信息网络安全 ›› 2020, Vol. 20 ›› Issue (4): 73-80.doi: 10.3969/j.issn.1671-1122.2020.04.009
基于LightGBM的以太坊恶意账户检测方法
边玲玉1,2, 张琳琳1,2( ), 赵楷1,2, 石飞1,2
), 赵楷1,2, 石飞1,2
- 1.新疆大学信息科学与工程学院,乌鲁木齐 830046
2.新疆大学网络空间安全学院,乌鲁木齐 830046
-
收稿日期:2020-01-03出版日期:2020-04-10发布日期:2020-05-11 -
通讯作者:张琳琳 E-mail:zllnadasha@xju.edu.cn -
作者简介:作者简介:边玲玉(1996—),女,新疆,硕士研究生,主要研究方向为区块链数据安全;张琳琳(1974—),女,河南,副教授,博士,主要研究方向为软件安全、大数据分析;赵楷(1976—),男,安徽,副教授,博士,主要研究方向为恶意代码检测、云计算安全;石飞(1983—),男,重庆,实验师,硕士,主要研究方向为智能仪器研究、图像处理。
-
基金资助:国家自然科学基金[61867006];新疆维吾尔自治区科技厅创新环境建设专项[PT1811];新疆维吾尔自治区高校科研计划[XJEDU2017T002,XJEDU2017M005];新疆维吾尔自治区创新环境(人才、基地)建设专项(自然科学基金)联合基金[2019D01C062,2019D01C041];国家级大学生创新计划[201910755030]
Ethereum Malicious Account Detection Method Based on LightGBM
BIAN Lingyu1,2, ZHANG Linlin1,2( ), ZHAO Kai1,2, SHI Fei1,2
), ZHAO Kai1,2, SHI Fei1,2
- 1. College of Information Science and Engineering, Xinjiang University, Urumqi 830046, China
2. College of Cyber Science and Engineering, Xinjiang University, Urumqi 830046, China
-
Received:2020-01-03Online:2020-04-10Published:2020-05-11 -
Contact:Linlin ZHANG E-mail:zllnadasha@xju.edu.cn
摘要:
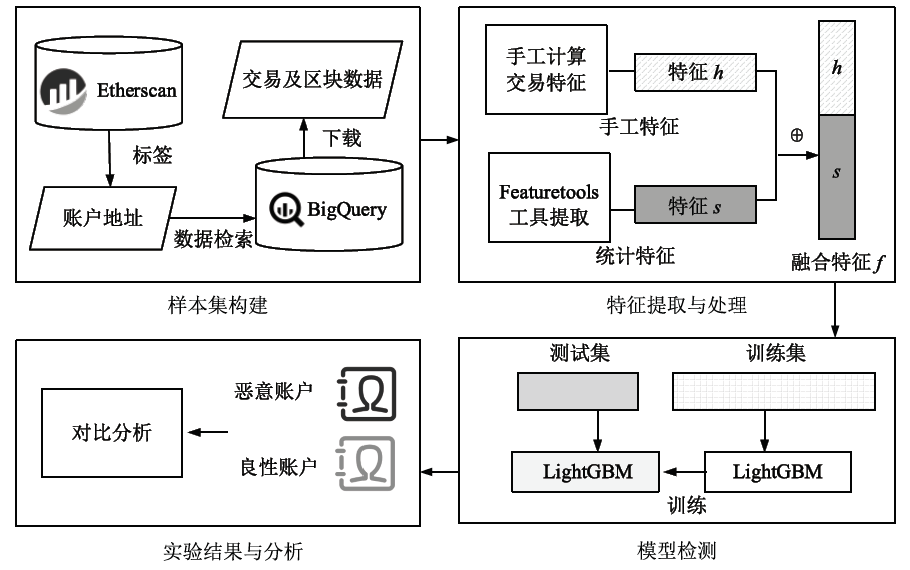
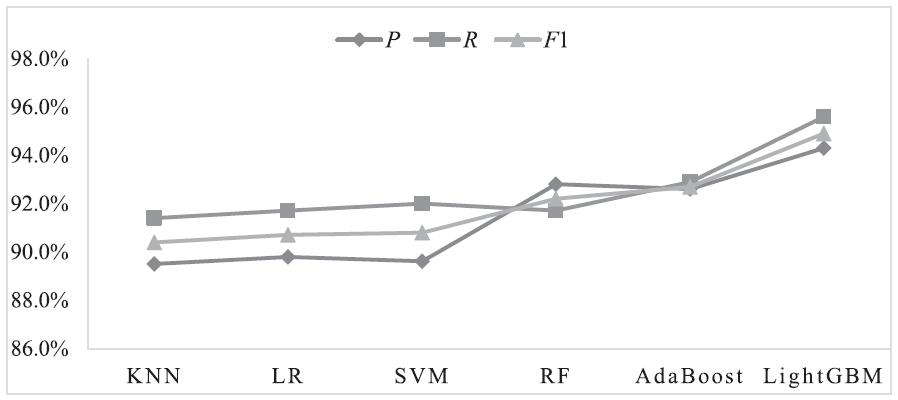
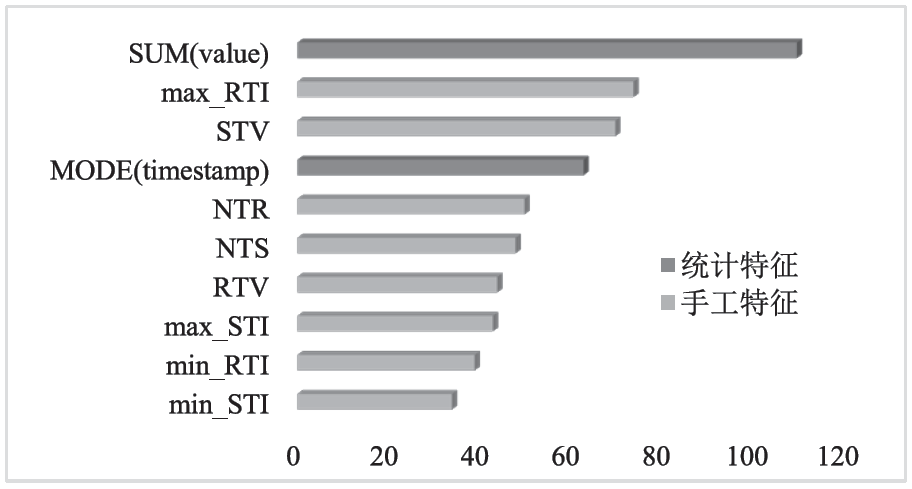
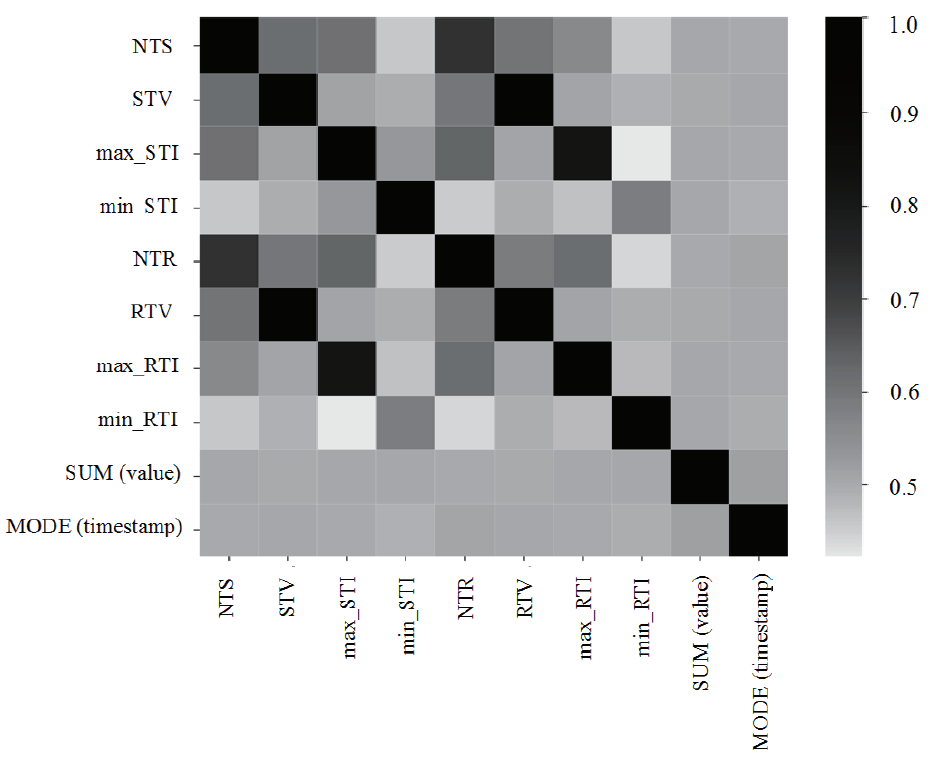
由于区块链匿名性的特点,以太坊逐渐成为恶意账户利用漏洞攻击、网络钓鱼等手段实施欺诈的平台。针对上述问题,文章提出了一种基于LightGBM的以太坊恶意账户检测方法。首先通过收集并标注8028个以太坊账户,基于交易历史规律提取手工特征;然后使用自动特征构造工具featuretools提取统计特征;最后通过融合的两类特征训练LightGBM分类器完成以太坊恶意账户检测。实验结果表明,文章提出方法的F1值为94.9%,相较于SVM、KNN等方法更加高效准确,引入手工特征有效提升了恶意账户的检测性能。
中图分类号:
引用本文
边玲玉, 张琳琳, 赵楷, 石飞. 基于LightGBM的以太坊恶意账户检测方法[J]. 信息网络安全, 2020, 20(4): 73-80.
BIAN Lingyu, ZHANG Linlin, ZHAO Kai, SHI Fei. Ethereum Malicious Account Detection Method Based on LightGBM[J]. Netinfo Security, 2020, 20(4): 73-80.
