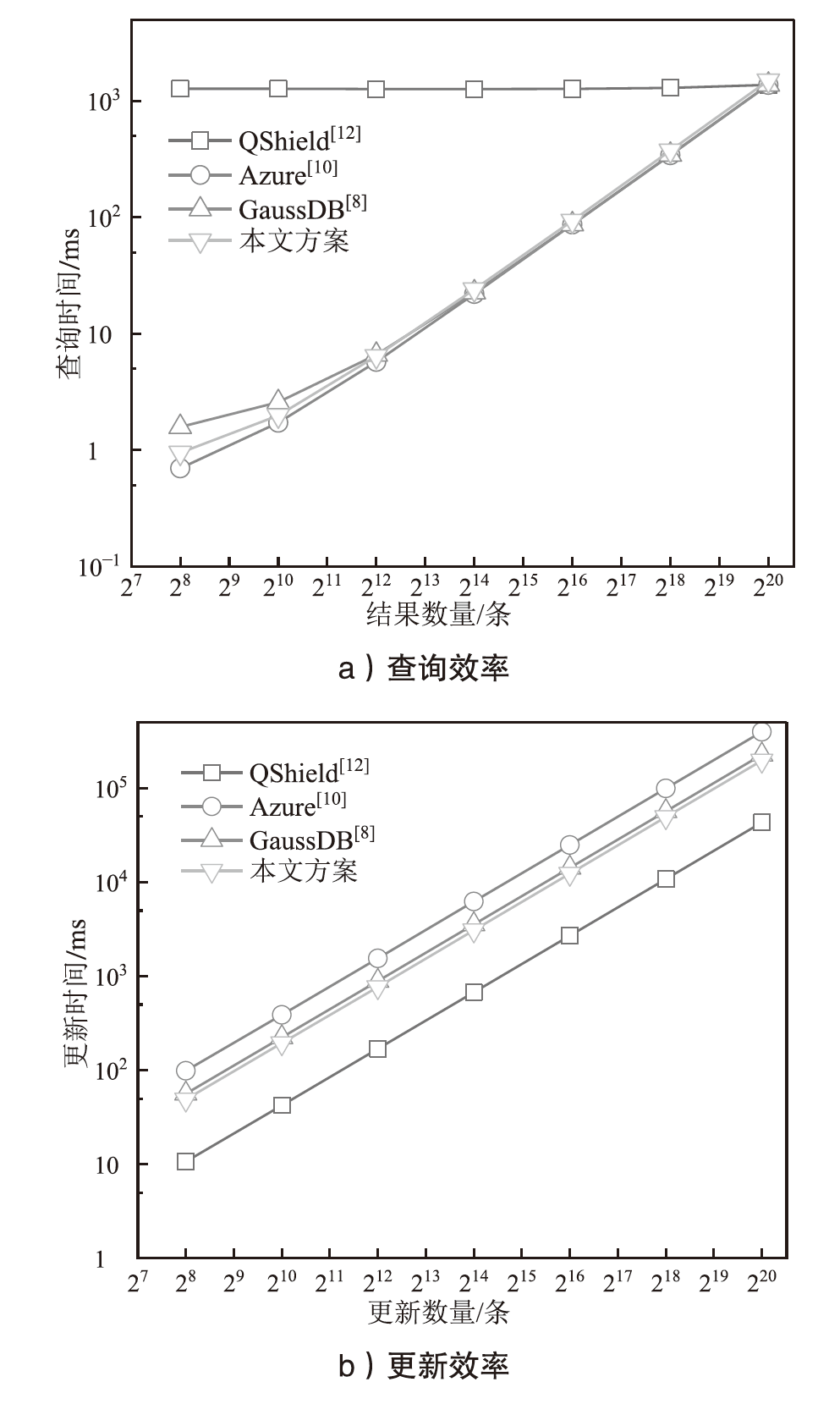
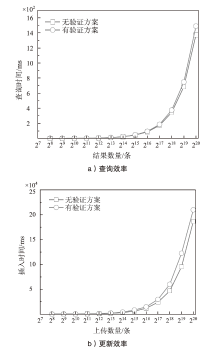
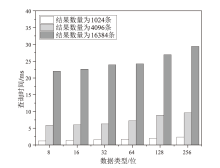
基于可信执行环境的加密数据库方案相较于其他技术路径具有显著的性能优势,然而在索引结构设计方面仍面临安全挑战。现有方案存在数据顺序信息泄露与解密接口滥用等风险。针对上述问题,文章提出一种基于可信执行环境的加密数据库索引安全增强方案。该方案采用基于动态对称可搜索加密的索引结构,在加快等值查询与范围查询速度的同时,确保索引结构的信息泄露可控。此外,文章设计了一种嵌入索引的验证机制,以防止恶意攻击者通过任意调用接口获取敏感数据的明文信息。安全性分析表明,文章所提方案在保护数据隐私的同时,能够有效抵御恶意接口调用攻击。在Intel SGX环境下的性能测试结果表明,与无索引方案相比,文章所提方案显著提升了查询效率;与存在信息泄露的索引方案相比,文章所提方案在查询效率上保持相当水平,并在更新效率、验证机制轻量化以及可信区内数据处理量等指标上展现出良好的可行性。
中图分类号:
引用本文
薛开平, 张淳一, 柳枫, 王峰. 基于可信执行环境的加密数据库索引安全增强方案[J]. 信息网络安全, 2025, 25(11): 1718-1731.
