信息网络安全 ›› 2021, Vol. 21 ›› Issue (10): 41-47.doi: 10.3969/j.issn.1671-1122.2021.10.006
基于融合CNN与LSTM的DGA恶意域名检测方法
- 中国刑事警察学院,沈阳 110854
-
收稿日期:2021-06-17出版日期:2021-10-10发布日期:2021-10-14 -
通讯作者:徐国天 E-mail:xu_guo_tian888@163.com -
作者简介:徐国天(1978—),男,辽宁,副教授,硕士,主要研究方向为网络空间安全、电子数据取证|盛振威(1997—),男,湖北,硕士研究生,主要研究方向为网络空间安全 -
基金资助:中央高校基本科研业务费(3242017013);公安部软科学计划(2020LLYJXJXY031);公安部技术研究计划(2016JSYJB06);辽宁省自然科学基金(2019-ZD-0167);辽宁省自然科学基金(20180550841);辽宁省自然科学基金(2015020091);辽宁省社会科学规划基金(L16BFX012);辽宁网络安全执法协同创新中心资助项目(WXZX-201807010);辽宁省教育厅科学研究经费(LJK20072)
DGA Malicious Domain Name Detection Method Based on Fusion of CNN and LSTM
- Criminal Investigation Police University of China, Shenyang 110854, China
-
Received:2021-06-17Online:2021-10-10Published:2021-10-14 -
Contact:XU Guotian E-mail:xu_guo_tian888@163.com