| [1] | SHAO Qifeng, JIN Cheqing, ZHANG Zhao, et al.Blockchain: Architecture and Research Progress[J]. Chinese Journal of Computers, 2018, 41(5): 969-988. |
| 邵奇峰,金澈清,张召,等.区块链技术:架构及进展[J].计算机学报,2018,41(5):969-988. | |
| [2] | GUO Dongchao, DONG Jiaqing, WANG Kai.Graph Structure and Statistical Properties of Ethereum Transaction Relationships[J]. Information Sciences, 2019, 492(2019): 58-71. |
| [3] | DEEPAK P, NISHA M, MOHANTY S P, et al.Everything You Wanted to Know About the Blockchain: Its Promise, Components, Processes, and Problems[J]. IEEE Consumer Electronics Magazine, 2018, 7(4): 6-14. |
| [4] | ZHU Liehuang, GAO Feng, SHEN Meng, et al.Survey on Privacy Preserving Techniques for Blockchain Technology[J]. Journal of Computer Research and Development, 2017, 54(10): 2170-2186. |
| 祝烈煌,高峰,沈蒙,等.区块链隐私保护研究综述[J].计算机研究与发展,2017,54(10):2170-2186. | |
| [5] | ETHERSCAN. Ethereum Block Explorer[EB/OL]. , 2019-9-27. |
| [6] | YUAN Yong, WANG Feiyue.Blockchain: The State of the Art and Future Trends[J]. Acta Automatica Sinica, 2016, 42(4): 481-494. |
| 袁勇,王飞跃.区块链技术发展现状与展望[J].自动化学报,2016,42(4):481-494. | |
| [7] | LIU Han, YANG Zhiqiang, JIANG Yu, et al.Enabling Clone Detection for Ethereum via Smart Contract Birthmarks[C]//IEEE/ACM. 27th International Conference on Program Comprehension(ICPC), May 25-31, 2019, Montreal, QC, Canada. New York: ACM, 2019: 105-115. |
| [8] | SUN Guozi, WANG Jitao, GU Yu.Security Threat Analysis of Blockchain Technology[J]. Journal of Nanjing University of Posts and Telecommunications(Natural Science Edition), 2019, 39(5): 48-62. |
| 孙国梓,王纪涛,谷宇.区块链技术安全威胁分析[J].南京邮电大学学报(自然科学版),2019,39(5):48-62. | |
