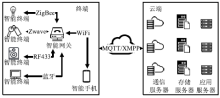
信息网络安全 ›› 2018, Vol. 18 ›› Issue (11): 81-88.doi: 10.3969/j.issn.1671-1122.2018.11.011
基于风险矩阵的物联网系统漏洞关联性危害评估
- 1.北方工业大学计算机学院,北京100144
2. 四川省公安厅网络安全保卫总队,四川成都 610000
3.北京邮电大学网络空间安全学院,北京100876
4.贵州大学贵州省公共大数据重点实验室,贵州贵阳550025
-
收稿日期:2018-09-20出版日期:2018-11-10发布日期:2020-05-11 -
作者简介:作者简介:任晓贤(1995—),女,北京,硕士研究生,主要研究方向为网络空间安全;陈洁(1980—),女,四川,本科,主要研究方向网络安全态势感知;李晨阳(1996—),女,山西,硕士研究生,主要研究方向为网络空间安全;杨义先(1961—),男,四川,教授,博士,主要研究方向为信息安全与密码学。
-
基金资助:国家重点研发计划[2017YFB0802703];贵州省公共大数据重点实验室开放课题[2018BDKFJJ014]
Hazard Assessment of IoT Vulnerabilities Correlation Based on Risk Matrix
Xiaoxian REN1( ), Jie CHEN2, Chenyang LI3, Yixian YANG3,4
), Jie CHEN2, Chenyang LI3, Yixian YANG3,4
- 1. College of Computer Science and Technology, North China University of Technology, Beijing 100144, China
2. Cyber Security Guard, Sichuan Provincial Public Security Department, Chengdu Sichuan 610000, China
3. Information Security Center, Beijing University of Posts and Telecommunications, Beijing 100876, China
4. Guizhou Provincial Key Laboratory of Public Big Data, Guizhou University, Guizhou Guiyang 550025, China
-
Received:2018-09-20Online:2018-11-10Published:2020-05-11
摘要:
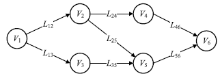
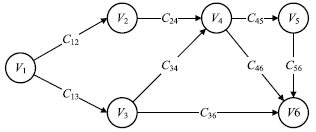
随着物联网的迅速发展和普及利用,针对物联网的攻击事件比例逐年上升。为了对物联网系统的漏洞进行科学评估,文章提出一种漏洞关联性危害评估方法。与传统的对单独漏洞进行孤立评估的方法不同,该方法利用CVSS v3评价指标,以漏洞关联图和风险矩阵为基础,同时考虑前序漏洞节点、后序漏洞节点的关联关系以及漏洞自身的因素,对漏洞进行关联评估。实验表明,该方法对网络安全的防护工作能够起到有效的指导作用,避免存在高关联性危害漏洞的物联网设备被攻击者控制发动DDoS攻击或者成为区块链的挖矿工具。
中图分类号:
引用本文
任晓贤, 陈洁, 李晨阳, 杨义先. 基于风险矩阵的物联网系统漏洞关联性危害评估[J]. 信息网络安全, 2018, 18(11): 81-88.
Xiaoxian REN, Jie CHEN, Chenyang LI, Yixian YANG. Hazard Assessment of IoT Vulnerabilities Correlation Based on Risk Matrix[J]. Netinfo Security, 2018, 18(11): 81-88.
