信息网络安全 ›› 2019, Vol. 19 ›› Issue (12): 47-52.doi: 10.3969/j.issn.1671-1122.2019.12.006
分布式访问控制模型中节点级联失效研究
- 北京工业大学信息学部,北京100124
-
收稿日期:2019-06-17出版日期:2019-12-10发布日期:2020-05-11 -
作者简介:作者简介:蔡方博(1990—),女,辽宁,博士研究生,主要研究方向为计算机与网络安全、网络检测与分析;何泾沙(1961—),男,陕西,教授,博士,主要研究方向为网络安全、测试与分析和云计算;朱娜斐(1981—),女,河南,副教授,博士,主要研究方向为网络安全、隐私保护和区块链;韩松(1994—),男,陕西,硕士研究生,主要研究方向为网络安全、访问控制。
-
基金资助:国家自然科学基金[61602456]
Research on Cascading Failure of Nodes in Distributed Access Control Model
Fangbo CAI( ), Jingsha HE, Nafei ZHU, Song HAN
), Jingsha HE, Nafei ZHU, Song HAN
- Faculty of Information Technology, Beijing University of Technology, Beijing 100124, China
-
Received:2019-06-17Online:2019-12-10Published:2020-05-11
摘要:
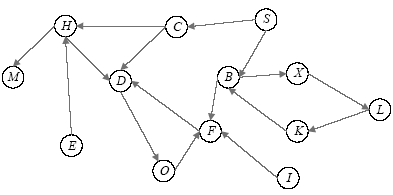
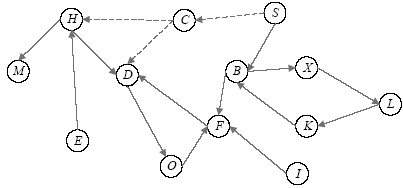
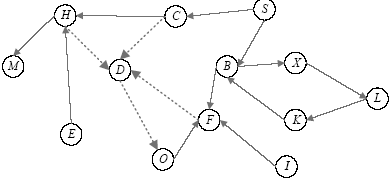
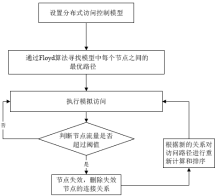
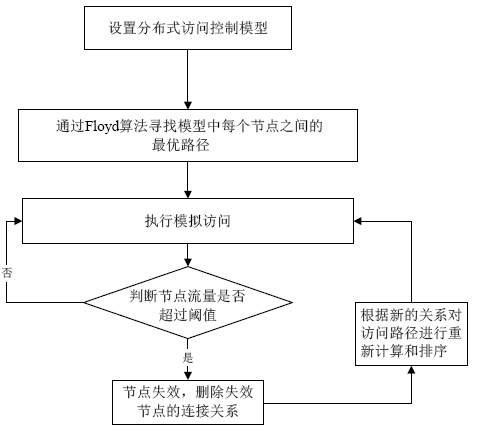
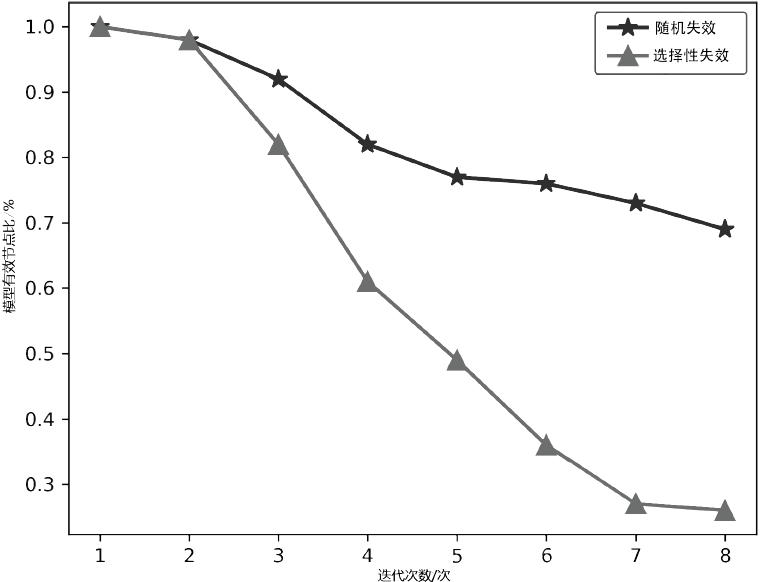
访问控制是指系统对用户身份及其所属的预先定义的策略组限制其使用数据资源的手段。访问控制是系统保密性、完整性、可用性和合法使用性的重要基础,是网络安全防范和资源保护的关键策略之一,也是主体依据某些控制策略或权限对客体本身或其资源进行的不同授权访问。随着计算机网络广泛普及,新的访问模式层出不穷,极大影响和改变了人们工作和生活的方式。在网络安全的大背景下,面对互联网用户与数据的爆炸性增长,当前由单一中心组织构建数据管理系统的方式面临更多的挑战。在分布式访问控制模型中,参与访问的节点在访问故障传递机理中是使访问控制模型变得脆弱,甚至失去访问控制能力的根源。文章在复杂网络级联模型的理论基础上,提出一种基于分布式访问控制模型节点级联失效的安全性分析方法。文章利用节点在执行访问控制过程中的相关属性参数,设计选择性失效和随机失效两种失效方式进行模拟实验,通过实验数据展示不同失效方式对访问控制模型中有效节点比的影响。
中图分类号:
引用本文
蔡方博, 何泾沙, 朱娜斐, 韩松. 分布式访问控制模型中节点级联失效研究[J]. 信息网络安全, 2019, 19(12): 47-52.