XUE Kaiping, ZHANG Chunyi, LIU Feng, WANG Feng. Security-Enhanced Index Scheme in Encrypted Database Based on Trusted Execution Environment[J]. Netinfo Security, 2025, 25(11): 1718-1731.
| [1] | POPA R A, REDFIELD C M S, ZELDOVICH N, et al. CryptDB: Protecting Confidentiality with Encrypted Query Processing[C]// ACM. The Twenty-Third ACM Symposium on Operating Systems Principles. New York: ACM, 2011: 85-100. |
| [2] | CHI Jialin, FENG Dengguo, ZHANG Min, et al. Advances in Privacy-Preserving Ciphertext Retrieval[J]. Journal of Electronics & Information Technology, 2024, 46(5): 1546-1569. |
| 迟佳琳, 冯登国, 张敏, 等. 隐私保护密文检索技术研究进展[J]. 电子与信息学报, 2024, 46(5): 1546-1569. | |
| [3] |
FANG Wenjing, CAO Shunde, HUA Guojin, et al. SecretFlow-SCQL: A Secure Collaborative Query Platform[J]. Proceedings of the VLDB Endowment, 2024, 17(12): 3987-4000.
doi: 10.14778/3685800.3685821 URL |
| [4] |
SHARMA S, LI Yin, MEHROTRA S, et al. Prism: Privacy-Preserving and Verifiable Set Computation over Multi-Owner Secret Shared Outsourced Databases[J]. IEEE Transactions on Dependable and Secure Computing, 2024, 21(3): 1355-1371.
doi: 10.1109/TDSC.2023.3279356 URL |
| [5] | ZHANG Zhou, BIAN Song, ZHAO Zian, et al. ArcEDB: An Arbitrary-Precision Encrypted Database via (Amortized) Modular Homomorphic Encryption[C]// ACM. ACM SIGSAC Conference on Computer and Communications Security 2024. New York: ACM, 2024: 4613-4627. |
| [6] |
MA Chengyan, LU Di, LYU Chaoyue, et al. BiTDB: Constructing a Built-In TEE Secure Database for Embedded Systems[J]. IEEE Transactions on Knowledge and Data Engineering, 2024, 36(9): 4472-4485.
doi: 10.1109/TKDE.2024.3380367 URL |
| [7] | PRIEBE C, VASWANI K, COSTA M. EnclaveDB: A Secure Database Using SGX[C]// IEEE. 2018 IEEE Symposium on Security and Privacy (S&P 2018). New York: IEEE, 2018: 264-278. |
| [8] |
ZHU Jinwei, CHENG Kun, LIU Jiayang, et al. Full Encryption[J]. Proceedings of the VLDB Endowment, 2021, 14(12): 2811-2814.
doi: 10.14778/3476311.3476351 URL |
| [9] |
WANG Sheng, LI Yiran, LI Huorong, et al. Operon: An Encrypted Database for Ownership-Preserving Data Management[J]. Proceedings of the VLDB Endowment, 2022, 15(12): 3332-3345.
doi: 10.14778/3554821.3554826 URL |
| [10] | ANTONOPOULOS P, ARASU A, SINGH K D, et al. Azure SQL Database Always Encrypted[C]// ACM. The 2020 ACM SIGMOD International Conference on Management of Data. New York: ACM, 2020: 1511-1525. |
| [11] | SEAH R, KHU D, HOOVER A, et al. LAMA: Leakage Abuse Attacks Against Microsoft Always Encrypted[EB/OL]. (2024-08-21)[2025-03-10]. https://eprint.iacr.org/2024/1308. |
| [12] |
CHEN Yaxing, ZHENG Qinghua, YAN Zheng, et al. QShield: Protecting Outsourced Cloud Data Queries with Multi-User Access Control Based on SGX[J]. IEEE Transactions on Parallel and Distributed Systems, 2021, 32(2): 485-499.