表1
漏洞分类和描述
| 漏洞分类 | 详细内容 |
|---|---|
| 不安全的Web接口 | 在智能设备的Web接口存在XSS、CSRF或SQL漏洞,使用默认用户名和密码,缺乏账户锁定机制 |
| 不安全的认证/授权 | 利用用户的弱密码、密码恢复机制的缺陷以及双因子身份验证机制的缺失来控制智能设备 |
| 不安全的网络服务 | 开放了不必要的端口、通过UPnP向互联网暴露端口以及开放了易受DoS攻击的网络服务 |
| 缺乏传输加密/完整性验证 | 敏感信息以明文形式传递、SSL/TLS不可用或配置不当或使用了专有加密协议。含有这类漏洞的设备容易受到MiTM攻击 |
| 不安全的隐私保护 | 收集的个人信息过多、收集的信息没有得到适当的保护或最终用户无权决定允许收集哪类数据 |
| 不安全的云接口 | 只要攻击者能够访问Internet,就可以获取私人数据 |
| 不安全移动设备接口 | 使用弱密码、缺乏双因子认证和帐户锁定机制 |
| 安全可配置性不足 | 由于用户无法管理或使用安全机制,导致安全机制无法对设备充分发挥作用 |
| 不安全的软件/固件 | 由于系统没有进行相应完整性或真实性检查,使攻击者能够安装任意固件 |
| 缺少物理安全措施 | 只要拆开智能设备,即可获取MCU、外部存储器等 |
表2
CVSS v3.0 漏洞属性描述
| 属性组 | 属性向量 |
|---|---|
| Base | AV:[N,A,L,P]/AC:[L,H]/PR:[N,L,H]/UI:[N,R]/S:[U,C]/C:[H,L,N]/I:[H,L,N]/A:[H,L,N] |
| Temporal | E:[X,H,F,P,U]/RL:[X,U,W,T,O]/RC: [X,C,R,U] |
| Environmental | CR:[X,H,M,L]/IR:[X,H,M,L]/AR:[X,H,M,L]/MAV:[X,N,A,L,P]/MAC:[X,L,H]/MPR:[X,N,L,H]/MUI:[X,N,R]/MS:[X,U,C]/MC:[X,N,L,H]/MI: [X,N,L,H]/MA:[X,N,L,H] |
表3
CVSS v3.0 属性取值赋值
| 属性 | 属性取值 | 对应数值 |
|---|---|---|
| AV (Attack Vector) | N (Network) | 0.85 |
| A (Adjacent Network) | 0.62 | |
| L (Local) | 0.55 | |
| P (Physical) | 0.2 | |
| AC (Attack Complexity) | L (Low) | 0.77 |
| H (High) | 0.44 | |
| PR (Privilege Required) | N (None) | 0.85 |
| L (Low) | 0.62 (如果更改/修改范围,则为0.68) | |
| H (High) | 0.27 (如果更改/修改范围,则为0.50) | |
| UI (User Interaction) | N (None) | 0.85 |
| R (Required) | 0.62 | |
| E(Exploit Code Maturity) | X (Not Defined) | 1 |
| H (High) | 1 | |
| F (Functional) | 0.97 | |
| P (Proof of Concept) | 0.94 | |
| U (Unproven) | 0.91 |
表5
CVSS v3.0给出的漏洞属性
| 漏洞编号 | CVE编号 | Base值 | Temporal值 |
|---|---|---|---|
| V1 | CVE-2016-6277 | AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H | E:X |
| V2 | CVE-2015-0569 | AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H | E:X |
| V3 | CVE-2017-8224 | AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H | E:X |
| V4 | CVE-2017-0781 | AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H | E:X |
| V5 | CVE-2016-1896 | AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H | E:X |
| V6 | CVE-2017-7494 | AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H | E:X |
| [1] | YE Zhonghua. Analysis of the Five Development Trends of the Internet of Things in 2017[N].China City Newspaper,2017-1-9(019). |
| 叶中华. 解析2017年物联网五大发展趋势[N].中国城市报,2017-1-9(019). | |
| [2] | SUN Zhixin, LUO Bingqing, LUO Shengmei,et al.Security Model of Internet of Things Based on Hierarchy[J]. Computer Engineering,2011,37(10):1-7. |
