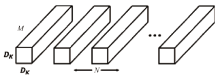
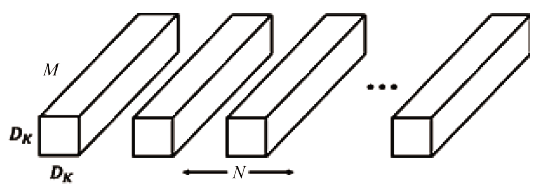
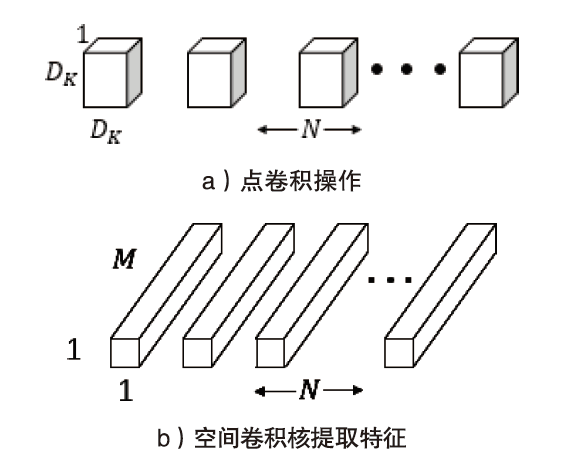
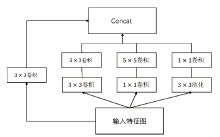
信息网络安全 ›› 2020, Vol. 20 ›› Issue (7): 77-84.doi: 10.3969/j.issn.1671-1122.2020.07.009
混合Gabor的轻量级卷积神经网络的验证码识别研究
- 1.公安部第三研究所,上海 200031
2.四川省公安厅网络安全保卫总队,成都 610000
3.山西大学计算机与信息技术学院,太原 030006
-
收稿日期:2020-01-15出版日期:2020-07-10发布日期:2020-08-13 -
通讯作者:刘全明 E-mail:liuqm@sxu.edu.cn -
作者简介:刘静(1978—),女,山东,硕士,主要研究方向为网络安全|张学谦(1981—),男,重庆,本科,主要研究方向为网络安全、等级保护|刘全明(1973—),男,山西,副教授,博士,主要研究方向为网络行业分析与数据挖掘、云存储与云安全、物联网应用 -
基金资助:国家自然科学基金(61673295);山西省国际科技合作重点研发计划(201903D421050)
Research on Captcha Recognition of Lightweight Convolutional Neural Network with Gabor
LIU Jing1, ZHANG Xueqian2, LIU Quanming3( )
)
- 1. The Third Research Institute of The Ministry of Public Security, Shanghai 200031, China
2. Cyber Security Team of Sichuan Provincial Public Security Department, Chengdu 610000, China
3. School of Computer and Information Technology, Shanxi University, Taiyuan 030006, China
-
Received:2020-01-15Online:2020-07-10Published:2020-08-13 -
Contact:Quanming LIU E-mail:liuqm@sxu.edu.cn
摘要:
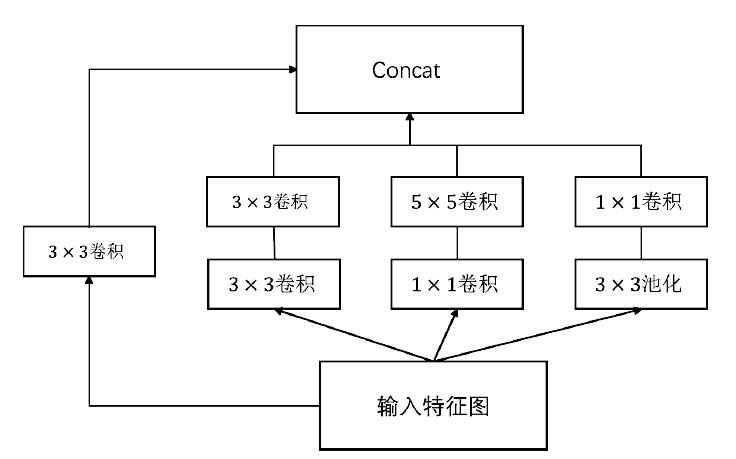
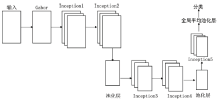
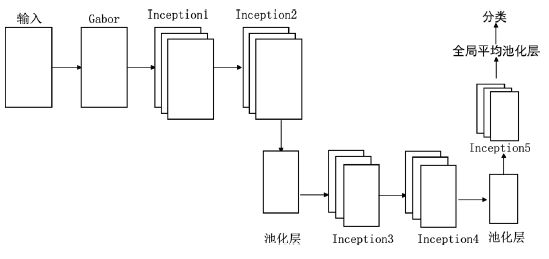
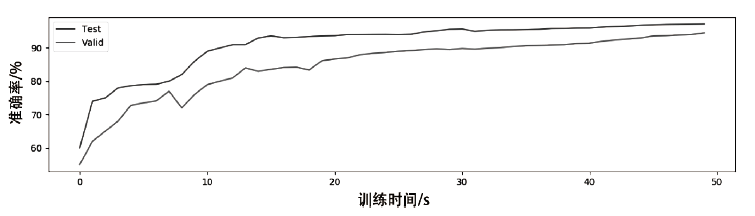
验证码作为一项广泛使用的验证手段,能有效地鉴别登录用户,对网络安全的保护有着重要的意义。针对卷积神经网络参数量大,训练成本和时间较大的问题,文章提出了一种基于图像Gabor特征与卷积神经网络相结合的图像验证码识别方法,实现了验证码图像的识别和分类。使用Gabor算子提取不同方向和角度的细节特征作为卷积神经网络的输入,并改进深度可分离卷积层获得多尺度特征向量,充分提取验证码图像中的不同特征,提高了模型的识别率。实验研究表明,改进的卷积神经网络对验证码的平均识别准确率达到98%左右,具有实际意义。
中图分类号:
引用本文
刘静, 张学谦, 刘全明. 混合Gabor的轻量级卷积神经网络的验证码识别研究[J]. 信息网络安全, 2020, 20(7): 77-84.
LIU Jing, ZHANG Xueqian, LIU Quanming. Research on Captcha Recognition of Lightweight Convolutional Neural Network with Gabor[J]. Netinfo Security, 2020, 20(7): 77-84.
| [1] | KWON H, KIM Y, YOON H, et al. CAPTCHA Image Generation Systems Using Generative Adversarial Networks[J]. Ieice Transactions on Information & Systems, 2018,12(2):543-546. |
| [2] | WANG F, JUN G H, FAN G, et al. Chinese Character CAPTCHA Recognition Based on Convolution Neural Network[EB/OL]. https://www.researchgate.net/publication/311251657_Chinese_character_CAPTCHA_recognition_based_on_convolution_neural_network, 2019-10-15. |
| [3] |
KAZUMA A. Server for Implementing Image Processing Functions Requested by A Printing Device[J]. Environmental Pollution, 2018,152(3):543-552.