| [9] | HUANG Butian, LIU Zhenguang, CHEN Jianhai, et al.Behavior Pattern Clustering in Blockchain Networks[J]. Multimedia Tools and Applications, 2017, 76(19): 20099-20110. |
| [10] | FEATURE LABS. Featuretools[EB/OL]. , 2019-9-27. |
| [11] | ZHAO Chen.Graph-Based Forensic Investigation of Bitcoin Transactions[D]. Ames, Jowa: Jowa State University, 2014. |
| [12] | MONACO J V.Identifying Bitcoin Users by Transaction Behavior[C]//SPIE. 2015 International Society for Optics and Photonics Defense Security and Sensing, April 20-24, 2015, Baltimore, MD, USA. Washington: SPIE, 2015: 33-47. |
| [13] | ANDROULAKI E, KARAME G O, ROESCHLIN M, et al.Evaluating User Privacy in Bitcoin[C]//Springer. 17th International Conference on Financial Cryptography and Data Security, April 1-5, 2013, Okinawa, Japan. Berlin: Springer, 2013: 34-51. |
| [14] | REID F, HARRIGAN M.An Analysis of Anonymity in the Bitcoin System[C]//IEEE. 3rd IEEE International Conference on Privacy, Security, Risk and Trust and 3rd IEEE International Conference on Social Computing, October 9-11, 2011, Boston, MA, USA. NJ: IEEE, 2011: 1318-1326. |
| [15] | YIN H S, LANGENHELDT K, HARLEV M, et al.Regulating Cryptocurrencies: A Supervised Machine Learning Approach to De-anonymizing the Bitcoin Blockchain[J]. Journal of Management Information Systems, 2019, 36(1): 37-73. |
| [16] | LIN Yujing, WU Powei, HSU Chenghan, et al.An Evaluation of Bitcoin Address Classification Based on Transaction History Summarization[C]//IEEE. International Conference on Blockchain and Cryptocurrency(ICBC), May 14-17, 2019, Seoul, Korea(South). NJ: IEEE, 2019: 302-310. |