| 孙知信,骆冰清,罗圣美,等.一种基于等级划分的物联网安全模型[J].计算机工程,2011,37(10):1-7. | |
| [3] | XIE Lixia, JIANG Diansheng,ZHANG Li,et al.Vulnerability Threat Correlation Assessment Method[J]. Journal of Computer Applications, 2012,32(3):679-682. |
| 谢丽霞,江典盛,张利,等.漏洞威胁的关联评估方法[J].计算机应用, 2012,32(3):679-682. | |
| [4] | XIE Changrong,ZENG Baoguo.Introduction to Internet of Things Technology [M].Chongqing:Chongqing University Press,2013. |
| 谢昌荣,曾宝国.物联网技术概论[M].重庆:重庆大学出版社,2013. | |
| [5] | LI Qingpeng,WANG Buhong,WANG Xiaodong,et al.Network Security Assessment Based on Probabilities of Attack Graph Nodes[J].Application Research of Computers,2013,30(3):906-908. |
| 李庆朋,王布宏,王晓东,等.基于攻击图节点概率的网络安全度量方法[J].计算机应用研究,2013,30(3):906-908. | |
| [6] | GAO Chuan, YAN Hanbing, JIA Zixiao.Research on the Method for Network Vulnerabilities Situational Awareness Based on the Features[J].Netinfo Security,2016,16(12):28-33. |
| 高川,严寒冰,贾子骁.基于特征的网络漏洞态势感知方法研究[J].信息网络安全,2016,16(12):28-33. | |
| [7] | ZHANG Hengwei.Research on Key Technology of Security Risk Assessment for Information System [D].Zhengzhou:Information Engineering University, 2015. |
| 张恒巍. 信息系统安全风险评估关键技术研究[D].郑州:信息工程大学, 2015. | |
| [8] | ZHANG Yuqing.Research on Network Security Vulnerabilities[J].Netinfo Security, 2008,8(11):24-26. |
| 张玉清. 网络安全漏洞研究[J].信息网络安全,2008,8(11):24-26. | |
| [9] | LEI Kenan, ZHANG Yuqing, WU Chensi,et al.A System for Scoring the Exploitability of Vulnerability Based Types[J].Journal of Computer Research and Development,2017,54(10):2296-2309. |
| 雷柯楠,张玉清,吴晨思,等.基于漏洞类型的漏洞可利用性量化评估系统[J].计算机研究与发展,2017,54(10):2296-2309. | |
| [10] | ZHANG Fengli, FENG Bo.Vulnerability Assessment Based on Correlation[J]. Application Research of Computers,2014,31(3):811-814. |
| 张凤荔,冯波.基于关联性的漏洞评估方法[J].计算机应用研究, 2014,31(3):811-814. | |
| [11] | GAO Zhimin.Application of Vulnerabilities Corelation Graph in Risk Evaluation[J]. Telecommunication Engineering,2009,49(10):26-30. |
| 高志民. 漏洞关联图在风险评估中的应用[J].电讯技术, 2009,49(10):26-30. | |
| [12] | LIU Pingping.Research on Vulnerability Assessment Technology Based on Correlation Relationship [D]. Beijing: Beijing University of Posts and Telecommunications,2015. |
| 刘平平. 基于关联关系的漏洞评估技术研究[D].北京:北京邮电大学,2015. | |
| [13] | QI Yong, LIU Min, LI Qianmu.Attack Graph Model Based on Extended Markov Chain[J]. Computer Engineering and Design,2014,35(12):4131-4135. |
| 戚湧,刘敏,李千目.基于扩展马尔科夫链的攻击图模型[J].计算机工程与设计,2014,35(12):4131-4135. | |
