信息网络安全 ›› 2020, Vol. 20 ›› Issue (4): 21-30.doi: 10.3969/j.issn.1671-1122.2020.04.003
物联网环境下基于DICE的设备度量方案
- 1.海军工程大学信息安全系,武汉 430033
2.武汉大学国家网络安全学院,武汉 430079
-
收稿日期:2020-01-22出版日期:2020-04-10发布日期:2020-05-11 -
通讯作者:张立强 E-mail:zhanglq@whu.edu.cn -
作者简介:作者简介:陈璐(1979—),女,广东,副教授,博士,主要研究方向为可信计算、网络安全;孙亚杰(1997—),男,河南,本科,主要研究方向为可信计算、网络安全;张立强(1979—),男,黑龙江,讲师,博士,主要研究方向为可信计算、云计算安全;陈云(1978—),男,湖北,讲师,博士,主要研究方向为信息安全。
-
基金资助:国家自然科学基金[11202239];海军工程大学自然科学基金引导项目[425317Q063]
A Scheme of Measurement for Terminal Equipment Based on DICE in IoT
CHEN Lu1, SUN Yajie1, ZHANG Liqiang2( ), CHEN Yun1
), CHEN Yun1
- 1. Department of Information Security, Naval University of Engineering, Wuhan 430033, China
2. School of Cyber Science and Engineering, Wuhan University, Wuhan 430079, China
-
Received:2020-01-22Online:2020-04-10Published:2020-05-11 -
Contact:Liqiang ZHANG E-mail:zhanglq@whu.edu.cn
摘要:
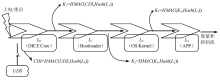
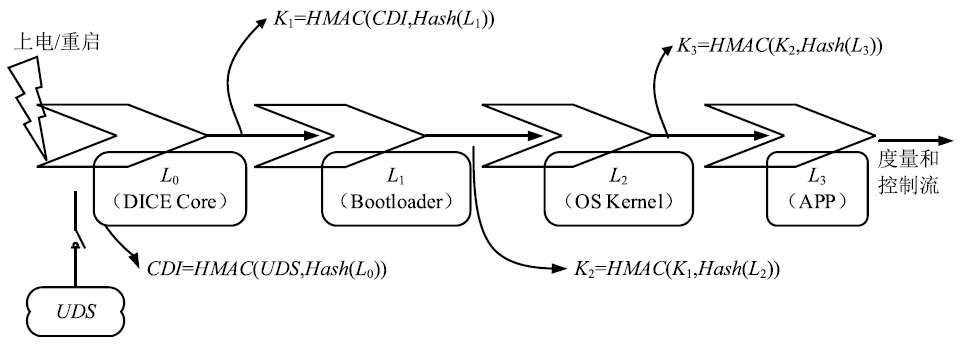
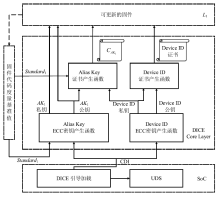
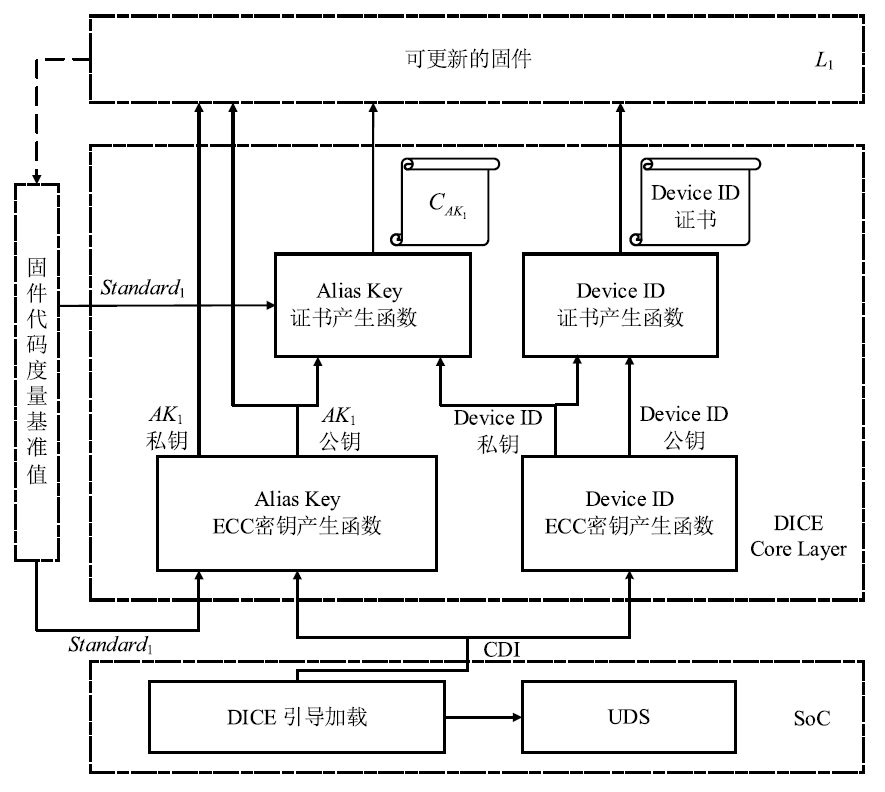
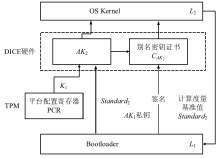
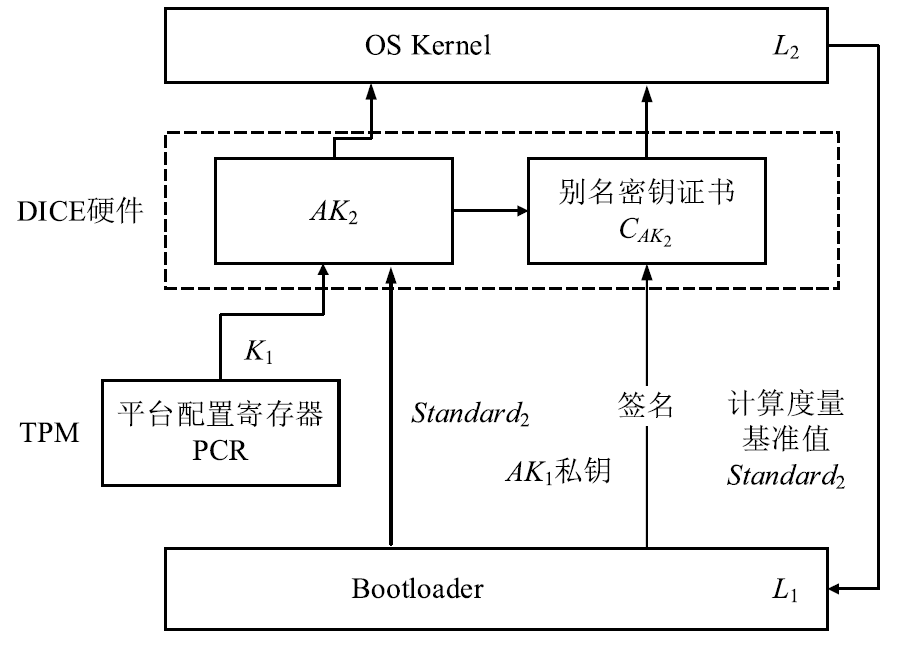
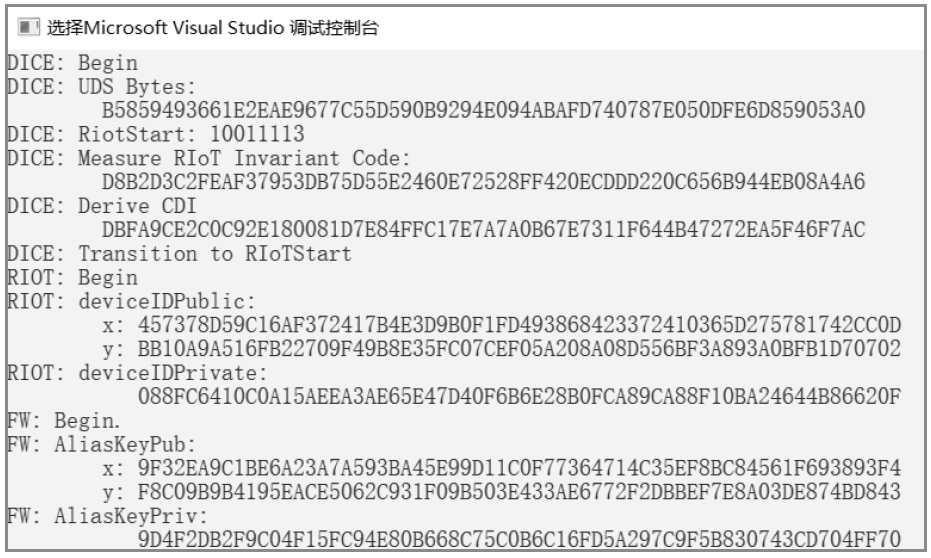
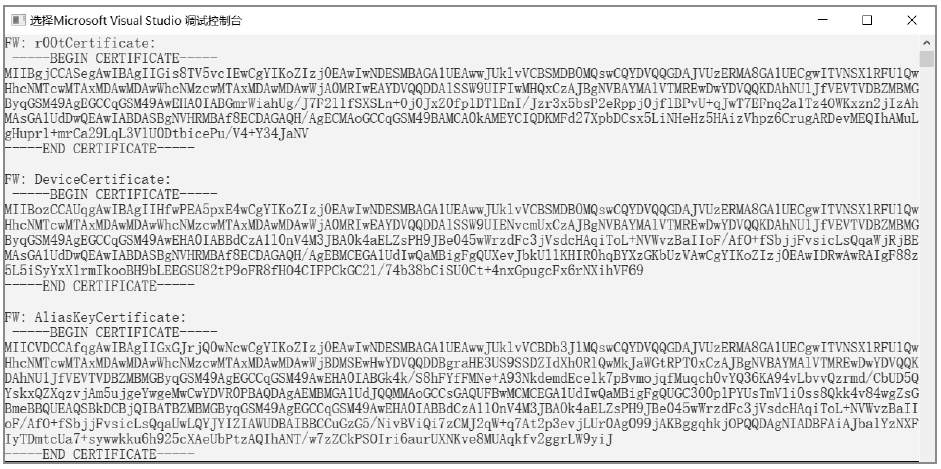
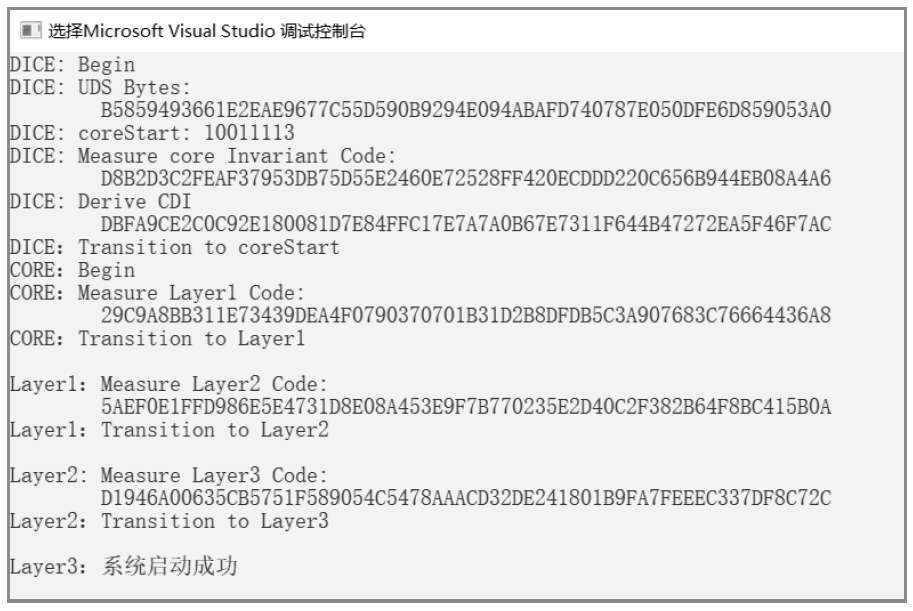
