信息网络安全 ›› 2016, Vol. 16 ›› Issue (2): 33-39.doi: 10.3969/j.issn.1671-1122.2016.02.006
基于评价可信度的云计算信任管理模型研究
- 1. 福州大学数学与计算机科学学院,福建福州 350108
2. 网络系统信息安全福建省高校重点实验室,福建福州 350108
3. 安徽省淮南市公安局,安徽淮南 232001
Research on the Model of Cloud Computing Trust Management Based on Evaluation Credibility
Ziyuan LIAO1,2, Mingzhi CHEN1,2( ), Hui DENG3
), Hui DENG3
- 1.College of Mathematics and Computer Science, Fuzhou University, Fuzhou Fujian 350108, China
2. Key Lab of Information Security of Network System in Fujian Province, Fuzhou Fujian 350108, China
3. Huainan Municipal Public Security Bureau, Huainan Anhui 232001, China
摘要:
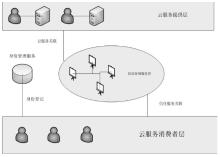
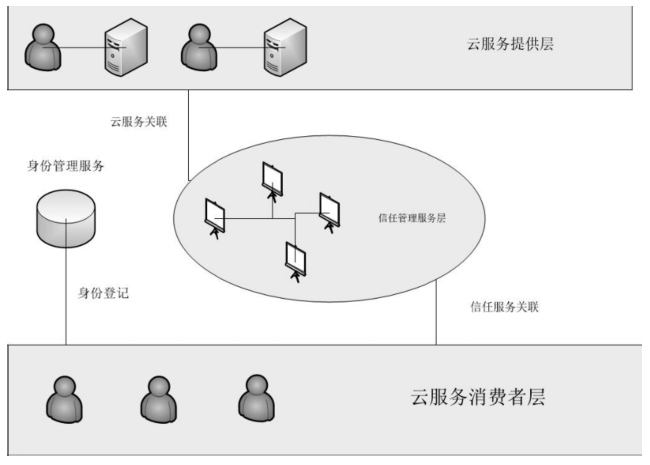
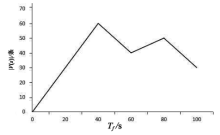
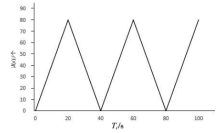
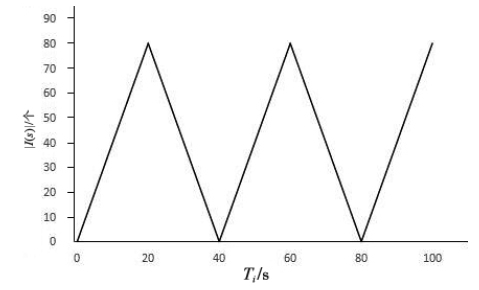
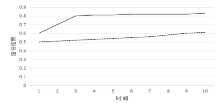
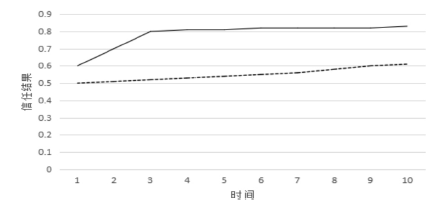
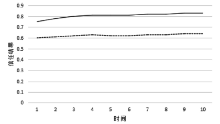
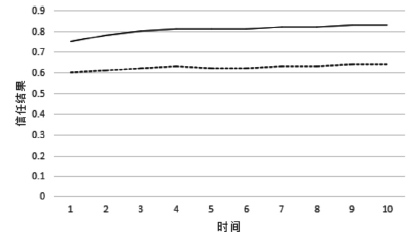
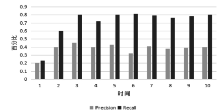
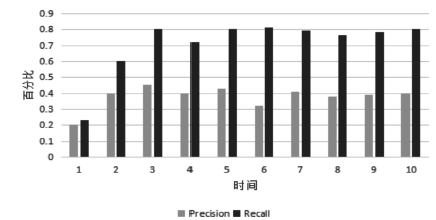
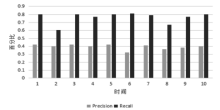
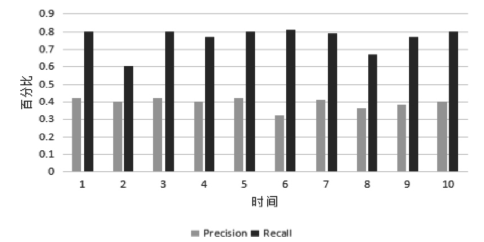
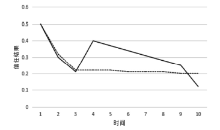
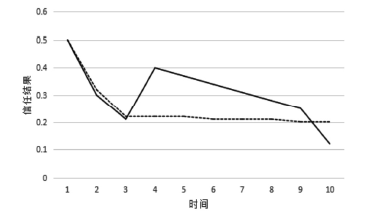
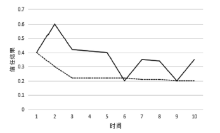
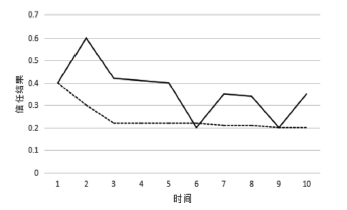
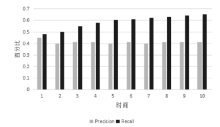
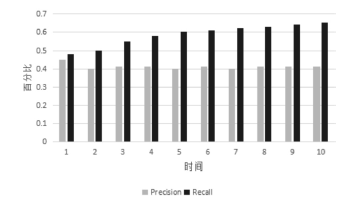
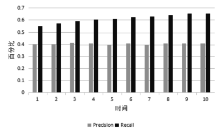
当前云计算发展十分迅速,而信任管理对其可持续发展而言是最具挑战性的问题之一。云计算因其高度动态、分布式以及非透明等特点而引发了若干关键性问题,如隐私性、安全性以及可用性。保护云服务商免受恶意用户的攻击也是一个棘手的问题。文章根据云计算信任管理的设计理念,引入一种计算用户评价可信度的方法,将计算得到的信任结果作为其评价证据的可信权重。用户一般分为两类,一类是正常用户,根据实际的交易情况给出可信评价;另一类是恶意用户,通过提交恶意评价来攻击服务实体。通过计算用户的评价可信度可识别出恶意用户,保护信任管理模型。文章使用云计算中真实的信任反馈建立实验,通过用户的评价可信度淘汰恶意用户,使用正常的用户反馈证明了该模型的可行性。
中图分类号: