信息网络安全 ›› 2020, Vol. 20 ›› Issue (4): 12-20.doi: 10.3969/j.issn.1671-1122.2020.04.002
无线传感器网络中信任管理机制研究综述
- 河海大学物联网工程学院,常州 213022
-
收稿日期:2019-12-09出版日期:2020-04-10发布日期:2020-05-11 -
通讯作者:韩光洁 E-mail:hanguangjie@gmail.com -
作者简介:作者简介:江金芳(1989—),女,安徽,副教授,博士,主要研究方向为物联网、无线传感网、网络安全和信任管理;韩光洁(1972—),男,黑龙江,教授,博士,主要研究方向为物联网、人工智能、工业互联网、智慧海洋和智能计算等。
-
基金资助:国家自然科学基金青年项目[61602152]
Survey of Trust Management Mechanism in Wireless Sensor Network
- College of Internet of Things Engineering, Hohai University, Changzhou 213022, China
-
Received:2019-12-09Online:2020-04-10Published:2020-05-11 -
Contact:Guangjie HAN E-mail:hanguangjie@gmail.com
摘要:
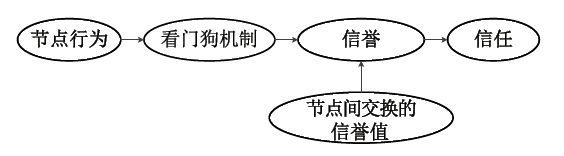
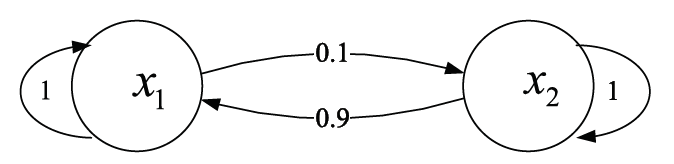
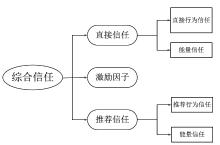
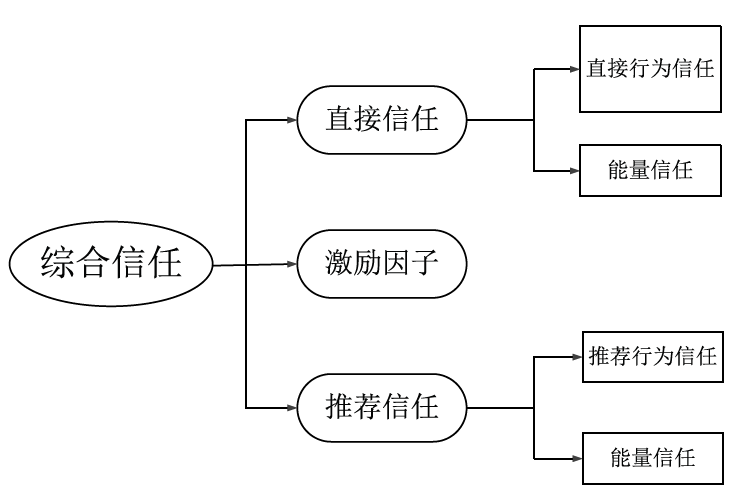
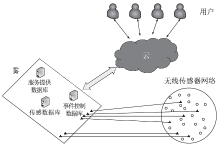
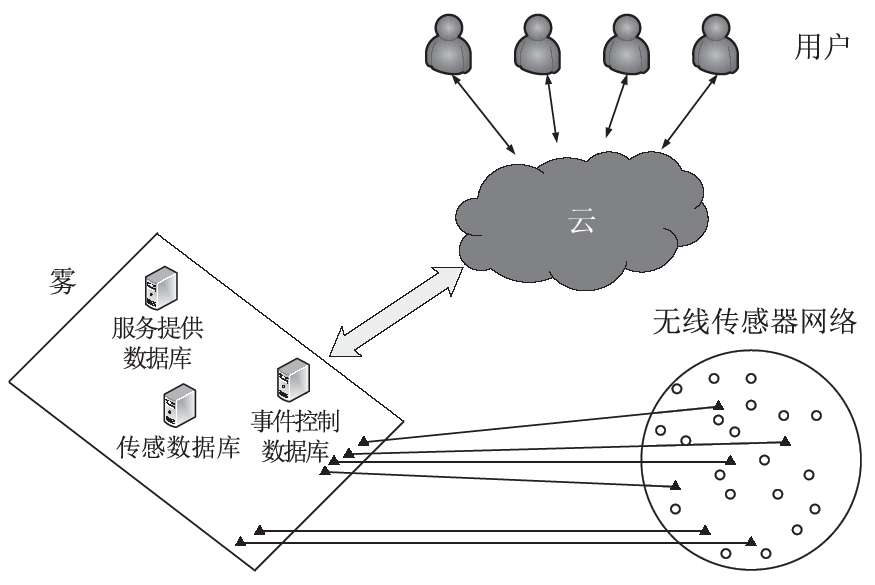
信任管理机制是近年来无线传感器网络安全领域的研究热点。文章首先从信任管理的基本概念出发,分析总结了已有的攻击模型,包括网络攻击模型和信任攻击模型;接着介绍了信任管理机制中使用的主要算法,包括贝叶斯统计、主观逻辑、模糊逻辑、D-S 证据理论、熵理论、云理论、层次分析法、雾计算和机器学习等,依次阐述了这些算法的主要思想、研究进展以及存在的问题。在此基础上,文章对无线传感器网络信任管理机制的未来发展趋势进行了展望,归纳总结了当前信任管理机制存在的主要问题及未来可能的研究方向。
中图分类号:
引用本文
江金芳, 韩光洁. 无线传感器网络中信任管理机制研究综述[J]. 信息网络安全, 2020, 20(4): 12-20.