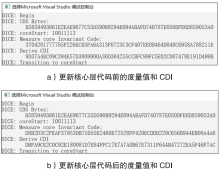
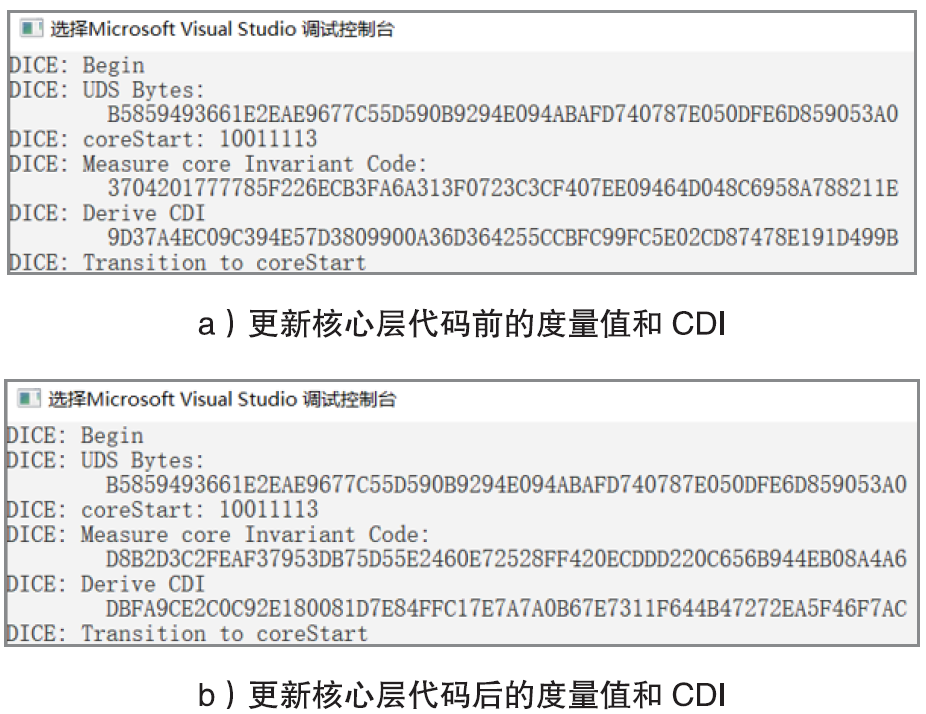
物联网设备的安全防护较为薄弱、安全事件层出不穷,只有从设备系统底层采取安全措施,才能有效提高物联网安全。DICE技术作为可信计算技术发展的最新成果,为解决物联网终端安全提供了新思路,不仅能够提供设备身份保护、数据加密和身份认证等功能,还可通过更新恢复机制来应对复杂多变的物联网环境。文章以DICE技术为基础,将物联网设备RFID读写器作为研究对象,通过分析系统启动过程,设计了信任链的建立和扩展方法,提出了物联网环境下基于DICE的设备度量和更新方案,通过对设备计算环境进行度量保证RFID读写器标签读写操作和数据上传操作的安全可信。最后在C语言编译环境下实现了基于DICE的信任链传递和可信度量方案。
中图分类号:
引用本文
陈璐, 孙亚杰, 张立强, 陈云. 物联网环境下基于DICE的设备度量方案[J]. 信息网络安全, 2020, 20(4): 21-30.
CHEN Lu, SUN Yajie, ZHANG Liqiang, CHEN Yun. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT[J]. Netinfo Security, 2020, 20(4): 21-30.
| [1] | Trusted Computing Group. RIoT[EB/OL]. , 2016-6-15. |
| [2] | Trusted Computing Group. Implicit Identity Based Device Attestation[EB/OL]. admin@trustedcomputinggroup.org, 2016-3-5. |
| [3] | HUA Cunqing.A Survey of Security Detection and Protection for Internet of Things[J]. Journal of Shanghai Jiaotong University, 2018, 52(10): 1307-1313. |
| 化存卿. 物联网安全检测与防护机制综述[J]. 上海交通大学学报,2018,52(10):1307-1313. | |
| [4] | COSTIN A, ZADDACH J, FRANCILLON A.A Large-scale Analysis of the Security of Embedded Firmwares[C]//ACM. 23rd USENIX conference on Security Symposium, August 19, 2014, Berkeley, CA, US. New York: ACM, 2014: 95-110. |
| [5] | KHOKHLOV I, REZNIK L.Data Security Evaluation for Mobile Android Devices[C]//IEEE. 20th Conference of Open Innovations Association(FRUCT), April 3-7, 2017, Petersburg, Russia. New Jersey: IEEE, 2017: 154-160. |
| [6] | MAVROPOULOS O, MOURATIDIS H, FISH A, et al.ASTO: A Tool for Security Analysis of IoT Systems[C]//IEEE. 15th International Conference on Software Engineering Research, Management and Applications, June 7-9, 2017, London, UK. New Jersey: IEEE, 2017:395-400. |
| [7] | RAZA S, WALLGREN L, VOIGT T.SVELTE:Real-time Intrusion Detection in the Internet of things[J]. Ad Hoc Networks, 2013, 11(8): 2661-2674. |
| [8] | NDIBANJE B, LEE H J, LEE S G.Security Analysis and Improvements of Authentication and Access Control in the Internet of Things[J]. Sensors, 2014, 14(8): 14786-14805. |
| [9] | NI Mingtao, ZHAO Bo, WU Fusheng, et al.CREBAD: Chip Radio Emission Based Anomaly Detection Scheme of IoT Devices[J]. Journal of Computer Research and Development, 2018, 55(7): 1451-1461. |
| 倪明涛,赵波,吴福生,等. CREBAD:基于芯片辐射的物联网设备异常检测方案[J]. 计算机研究与发展,2018,55(7):1451-1461. | |
| [10] | WU Zhenqiang, ZHOU Yanwei, MA Jianfeng.A Security Transmission Model for Internet of Things[J]. Chinese Journal of Computers, 2011, 34(8): 1351-1364. |
| 吴振强,周彦伟,马建峰. 物联网安全传输模型[J]. 计算机学报,2011,34(8):1351-1364. | |