| [14] | WU Jinyu.Research on Key Technologies of Network Security Risk Assessment [D].Beijing: Beijing University of Posts and Telecommunications,2013. |
| 吴金宇. 网络安全风险评估关键技术研究[D].北京:北京邮电大学,2013. | |
| [15] | ZHANG Hengwei, ZHANG Jian, HAN Jihong,et al.Vulnerability Risk Analysis Method Based on Game Model and Risk Matrix[J].Computer Engineering and Design,2016,37(6):1421-1427. |
| 张恒巍,张健,韩继红,等.基于博弈模型和风险矩阵的漏洞风险分析方法[J].计算机工程与设计,2016,37(6):1421-1427. | |
| [16] | WANG Hui, WANG Yunfeng, WANG Kunfu.Research on Predicting Attack Path Based on Bayesian Inference[J]. Application Research of Computers,2015,32(1):226-231. |
| 王辉,王云峰,王坤福.基于贝叶斯推理的攻击路径预测研究[J].计算机应用研究,2015,32(1):226-231. | |
| [17] | WEN Weiping, GUO Ronghua, MENG Zheng, et al.Research and Implementation on Information Security Risk Assessment Key Technology[J].Netinfo Security,2015,15(2):7-14. |
| 文伟平,郭荣华,孟正,等.信息安全风险评估关键技术研究与实现[J].信息网络安全,2015,15(2):7-14. | |
| [18] | ZHANG Xi,HUANG Shuguang,XIA Yang,et al.Attack Graph-based Method for Vulnerability Risk Evaluation[J]. Application Research of Computers, 2010, 27(1):278-280. |
| 张玺, 黄曙光, 夏阳,等. 一种基于攻击图的漏洞风险评估方法[J]. 计算机应用研究, 2010, 27(1):278-280. |
| [1] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [2] | 陈璐, 孙亚杰, 张立强, 陈云. 物联网环境下基于DICE的设备度量方案[J]. 信息网络安全, 2020, 20(4): 21-30. |
| [3] | 边玲玉, 张琳琳, 赵楷, 石飞. 基于LightGBM的以太坊恶意账户检测方法[J]. 信息网络安全, 2020, 20(4): 73-80. |
| [4] | 毛志来, 刘亚楠, 孙惠平, 陈钟. 区块链性能扩展与安全研究[J]. 信息网络安全, 2020, 20(3): 56-64. |
| [5] | 郎为民, 张汉, 赵毅丰, 姚晋芳. 一种基于区块链的物联网行为监控和活动管理方案[J]. 信息网络安全, 2020, 20(2): 22-29. |
| [6] | 姚萌萌, 唐黎, 凌永兴, 肖卫东. 基于串空间的安全协议形式化分析研究[J]. 信息网络安全, 2020, 20(2): 30-36. |
| [7] | 康健, 王杰, 李正旭, 张光妲. 物联网中一种基于多种特征提取策略的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 21-25. |
| [8] | 周艺华, 吕竹青, 杨宇光, 侍伟敏. 基于区块链技术的数据存证管理系统[J]. 信息网络安全, 2019, 19(8): 8-14. |
| [9] | 叶阿勇, 金俊林, 孟玲玉, 赵子文. 面向移动终端隐私保护的访问控制研究[J]. 信息网络安全, 2019, 19(8): 51-60. |
| [10] | 路爱同, 赵阔, 杨晶莹, 王峰. 区块链跨链技术研究[J]. 信息网络安全, 2019, 19(8): 83-90. |
| [11] | 郑敏, 王虹, 刘洪, 谭冲. 区块链共识算法研究综述[J]. 信息网络安全, 2019, 19(7): 8-24. |
| [12] | 周元健, 秦冬梅, 刘忆宁, 吕松展. 基于区块链的可信仓单系统设计[J]. 信息网络安全, 2019, 19(6): 84-90. |
| [13] | 王文明, 施重阳, 王英豪, 危德健. 基于区块链技术的交易及其安全性研究[J]. 信息网络安全, 2019, 19(5): 1-9. |
| [14] | 黑一鸣, 刘建伟, 张宗洋, 喻辉. 基于区块链的可公开验证分布式云存储系统[J]. 信息网络安全, 2019, 19(3): 52-60. |
| [15] | 赵国锋, 张明聪, 周继华, 赵涛. 基于纠删码的区块链系统区块文件存储模型的研究与应用[J]. 信息网络安全, 2019, 19(2): 28-35. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||