Fangbo CAI, Jingsha HE, Nafei ZHU, Song HAN. Research on Cascading Failure of Nodes in Distributed Access Control Model[J]. Netinfo Security, 2019, 19(12): 47-52.
| [1] | PENG Hao, KAN Zhe, ZHAO Dandan, et al.Cascading Failure and Security Evaluation of Information Physics Systems under Deliberate Attack Strategy[J]. Journal of Zhengzhou University(Science and Technology Edition), 2019, 51(3): 13-21. |
| 彭浩,阚哲,赵丹丹,等.蓄意攻击策略下信息物理系统的级联失效及安全评估[J].郑州大学学报(理学版),2019,51(3):13-21. | |
| [2] | MA Mingxin, SHI Guozhen, WANG Yaqiong, et al.Multi-level Security Access Control Strategy for Distributed Systems[J]. Journal of Network and Information Security, 2017, 3(8): 32-38. |
| 马铭鑫,史国振,王亚琼,等.适用于分布式系统的多级安全访问控制策略[J].网络与信息安全学报,2017,3(8):32-38. | |
| [3] | SANDHU R, FERRAIOLO D, KUHN R.The NIST Model for Role-based Access Control: towards a Unified Standard[C]//ACM. The fifth ACM Workshop on Role-based Access Control, July 26-28, 2000 , Berlin, Germany. New York: ACM, 2000: 47-63. |
| [4] | SHI ke. A Two-way Access Control Model Based on Behavioral Trust [D]. Nanjing: Nanjing University of Posts and Telecommunications, 2018. |
| 史可. 一种基于行为信任的双向访问控制模型[D]. 南京:南京邮电大学,2018. | |
| [5] | LI Chaoya.Research on Secure Communication and Access Control Mechanism in Internet of Things[D]. Xi’an: Xidian University, 2018. |
| 李超亚. 物联网环境下安全通信和访问控制机制的研究[D].西安:西安电子科技大学,2018. | |
| [6] | HUANG Yehua.Network Security Situation Assessment Technology Based on Subsection Attack[J]. Journal of Shandong Agricultural University(Natural Science Edition), 2019(3): 489-491. |
| 黄晔华. 基于分段攻击的网络安全态势评估技术[J].山东农业大学学报(自然科学版),2019(3):489-491. | |
| [7] | LEI Min, MO Shuangye.Vulnerability Analysis of Complex Power Network Based on Maximum Flow Algorithm[J]. Journal of Hunan University of Technology, 2019, 33(3): 55-61. |
| 雷敏,莫霜叶.基于最大流算法的复杂电力网络脆弱性分析[J].湖南工业大学学报,2019,33(3):55-61. | |
| [8] | YANG Hongyu, NING Yuguang.A Dynamic Risk Access Control Model for Cloud Platform[J]. Journal of Xidian University, 2018, 45(5): 80-88. |
| 杨宏宇,宁宇光.一种云平台动态风险访问控制模型[J].西安电子科技大学学报,2018,45(5):80-88. | |
| [9] | MA Xingchen, ZHU Jiantao, SHAO Jing, et al.A Decentralized Access Control Model Based on Attributes[J]. Computer Technology and Development, 2018, 28(9): 118-122. |
| 马星晨,朱建涛,邵婧,等.一种基于属性的去中心化访问控制模型[J].计算机技术与发展,2018,28(9):118-122. | |
| [10] | YANG Hongyu, NING Yuguang.Weight Allocation Method of Cloud Platform Access Control Adaptive Risk Assessment Index[J]. Computer Application, 2018, 38(6): 1614-1619. |