| [11] | RHEE K, KWAK J, KIM S.Challenge-response based RFID Authentication Protocol for Distributed Database Environment[C]//Springer. 2nd International Conference on Security in Pervasive Computing(SPC 2005), April 6-8, 2005, Boppard, Germany. Heidelberg: Springer, 2005: 70-84. |
| [12] | Golle P, Jakobsson M, Juels A, et al.Universal Re-encryption for Mixners[C]//Springer. The Cryptographers’ Track at the RSA Conference 2004(CT-RSA 2004), February 23-27, 2004, San Francisco, CA, USA. Heidelberg: Springer, 2004: 163-178. |
| [13] | ZHOU Yongbin, FENG Dengguo.Design and Analysis of Cryptographic Protocols for RFID[J]. Chinese Journal of Computers, 2006, 29(4): 581-589. |
| 周永彬,冯登国. RFID安全协议的设计与分析[J]. 计算机学报,2006,29(4):581-589. | |
| [14] | JUELS A.RFID Security and Privacy: a research survey[J]. IEEE Journal on Selected Areas in Communication, 2006, 24(2): 381-394. |
| [15] | ZHANG Jiawei.Research and Implementation of Trusted Computing Platform Based on Linux[J]. Beijing: Beijing University of Posts and Telecommunication, 2018. |
| 张家伟. 基于Linux的可信计算平台研究与实现[D]. 北京:北京邮电大学,2018. | |
| [16] | WANG Juan, SHI Yuan, PENG Guojun, et al.Survey on Key Technology Development and Application in Trusted Computing[J]. China Communication, 2016(11): 69-90. |