doi: 10.1109/TPDS.71 URL |
| [13] | CHEN Yaxing, ZHENG Qinghua, YAN Zheng. Efficient Bi-Objective SQL Optimization for Enclaved Cloud Databases with Differentially Private Padding[J]. ACM Transactions on Database Systems, 2023, 48(2): 1-40. |
| [14] | ESKANDARIAN S, ZAHARIA M. ObliDB: Oblivious Query Processing for Secure Databases[C]// ACM. The 2019 International Conference on Very Large DataBases (VLDB). New York: ACM, 2019: 169-183. |
| [15] | ZHENG Wenting, DAVE A, BEEKMAN J G, et al. Opaque: An Oblivious and Encrypted Distributed Analytics Platform[C]// USENIX. The 2017 USENIX Symposium on Network System Design and Implementation (NSDI). Berkeley: USENIX, 2017: 283-298. |
| [16] | SONG D X, WAGNER D, PERRIG A. Practical Techniques for Searches on Encrypted Data[C]// IEEE. 2000 IEEE Symposium on Security and Privacy(S&P 2000). New York: IEEE, 2000: 44-55. |
| [17] | BOST R. ∑oϕoς: Forward Secure Searchable Encryption[C]// ACM. The 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 1143-1154. |
| [18] |
SONG Xiangfu, DONG Changyu, YUAN Dandan, et al. Forward Private Searchable Symmetric Encryption with Optimized I/O Efficiency[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 17(5): 912-927.
doi: 10.1109/TDSC.8858 URL |
| [19] | DEMERTZIS I, PAPADOPOULOS S, PAPAPETROU O, et al. Practical Private Range Search Revisited[C]// ACM. The 2016 International Conference on Management of Data. New York: ACM, 2016: 185-198. |
| [20] | KAMARA S, MOATAZ T. SQL on Structurally-Encrypted Databases[C]// Springer. The 24th International Conference on the Theory and Application of Cryptology and Information Security(Cryptology-ASIACRYPT 2018). Heidelberg: Springer, 2018: 149-180. |
| [1] | 拾以娟, 周丹平, 范磊, 刘茵. 基于可信执行环境的安全多方计算协议[J]. 信息网络安全, 2025, 25(9): 1439-1446. |
| [2] | 郝萌, 李佳勇, 杨洪伟, 张伟哲. 异构CPU-GPU系统机密计算综述[J]. 信息网络安全, 2025, 25(11): 1658-1672. |
| [3] | 关志, 胡建斌, 李悦, 陈钟. 基于可信执行环境的区块链技术与应用综述[J]. 信息网络安全, 2025, 25(11): 1673-1690. |
| [4] | 赵波, 吕佳敏, 王一琁. 一种面向容器生命周期的多维安全度量架构[J]. 信息网络安全, 2025, 25(11): 1745-1761. |
| [5] | 王亚杰, 陆锦标, 李宇航, 范青, 张子剑, 祝烈煌. 基于可信执行环境的联邦学习分层动态防护算法[J]. 信息网络安全, 2025, 25(11): 1762-1773. |
| [6] | 卢笛, 刘玉佳, 吕超越, 孙梦娜, 张清文, 杨力. 一种云原生TEE服务共享机制[J]. 信息网络安全, 2025, 25(11): 1774-1791. |
| [7] | 金娃, 秦宇, 刘菁润, 尚科彤, 贾梦涵, 林江南. 基于机密计算平台的TEE和TPM硬件可信信道构建方案[J]. 信息网络安全, 2025, 25(11): 1792-1810. |
| [8] | 胡宇义, 蔡炜, 陈竞凡, 刘莫寒, 王鹃, 何运. 面向机密容器的统一远程证明机制研究[J]. 信息网络安全, 2025, 25(11): 1811-1823. |
| [9] | 余发江, 王朝州. TrustZone半虚拟化与容器化实现机制[J]. 信息网络安全, 2025, 25(10): 1523-1536. |
| [10] | 孙钰, 熊高剑, 刘潇, 李燕. 基于可信执行环境的安全推理研究进展[J]. 信息网络安全, 2024, 24(12): 1799-1818. |
| [11] | 王南, 袁也, 杨浩然, 文周之, 苏明, 刘晓光. 环保大数据在区块链中的隐私计算[J]. 信息网络安全, 2024, 24(10): 1515-1527. |
| [12] | 唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65. |
| [13] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [14] | 尤玮婧, 刘丽敏, 马悦, 韩东. 基于安全硬件的云端数据机密性验证方案[J]. 信息网络安全, 2020, 20(12): 1-8. |
| [15] | 刘志娟, 高隽, 丁启枫, 王跃武. 移动终端TEE技术进展研究[J]. 信息网络安全, 2018, 18(2): 84-91. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||