| [17] | TOYODA K, OHTSUKI T, MATHIOPOULOS P T.Multi-Class Bitcoin-Enabled Service Identification Based on Transaction History Summarization[C]//IEEE. 11th IEEE International Conference on Internet of Things(iThings) and 14th IEEE Green Computing and Communications(GreenCom) and 11th IEEE Cyber, Physical and Social Computing(CPSCom) and 4th IEEE Smart Data(SmartData), July 30-August 3, 2018, Halifax, NS, Canada. NJ: IEEE, 2018: 1153-1160. |
| [18] | TOYODA K, OHTSUKI T, MATHIOPOULOS P T.Identification of High Yielding Investment Programs in Bitcoin via Transactions Pattern Analysis[C]//IEEE. 60th IEEE Global Communications Conference, June 12-14, 2017, Singapore. NJ: IEEE, 2017: 1-6. |
| [19] | KANEMURA K, TOYODA K, OHTSUKI T.Identification of Darknet Markets’ Bitcoin Addresses by Voting Per-address Classification Results[C]//IEEE. International Conference on Blockchain and Cryptocurrency(ICBC), May 14-17, 2019, Seoul, Korea(South). NJ: IEEE, 2019: 154-158. |
| [20] | CHEN Weili, ZHENG Zibin, NGAI E C, et al.Exploiting Blockchain Data to Detect Smart Ponzi Schemes on Ethereum[J]. IEEE Access, 2019, 7(2019): 37575-37586. |
| [21] | LIAO K, ZHAO Ziming, DOUPE A, et al.Behind Closed Doors: Measurement and Analysis of CryptoLocker Ransoms in Bitcoin[C]//IEEE. 11th APWG Symposium on Electronic Crime Research(eCrime), June 1-3, 2016, Toronto, Canada. NJ: IEEE, 2016: 1-13. |
| [22] | KE Guolin, MENG Qi, THOMAS F, et al.LightGBM: A Highly Efficient Gradient Boosting Decision Tree[C]//NIPS. 31st Conference on Neural Information Processing Systems, December 4-9, 2017, Long Beach, CA, USA. New York: Curran Associates, 2017: 3146-3154. |
| [23] | YUN Ju, SUN Guangyu, CHEN Quanhe, et al.A Model Combining Convolutional Neural Network and LightGBM Algorithm for Ultra-Short-Term Wind Power Forecasting[J]. IEEE Access, 2019, 7(2019): 28309-28318. |