摘要:
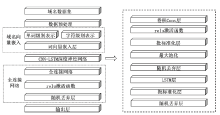
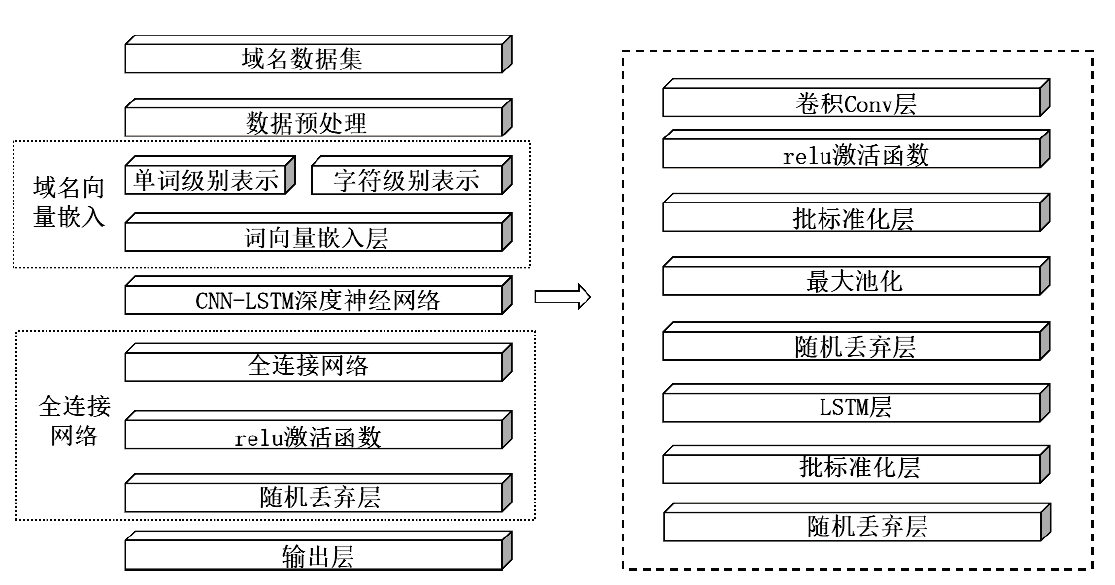
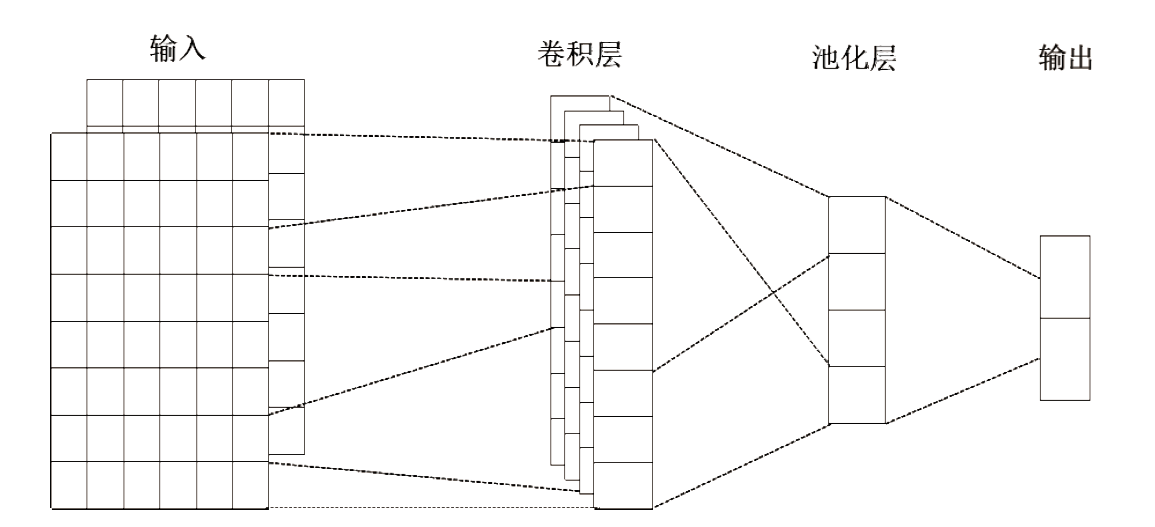
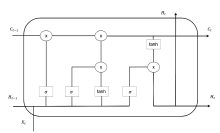
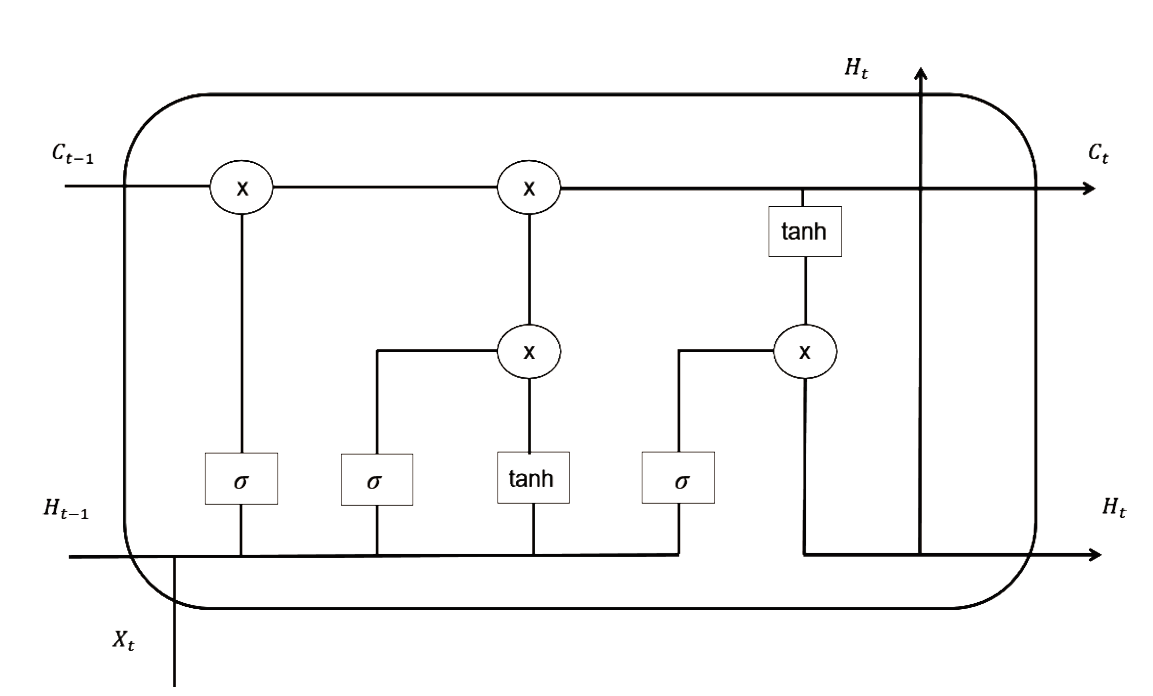
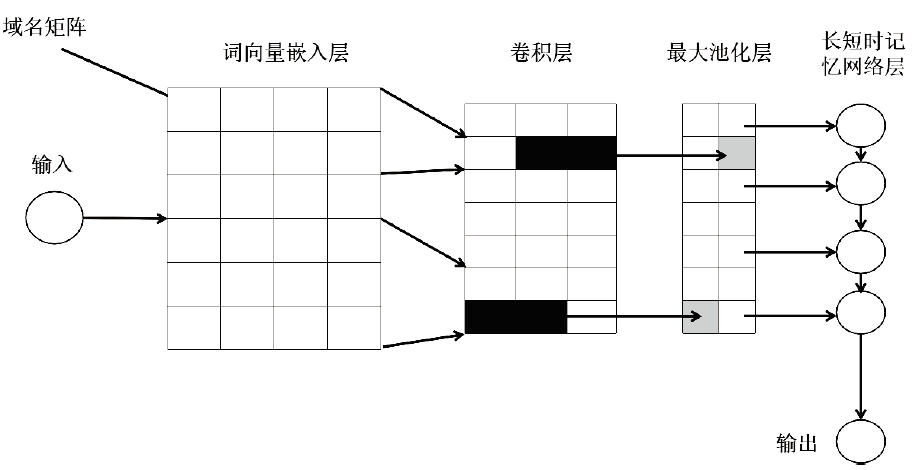
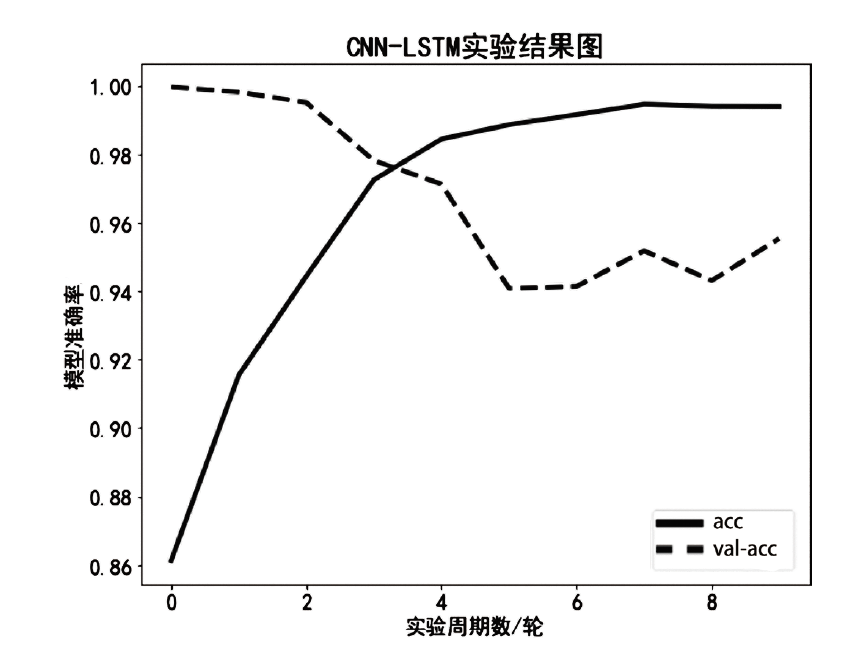
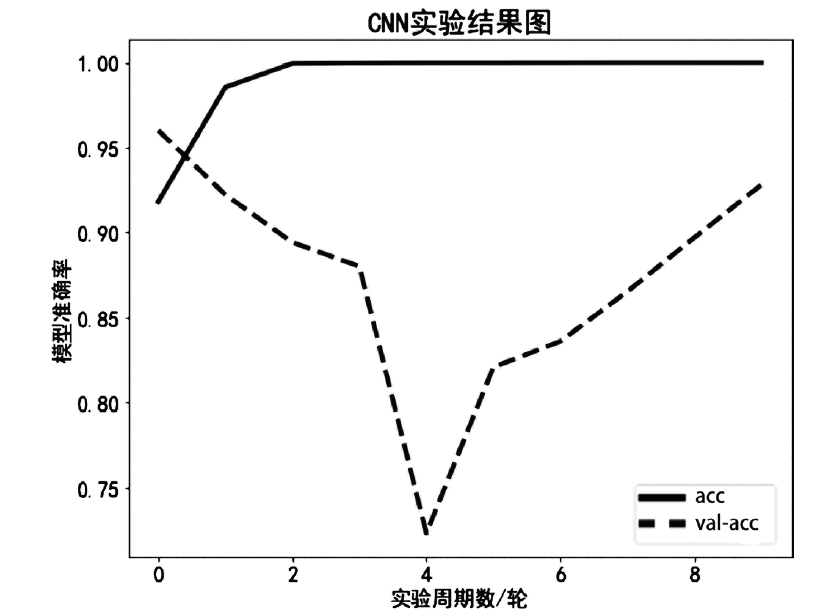
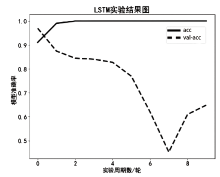
