信息网络安全 ›› 2020, Vol. 20 ›› Issue (4): 1-11.doi: 10.3969/j.issn.1671-1122.2020.04.001
5G网络切片安全模型研究
- 北京航空航天大学网络空间安全学院,北京 100191
-
收稿日期:2019-10-23出版日期:2020-04-10发布日期:2020-05-11 -
通讯作者:刘斌 E-mail:liubin12sun@163.com -
作者简介:作者简介:刘建伟(1964—),男,山东,教授,博士,主要研究方向为网络与信息安全、通信网络安全、密码学、信道编码技术等;韩祎然(1997—),女,辽宁,硕士研究生,主要研究方向为网络空间安全;刘斌(1995—),男,河南,硕士研究生,主要研究方向为5G网络接入认证与密钥协商协议;余北缘(1996—),男,北京,博士研究生,主要研究方向为物联网安全。
-
基金资助:国家自然科学基金[61972018]
Research on 5G Network Slicing Security Model
LIU Jianwei, HAN Yiran, LIU Bin( ), YU Beiyuan
), YU Beiyuan
- School of Cyber Science and Technology, Beihang University, Beijing 100191, China
-
Received:2019-10-23Online:2020-04-10Published:2020-05-11 -
Contact:Bin LIU E-mail:liubin12sun@163.com
摘要:
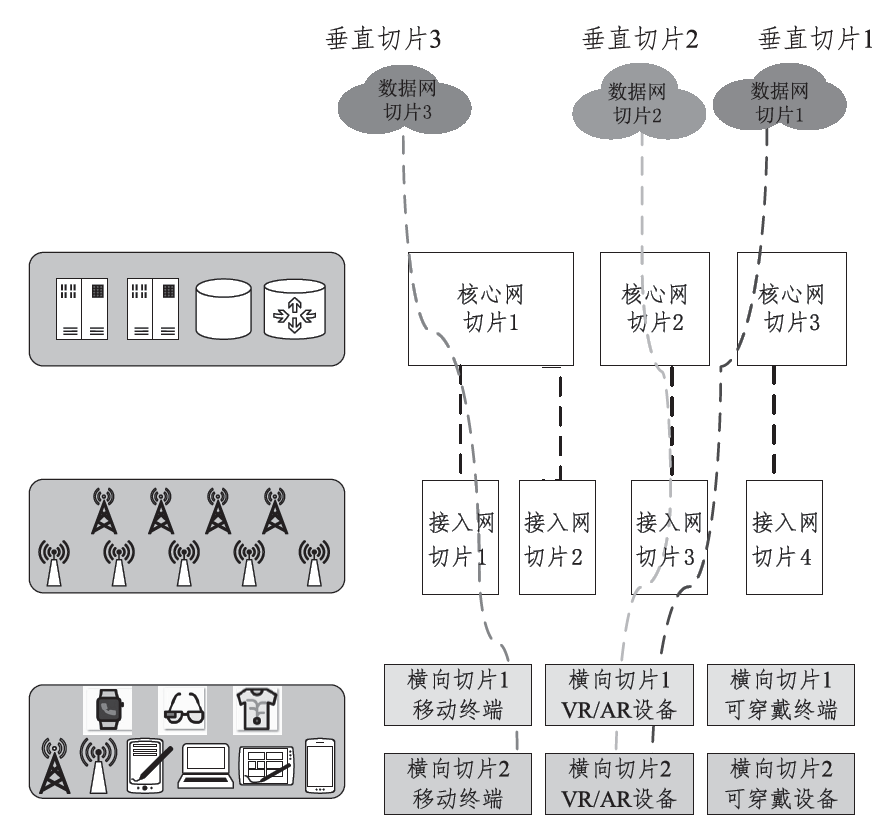
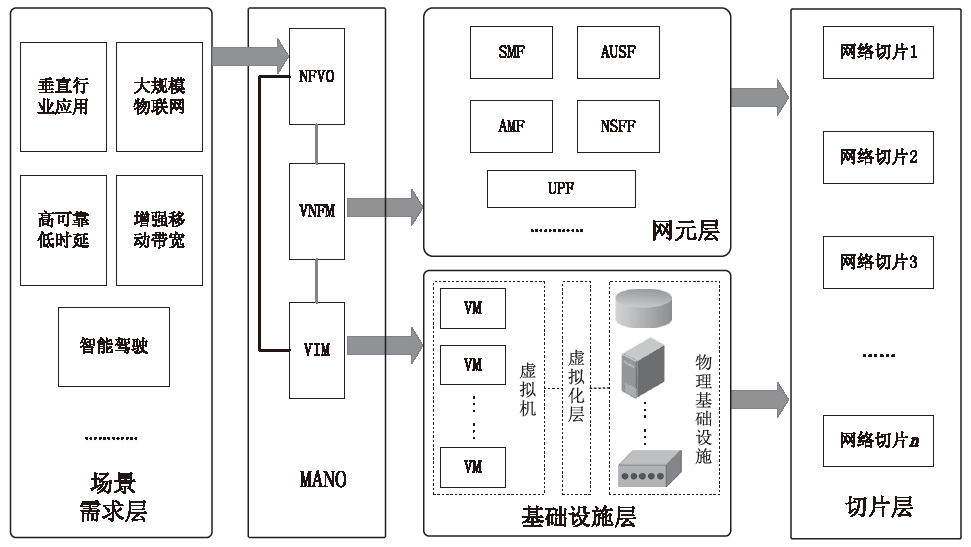
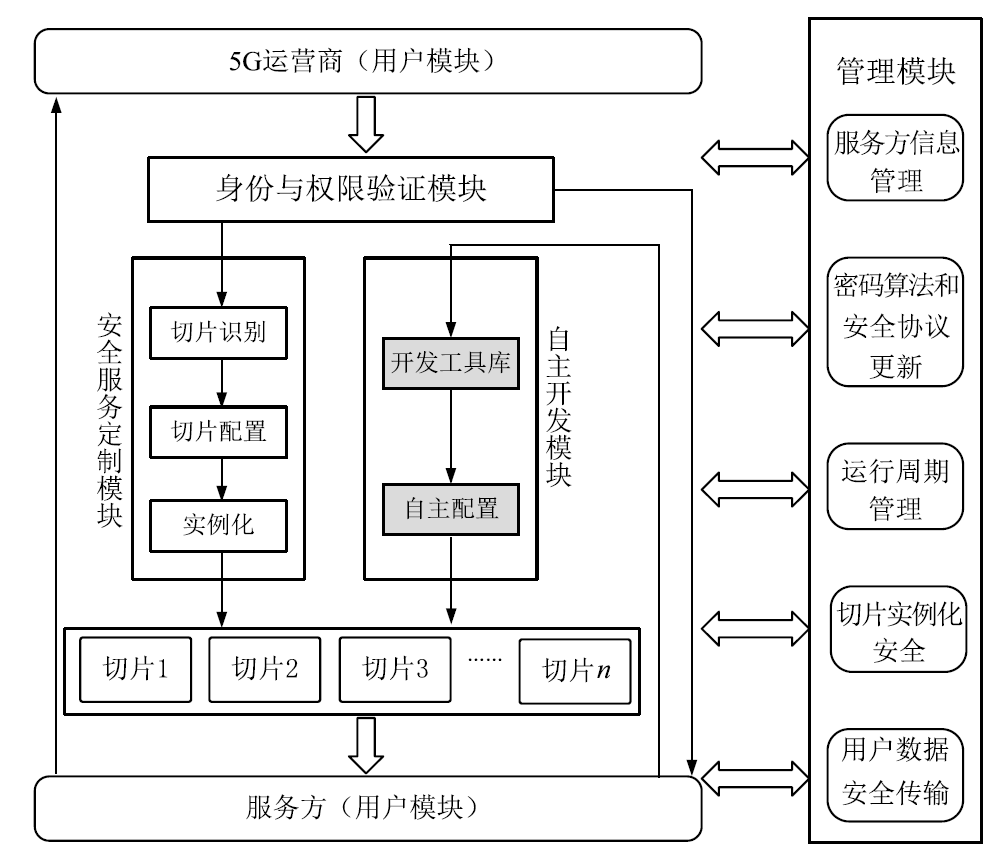
随着5G通信时代的到来,网络切片技术将与垂直行业深度融合,为用户提供更丰富的移动互联网和物联网业务。然而,网络切片技术的引入带来许多新的安全隐患与挑战,部分原有的安全防护技术不再适用。此外,各类切片的不同特点使得原有的安全服务无法满足网络切片中的不同需求。因此,研究网络切片技术存在的安全问题以及相应的应对策略并提出新的安全策略,是保障实现5G网络安全的关键所在。文章首先从网络切片的架构、管理模型和实现技术3个方面阐述了网络切片技术现存的安全问题;然后针对这些安全问题提出了维护切片安全的相关措施;最后建立了一个网络切片安全模型,为5G网络切片提供差异化的安全服务。
中图分类号:
引用本文
刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11.