URL pmid: 17703858 |
| [4] |
CHEN L C, PAPANDREOU G, KOKKINOS I, et al. Deep Lab: Semantic Image Segmentation with Deep Convolutional Nets, Atrous Convolution, and Fully Connected CRFs[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2018,40(4):834.
doi: 10.1109/TPAMI.2017.2699184 URL pmid: 28463186 |
| [5] | MILTIADIS A, BARR E T, PREMKUMAR D, et al. A Survey of Machine Learning for Big Code and Naturalness[J]. ACM Computing Surveys, 2018,51(4):1-37. |
| [6] | RAISSI M, KARNIADAKIS G E. Hidden Physics Models: Machine Learning of Nonlinear Partial, Differential Equations[EB/OL]. http://www.researchgate.net/publication/318868462_Hidden_Physics_Models_Machine_Learning_of_Nonlinear_Partial_Differential_Equations, 2019-10-15. |
| [7] | CHEN X, MAKKI K, YEN K, et al. Sensor Network Security: A Survey[J]. IEEE Communications Surveys & Tutorials, 2009,11(2):52-73. |
| [8] | SARWAR S S, PANDA P, ROY K. Gabor Filter Assisted Energy Efficient Fast Learning Convolutional Neural Networks[C]// IEEE. 2017 IEEE/ACM International Symposium on Low Power Electronics and Design (ISLPED), July 24-26, 2017, Taipei, China. NJ: IEEE, 2017: 1-6. |
| [9] | MEHTA R, EGIAZARIAN K. Dominant Rotated Local Binary Patterns (DRLBP) for Texture Classification[J]. Pattern Recognition Letters, 2016,71(11):16-22. |
| [10] | YI K M, TRULLS E, LEPETIT V, et al. Lift: Learned Invariant Feature Transform[EB/OL]. http://www.researchgate.net/publication/308277668_LIFT_Learned_Invariant_Feature_Transform, 2019-10-15. |
| [11] | YAN G, YU M, YU Y, et al. Real-Time Vehicle Detection Using Histograms of Oriented Gradients and AdaBoost Classification[J]. Optik, 2016,127(19):7941-7951. |
| [12] | WANG Hu, FENG Lin, SUN Yuzhe. Research and Design of Digital Character-Based CAPTCHA Decoder[J]. Computer Engineering and Applications, 2007,43(32):86-88. |
| 王虎, 冯林, 孙宇哲. 数字验证码识别算法的研究和设计[J]. 计算机工程与应用, 2007,43(32):86-88. | |
| [13] | TIAN Huaichuan. Research and Application on Captcha Recognition and Prevention Based on Neural Network[D]. Harbin: Harbin Institute of Technology, 2010. |
| 田怀川. 基于神经网络的图形验证码识别及防识别的研究与应用[D]. 哈尔滨:哈尔滨工业大学, 2010. | |
| [14] | GANG Lv, HAO Ping. Research on Recognition of CAPTCHA Based on Neural Network[J]. Journal of Zhejiang University of Technology, 2010,38(4):433-436. |