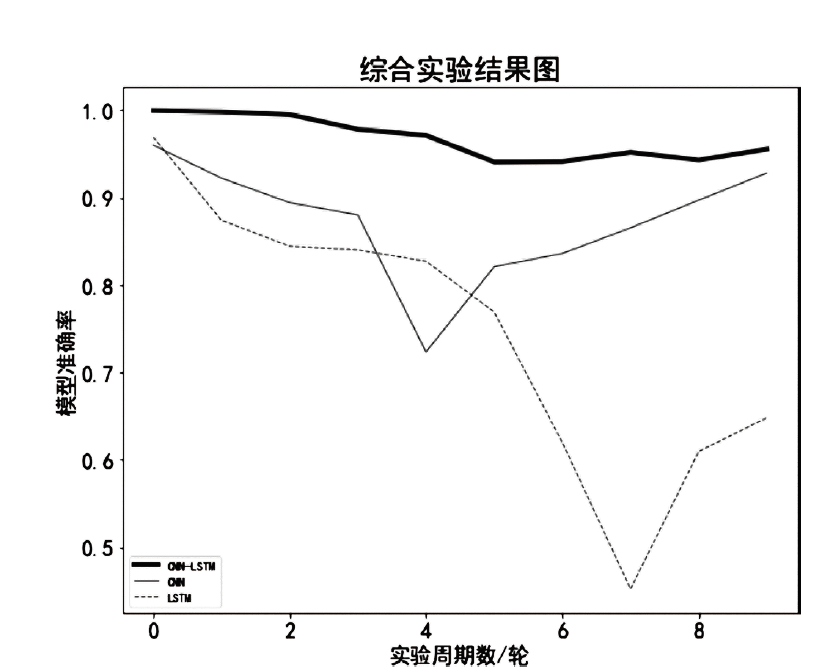
目前,恶意域名生成算法被广泛应用于各类网络攻击中,针对恶意域名检测中存在的特征工程效率低、域名编码维度过高、部分域名信息特征丢失等问题,文章提出一种基于融合卷积神经网络和长短期记忆网络的恶意域名检测深度学习模型。模型采用词向量嵌入方式对域名字符进行编码,构建一个密集向量,利用单词之间的相关性来进行相应编码。该方法有效解决了独热编码带来的稀疏矩阵和维度灾难等问题,缩短了字符的编码时间、提高了编码效率。该模型不仅可以提取域名信息中局部特征,还能有效提取域名字符间上下文关联性特征。实验结果表明,与传统恶意域名检测模式相比,文章方法可以获得更好的分类效果和检测率。
中图分类号:
引用本文
徐国天, 盛振威. 基于融合CNN与LSTM的DGA恶意域名检测方法[J]. 信息网络安全, 2021, 21(10): 41-47.
