信息网络安全 ›› 2020, Vol. 20 ›› Issue (4): 65-72.doi: 10.3969/j.issn.1671-1122.2020.04.008
一种基于信任值的雾计算动态访问控制方法
- 战略支援部队信息工程大学,郑州 450002
-
收稿日期:2019-10-15出版日期:2020-04-10发布日期:2020-05-11 -
通讯作者:杜义峰 E-mail:du395864653@163.com -
作者简介:作者简介:杜义峰(1985—),男,河南,硕士研究生,主要研究方向为物联网安全;郭渊博(1975—),男,陕西,教授,博士,主要研究方向为大数据安全、态势感知。
-
基金资助:国家自然科学基金[61602515]
A Dynamic Access Control Method for Fog Computing Based on Trust Value
- PLA Strategic Support Force Information Engineering University, Zhengzhou 450002, China
-
Received:2019-10-15Online:2020-04-10Published:2020-05-11 -
Contact:Yifeng DU E-mail:du395864653@163.com
摘要:
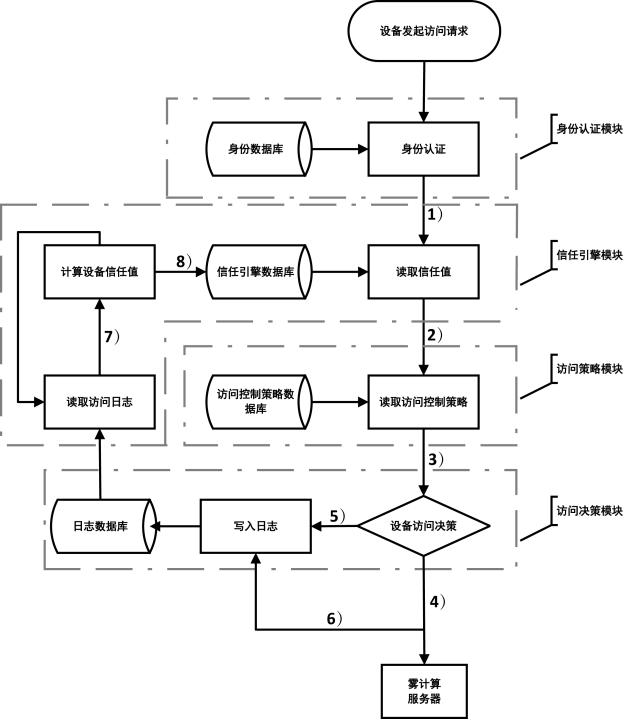
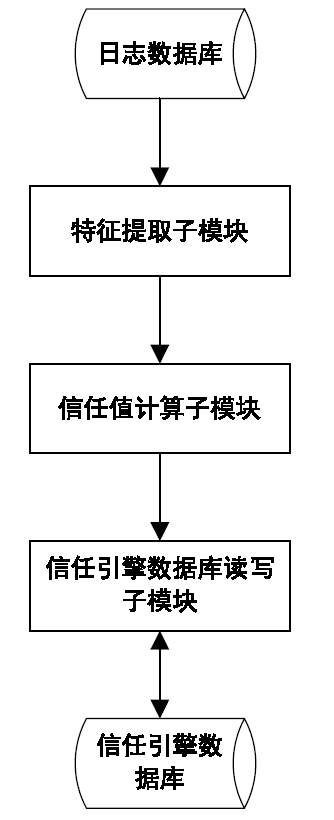
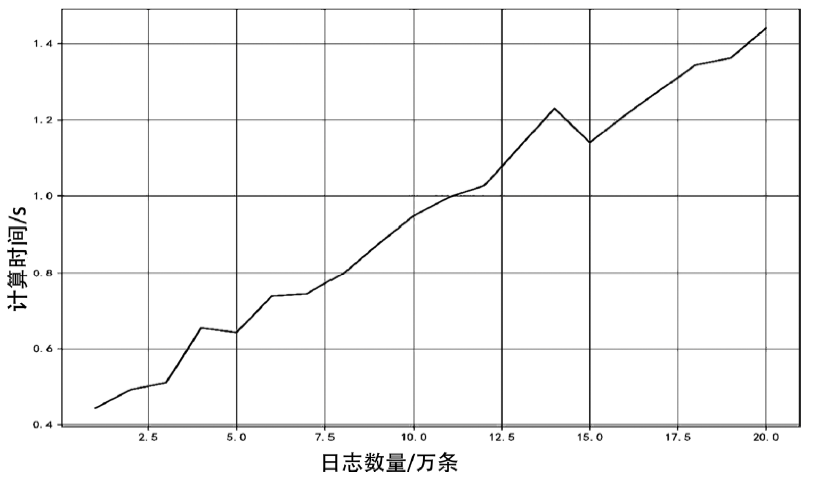
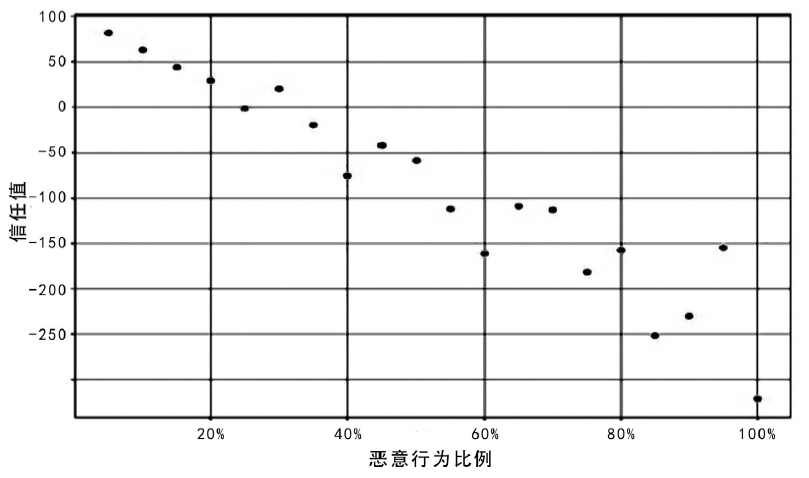
雾计算服务对象是数量庞大、形态各异的物联网设备,且多应用于工业控制、车联网、智慧医疗等形态各异的实时场景,对其访问控制系统动态性、适应性和时延都提出了比较苛刻的要求。传统的访问控制方法不能满足雾计算系统要求,针对这一问题,文章提出了一种基于信任值的动态访问控制方法,从日志数据中提取设备行为特征,使用训练好的机器学习模型计算当前活跃设备的信任值,使用灰度化方法计算当前不活跃设备的信任值,并作为访问决策的依据。该方法从复杂的设备行为特征中提取信任值作为单一访问决策依据,既可以实现快速动态的访问控制,又能迅速迁移到不同应用场景,具备良好的适应性。通过实验对该访问控制方法进行了验证,实验结果表明该方法在运行速度、适应性等方面表现良好。
中图分类号:
引用本文
杜义峰, 郭渊博. 一种基于信任值的雾计算动态访问控制方法[J]. 信息网络安全, 2020, 20(4): 65-72.
DU Yifeng, GUO Yuanbo. A Dynamic Access Control Method for Fog Computing Based on Trust Value[J]. Netinfo Security, 2020, 20(4): 65-72.
| [1] | VARGHESE B, BUYYA R.Next Generation Cloud Computing: New Trends and Research Directions[J]. Future Generation Computer Systems, 2018, 79(3): 849-861. |
| [2] | BONOMI F, MILITO R, et al.Fog Computing and Its Role in the Internet of Things[C]//SIGCOMM. 1st ACM Mobile Cloud Computing Workshop, August 17, 2012, Helsinki, Finland. New York: ACM, 2012: 13-16. |
| [3] | ZHANG Peiyun, ZHOU Mengchu, et al.Security and Trust Issues in Fog Computing: A Survey[J]. Future Generation Computer Systems, 2018, 88(5): 16-27. |
| [4] | PRASANTH A.Cloud Computing Services: A Survey[J]. International Journal of Computer Applications. 2012, 46(3): 25-29. |