LIU Jianwei, HAN Yiran, LIU Bin, YU Beiyuan. Research on 5G Network Slicing Security Model[J]. Netinfo Security, 2020, 20(4): 1-11.
| [1] | IMT-2020(5G). 5G Concept White Paper [EB/OL]. , 2018-10-13. |
| 第五代移动通信技术推进组. 5G概念白皮书[EB/OL]. , 2018-10-13. | |
| [2] | 3GPP TR 38.913. Study on Scenarios and Requirements for Next Generation Access Technologies[EB/OL]. , 2019-7-19. |
| [3] | IMT-2020(5G). 5G Security Requirements and Architecture White Paper[EB/OL]. , 2018-10-24. |
| 第五代移动通信技术推进组. 5G安全需求与架构白皮书[EB/OL]. , 2018-10-24. | |
| [4] | 3GPP TS 33.501. Security Architecture and Procedures for 5G System (Release 15)[EB/OL]. , 2019-7-19. |
| [5] | LIU Jianwei, WANG Yumin.Network Security: Technology and Practice[M]. 3rd editon. Beijing: Tsinghua University Press, 2017. |
| 刘建伟,王育民.网络安全: 技术与实践[M].第3版.北京:清华大学出版社,2017. | |
| [6] | Huawei. 5G Service Guaranteed Network Slicing Whitepaper[EB/OL]. , 2019-2-15. |
| [7] | 3GPP TS 33. 512. Access and Mobility Management Function(AMF)[EB/OL]. 2, 2018-11-19. |
| [8] | 3GPP TS 33.514.5G Security Assurance Specification(SCAS) for the Unified Data Management(UDM) Network Product Class[EB/OL]. , 2019-7-19. |
| [9] | KHAN M, NIEMI V.Concealing IMSI in 5G Network Using Identity Based Encryption[M]// Springer. Network and System Security. Cham: Springer, Cham, 2017: 544-554. |
| [10] | 3GPP TS 23. 012. Location Management Procedures(Release 14)[EB/OL]. , 2018-6-22. |
| [11] | YAO Shixiong, CHEN Jing, HE Kun, et al.PBCert: Privacy-Preserving Blockchain-based Certificate Status Validation Toward Mass Storage Management[J]. IEEE Access, 2018, 7: 6117-6128. |
| [12] | CEBE M, AKKAYA K. Efficient Certificate Revocation Management Schemes for IoT-based Advanced Metering Infrastructures in Smart Cities[EB/OL]. , 2019-7-19. |
| [13] | Huawei. 5G Security Architecture White Paper[EB/OL]. , 2019-3-17. |
| 华为. 5G安全架构白皮书[EB/OL]. ,2019-3-17. | |
| [14] | 3GPP TR 38. 802. Study on New Radio Access Technology Physical Layer Aspects(release 14)[EB/OL]. , 2017-9-26. |
| [15] | LIU Caixia, HU Xinxin, LIU Shuxin, et al.Security Analysis of 5G Network EAP-AKA’ Protocol Based on Lowe’s Taxonomy[J]. Journal of Electronics & Information Technology, 2019, 41(8): 1800-1807. |
| 刘彩霞,胡鑫鑫,刘树新,等.基于Lowe分类法的5G网络EAP-AKA’协议安全性分析[J].电子与信息学报,2019,41(8):1800-1807. | |
| [16] | BORDEL B, ORUE A B, ALCARRIA R, et al.An IntraSlice Security Solution for Emerging 5G Networks Based on Pseudo-Random Number Generators[J]. IEEE Access, 2018, 7: 16149-16164. |
| [17] | FU Yulong, ZHENG Yan, LI Hui.A Secure SDN-based Multi-RANs Architecture for Future 5G Networks[J]. Computers & Security, 2017, 70(9): 648-662. |
| [18] | 3GPP TS 23. 501. System Architecture for the 5G System[EB/OL]. , 2019-7-19. |
| [19] | SATTAR D, MATRAWY A.Towards Secure Slicing: Using Slice Isolation to Mitigate DDoS Attacks on 5G Core Network Slices[C]//IEEE. Conference on Communications and Network Security, June 10-12, 2019, Washington, USA. New York: IEEE, 2019: 82-90. |
| [20] | KHETTAB Y, BAGAA M, LEONEL D, et al.Virtual Security as a Service for 5G Verticals[C]//IEEE. Wireless Communications and Networking IEEE Conference, April 15-18, 2018, Barcelona, Spain. New York: IEEE, 2018: 1-6. |
| [21] | KOTULSKI Z, NOWAK T W, SEPCZUK M, et al. Graph-based Quantitative Description of Networks’ Slices Isolation[EB/OL]. , 2019-7-19. |
| [22] | HU Xinxin, LIU Caixia, LIU Shuxin, et al.Signalling Security Analysis: Is HTTP/2 Secure in 5G Core Network?[C]//IEEE. 10th International Conference on Wireless Communications and Signal Processing, October 18-20, 2018, Hangzhou, China. New York: IEEE, 2018: 1-6. |
| [23] | SATHI V N, SRINIVASAN M, THIRUVASAGAM P K, et al.A Novel Protocol for Securing Network Slice Component Association and Slice Isolation in 5G Networks[C]//MSWiM. The 21st ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, October 28-November 2, 2018, Montreal, QC, Canada. New York: ACM, 2018: 249-253. |
| [24] | HE Jialing, ZHANG Zijian, LI Meng, et al.Provable Data Integrity of Cloud Storage Service with Enhanced Security in the Internet of Things[J]. IEEE Access, 2018, 7: 6226-6239. |
| [25] | IMT-2020(5G). AI-based Intelligent Slice Management and Collaboration White Paper [EB/OL]. , 2019-3-21. |
| 第五代移动通信技术推进组. 基于AI的智能切片管理和协同白皮书[EB/OL]. , 2019-3-21. | |
| [26] | 3GPP TS 28.530. Management and Orchestration; Concepts, Use Cases and Requirements[EB/OL]. ,2019-9-25. |
| [27] | 3GPP TR 33.813. Study on Security Aspects of Enhanced Network Slicing(Rel-16)[EB/OL]. , 2019-9-25. |
| [28] | NI Jianbing, LIN Xiaodong, SHEN X S.Efficient and Secure Service-oriented Authentication Supporting Network Slicing for 5G-Enabled IoT[J]. IEEE Journal on Selected Areas in Communications, 2018, 36(3): 644-657. |
| [29] | WANG Xiaolei.Research on Virtual Resource Management Technology of 5G Network Slice[D]. Zhengzhou: Information Engineering University, 2018. |
| 王晓雷. 5G网络切片的虚拟资源管理技术研究[D].郑州:战略支援部队信息工程大学,2018. | |