| [1] | 徐绘凯, 刘跃, 马振邦, 段海新. MQTT安全大规模测量研究[J]. 信息网络安全, 2020, 20(9): 37-41. |
| [2] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [3] | 王晓, 赵军, 张建标. 基于可信软件基的虚拟机动态监控机制研究[J]. 信息网络安全, 2020, 20(2): 7-13. |
| [4] | 郎为民, 张汉, 赵毅丰, 姚晋芳. 一种基于区块链的物联网行为监控和活动管理方案[J]. 信息网络安全, 2020, 20(2): 22-29. |
| [5] | 吴宏胜. 基于可信计算和UEBA的智慧政务系统[J]. 信息网络安全, 2020, 20(1): 89-93. |
| [6] | 康健, 王杰, 李正旭, 张光妲. 物联网中一种基于多种特征提取策略的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 21-25. |
| [7] | 叶阿勇, 金俊林, 孟玲玉, 赵子文. 面向移动终端隐私保护的访问控制研究[J]. 信息网络安全, 2019, 19(8): 51-60. |
| [8] | 尚文利, 尹隆, 刘贤达, 赵剑明. 工业控制系统安全可信环境构建技术及应用[J]. 信息网络安全, 2019, 19(6): 1-10. |
| [9] | 尚文利, 张修乐, 刘贤达, 尹隆. 工控网络局域可信计算环境构建方法与验证[J]. 信息网络安全, 2019, 19(4): 1-10. |
| [10] | 段琼琼, 项定华, 史红周. 基于区块链的智能物件认证技术方案设计[J]. 信息网络安全, 2018, 18(9): 95-101. |
| [11] | 王晋, 喻潇, 刘畅, 赵波. 智能电网环境下一种基于SDKey的智能移动终端远程证明方案[J]. 信息网络安全, 2018, 18(7): 1-6. |
| [12] | 张建标, 杨石松, 涂山山, 王晓. 面向云计算环境的vTPCM可信管理方案[J]. 信息网络安全, 2018, 18(4): 9-14. |
| [13] | 赵娜, 龙慧, 苏金树. 一种适用于物联网环境的匿名认证与隐私保护方案[J]. 信息网络安全, 2018, 18(11): 1-7. |
| [14] | 陈付龙, 张紫阳, 王涛春, 谢冬. 一种基于联络信号的物联网安全身份认证方法[J]. 信息网络安全, 2018, 18(11): 40-48. |
| [15] | 任晓贤, 陈洁, 李晨阳, 杨义先. 基于风险矩阵的物联网系统漏洞关联性危害评估[J]. 信息网络安全, 2018, 18(11): 81-88. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||