| 杨宏宇,宁宇光.云平台访问控制自适应风险评估指标权重分配方法[J].计算机应用,2018,38(6):1614-1619. | |
| [11] | YAN Li, LI Ming, ZHANG Cheng, et al.Network Security Analysis and Monitoring Platform Security Protection Key Technology[J]. Software Guide, 2019(6): 196-199. |
| 严莉,李明,张丞,等.网络安全分析与监控平台安全防护关键技术[J]. 软件导刊,2019(6):196-199. | |
| [12] | WANG Qiong, HE Xinhua, ZHAO Yingkun, et al.Load Balancing Algorithm Based on Load Prediction of Access Characteristics[J]. Journal of Academy of Armored Force Engineering, 2009, 23(5): 68-71. |
| 王琼,何新华,赵颖坤,等.基于访问特征负载预测的负载均衡算法[J].装甲兵工程学院学报,2009,23(5):68-71. | |
| [13] | GE Jun, MENG Gan, ZHOU Dongqing, et al.Construction of Network Situation Assessment Model for Smart Grid[J]. Automation & Instrumentation, 2019(4): 113-117. |
| 葛军,孟干,周冬青,等.面向智能电网的网络态势评估模型构建[J].自动化与仪器仪表,2019(4):113-117. | |
| [14] | ZHANG Kun, LI Peipei, ZHU Baoping, et al.Evaluation Method of Node Importance of Directed Weighted Complex Network Based on PageRank[J]. Journal of Nanjing University of Aeronautics and Astronautics, 2013, 45(3): 429-434. |
| 张琨,李配配,朱保平,等.基于PageRank的有向加权复杂网络节点重要性评估方法[J].南京航空航天大学学报,2013,45(3):429-434. | |
| [15] | WANG Yu, GUO Jinli.A Directed Weighted Network Node Importance Assessment Method Based on Multiple Influence Matrix[J]. Acta Physica Sinica, 2017, 66(5): 19-30. |
| 王雨,郭进利.基于多重影响力矩阵的有向加权网络节点重要性评估方法[J].物理学报,2017,66(5):19-30. |
| [1] | 杜义峰, 郭渊博. 一种基于信任值的雾计算动态访问控制方法[J]. 信息网络安全, 2020, 20(4): 65-72. |
| [2] | 刘鹏, 何倩, 刘汪洋, 程序. 支持撤销属性和外包解密的CP-ABE方案[J]. 信息网络安全, 2020, 20(3): 90-97. |
| [3] | 喻露, 罗森林. RBAC模式下数据库内部入侵检测方法研究[J]. 信息网络安全, 2020, 20(2): 83-90. |
| [4] | 许盛伟, 王飞杰. 多机构授权下可追踪可隐藏的属性基加密方案[J]. 信息网络安全, 2020, 20(1): 33-39. |
| [5] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [6] | 叶阿勇, 金俊林, 孟玲玉, 赵子文. 面向移动终端隐私保护的访问控制研究[J]. 信息网络安全, 2019, 19(8): 51-60. |
| [7] | 秦中元, 韩尹, 张群芳, 朱雪金. 一种改进的多私钥生成中心云存储访问控制方案[J]. 信息网络安全, 2019, 19(6): 11-18. |
| [8] | 时向泉, 陶静, 赵宝康. 面向虚拟化环境的网络访问控制系统[J]. 信息网络安全, 2019, 19(10): 1-9. |
| [9] | 石悦, 李相龙, 戴方芳. 一种基于属性基加密的增强型软件定义网络安全框架[J]. 信息网络安全, 2018, 18(1): 15-22. |
| [10] | 马国峻, 李凯, 裴庆祺, 詹阳. 一种社交网络中细粒度人脸隐私保护方案[J]. 信息网络安全, 2017, 17(8): 26-32. |
| [11] | 卿勇, 孙伟, 熊虎, 赵洋. 云计算中可撤销存储的外包加解密CP-ABE方案[J]. 信息网络安全, 2017, 17(6): 6-8. |
| [12] | 顾春华, 高远, 田秀霞. 安全性优化的RBAC访问控制模型[J]. 信息网络安全, 2017, 17(5): 74-79. |
| [13] | 庄浩霖, 尚涛, 刘建伟. 基于角色的大数据认证授权一体化方案[J]. 信息网络安全, 2017, 17(11): 55-61. |
| [14] | 邵剑雨, 陈福臻, 秦鹏宇, 程久军. 移动互联网环境下基于动态信任值的访问控制方法研究[J]. 信息网络安全, 2016, 16(8): 46-53. |
| [15] | 余丽芳, 杨天长, 牛少彰. 一种增强型Android组件间安全访问控制方案[J]. 信息网络安全, 2016, 16(8): 54-60. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||