JIANG Jinfang, HAN Guangjie. Survey of Trust Management Mechanism in Wireless Sensor Network[J]. Netinfo Security, 2020, 20(4): 12-20.
| [1] | BLAZE M, FEIGENBAUM J, LACY J.Decentralized Trust Management[C]//IEEE. The 17th Symposium on Security and Privacy, May 6-8, 1996, Oakland, CA, USA. NJ: IEEE, 1996: 164-173. |
| [2] | GANERIWAL S, BALZAN L J, SRIVASTAVA M B. Reputation-based Framework for High Integrity Sensor Networks[EB/OL]. , 2019-11-11. |
| [3] | HUANG Qiming, NAN Haiyan.Reputation Computing for Wireless Sensor Networks Based on Dirichlet Distribution[J]. Chinese Journal of Sensors and Actuators, 2009, 22(4): 526-530. |
| 黄旗明,南海燕.基于Dirichlet 分布的无线传感器网络的信誉计算模型研究[J].传感技术学报,2009,22(4):526-530. | |
| [4] | FANG Weidong, ZHANG Xiaolong, SHI Zhidong, et al.Binomial-based Trust Management System in Wireless Sensor Networks[J]. Chinese Journal of Sensors and Actuators, 2015(5): 703-708. |
| 房卫东,张小珑,石志东,等.基于二项分布的无线传感器网络信任管理系统[J]. 传感技术学报, 2015(5):703-708. | |
| [5] | JØSANG A, BHUIYAN T. Optimal Trust Network Analysis with Subjective Logic[C]//IEEE. 2008 Second International Conference on Emerging Security Information, Systems and Technologies, August 25-31, 2008, Cap Esterel, France. NJ: IEEE, 2008: 179-184. |
| [6] | REN Yi, ZADOROZHNY V I, OLESHCHUK V A, et al.A Novel Approach to Trust Management in Unattended Wireless Sensor Networks[J]. IEEE Transactions on Mobile Computing, 2014, 13(7): 1409-1423. |
| [7] | JIANG Jinfang, HAN Guangjie, WANG Feng, et al.An Efficient Distributed Trust Model for Wireless Sensor Networks[J]. IEEE Transactions on Parallel and Distributed Systems, 2015, 26(5): 1228-1237. |
| [8] | FARHAD F, ZADOROZHNY V I, LI F Y.Subjective Logic-based In-network Data Processing for Trust Management in Collocated and Distributed Wireless Sensor Networks[J]. IEEE Sensors Journal, 2018, 18(5): 6446-6460. |
| [9] | ZADEH L A.Fuzzy Sets[J]. Information and Control, 1965, 8(3): 338-353. |
| [10] | CHEN Chao, WANG Ruchuan, ZHANG Lin.The Research of Subjective Trust Model Based on Fuzzy Theory in Open Networks[J]. Acta Electronica Sinica, 2010, 38(11): 2505-2509. |
| 陈超,王汝传,张琳,一种基于开放式网络环境的模糊主观信任模型研究[J].电子学报,2010,38(11):2505-2509. | |
| [11] | DEMPSTER A P.Upper and Lower Probabilities Induced by a Multi- valued Mapping[J]. Annals of Mathematical Statistics, 1967, 38(2): 325-339. |
| [12] | SHAFER G.A Mathematical Theory of Evidence[M]. New Jersey: Princeton University Press, 1976. |
| [13] | FENG Renjian, XU Xiaofeng, ZHOU Xiang, et al.Trust Evaluation Algorithm for Wireless Sensor Networks Based on Node Behaviors and D-S Evidence Theory[J]. Sensors, 2011, 11(2): 1345-1360. |