XU Guotian, SHENG Zhenwei. DGA Malicious Domain Name Detection Method Based on Fusion of CNN and LSTM[J]. Netinfo Security, 2021, 21(10): 41-47.
| [1] |
SINGH M, SINGH M, KAUR S. Detecting Bot-infected Machines Using DNS Fingerprinting[J]. Digital Investigation, 2019, 28(2):14-33.
doi: 10.1016/j.diin.2018.12.005 URL |
| [2] | GARCIA S, GRILL M, STIBOREK J, et al. An Empirical Comparison of Botnet Detection Methods[J]. Computers & Security, 2014, 32(45):100-123. |
| [3] | ZUO Yuanwei. Research on Malicious Domain Name Detection and Defense Based on Deep Learning and SDN Network[D]. Nanjing:Nanjing University of Posts and Telecommunications, 2020. |
| 左元威. 基于深度学习和SDN网络的恶意域名检测与防御的研究[D]. 南京:南京邮电大学, 2020. | |
| [4] | DRICHEL A, MEYER U, SCHÜPPEN S, et al. Making Use of NXt to Nothing: The Effect of Class Imbalances on DGA Detection Classifiers [C]//ICOSST. Proceedings of the 15th International Conference on Availability, August 12-16, 2020, Lahore, Pakistan. USA: Reliability and Security, 2020: 1-9. |
| [5] | FEILY M, SHAHRESTANI A, RAMADASS S. A Survey of Botnet and Botnet Detection [C]//IEEE. Third International Conference on Emerging Security Information, June 18-23, 2009, Athens, Greece. New York: IEEE, 2009: 268-273. |
| [6] |
SHARIFNYA R, ABADI M. Dfbotkiller: Domain-flux Botnet Detection Based on the History of Group Activities and Failures in DNS Traffic[J]. Digital Investigation, 2015, 12(5):15-26.
doi: 10.1016/j.diin.2014.11.001 URL |
| [7] | ZHOU Yonglin, LI Qingshan, MIAO Qidi, et al. DGA-based Botnet Detection Using DNS Traffic[J]. J. Internet Serv. Inf. Secur., 2013, 3(3/4):116-123. |
| [8] | ANTONAKAKIS M, PERDISCI R, NADJI Y, et al. From Throw-away Traffic to Bots: Detecting The Rise of DGA-based Malware [C]//IEEE. 21st USENIX Conference on Security Symposium, Auguest 8-10, 2012, Bellevue, WA, USA. New York: IEEE, 2012: 491-506. |
| [9] |
SHI Yong, CHEN Gong, LI Juntao. Malicious Domain Name Detection Based on Extreme Machine Learning[J]. Neural Processing Letters, 2018, 48(3):1347-1357.
doi: 10.1007/s11063-017-9666-7 URL |
| [10] | JIANG Hongling, DAI Junwei. DGA Malicious Domain Name Detection Method[J]. Journal of Beijing Information Science and Technology University (Natural Science Edition), 2019, 34(5):45-50. |
| 蒋鸿玲, 戴俊伟. DGA恶意域名检测方法[J]. 北京信息科技大学学报(自然科学版), 2019, 34(5):45-50. | |
| [11] | GU Zhaojun, YANG Wenjin, ZHOU Jingxian. A Small Sample DGA Malicious Domain Name Detection Method Based on Transfer Learning[EB/OL]. http://kns.cnki.net/kcms/detail/11.2127.TP.20200709.0928.008.html,2021-06-11. |
| 顾兆军, 杨文瑾, 周景贤. 基于迁移学习的小样本DGA恶意域名检测方法[EB/OL]. http://kns.cnki.net/kcms/detail/11.2127.TP.20200709.0928.008.html,2021-06-11. | |
| [12] | TOBIYAMA S, YAMAGUCHI Y, SHIMADA H, et al. Malware Detection with Deep Neural Network Using Process Behavior [C]//IEEE. 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), June 10-14, 2016, Atlanta, USA. New York: IEEE, 2016: 577-582. |
| [13] | WANG Zhiqiang, LI Shuhao, CHI Yaping, et al. Malicious DGA Domain Name Detection Based on Deep Learning[J]. Computer Engineering and Design, 2021, 42(3):601-606. |
| 王志强, 李舒豪, 池亚平, 等. 基于深度学习的恶意DGA域名检测[J]. 计算机工程与设计, 2021, 42(3):601-606. | |
| [14] |
EBRAHIMI M, SUEN C Y, ORMANDJIEVA O. Detecting Predatory Conversations in Social Media by Deep Convolutional Neural Networks[J]. Digital Investigation, 2016, 18(6):33-49.