| [30] | 3GPP TS 28.531. Management and Orchestration; Provisioning[EB/OL]. ,2019-6-12. |
| [31] | 3GPP TR 22.862. Technical Specification Group Services and System Aspects; Feasibility Study on New Services and Markets Technology Enablers for Critical Communications; Stage 1(Rel 14)[EB/OL]. ,2016-3-9. |
| [32] | BANNOUR F, SOUIHI S, MELLOUK A.Distributed SDN Control: Survey, Taxonomy, and Challenges[J]. IEEE Communications Surveys & Tutorials, 2018, 20(1): 333-354. |
| [33] | ETSI GS NFV-SEC 012. Network Functions Virtualisation(NFV) Release 3; Security; System Architecture Specification for Execution of Sensitive NFV Components[EB/OL]. ,2017-1-1. |
| [34] | YAO Jiaying, HAN Zhigeng, SOHAIL M, et al.A Robust Security Architecture for SDN-based 5G Networks[J]. Future Internet, 2019, 11(4): 338-346. |
| [35] | KIM H, PARK P, RYOU J.Auto-configurable Security Mechanism for NFV[J]. TIIS, 2018, 12(2): 786-799. |
| [36] | CCID Think Tank Radio Management Institute. Research Report on the Top 10 Application Segments of 5G [EB/OL]. , 2019-4-17. |
| 赛迪智库无线电管理研究所. 5G十大细分应用场景研究报告[EB/OL]. , 2019-4-17. | |
| [37] | CAICT. AR / VR White Paper[EB/OL]. , 2019-5-8. |
| 中国信息通信研究院. AR/VR白皮书[EB/OL]. , 2019-5-8. | |
| [38] | HSIAO T C, HUANG Yumin, CHUNG Y F, et al.Efficient Hierarchical Key Management Scheme for VR/AR Database Systems[J]. International Journal of Network Security, 2019, 22(4): 551-555. |
| [39] | CCID Research Institute. White Paper on the Development of China Ultra HD Video Industry[EB/OL]. , 2019-5-19. |
| 赛迪研究院. 中国超高清视频产业发展白皮书[EB/OL]. ,2019-5-19. | |
| [40] | CAICT. Internet of Vehicles White Paper[EB/OL]. , 2019-5-26. |
| 中国信息通信研究院. 车联网白皮书[EB/OL]. , 2019-5-26. | |
| [41] | TIMO VAN ROERMUND. In-Vehicle Networks and Security. Automotive Systems and Software Engineering[EB/OL]. , 2019-7-18. |
| [42] | IMT-2020(5G). 5G Drone Application White Paper[EB/OL]. , 2019-6-3. |
| 第五代移动通信技术推进组. 5G无人机应用白皮书[EB/OL]. , 2019-6-3. | |
| [43] | Internet Healthcare Industry Alliance. White Paper on Smart Healthcare in the 5G Era[EB/OL]. , 2019-6-23. |
| 互联网医疗健康产业联盟. 5G时代智慧医疗健康白皮书[EB/OL]. , 2019-6-23. | |
| [44] | LÜ Denglong, ZHU Shibing, LIU Ran. Research on Big Data Security Storage Based on Compressed Sensing[EB/OL]. , 2019-1-11. |
| [45] | Huawei. 5G Network Slicing for Vertical Industries[EB/OL]. , 2019-7-10. |
| [46] | IMT-2020(5G). M2M Task Force Technical Report[EB/OL]. , 2019-6-20. |
| 第五代移动通信技术推进组. M2M专题组技术报告[EB/OL]. ,2019-6-20. | |