| [5] | ZHAO Kai, GE Lina.A Survey on the Internet of Things Security[C]//IEEE. Ninth International Conference on Computational Intelligence and Security, December 14-15, 2013, E’Mei Mountain, Sichuan, China. Washington: IEEE, 2013: 663-667. |
| [6] | HOU Xueshi, LI Yong, et al.Vehicular Fog Computing: A Viewpoint of Vehicles as the Infrastructures[J]. IEEE Transactions on Vehicular Technology, 2016, 65(6): 3860-3873. |
| [7] | CAO Yu, HOU Peng, et al.Distributed Analytics and Edge Intelligence: Pervasive Health Monitoring at The Era of Fog Computing[C]//ACM. The 2015 Workshop on Mobile Big Data, June 21, 2015, Hangzhou, China. New York, USA: ACM, 2015: 43-48. |
| [8] | OKAY F Y, OZDEMIR S.A Fog Computing Based Smart Grid Model[C]//IEEE. 2016 International Symposium on Networks, Computers and Communications(ISNCC), May 11-13, 2016, Yasmine Hammamet, Tunisia. Washington, DC, USA: IEEE, 2016: 1-6. |
| [9] | ZHANG Peng, LIU J K, et al.A Survey on Access Control in Fog Computing[J]. IEEE Communications Magazine, 2018, 56(2): 144-149. |
| [10] | FANG Liang, YIN Lihua, GUO Yunchuan, et al.A Survey of Technologies in Attribute-Based Access Control Scheme[J]. Chinese Journal of Computers, 2017, 40(7): 1680-1698. |
| 房梁,殷丽华,郭云川,等.基于属性的访问控制关键技术研究综述[J].计算机学报,2017,40(7):1680-1698. | |
| [11] | DSOUZA C, AHN G J, et al.Policy-Driven Security Management for Fog Computing: Preliminary Framework and A Case Study[C]//IEEE. 15th International Conference on Information Reuse and Integration(IEEE IRI 2014), Auguest 13-15, 2014, Redwood City, USA. Washington: IEEE, 2014: 16-23. |
| [12] | SALONIKIAS S, MAVRIDIS I, et al.Access Control Issues in Utilizing Fog Computing for Transport Infrastructure[C]//EU. The 10th International Conference on Critical Information Infrastructures Security, October 5-7, 2015, Berlin, Germany. Berlin: Springer, 2015: 15-26. |
| [13] | STOJMENOVIC I, WEN Sheng, et al.An Overview of Fog Computing and Its Security Issues[J]. Concurrency and Computation: Practice and Experience, 2016, 28(10): 2991-3005. |
| [14] | LI Fei, RAHULAMATHAVAN Y, et al.Robust Access Control Framework for Mobile Cloud Computing Network[J]. Computer Communications, 2015, 68(6): 61-72. |
| [15] | MOLLAH M B, AZAD M A K, et al. Secure Data Sharing and Searching at the Edge of Cloud-Assisted Internet of Things[J]. IEEE Cloud Computing, 2017, 4(1): 34-42. |
| [16] | ZAGHDOUDI B, AYED K B, et al.Generic Access Control System for Ad Hoc MCC and Fog Computing[C]//Springer. International Conference on Cryptology and Network Security, November 14-16, 2016, Milan, Italy. Berlin: Springer, 2016: 400-415. |
| [17] | JIA Weijia, ZHOU Xiaojie.Concepts, Issues, and Applications of Fog Computing[J]. Journal on Communications, 2018, 39(5): 153-165. |
| 贾维嘉,周小杰. 雾计算的概念,相关研究与应用[J]. 通信学报,2018,39(5):153-165. | |
| [18] | GILMAN E.Zero Trust Networks: Building Systems in Untrusted Networks[M]. California: O’Reilly Media, 2017. |
| [1] | 徐瑜, 周游, 林璐, 张聪. 无监督机器学习在游戏反欺诈领域的应用研究[J]. 信息网络安全, 2020, 20(9): 32-36. |
| [2] | 汪金苗, 谢永恒, 王国威, 李易庭. 基于属性基加密的区块链隐私保护与访问控制方法[J]. 信息网络安全, 2020, 20(9): 47-51. |
| [3] | 郭春, 陈长青, 申国伟, 蒋朝惠. 一种基于可视化的勒索软件分类方法[J]. 信息网络安全, 2020, 20(4): 31-39. |
| [4] | 刘鹏, 何倩, 刘汪洋, 程序. 支持撤销属性和外包解密的CP-ABE方案[J]. 信息网络安全, 2020, 20(3): 90-97. |
| [5] | 喻露, 罗森林. RBAC模式下数据库内部入侵检测方法研究[J]. 信息网络安全, 2020, 20(2): 83-90. |
| [6] | 许盛伟, 王飞杰. 多机构授权下可追踪可隐藏的属性基加密方案[J]. 信息网络安全, 2020, 20(1): 33-39. |
| [7] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [8] | 马泽文, 刘洋, 徐洪平, 易航. 基于集成学习的DoS攻击流量检测技术[J]. 信息网络安全, 2019, 19(9): 115-119. |
| [9] | 叶阿勇, 金俊林, 孟玲玉, 赵子文. 面向移动终端隐私保护的访问控制研究[J]. 信息网络安全, 2019, 19(8): 51-60. |
| [10] | 秦中元, 韩尹, 张群芳, 朱雪金. 一种改进的多私钥生成中心云存储访问控制方案[J]. 信息网络安全, 2019, 19(6): 11-18. |
| [11] | 陈冠衡, 苏金树. 基于深度神经网络的异常流量检测算法[J]. 信息网络安全, 2019, 19(6): 68-75. |
| [12] | 田春岐, 李静, 王伟, 张礼庆. 一种基于机器学习的Spark容器集群性能提升方法[J]. 信息网络安全, 2019, 19(4): 11-19. |
| [13] | 蔡方博, 何泾沙, 朱娜斐, 韩松. 分布式访问控制模型中节点级联失效研究[J]. 信息网络安全, 2019, 19(12): 47-52. |
| [14] | 胡建伟, 赵伟, 闫峥, 章芮. 基于机器学习的SQL注入漏洞挖掘技术的分析与实现[J]. 信息网络安全, 2019, 19(11): 36-42. |
| [15] | 时向泉, 陶静, 赵宝康. 面向虚拟化环境的网络访问控制系统[J]. 信息网络安全, 2019, 19(10): 1-9. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||