| [14] | ZHANG Lin, LIU Jingwen, WANG Ruchuan, et al.Trust Evaluation Model Based on Improved D-S Evidence Theory[J]. Journal on Communications, 2013, 34(7): 167-173. |
| 张琳,刘婧文,王汝传,等.基于改进D-S 证据理论的信任评估模型[J].通信学报,2013,34(7):167-173. | |
| [15] | SONG Yafei, WANG Xiaodan, LEI Lei, et al.Evidence Combination Based on the Degree of Credibility and Falsity[J]. Journal on Communications, 2015, 36(5): 98-105. |
| 宋亚飞,王晓丹,雷蕾,等.基于信任度和虚假度的证据组合方法[J].通信学报,2015,36(5):98-105. | |
| [16] | ZHOU Zhiping, ZHAO Xiaoxiao, SHAO Nannan.WSN Trust Evaluation Model Based on Fuzzy Set and D-S Evidence Theory[J]. Journal of System Simulation, 2018, 30(4): 1229-1236. |
| 周治平,赵晓晓,邵楠楠.结合模糊集合与D-S证据理论的WSN信任评估模型[J].系统仿真学报, 2018, 30(4):1229-1236. | |
| [17] | SUN Y L, YU Wei, HAN Zhu, et al.Information Theoretic Framework of Trust Modeling and Evaluation for Ad Hoc Networks[J]. IEEE Journal on Selected Areas in Communications, 2006, 24(2): 305-317. |
| [18] | DAI Hongjun, JIA Zhiping, DONG Xiaona.An Entropy-based Trust Modeling and Evaluation for Wireless Sensor Networks[C]//IEEE. 2008 International Conference on Embedded Software and Systems(ICESS2008), July 29-31, 2008, Sichuan, China. NJ: IEEE, 2008: 27-34. |
| [19] | LI Xiayong, GUI Xiaolin, MAO Qian, et al.Adaptive Dynamic Trust Measurement and Prediction Model Based on Behavior Monitoring[J]. Chinese Journal of Computers, 2009(4): 76-86. |
| 李小勇,桂小林,毛倩,等.基于行为监控的自适应动态信任度测模型[J]. 计算机学报,2009(4):76-86. | |
| [20] | ZHANG Lin, XING Huan, WANG Ruchuan, et al.Dynamic Trust Model Based on Recommendation Chain Classification in Complex Network Environment[J]. Journal on Communications, 2015, 36(9): 55-64. |
| 张琳,邢欢,王汝传,等.复杂网络环境下基于推荐链分类的动态信任模型[J].通信学报,2015, 36(9):55-64. | |
| [21] | LI Deyi, MENG Haijun, SHI Xuemei.Subordinate Cloud and Subordinate Cloud Generator[J]. Journal of Computer Research and Development, 1995, 32(6): 15-20. |
| 李德毅,孟海军,史雪梅.隶属云和隶属云发生器[J].计算机研究与发展,1995,32(6):15-20. | |
| [22] | MA Bin.Cross-layer Trust Model and Algorithm of Node Selection in Wireless Sensor Networks[C]//IEEE. 2009 International Conference on Communication Software and Networks, February 27-28, 2009, Macao, China. NJ: IEEE, 2009: 812-815. |
| [23] | ZHANG Shibin, XU Chunxiang.Study on the Trust Evaluation Approach Based on Cloud Model[J]. Chinese Journal of Computers, 2013, 36(2): 422-431. |
| 张仕斌,许春香.基于云模型的信任评估方法研究[J].计算机学报,2013,36(2):422-431. | |
| [24] | XU Xiaobin, ZHANG Guangwei, WANG Shangguang, et al.Uncertainty Trust Representation of WSN Based on Lightweight Cloud Model[J]. Journal on Communications,2014, 35(2): 63-69. |