| [47] | China Mobile Communications Corporation. 5G Smart City White Paper[EB/OL]. , 2019-7-18. |
| 中国移动通信集团公司. 5G智慧城市白皮书[EB/OL]. , 2019-7-18. | |
| [48] | China Mobile Communications Corporation. China Mobile Edge Computing White Paper[EB/OL]. , 2019-6-27. |
| 中国移动通信集团公司. 中国移动边缘计算白皮书[EB/OL]. ,2019-6-27. | |
| [49] | CSHIA, CAICT. China Smart Home Development White Paper[EB/OL]. , 2019-7-28. |
| 中国智能家居产业联盟,中国信息通信研究院. 中国智能家居发展白皮书[EB/OL]. , 2019-7-28. | |
| [50] | WHITEHURST L N, ANDEL T R, MCDONALD J T.Exploring Security in ZigBee Networks[C]//CISR. The 9th Annual Cyber and Information Security Research Conference, April 8-10, 2014, Oak Ridge, Tennessee, USA. New York: ACM, 2014: 25-28. |
| [51] | Huawei. Smart Security Open Architecture and Ecological White Paper[EB/OL]. , 2019-8-26. |
| 华为. 智能安防开放架构与生态白皮书[EB/OL]. ,2019-8-26. | |
| [52] | SIGWELE T, PILLAI P, SANGODOYIN A, et al.Security Aware Virtual Base Station Placement in 5G Cloud Radio Access Networks[C]//WISATS. International Conference on Wireless and Satellite Systems, September 14-15, 2017, Oxford, UK. Cham:Springer, Cham, 2017: 3-10. |
| [53] | CAICT. Artificial Intelligence Security White Paper[EB/OL]. , 2019-9-26. |
| 中国信息通信研究院. 人工智能安全白皮书[EB/OL]. , 2019-9-26. |
| [1] | 徐绘凯, 刘跃, 马振邦, 段海新. MQTT安全大规模测量研究[J]. 信息网络安全, 2020, 20(9): 37-41. |
| [2] | 刘大恒, 李红灵. QR码网络钓鱼检测研究[J]. 信息网络安全, 2020, 20(9): 42-46. |
| [3] | 李世斌, 李婧, 唐刚, 李艺. 基于HMM的工业控制系统网络安全状态预测与风险评估方法[J]. 信息网络安全, 2020, 20(9): 57-61. |
| [4] | 毕亲波, 赵呈东. 基于STRIDE-LM的5G网络安全威胁建模研究与应用[J]. 信息网络安全, 2020, 20(9): 72-76. |
| [5] | 孟相如, 徐江, 康巧燕, 韩晓阳. 基于熵权VIKOR的安全虚拟网络映射算法[J]. 信息网络安全, 2020, 20(5): 21-28. |
| [6] | 陈璐, 孙亚杰, 张立强, 陈云. 物联网环境下基于DICE的设备度量方案[J]. 信息网络安全, 2020, 20(4): 21-30. |
| [7] | 赵志岩, 纪小默. 智能化网络安全威胁感知融合模型研究[J]. 信息网络安全, 2020, 20(4): 87-93. |
| [8] | 黎水林, 祝国邦, 范春玲, 陈广勇. 一种新的等级测评综合得分算法研究[J]. 信息网络安全, 2020, 20(2): 1-6. |
| [9] | 郎为民, 张汉, 赵毅丰, 姚晋芳. 一种基于区块链的物联网行为监控和活动管理方案[J]. 信息网络安全, 2020, 20(2): 22-29. |
| [10] | 荆涛, 万巍. 面向属性迁移状态的P2P网络行为分析方法研究[J]. 信息网络安全, 2020, 20(1): 16-25. |
| [11] | 康健, 王杰, 李正旭, 张光妲. 物联网中一种基于多种特征提取策略的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 21-25. |
| [12] | 裘玥. 大型体育赛事网络安全风险分析与评估[J]. 信息网络安全, 2019, 19(9): 61-65. |
| [13] | 高孟茹, 谢方军, 董红琴, 林祥. 面向关键信息基础设施的网络安全评价体系研究[J]. 信息网络安全, 2019, 19(9): 111-114. |
| [14] | 陈良臣, 刘宝旭, 高曙. 网络攻击检测中流量数据抽样技术研究[J]. 信息网络安全, 2019, 19(8): 22-28. |
| [15] | 叶阿勇, 金俊林, 孟玲玉, 赵子文. 面向移动终端隐私保护的访问控制研究[J]. 信息网络安全, 2019, 19(8): 51-60. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||