doi: 10.1016/j.diin.2016.07.001 URL |
| [15] | LE Q, BOYDELL O, MAC N B, et al. Deep Learning at the Shallow End: Malware Classification for Non-domain Experts[J]. Digital Investigation, 2018, 26(9):118-126. |
| [16] | ZHANG You, YUAN Hang, WANG Jin, et al. YNU-HPCC at EmoInt-2017: Using a CNN-LSTM Model for Sentiment Intensity Prediction [C]//Association for Computational Linguistics. Proceedings of the 8th Workshop on Computational Approaches to Subjectivity, Sentiment and Social Media Analysis, September 7-11, 2017, Copenhagen, Denmark. USA: Association for Computational Linguistics, 2017: 200-204. |
| [17] | ZHOU Kang, WAN Liang, DING Hongwei. Malicious Domain Name Detection Based on AN and LSTM[J]. Computer Engineering and Applications, 2020, 56(4):92-98. |
| 周康, 万良, 丁红卫. 基于AN和LSTM的恶意域名检测[J]. 计算机工程与应用, 2020, 56(4):92-98. |
| [1] | 弋晓洋, 张健. 基于图像的网络钓鱼邮件检测方法研究[J]. 信息网络安全, 2021, 21(9): 52-58. |
| [2] | 李彦霖, 蔡满春, 芦天亮, 席荣康. 遗传算法优化CNN的网站指纹攻击方法[J]. 信息网络安全, 2021, 21(9): 59-66. |
| [3] | 朱新同, 唐云祁, 耿鹏志. 基于特征融合的篡改与深度伪造图像检测算法[J]. 信息网络安全, 2021, 21(8): 70-81. |
| [4] | 路宏琳, 王利明. 面向用户的支持用户掉线的联邦学习数据隐私保护方法[J]. 信息网络安全, 2021, 21(3): 64-71. |
| [5] | 郭烜臻, 潘祖烈, 沈毅, 陈远超. 一种基于被动DNS数据分析的DNS重绑定攻击检测技术[J]. 信息网络安全, 2021, 21(3): 87-95. |
| [6] | 潘孝勤, 杜彦辉. 基于混合特征和多通道GRU的伪造语音鉴别方法[J]. 信息网络安全, 2021, 21(10): 1-7. |
| [7] | 杨铭, 张健. 基于图像识别的恶意软件静态检测模型[J]. 信息网络安全, 2021, 21(10): 25-32. |
| [8] | 马骁, 蔡满春, 芦天亮. 基于CNN改进模型的恶意域名训练数据生成技术[J]. 信息网络安全, 2021, 21(10): 69-75. |
| [9] | 李桥, 龙春, 魏金侠, 赵静. 一种基于LMDR和CNN的混合入侵检测模型[J]. 信息网络安全, 2020, 20(9): 117-121. |
| [10] | 吴警, 芦天亮, 杜彦辉. 基于Char-RNN改进模型的恶意域名训练数据生成技术[J]. 信息网络安全, 2020, 20(9): 6-11. |
| [11] | 王文华, 郝新, 刘焱, 王洋. AI系统的安全测评和防御加固方案[J]. 信息网络安全, 2020, 20(9): 87-91. |
| [12] | 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. |
| [13] | 刘静, 张学谦, 刘全明. 混合Gabor的轻量级卷积神经网络的验证码识别研究[J]. 信息网络安全, 2020, 20(7): 77-84. |
| [14] | 罗峥, 张学谦. 基于思维进化算法优化S-Kohonen神经网络的恶意域名检测模型[J]. 信息网络安全, 2020, 20(6): 82-89. |
| [15] | 张永生, 王志, 武艺杰, 杜振华. 基于Conformal Prediction的威胁情报繁殖方法[J]. 信息网络安全, 2020, 20(6): 90-95. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||