| [24] | JOURDAN M, BLANDIN S, WYNTER L, et al.Characterizing Entities in the Bitcoin Blockchain[C]//IEEE. 18th IEEE International Conference on Data Mining(ICDM), November 17-19, 2018, Singapore. NJ: IEEE, 2018: 55-62. |
| [25] | LEE D, KWON T.Automated Classification of Unknown Smart Contracts of Ethereum Using Machine Learning[J]. Journal of the Korea Institute of Information Security & Cryptology, 2018, 28(6): 1319-1328. |
| [1] | 韩磊, 陈武平, 曾志强, 曾颖明. 区块链层级网络结构与应用研究[J]. 信息网络安全, 2020, 20(9): 112-116. |
| [2] | 汪金苗, 谢永恒, 王国威, 李易庭. 基于属性基加密的区块链隐私保护与访问控制方法[J]. 信息网络安全, 2020, 20(9): 47-51. |
| [3] | 毛志来, 刘亚楠, 孙惠平, 陈钟. 区块链性能扩展与安全研究[J]. 信息网络安全, 2020, 20(3): 56-64. |
| [4] | 郎为民, 张汉, 赵毅丰, 姚晋芳. 一种基于区块链的物联网行为监控和活动管理方案[J]. 信息网络安全, 2020, 20(2): 22-29. |
| [5] | 姚萌萌, 唐黎, 凌永兴, 肖卫东. 基于串空间的安全协议形式化分析研究[J]. 信息网络安全, 2020, 20(2): 30-36. |
| [6] | 周艺华, 吕竹青, 杨宇光, 侍伟敏. 基于区块链技术的数据存证管理系统[J]. 信息网络安全, 2019, 19(8): 8-14. |
| [7] | 路爱同, 赵阔, 杨晶莹, 王峰. 区块链跨链技术研究[J]. 信息网络安全, 2019, 19(8): 83-90. |
| [8] | 郑敏, 王虹, 刘洪, 谭冲. 区块链共识算法研究综述[J]. 信息网络安全, 2019, 19(7): 8-24. |
| [9] | 周元健, 秦冬梅, 刘忆宁, 吕松展. 基于区块链的可信仓单系统设计[J]. 信息网络安全, 2019, 19(6): 84-90. |
| [10] | 王文明, 施重阳, 王英豪, 危德健. 基于区块链技术的交易及其安全性研究[J]. 信息网络安全, 2019, 19(5): 1-9. |
| [11] | 黑一鸣, 刘建伟, 张宗洋, 喻辉. 基于区块链的可公开验证分布式云存储系统[J]. 信息网络安全, 2019, 19(3): 52-60. |
| [12] | 赵国锋, 张明聪, 周继华, 赵涛. 基于纠删码的区块链系统区块文件存储模型的研究与应用[J]. 信息网络安全, 2019, 19(2): 28-35. |
| [13] | 王文明, 王全玉, 王英豪, 任好盼. 面向敏感区域的智能监控与预警数据库研究与设计[J]. 信息网络安全, 2019, 19(12): 1-9. |
| [14] | 田秀霞, 陈希, 田福粮. 基于区块链的社区分布式电能安全交易平台方案[J]. 信息网络安全, 2019, 19(1): 51-58. |
| [15] | 李佩丽, 徐海霞, 马添军, 穆永恒. 区块链技术在网络互助中的应用及用户隐私保护[J]. 信息网络安全, 2018, 18(9): 60-65. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||