| 徐晓斌,张光卫,王尚广,等.基于轻量云模型的WSN不确定性信任表示方法[J]. 通信学报,2014,35(2):63-69. | |
| [25] | XIAO Yunpeng, YAO Haohao, LIU Yanbing.A WSNs Node Reputation Security Scheme Based on Cloud Model[J]. Acta Electronica Sinica, 2016, 44(1): 168-175. |
| 肖云鹏,姚豪豪,刘宴兵.一种基于云模型的WSNs节点信誉安全方案[J].电子学报,2016,44(1):168-175. | |
| [26] | SAATY T L.The Analytic Hierarchy Process[M]. New York: McGraw-Hill, 1980. |
| [27] | QIN Danyang, JIA Shuang, YANG Songxiang, et al.Research on Trust Sensing-based Secure Routing Mechanism for Wireless Sensor Network[J]. Journal on Communications,2017(10): 60-70. |
| 秦丹阳,贾爽,杨松祥,等.基于信任感知的无线传感器网络安全路由机制研究[J]. 通信学报,2017(10):60-70. | |
| [28] | WANG Tian, ZHANG Guangxue, CAI Shaobin, et al.Research Progress of Trust Evaluation Mechanism in Sensor Cloud[J]. Journal on Communications,2018, 39(6): 41-55. |
| 王田,张广学,蔡绍滨,等.传感云中的信任评价机制研究进展[J].通信学报,2018,39(6):41-55. | |
| [29] | WANG Tian, ZHANG Guangxue, MD Zakirul Alam Bhuiyan, et al. A Novel Trust Mechanism Based on Fog Computing in Sensor-Cloud System[EB/OL]. , 2019-11-11. |
| [30] | CORTES C, VAPNIK V.Support-vector Networks[J]. Machine Learning, 1995, 20(3): 273-297. |
| [31] | HAN Guangjie, HE Yu, JIANG Jinfang, et al, A Synergetic Trust Model Based on SVM in Underwater Acoustic Sensor Networks[J]. IEEE Transactions on Vehicular Technology, 2019, 68(11): 11239-11247. |
| [1] | 亢保元, 王佳强, 邵栋阳, 李春青. 一种适用于异构Ad Hoc无线传感器网络的身份认证与密钥共识协议[J]. 信息网络安全, 2018, 18(1): 23-30. |
| [2] | 章红艳, 许力, 林丽美. 无线传感器网络中基于超立方体的对密钥建立方案研究[J]. 信息网络安全, 2017, 17(12): 1-5. |
| [3] | 沈天辰, 李欣, 孙海春. 基于MongoDB的云服务可靠性测量[J]. 信息网络安全, 2017, 17(11): 80-83. |
| [4] | 钟敦昊, 张冬梅, 张玉. 一种基于相似度计算的无线传感器网络入侵检测方法[J]. 信息网络安全, 2016, 16(2): 22-27. |
| [5] | 廖子渊, 陈明志, 邓辉. 基于评价可信度的云计算信任管理模型研究[J]. 信息网络安全, 2016, 16(2): 33-39. |
| [6] | 邵旭东, 蒋海平, 张菡. 基于光纤通信技术的数据单向传输可靠性研究[J]. 信息网络安全, 2016, 16(10): 76-79. |
| [7] | 刘伟, 叶清, 王成. 基于动态密钥管理的改进LEACH路由算法[J]. 信息网络安全, 2015, 15(8): 41-46. |
| [8] | 冯济舟, 田明辉. 软件潜在安全性缺陷测试案例的研究及思考[J]. 信息网络安全, 2015, 15(6): 85-90. |
| [9] | 苏彬庭, 方禾, 许力. 基于Q-Learning的无线传感器网络生命周期平衡路由[J]. 信息网络安全, 2015, 15(4): 74-77. |
| [10] | 龚婉婉, 刘士兴, 冯婷婷. 基于无线传感器网络的智能家居监控平台设计[J]. 信息网络安全, 2015, 15(3): 79-83. |
| [11] | 仇各各, 汪学明, 张言胜. 基于HECC的WSN身份认证协议研究[J]. 信息网络安全, 2015, 26(12): 54-58. |
| [12] | 杨骏玮, 方杰, 张仕斌, 陈建钧. WSNs中基于重复博弈的信任评价方法研究[J]. 信息网络安全, 2014, 14(8): 82-87. |
| [13] | 佟鑫;张利;戴明. 物联网感知层安全威胁建模研究[J]. , 2013, 13(Z): 0-0. |
| [14] | 胡刚;罗皓;梅越. 基于FMEA的OLTP系统可靠性设计与评价[J]. , 2013, 13(5): 0-0. |
| [15] | 郎为民;陈林;王昊. 无线传感器网络云连接认证研究[J]. , 2013, 13(3): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||