| 吕刚, 郝平. 基于神经网络的数字验证码识别研究[J]. 浙江工业大学学报, 2010,38(4):433-436. | |
| [15] | CAO Yanrong, GONG Yanhong, JIA Huizhen. Verification Code Recognition Method Based on Adversarial Network[J]. Computer Engineering and Applications, 2020,56(8):199-204. |
| 曹廷荣, 龚燕红, 贾惠珍. 基于对抗网络的验证码识别方法[J]. 计算机工程与应用, 2020,56(8):199-204. | |
| [16] | SCHMIDHUBER , JÜRGEN . Deep Learning in Neural Networks: An Overview[J]. Neural Networks, 2015,61(1):85-117. |
| [17] |
LITJENS , GEERT , KOOI , et al. A Survey on Deep Learning in Medical Image Analysis[J]. Medical Image Analysis, 2017,42(9):60-88.
doi: 10.1016/j.media.2017.07.005 URL |
| [18] |
SHIN H C, ROTH H R, GAO M, et al. Deep Convolutional Neural Networks for Computer-Aided Detection: CNN, Architectures, Dataset Characteristics and Transfer Learning[J]. IEEE Transactions on Medical Imaging, 2016,35(5):1285-1298.
doi: 10.1109/TMI.2016.2528162 URL pmid: 26886976 |
| [19] |
ZHANG Q, YANG L T, CHEN Z, et al. A Survey on Deep Learning for Big Data[J]. Information Fusion, 2018,42(10):146-157.
doi: 10.1016/j.inffus.2017.10.006 URL |
| [20] | LEDDY J. Ultrathin Layer Convolution[J]. Journal of Electroanalytical Chemistry, 1991,300(1-2):295-307. |
| [21] |
LUAN S, CHEN C, ZHANG B, et al. Gabor Convolutional Networks[J]. IEEE Transactions on Image Processing, 2018,27(9):1.
doi: 10.1109/TIP.2017.2787262 URL |
| [22] | SZEGEDY C, LIU W, JIA Y, et al. Going Deeper with Convolutions[C]// IEEE. 2015 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), June 7-12, 2015, Boston, MA, USA. NJ: IEEE, 2015: 1-9. |
| [23] | CHOLLET F. Xception: Deep Learning with Depthwise Separable Convolutions[C]// IEEE. Proceedings of 2017 IEEE Conference on Computer Vision and Pattern Recognition, July 21-26, 2017, Honolulu. NJ: IEEE, 2017: 1800-1807. |
| [1] | 李桥, 龙春, 魏金侠, 赵静. 一种基于LMDR和CNN的混合入侵检测模型[J]. 信息网络安全, 2020, 20(9): 117-121. |
| [2] | 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. |
| [3] | 张蕾华, 黄进, 张涛, 王生玉. 视频侦查中人像智能分析应用及算法优化[J]. 信息网络安全, 2020, 20(5): 88-93. |
| [4] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [5] | 龙敏, 龙啸海, 马莉. 基于深度卷积神经网络的指纹活体检测算法研究[J]. 信息网络安全, 2018, 18(6): 28-35. |
| [6] | 夏玉明, 胡绍勇, 朱少民, 刘丽丽. 基于卷积神经网络的网络攻击检测方法研究[J]. 信息网络安全, 2017, 17(11): 32-36. |
| [7] | 胡青, 刘本永. 基于卷积神经网络分类的说话人识别算法[J]. 信息网络安全, 2016, 16(4): 55-60. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||